Tunneling Definition E Commerce . It allows vpns to securely connect remote users. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. The transmission takes place using a public network; Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. However, the data are intended. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling is a networking technique used to securely transfer data over a public network. Learn more about tunneling protocols here.
from techterms.com
Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Learn more about tunneling protocols here. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling is a networking technique used to securely transfer data over a public network. However, the data are intended. Tunneling is a method of discretely transmitting data across an otherwise public network. The transmission takes place using a public network; It allows vpns to securely connect remote users.
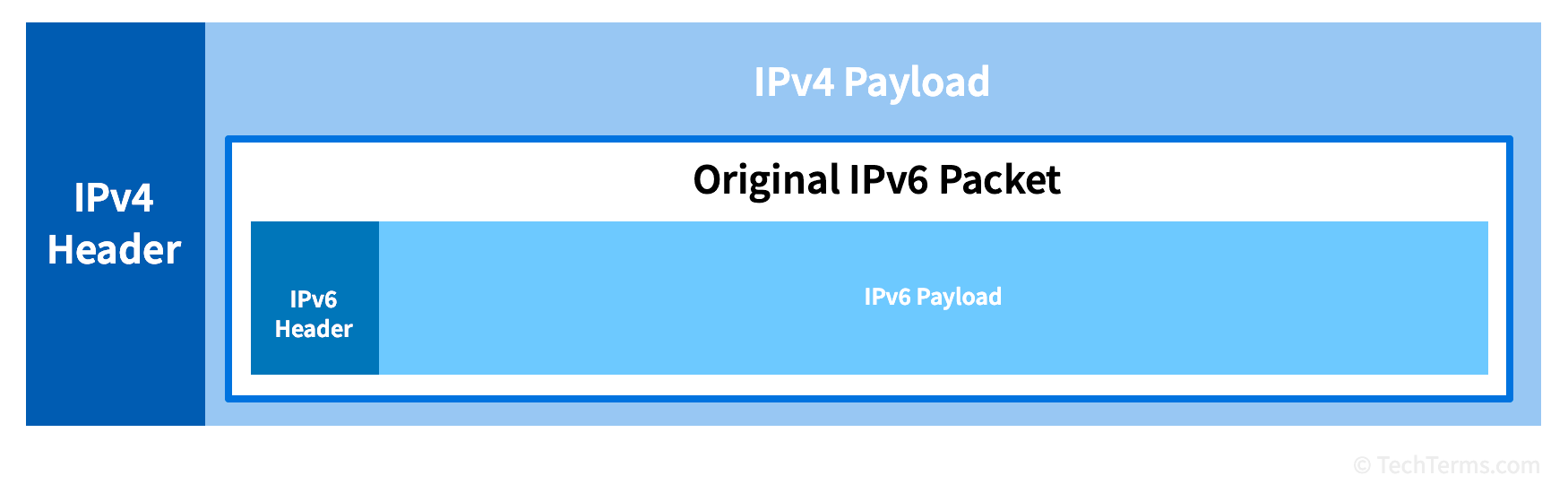
Tunneling Definition What is data tunneling?
Tunneling Definition E Commerce The transmission takes place using a public network; However, the data are intended. Learn more about tunneling protocols here. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. It allows vpns to securely connect remote users. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. The transmission takes place using a public network; Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Tunneling is a networking technique used to securely transfer data over a public network.
From www.definitions-webmarketing.com
Définition Tunnel de Conversion. Qu'est ce que ce terme signifie? Tunneling Definition E Commerce The transmission takes place using a public network; Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. However, the data are intended. Learn more about tunneling protocols here. Tunneling is a networking technique used to. Tunneling Definition E Commerce.
From www.socinvestigation.com
How DNS Tunneling works Detection & Response Security Investigation Tunneling Definition E Commerce Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. The transmission takes place using a public network; Tunneling is a method of discretely transmitting data across an otherwise public network. However, the data are intended. It allows vpns. Tunneling Definition E Commerce.
From www.dnssense.com
What is DNS Tunnelling? How Can You Prevent DNS Tunnelling Attacks? Tunneling Definition E Commerce Tunneling is a networking technique used to securely transfer data over a public network. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling is a method of discretely transmitting data across an otherwise public network. It allows vpns to securely connect remote users. Tunneling in computer networks is a way of communicating or transferring data. Tunneling Definition E Commerce.
From www.kpstructures.in
CLASSIFICATION OF TUNNELS KPSTRUCTURES Tunneling Definition E Commerce Tunneling is a method of discretely transmitting data across an otherwise public network. The transmission takes place using a public network; Tunneling is a networking technique used to securely transfer data over a public network. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Learn more about tunneling protocols here. However,. Tunneling Definition E Commerce.
From www.networkingsignal.com
What Is Tunnel In Networking, Its Types, And Its Benefits? Tunneling Definition E Commerce Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling is a networking technique used to securely transfer data over a public network. However, the data are intended. The transmission takes place using a public network; Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process. Tunneling Definition E Commerce.
From www.wizishop.fr
Tunnel de conversion Définition, étapes, conseils et exemples Tunneling Definition E Commerce Tunneling is a networking technique used to securely transfer data over a public network. It allows vpns to securely connect remote users. The transmission takes place using a public network; Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling is a versatile technique in cybersecurity, used for. Tunneling Definition E Commerce.
From bluecatnetworks.com
Why you should pay attention to DNS tunneling BlueCat Networks Tunneling Definition E Commerce Learn more about tunneling protocols here. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. The transmission takes place using a public network; Tunneling is a method of discretely transmitting data across an otherwise public. Tunneling Definition E Commerce.
From www.kpstructures.in
What is Tunnel Engineering Benefits of Tunneling (2024) KPSTRUCTURES Tunneling Definition E Commerce It allows vpns to securely connect remote users. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling is a networking technique used to securely transfer data over a public network. Tunneling—also referred to as. Tunneling Definition E Commerce.
From grammartop.com
TUNNEL Synonyms and Related Words. What is Another Word for TUNNEL Tunneling Definition E Commerce Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting. Tunneling Definition E Commerce.
From www.slideserve.com
PPT TUNNELLING PowerPoint Presentation, free download ID9503951 Tunneling Definition E Commerce Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling is a networking technique used to securely transfer data over a public network. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. The transmission takes place using a public network; Tunneling is a versatile technique in cybersecurity,. Tunneling Definition E Commerce.
From mungfali.com
Tunneling Diagram Tunneling Definition E Commerce Learn more about tunneling protocols here. Tunneling is a networking technique used to securely transfer data over a public network. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. The transmission takes place using a public network; Tunneling in computer networks is a way of communicating or transferring data from one. Tunneling Definition E Commerce.
From www.ma-formation-ecommerce.com
Tunnel de vente définition & explications Ma formation Tunneling Definition E Commerce The transmission takes place using a public network; Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Learn more about tunneling protocols here. However, the data are intended. Tunneling is. Tunneling Definition E Commerce.
From emi.mines.edu
Tunneling Earth Mechanics Institute Tunneling Definition E Commerce Learn more about tunneling protocols here. It allows vpns to securely connect remote users. Tunneling is a method of discretely transmitting data across an otherwise public network. However, the data are intended. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network. Tunneling Definition E Commerce.
From www.kpstructures.in
ENGLISH METHOD OF TUNNELING KPSTRUCTURES Tunneling Definition E Commerce Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Learn more about tunneling protocols here. However, the. Tunneling Definition E Commerce.
From www.youtube.com
DNS Tunneling Explained TryHackMe DNS Data Exfiltration YouTube Tunneling Definition E Commerce Tunneling is a networking technique used to securely transfer data over a public network. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. It allows vpns to securely connect remote users. However, the data are intended. Tunneling in. Tunneling Definition E Commerce.
From www.slideserve.com
PPT Network Protocol Tunneling PowerPoint Presentation, free download Tunneling Definition E Commerce Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. It allows vpns to securely connect remote users. Learn more about tunneling protocols here. However, the data are intended. The transmission takes place using a public network; Tunneling is a networking technique used to securely transfer data over a public network. Tunneling. Tunneling Definition E Commerce.
From www.ipvanish.com
What is split tunneling? Definition and use cases IPVanish Tunneling Definition E Commerce Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. It allows vpns to securely connect remote users. Learn more about tunneling protocols here. Tunneling is a method of discretely transmitting data across an otherwise public. Tunneling Definition E Commerce.
From www.slideserve.com
PPT Introduction to PPP PowerPoint Presentation, free download ID Tunneling Definition E Commerce However, the data are intended. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Learn more about tunneling protocols here. Tunneling is a method of discretely transmitting data across an otherwise public network. The transmission. Tunneling Definition E Commerce.
From www.entrepreneur-liberte.com
Qu'estce qu'un Tunnel de Vente ? EntrepreneurLiberte Tunneling Definition E Commerce The transmission takes place using a public network; Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. It allows vpns to securely connect remote users. Tunneling is a method of discretely transmitting data across an. Tunneling Definition E Commerce.
From techterms.com
Tunneling Definition What is data tunneling? Tunneling Definition E Commerce However, the data are intended. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling is a networking technique used to securely transfer data over a public network. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Tunneling in computer networks is a way of communicating or. Tunneling Definition E Commerce.
From www.researchgate.net
Multitenant packet definition. GTP, general tunneling protocol; IP Tunneling Definition E Commerce It allows vpns to securely connect remote users. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Learn more about tunneling protocols here. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling is. Tunneling Definition E Commerce.
From www.fastestvpnguide.com
What is VPN Split Tunneling? FastestVPNGuide Tunneling Definition E Commerce It allows vpns to securely connect remote users. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling is a networking technique used to securely transfer data over a public network. Learn more about tunneling protocols here. The transmission takes place using a public network; However, the data are intended. Tunneling is a versatile technique in. Tunneling Definition E Commerce.
From hsseworld.com
Tunneling Safety HSSE WORLD Tunneling Definition E Commerce Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling is a networking technique used to securely transfer data over a public network. It allows vpns to securely connect remote users. Tunneling—also referred to as port forwarding or network tunneling—is the process of. Tunneling Definition E Commerce.
From www.romainplagnard.com
Comment créer un tunnel de vente automatisé Tunneling Definition E Commerce Tunneling is a networking technique used to securely transfer data over a public network. It allows vpns to securely connect remote users. Learn more about tunneling protocols here. Tunneling is a method of discretely transmitting data across an otherwise public network. However, the data are intended. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private. Tunneling Definition E Commerce.
From unit42.paloaltonetworks.com
Understanding DNS Tunneling Traffic in the Wild Tunneling Definition E Commerce Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. The transmission takes place using a public network; Tunneling is a networking technique used to securely transfer data over a public network. However, the data are intended. It allows vpns to securely connect remote users. Learn more about tunneling. Tunneling Definition E Commerce.
From www.wizishop.fr
Tunnel de conversion Définition, étapes, conseils et exemples Tunneling Definition E Commerce However, the data are intended. Learn more about tunneling protocols here. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. The transmission takes place using a public network; Tunneling in computer networks is a way of communicating or. Tunneling Definition E Commerce.
From dataprot.net
What Is Split Tunneling? Best of Both Worlds DataProt Guides Tunneling Definition E Commerce The transmission takes place using a public network; Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Learn more about tunneling protocols here. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Tunneling is a versatile technique in cybersecurity,. Tunneling Definition E Commerce.
From www.blogdumoderateur.com
10 conseils pour optimiser votre tunnel d’achat Tunneling Definition E Commerce Learn more about tunneling protocols here. It allows vpns to securely connect remote users. The transmission takes place using a public network; Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through. Tunneling Definition E Commerce.
From civilmint.com
Tunnel engineering Everything You Need To Know Tunneling Definition E Commerce Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling in computer networks is a way of communicating or transferring data from one network to. Tunneling Definition E Commerce.
From www.enterprisenetworkingplanet.com
What Is Tunneling in Networking? Definition & How It Works Tunneling Definition E Commerce Learn more about tunneling protocols here. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Tunneling is a networking technique used to securely transfer data over a public network. The transmission takes place using a public network; Tunneling. Tunneling Definition E Commerce.
From gcore.com
What Is Tunneling? How Does Network Tunneling Work? Gcore Tunneling Definition E Commerce Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. It allows vpns to securely connect remote users. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling is a networking technique used to securely transfer data over a public network. Tunneling in computer networks is a way. Tunneling Definition E Commerce.
From www.thedigitalmkt.com
매출 극대화를 위한 세일즈 파이프라인 관리 5가지 방법 Digital Marketing Curation Tunneling Definition E Commerce Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. Tunneling is a networking technique used to securely transfer data over a public network. However, the data are intended. Tunneling is a method of discretely transmitting data across an otherwise public network. Tunneling in computer networks is a way of communicating or. Tunneling Definition E Commerce.
From www.sam-solutions.com
A Guide to an Efficient Platform SaM Solutions Tunneling Definition E Commerce Tunneling is a networking technique used to securely transfer data over a public network. However, the data are intended. Tunneling is a method of discretely transmitting data across an otherwise public network. Learn more about tunneling protocols here. Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. It. Tunneling Definition E Commerce.
From www.entrepreneur-liberte.com
Qu'estce qu'un Tunnel de Vente ? EntrepreneurLiberte Tunneling Definition E Commerce It allows vpns to securely connect remote users. Tunneling is a versatile technique in cybersecurity, used for a variety of purposes. The transmission takes place using a public network; Tunneling is a method of discretely transmitting data across an otherwise public network. However, the data are intended. Tunneling in computer networks is a way of communicating or transferring data from. Tunneling Definition E Commerce.
From www.gitech.info
[Marketing Digital] Gestion de la relation client en ligne GITECH Tunneling Definition E Commerce Tunneling in computer networks is a way of communicating or transferring data from one network to another through a process called. Learn more about tunneling protocols here. Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a. It allows vpns to securely connect remote users. The transmission takes place using a public. Tunneling Definition E Commerce.