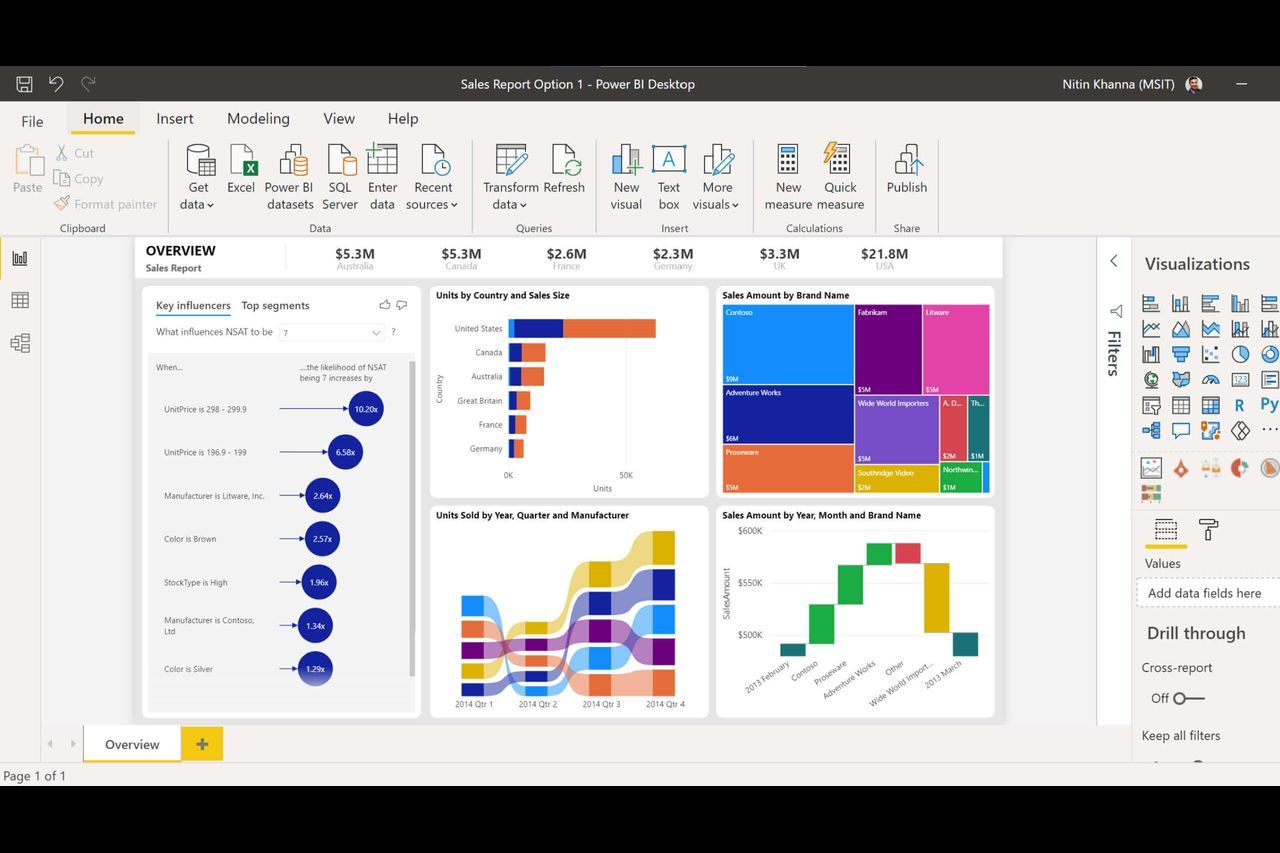
Power Bi Service Security Roles . In this power bi tutorial, we have learned what is power bi. Members can be user accounts, security groups, distribution groups or mail. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Create security groups on your aad or from the m365 admin centre and add members to them according to. With rls, you can ensure that users only see the. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. To use security groups in role mapping, you need to follow these steps:
from www.ilink-digital.com
With rls, you can ensure that users only see the. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Create security groups on your aad or from the m365 admin centre and add members to them according to. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Members can be user accounts, security groups, distribution groups or mail. To use security groups in role mapping, you need to follow these steps: In this power bi tutorial, we have learned what is power bi.
Microsoft Power BI Security 6 Best Practices iLink Digital
Power Bi Service Security Roles To use security groups in role mapping, you need to follow these steps: With rls, you can ensure that users only see the. Members can be user accounts, security groups, distribution groups or mail. Create security groups on your aad or from the m365 admin centre and add members to them according to. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. In this power bi tutorial, we have learned what is power bi. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. To use security groups in role mapping, you need to follow these steps:
From www.phdata.io
What Are the Workspace Access Roles in Power BI? phData Power Bi Service Security Roles With rls, you can ensure that users only see the. In this power bi tutorial, we have learned what is power bi. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Some roles are needed to create dataflows, and others. Power Bi Service Security Roles.
From alphabold.com
Power BI Security Roles Microsoft Dynamics Partner and CRM Consultant Power Bi Service Security Roles Members can be user accounts, security groups, distribution groups or mail. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. With rls, you can ensure that users only see the. To use security groups in role mapping, you need to follow these steps: In this power bi. Power Bi Service Security Roles.
From www.sqlshack.com
Implementing Security in Power BI Workspaces using User Roles Power Bi Service Security Roles Create security groups on your aad or from the m365 admin centre and add members to them according to. With rls, you can ensure that users only see the. In this power bi tutorial, we have learned what is power bi. To use security groups in role mapping, you need to follow these steps: Row level security (rls) is a. Power Bi Service Security Roles.
From www.enjoysharepoint.com
Power bi row level security tutorial Enjoy SharePoint Power Bi Service Security Roles Create security groups on your aad or from the m365 admin centre and add members to them according to. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data. Power Bi Service Security Roles.
From binokula.com
Binokula & Power BI RowLevel Security Power Bi Service Security Roles Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Create security groups on your aad or from the m365 admin centre and add members to them according to. With rls, you can ensure that users only see the. To use security groups in role mapping, you need. Power Bi Service Security Roles.
From community.powerbi.com
(Managing Roles) Assigning RowLevel Security with... Microsoft Power Power Bi Service Security Roles In this power bi tutorial, we have learned what is power bi. Create security groups on your aad or from the m365 admin centre and add members to them according to. Members can be user accounts, security groups, distribution groups or mail. To use security groups in role mapping, you need to follow these steps: Some roles are needed to. Power Bi Service Security Roles.
From www.mssqltips.com
Power BI Row Level Security Power Bi Service Security Roles Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. To use security groups in role mapping, you need to follow these steps: Members can be user accounts, security groups, distribution groups or mail. In this power bi tutorial, we have learned what is power bi. Create security. Power Bi Service Security Roles.
From skypointcloud.com
How Do We Improve Power BI Security? SkyPoint Cloud Power Bi Service Security Roles Members can be user accounts, security groups, distribution groups or mail. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. In this power bi tutorial, we have learned what is power bi. Create security groups on your aad or from the m365 admin centre and add members. Power Bi Service Security Roles.
From www.sqlshack.com
Implementing Security in Power BI Workspaces using User Roles Power Bi Service Security Roles Members can be user accounts, security groups, distribution groups or mail. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles. Power Bi Service Security Roles.
From learn.microsoft.com
Seguridad de nivel de fila (RLS) con Power BI Power BI Microsoft Learn Power Bi Service Security Roles Create security groups on your aad or from the m365 admin centre and add members to them according to. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Some roles are needed to create dataflows, and others are required to. Power Bi Service Security Roles.
From learn.microsoft.com
Power BI Security Power BI Microsoft Learn Power Bi Service Security Roles Members can be user accounts, security groups, distribution groups or mail. Create security groups on your aad or from the m365 admin centre and add members to them according to. To use security groups in role mapping, you need to follow these steps: With rls, you can ensure that users only see the. Some roles are needed to create dataflows,. Power Bi Service Security Roles.
From www.datasarva.com
Rowlevel security (RLS) in Power BI Power Bi Service Security Roles To use security groups in role mapping, you need to follow these steps: Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator. Power Bi Service Security Roles.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Service Security Roles To use security groups in role mapping, you need to follow these steps: Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. With rls, you can ensure that users only see the. In this power bi tutorial, we have learned. Power Bi Service Security Roles.
From www.biconnector.com
Power BI Row Level Security RLS Setup Stepbystep guide Power Bi Service Security Roles Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. To use security groups in role mapping, you need. Power Bi Service Security Roles.
From devblogs.microsoft.com
Implementing Power BI Rowlevel security (RLS) at the user level Power Bi Service Security Roles Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. In this power bi tutorial, we have learned what is power bi. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user. Power Bi Service Security Roles.
From www.pk-anexcelexpert.com
Static and Dynamic Row Level Security in Power BI PK An Excel Expert Power Bi Service Security Roles Members can be user accounts, security groups, distribution groups or mail. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Create security groups on your aad or from the m365 admin centre and add members to them according to. Some. Power Bi Service Security Roles.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Service Security Roles Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. With rls, you can ensure that users only see the. In this power bi tutorial, we have learned what is power bi. Some roles are needed to create dataflows, and others. Power Bi Service Security Roles.
From k21academy.com
Data Security in Power BI How to Implement and Configure Power Bi Service Security Roles Create security groups on your aad or from the m365 admin centre and add members to them according to. In this power bi tutorial, we have learned what is power bi. Members can be user accounts, security groups, distribution groups or mail. With rls, you can ensure that users only see the. Some roles are needed to create dataflows, and. Power Bi Service Security Roles.
From subscription.packtpub.com
Power BI project roles Mastering Microsoft Power BI Power Bi Service Security Roles Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Create security groups on your aad or from the. Power Bi Service Security Roles.
From techtarsolutions.com
Power BI Service Security, Collaboration, and Governance TechTAR Power Bi Service Security Roles With rls, you can ensure that users only see the. Members can be user accounts, security groups, distribution groups or mail. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. In this power bi tutorial, we have learned what is power bi. To use security groups in. Power Bi Service Security Roles.
From www.sqlcircuit.com
SQLCircuit Power BI Security Model Power Bi Service Security Roles In this power bi tutorial, we have learned what is power bi. To use security groups in role mapping, you need to follow these steps: With rls, you can ensure that users only see the. Create security groups on your aad or from the m365 admin centre and add members to them according to. Members can be user accounts, security. Power Bi Service Security Roles.
From www.youtube.com
Setting Up Power BI Row Level Security YouTube Power Bi Service Security Roles In this power bi tutorial, we have learned what is power bi. To use security groups in role mapping, you need to follow these steps: With rls, you can ensure that users only see the. Create security groups on your aad or from the m365 admin centre and add members to them according to. Members can be user accounts, security. Power Bi Service Security Roles.
From www.youtube.com
Row Level Security in Power BI to Manage Report Access By Job Role Power Bi Service Security Roles With rls, you can ensure that users only see the. Create security groups on your aad or from the m365 admin centre and add members to them according to. To use security groups in role mapping, you need to follow these steps: In this power bi tutorial, we have learned what is power bi. Members can be user accounts, security. Power Bi Service Security Roles.
From www.datasarva.com
Rowlevel security (RLS) in Power BI Power Bi Service Security Roles Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Create security groups on your aad or from the m365 admin centre and add members to them according to. To use security groups in role mapping, you need to follow these. Power Bi Service Security Roles.
From www.biinsight.com
Good Practice Use Security Groups in Role Mapping Instead of User Power Bi Service Security Roles Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Create security groups on your aad or from the. Power Bi Service Security Roles.
From www.myxxgirl.com
Describing Power Bi Row Level Security Roles In Tabular Editor My XXX Power Bi Service Security Roles Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. In this power bi tutorial, we have learned what is power bi. Members can be user accounts, security groups, distribution groups or mail. With rls, you can ensure that users only see the. Create security groups on your. Power Bi Service Security Roles.
From minova.nl
The four Power BI roles Minova Power Bi Service Security Roles To use security groups in role mapping, you need to follow these steps: Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Members can be user accounts, security groups, distribution groups or mail. In this power bi tutorial, we have learned what is power bi. Row level. Power Bi Service Security Roles.
From dxosydcqp.blob.core.windows.net
Power Bi Security Management at Lee Causey blog Power Bi Service Security Roles In this power bi tutorial, we have learned what is power bi. To use security groups in role mapping, you need to follow these steps: Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. Create security groups on your aad. Power Bi Service Security Roles.
From www.sqlchick.com
Groups in Power BI How Sharing and Security Works — SQL Chick Power Bi Service Security Roles Members can be user accounts, security groups, distribution groups or mail. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Create security groups on your aad or from the m365 admin centre and add members to them according to. To use security groups in role mapping, you. Power Bi Service Security Roles.
From k21academy.com
Data Security in Power BI How to Implement and Configure Power Bi Service Security Roles In this power bi tutorial, we have learned what is power bi. Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. To use security groups in role mapping, you need to follow these steps: With rls, you can ensure that. Power Bi Service Security Roles.
From www.datasarva.com
Rowlevel security (RLS) in Power BI Power Bi Service Security Roles In this power bi tutorial, we have learned what is power bi. To use security groups in role mapping, you need to follow these steps: Create security groups on your aad or from the m365 admin centre and add members to them according to. Some roles are needed to create dataflows, and others are required to control which tables a. Power Bi Service Security Roles.
From www.antaresanalytics.net
3 Steps to use Power BI Role Level Security Power Bi Service Security Roles Members can be user accounts, security groups, distribution groups or mail. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. With rls, you can ensure that users only see the. To use security groups in role mapping, you need to follow these steps: Row level security (rls). Power Bi Service Security Roles.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Service Security Roles Row level security (rls) is a crucial feature in power bi that allows you to restrict access to data at the row level based on user roles or permissions. With rls, you can ensure that users only see the. In this power bi tutorial, we have learned what is power bi. Create security groups on your aad or from the. Power Bi Service Security Roles.
From www.ilink-digital.com
Microsoft Power BI Security 6 Best Practices iLink Digital Power Bi Service Security Roles To use security groups in role mapping, you need to follow these steps: Create security groups on your aad or from the m365 admin centre and add members to them according to. Some roles are needed to create dataflows, and others are required to control which tables a dataflow creator can create or update. Row level security (rls) is a. Power Bi Service Security Roles.