Improper Access Control Security Vulnerability . Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. Common access control vulnerabilities include: The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. In addition to viewing unauthorized.
from cegchtdh.blob.core.windows.net
The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. Common access control vulnerabilities include: Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. In addition to viewing unauthorized. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform.
What Is Improper Asset Management Vulnerability at Charles Gomez blog
Improper Access Control Security Vulnerability In addition to viewing unauthorized. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. Common access control vulnerabilities include: The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. In addition to viewing unauthorized. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or.
From infosecwriteups.com
OWASPAccess Control Vulnerability by Sagar InfoSec Writeups Improper Access Control Security Vulnerability Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. In addition to viewing unauthorized. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles,. Improper Access Control Security Vulnerability.
From www.pullrequest.com
Golang's Improper Error Handling A Subtle Path to Security Improper Access Control Security Vulnerability The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. In addition to viewing unauthorized. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. Common access control vulnerabilities include: The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access. Improper Access Control Security Vulnerability.
From wsecservices.com
Vulnerability Assessment Sec Services Improper Access Control Security Vulnerability In addition to viewing unauthorized. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to. Improper Access Control Security Vulnerability.
From github.com
Improper access control to download file · Advisory · metersphere Improper Access Control Security Vulnerability The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based. Improper Access Control Security Vulnerability.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Improper Access Control Security Vulnerability The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The mechanism contains errors that prevent it from properly enforcing the. Improper Access Control Security Vulnerability.
From www.vogelitlawblog.com
Biggest cloud security vulnerability is misuse of employee credentials Improper Access Control Security Vulnerability Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The key aspect is. Improper Access Control Security Vulnerability.
From davidjosearaujo.gitbook.io
Finding Improper Assets Management Vulnerabilities API Improper Access Control Security Vulnerability Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Common access control vulnerabilities include: In addition to viewing unauthorized. The. Improper Access Control Security Vulnerability.
From safetyandsecurityafrica.com
What Is Broken Access Control Vulnerability, and How Can I Prevent It Improper Access Control Security Vulnerability In addition to viewing unauthorized. Common access control vulnerabilities include: Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. The key aspect is that improper access controls create vulnerabilities. Improper Access Control Security Vulnerability.
From lvivity.com
10 Most Common Application Security Vulnerabilities and Threats Improper Access Control Security Vulnerability The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. Common access control vulnerabilities include: Violation of the principle of least privilege or deny by default, where access should only. Improper Access Control Security Vulnerability.
From guvenlikzafiyet.barikat.com.tr
Improper Authorization Vulnerability In Confluence Data Center and Improper Access Control Security Vulnerability In addition to viewing unauthorized. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Violation of the principle of least privilege or deny by default, where. Improper Access Control Security Vulnerability.
From www.youtube.com
Understanding Improper Access Control Errors in Applications 7th Improper Access Control Security Vulnerability Common access control vulnerabilities include: Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems. Improper Access Control Security Vulnerability.
From www.prancer.io
Improper Asset Management OWASP top Security vulnerabilities Improper Access Control Security Vulnerability Common access control vulnerabilities include: In addition to viewing unauthorized. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. The key aspect is that improper access controls create vulnerabilities by allowing. Improper Access Control Security Vulnerability.
From securityboulevard.com
Improper Access Control In Django What It Looks Like and How To Fix It Improper Access Control Security Vulnerability Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. Common access control vulnerabilities include: The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Violation of the principle of least. Improper Access Control Security Vulnerability.
From www.nsa.gov
New Cybersecurity Advisory Warns About Application Vulnerabilities Improper Access Control Security Vulnerability Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. In addition to viewing unauthorized. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by. Improper Access Control Security Vulnerability.
From www.archerirm.community
"Improper Access Control Vulnerability" resulting in a change of access Improper Access Control Security Vulnerability Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. Broken access control (bac). Improper Access Control Security Vulnerability.
From coky-t.gitbook.io
脆弱性 不適切なアクセス制御 (Vulnerability Improper Access Control) owaspsmart Improper Access Control Security Vulnerability In addition to viewing unauthorized. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Once a flaw is discovered, the consequences of a flawed access control scheme can be. Improper Access Control Security Vulnerability.
From www.aserto.com
How to avoid Broken Access Control vulnerabilities a developer's guide Improper Access Control Security Vulnerability Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. In addition to viewing unauthorized. Violation of the principle of least privilege or deny by default, where access should only be granted. Improper Access Control Security Vulnerability.
From studioconsi.com
Improper Access Control Studio Consi Improper Access Control Security Vulnerability Common access control vulnerabilities include: In addition to viewing unauthorized. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The key aspect is that improper. Improper Access Control Security Vulnerability.
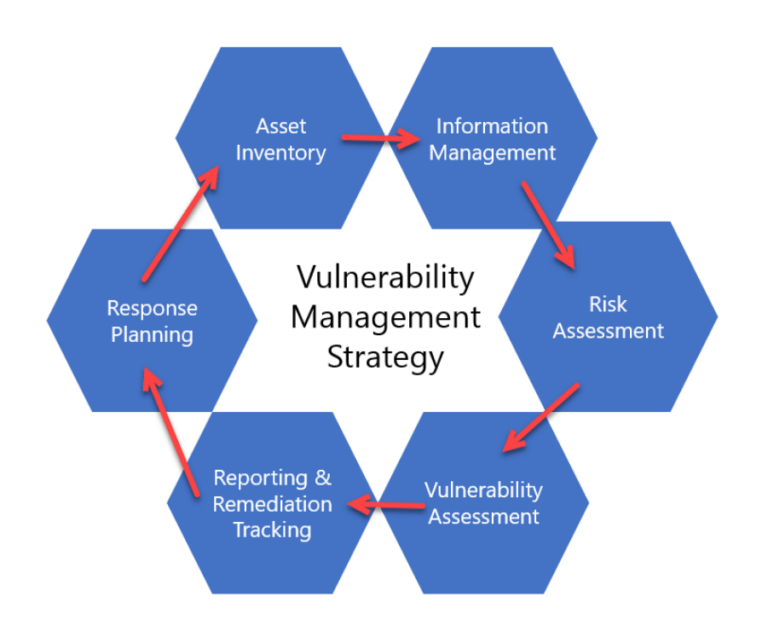
From digitalsecurityguide.eset.com
Vulnerability Management An essential component of your security strategy Improper Access Control Security Vulnerability Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Broken access control (bac) is a critical vulnerability that undermines the. Improper Access Control Security Vulnerability.
From cegchtdh.blob.core.windows.net
What Is Improper Asset Management Vulnerability at Charles Gomez blog Improper Access Control Security Vulnerability Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. The mechanism contains errors that prevent it from properly enforcing the. Improper Access Control Security Vulnerability.
From www.cve.news
CVE202352367 Vulnerability of Improper Access Control in the Media Improper Access Control Security Vulnerability Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. In addition to viewing unauthorized. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Once a flaw is discovered, the. Improper Access Control Security Vulnerability.
From www.youtube.com
How improper access controls lead to a breach YouTube Improper Access Control Security Vulnerability Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. Common access control vulnerabilities include: Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. Once a flaw is discovered, the consequences of a flawed access. Improper Access Control Security Vulnerability.
From github.com
Vulnerability Improper Access Control · Issue 2 · cybelesoft Improper Access Control Security Vulnerability In addition to viewing unauthorized. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Once a flaw is discovered, the consequences of a flawed. Improper Access Control Security Vulnerability.
From www.youtube.com
Stackhack improper access control vulnerability YouTube Improper Access Control Security Vulnerability Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they. Improper Access Control Security Vulnerability.
From themindstudios.com
How to Secure a site from Hackers Vulnerabilities + List of Tips Improper Access Control Security Vulnerability Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities,. Improper Access Control Security Vulnerability.
From cegchtdh.blob.core.windows.net
What Is Improper Asset Management Vulnerability at Charles Gomez blog Improper Access Control Security Vulnerability In addition to viewing unauthorized. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Violation of the principle of least. Improper Access Control Security Vulnerability.
From beaglesecurity.com
Improper Access Control Improper Access Control Security Vulnerability Common access control vulnerabilities include: The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. In addition to viewing unauthorized. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Once a flaw is discovered,. Improper Access Control Security Vulnerability.
From hackerone.com
Improper Access Control What Is It & How to Remediate Improper Access Control Security Vulnerability The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The mechanism contains errors that prevent it from properly enforcing the. Improper Access Control Security Vulnerability.
From cegchtdh.blob.core.windows.net
What Is Improper Asset Management Vulnerability at Charles Gomez blog Improper Access Control Security Vulnerability Common access control vulnerabilities include: The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. In addition to viewing unauthorized. Violation of the principle of least privilege. Improper Access Control Security Vulnerability.
From cegchtdh.blob.core.windows.net
What Is Improper Asset Management Vulnerability at Charles Gomez blog Improper Access Control Security Vulnerability Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. In addition to viewing unauthorized. Violation of the principle of least. Improper Access Control Security Vulnerability.
From www.youtube.com
900 Bounty for IMPROPER ACCESS CONTROLGENERIC Vulnerability BUG Improper Access Control Security Vulnerability Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or.. Improper Access Control Security Vulnerability.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Improper Access Control Security Vulnerability Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Common access control vulnerabilities include: In addition to viewing unauthorized. Broken access control (bac) is a critical vulnerability that undermines. Improper Access Control Security Vulnerability.
From www.tenablecloud.cn
ProFTPD Improper Access Control Vulnerability CVE201912815 Tenable® Improper Access Control Security Vulnerability Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or. Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g.,. Improper Access Control Security Vulnerability.
From www.openbugbounty.org
pari.edu Improper Access Control vulnerability OBB3925858 Open Bug Improper Access Control Security Vulnerability Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. Common access control vulnerabilities include: The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on. Violation of the principle of least privilege or deny by default, where. Improper Access Control Security Vulnerability.
From www.slideserve.com
PPT Secure Software PowerPoint Presentation, free download ID964405 Improper Access Control Security Vulnerability Broken access control (bac) is a critical vulnerability that undermines the security protocols of web applications by allowing unauthorized users to perform. The mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the. Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities,. Improper Access Control Security Vulnerability.