Create Connection With Ssh . Ssh, or secure shell, is a protocol used to securely log onto remote systems. You must connect your hardware security key to. To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. It is the most common way to access remote linux servers. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. The protocol provides a secure connection between a client and a server. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. It enables managing other computers, transferring.
from www.geeksforgeeks.org
It enables managing other computers, transferring. You must connect your hardware security key to. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. The protocol provides a secure connection between a client and a server. It is the most common way to access remote linux servers. Ssh, or secure shell, is a protocol used to securely log onto remote systems. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password.
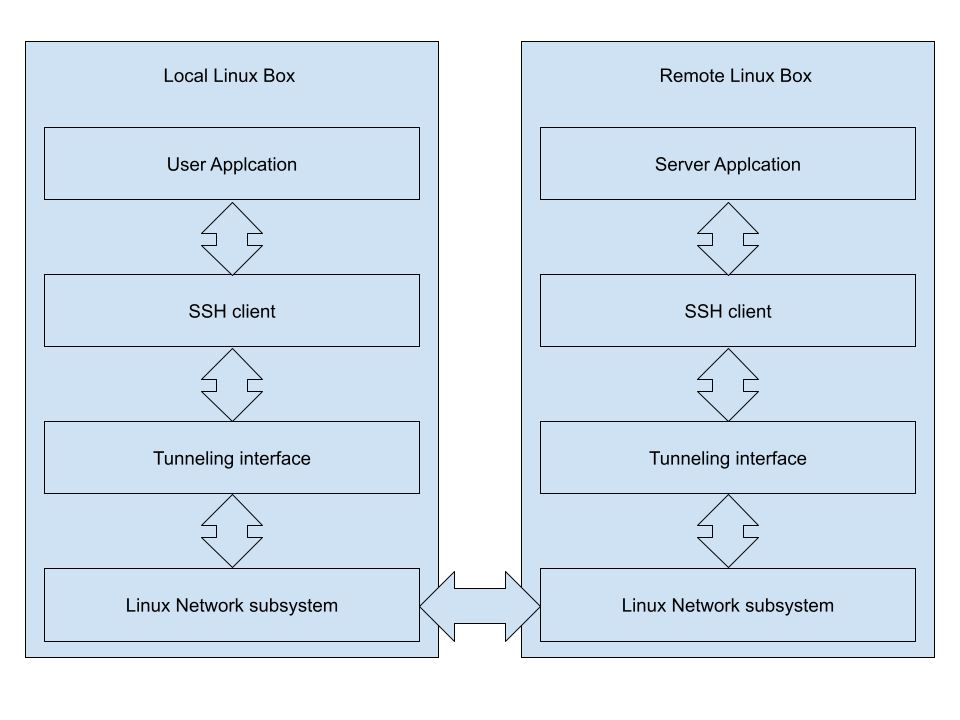
How to Create SSH Tunneling or Port Forwarding in Linux?
Create Connection With Ssh The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. You must connect your hardware security key to. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. Ssh, or secure shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote linux servers. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. The protocol provides a secure connection between a client and a server. It enables managing other computers, transferring. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer.
From ozeki.hu
How to create SSH tunnel for Ozeki softwares Create Connection With Ssh If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. It enables managing other computers, transferring. Ssh, or secure shell, is a protocol used to securely log onto remote systems. You must connect your hardware security key to. This article explains how to configure two. Create Connection With Ssh.
From cloudzy.com
vs. SSH How Is SSH Different From in 2022?🔍 Cloudzy Create Connection With Ssh To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. It is the most common way to access remote linux servers. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. This. Create Connection With Ssh.
From soft-builder.com
SSH Connection using Password authentication Docs for ERBuilder 7.0 Create Connection With Ssh To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. If you want to use a hardware security key to authenticate to. Create Connection With Ssh.
From www.geeksforgeeks.org
How to Troubleshoot SSH Connection Issues Create Connection With Ssh It enables managing other computers, transferring. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. You must connect your hardware security key to. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security. Create Connection With Ssh.
From blog.cybelesoft.com
How to create SSH connections from your browser using the New Create Connection With Ssh To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. It enables managing other computers, transferring. The protocol. Create Connection With Ssh.
From cloudonaut.io
Connect to your EC2 instance using SSH the modern way cloudonaut Create Connection With Ssh It is the most common way to access remote linux servers. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. The protocol provides a secure connection between a client and a server. Ssh, or secure shell, is a protocol used to securely log. Create Connection With Ssh.
From www.geeksforgeeks.org
How to use SSH to connect to a remote server in Linux ssh Command Create Connection With Ssh This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. It is the most common way to access remote linux servers. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. You. Create Connection With Ssh.
From www.stackscale.com
SSH protocol usage, versions and implementations Create Connection With Ssh Ssh, or secure shell, is a protocol used to securely log onto remote systems. To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your. Create Connection With Ssh.
From www.filecloud.com
How to Make Virtual Private Network (VPN) for SSH with Putty Create Connection With Ssh To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. It enables managing other computers, transferring. The protocol provides a secure connection between a client and a server. This article explains how to configure two computers for secure shell (ssh) connections, and how to. Create Connection With Ssh.
From supporthost.com
SSH connection the definitive guide (2024) SupportHost Create Connection With Ssh You must connect your hardware security key to. It is the most common way to access remote linux servers. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. It enables managing other computers, transferring. To initiate an ssh connection to a remote system, you need the internet. Create Connection With Ssh.
From publishingfasr602.weebly.com
Ssh Terminal publishingfasr Create Connection With Ssh It is the most common way to access remote linux servers. The protocol provides a secure connection between a client and a server. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. It enables managing other computers, transferring. This article explains how to configure. Create Connection With Ssh.
From blog.cloudlets.com.au
SSH Access Securely Connect and Manage Your Projects Remotely Create Connection With Ssh Ssh, or secure shell, is a protocol used to securely log onto remote systems. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. The protocol provides a secure connection between a client and a server. You must connect your hardware security key to. The. Create Connection With Ssh.
From winbuzzerag.pages.dev
How To Enable And Use Ssh Commands On Windows 10 winbuzzer Create Connection With Ssh Ssh, or secure shell, is a protocol used to securely log onto remote systems. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. It enables managing other computers, transferring. To initiate an ssh connection to a remote system, you need the internet protocol. Create Connection With Ssh.
From www.anyviewer.com
How to Create SSH Port Forwarding Create Connection With Ssh Ssh, or secure shell, is a protocol used to securely log onto remote systems. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. The protocol provides a secure connection between a client and a server. It enables managing other computers, transferring. You must connect. Create Connection With Ssh.
From www.keycdn.com
How to Create an SSH Key KeyCDN Support Create Connection With Ssh To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. The protocol provides a secure connection between a client and a server.. Create Connection With Ssh.
From phoenixnap.com
How to Use SSH to Connect to a Remote Server in Linux or Windows Create Connection With Ssh The protocol provides a secure connection between a client and a server. It is the most common way to access remote linux servers. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. The first step to configure ssh key authentication to your server is. Create Connection With Ssh.
From ostechnix.com
How To Manage Multiple SSH Connections In Linux OSTechNix Create Connection With Ssh If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. It enables managing other computers, transferring. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. Ssh, or secure shell, is a protocol. Create Connection With Ssh.
From blog.cybelesoft.com
How to create SSH connections from your browser using the New Create Connection With Ssh Ssh, or secure shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote linux servers. To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. It enables managing other computers, transferring. The protocol provides. Create Connection With Ssh.
From ploi.io
How do I connect with SSH? (Windows) Server Management Tool Create Connection With Ssh It enables managing other computers, transferring. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. You must connect your hardware security key to. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without. Create Connection With Ssh.
From www.hostinger.in
How to Use PuTTY SSH Client on Windows, Mac and Linux Create Connection With Ssh It enables managing other computers, transferring. To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a valid username. Ssh, or secure shell, is a protocol used to securely log onto remote systems. This article explains how to configure two computers for secure shell (ssh) connections, and. Create Connection With Ssh.
From gcore.de
Putty install and generate ssh keys GCore GmbH Create Connection With Ssh The protocol provides a secure connection between a client and a server. It is the most common way to access remote linux servers. Ssh, or secure shell, is a protocol used to securely log onto remote systems. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware. Create Connection With Ssh.
From www.nas.nasa.gov
Using MobaXterm for SSH Connections from Windows Systems to NAS HECC Create Connection With Ssh The protocol provides a secure connection between a client and a server. Ssh, or secure shell, is a protocol used to securely log onto remote systems. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. It is the most common way to access remote. Create Connection With Ssh.
From www.redswitches.com
Learn All About SSH Remote Connections In 7 Minutes Create Connection With Ssh It enables managing other computers, transferring. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. Ssh, or secure shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote linux servers. The protocol provides a secure connection between. Create Connection With Ssh.
From daily-dev-tips.com
Creating an SSH connection to a server Create Connection With Ssh This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. To initiate an ssh connection to a remote system, you need the. Create Connection With Ssh.
From www.dir-tech.com
How to connect to a server with SSH? Step by step guide Create Connection With Ssh If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. Ssh, or secure shell, is a protocol used to securely log onto remote systems. It enables managing other computers, transferring. You must connect your hardware security key to. This article explains how to configure two. Create Connection With Ssh.
From operisoft.com
SSH Connections to EC2 3 Methods for Secure Access Create Connection With Ssh This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. It enables managing other computers, transferring. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. Ssh, or secure. Create Connection With Ssh.
From www.tunnelsup.com
How to Create SSH Tunnels TunnelsUP Create Connection With Ssh You must connect your hardware security key to. It enables managing other computers, transferring. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to. Create Connection With Ssh.
From www.wpoven.com
How To Use SSH To Connect To Your Server Securely [Guide] Create Connection With Ssh If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. It is the most common way to access remote linux servers. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. It enables. Create Connection With Ssh.
From www.jetbrains.com.cn
Create SSH configurations Storm Create Connection With Ssh It is the most common way to access remote linux servers. It enables managing other computers, transferring. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. The protocol provides a secure connection between a client and a server. The first step to configure ssh. Create Connection With Ssh.
From www.geeksforgeeks.org
How to Create SSH Tunneling or Port Forwarding in Linux? Create Connection With Ssh The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. The protocol provides a secure connection between a client and a server. You. Create Connection With Ssh.
From www.works-hub.com
Managing remote servers with SSH and SFTP connections a stepbystep guide Create Connection With Ssh The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. Ssh, or secure shell, is a protocol used to securely log onto remote systems. To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote server and a. Create Connection With Ssh.
From blog.cybelesoft.com
How to create SSH connections from your browser using the New Create Connection With Ssh It is the most common way to access remote linux servers. It enables managing other computers, transferring. The first step to configure ssh key authentication to your server is to generate an ssh key pair on your local computer. Ssh, or secure shell, is a protocol used to securely log onto remote systems. You must connect your hardware security key. Create Connection With Ssh.
From www.youtube.com
How to Log in with a SSH Private Key on Linux Using PuTTY Login to Create Connection With Ssh This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other without a password. Ssh, or secure shell, is a protocol used to securely log onto remote systems. It enables managing other computers, transferring. The first step to configure ssh key authentication to your server is to generate. Create Connection With Ssh.
From www.arjancodes.com
ArjanCodes The Ultimate Guide to SSH Keys How to Create and Use Them Create Connection With Ssh If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. Ssh, or secure shell, is a protocol used to securely log onto remote systems. To initiate an ssh connection to a remote system, you need the internet protocol (ip) address or hostname of the remote. Create Connection With Ssh.
From www.geeksforgeeks.org
ssh command in Linux with Examples Create Connection With Ssh The protocol provides a secure connection between a client and a server. If you want to use a hardware security key to authenticate to github, you must generate a new ssh key for your hardware security key. This article explains how to configure two computers for secure shell (ssh) connections, and how to securely connect from one to the other. Create Connection With Ssh.