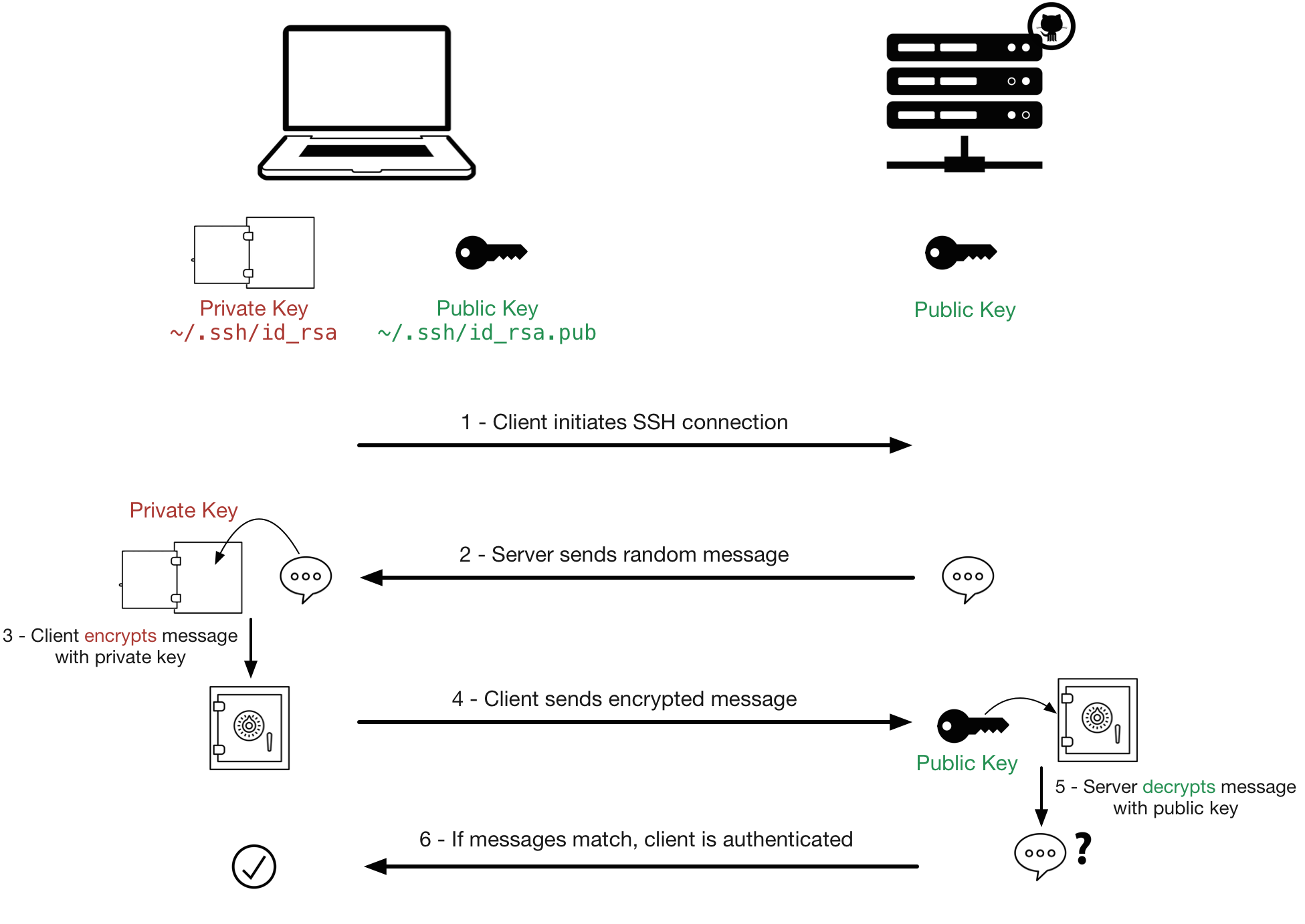
Sign Message Using Private Key . When encrypting, you use their public key to write a message and they use their private key to read it. Gpg, or gnu privacy guard, is a public key cryptography implementation. Encrypt with the public key, decrypt with the private key. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? This allows for the secure transmission of information between. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. You sign a message using the private key (not encrypt under the private key). A public key and a private key. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. Signing might superficially look similar to. Now, let's sign a message, using the rsa private key {n, d}. The hash function is selected with.
from sebastien.saunier.me
Gpg, or gnu privacy guard, is a public key cryptography implementation. When encrypting, you use their public key to write a message and they use their private key to read it. You sign a message using the private key (not encrypt under the private key). This allows for the secure transmission of information between. A public key and a private key. Signing might superficially look similar to. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. The hash function is selected with. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. Encrypt with the public key, decrypt with the private key.
GitHub public key authentication Sébastien Saunier
Sign Message Using Private Key This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. Signing might superficially look similar to. A public key and a private key. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. Encrypt with the public key, decrypt with the private key. Now, let's sign a message, using the rsa private key {n, d}. This allows for the secure transmission of information between. When encrypting, you use their public key to write a message and they use their private key to read it. The hash function is selected with. You sign a message using the private key (not encrypt under the private key). How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string?
From newscom.pages.dev
Public and private key encryption system News Com Sign Message Using Private Key How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. This allows. Sign Message Using Private Key.
From www.translateen.com
Use "Private Key" In A Sentence Sign Message Using Private Key To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. When encrypting, you use their public key to write a message and they use their private key to read it. A public key and. Sign Message Using Private Key.
From sebastien.saunier.me
GitHub public key authentication Sébastien Saunier Sign Message Using Private Key Now, let's sign a message, using the rsa private key {n, d}. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? Signing might superficially look similar to. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. Encrypt with. Sign Message Using Private Key.
From www.1kosmos.com
What Is a Private Key & How Does It Work? 1Kosmos Sign Message Using Private Key You sign a message using the private key (not encrypt under the private key). To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. Now, let's sign a message, using the rsa private key. Sign Message Using Private Key.
From cheapsslweb.com
Public Key and Private Key Pairs How do they work? Sign Message Using Private Key When encrypting, you use their public key to write a message and they use their private key to read it. Signing might superficially look similar to. Encrypt with the public key, decrypt with the private key. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a. Sign Message Using Private Key.
From sectigostore.com
What Is a Private Key? A 90Second Look at Secret Keys in Cybersecurity Sign Message Using Private Key The hash function is selected with. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? You sign a message using the private key (not encrypt under the private key). A public key and a private key. Gpg, or gnu privacy guard, is a public key cryptography implementation.. Sign Message Using Private Key.
From stackoverflow.com
go How to decrypt an encrypted message with RSA private key Stack Sign Message Using Private Key This allows for the secure transmission of information between. Now, let's sign a message, using the rsa private key {n, d}. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? When encrypting, you use their public key to write a message and they use their private key. Sign Message Using Private Key.
From www.immunebytes.com
Public and Private Keys What's the Difference? ImmuneBytes Sign Message Using Private Key When encrypting, you use their public key to write a message and they use their private key to read it. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the.. Sign Message Using Private Key.
From 12ships.pages.dev
Public key private key encryption example 12 Ships Sign Message Using Private Key This allows for the secure transmission of information between. A public key and a private key. Encrypt with the public key, decrypt with the private key. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? Calculate its hash and raise the hash to the power d modulo. Sign Message Using Private Key.
From bloxbytes.com
Blockchain Private Key QR Code Explained BloxBytes Sign Message Using Private Key The hash function is selected with. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? Encrypt with the public key, decrypt with the private key. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. Signing might superficially look. Sign Message Using Private Key.
From coindoo.com
How to Get Trust Wallet Private Key? Sign Message Using Private Key How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? This allows for the secure transmission of information between. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. Now, let's sign a message, using the rsa private key {n,. Sign Message Using Private Key.
From slideplayer.com
PublicKey Cryptography and Message Authentication ppt download Sign Message Using Private Key How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? The hash function is selected with. This allows for the secure transmission of information between. Now, let's sign a message, using the rsa private key {n, d}. You sign a message using the private key (not encrypt under. Sign Message Using Private Key.
From telegra.ph
Public And Private Keys Telegraph Sign Message Using Private Key This allows for the secure transmission of information between. The hash function is selected with. Gpg, or gnu privacy guard, is a public key cryptography implementation. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can. Sign Message Using Private Key.
From slideplayer.com
PublicKey Cryptography and Message Authentication ppt download Sign Message Using Private Key A public key and a private key. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? This allows for the secure transmission of information between. Now, let's sign a message, using the rsa private key {n, d}. Signing might superficially look similar to. You sign a message. Sign Message Using Private Key.
From www.preveil.com
Public and private encryption keys PreVeil Sign Message Using Private Key Encrypt with the public key, decrypt with the private key. This allows for the secure transmission of information between. Signing might superficially look similar to. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? A public key and a private key. The hash function is selected with.. Sign Message Using Private Key.
From www.dreamstime.com
Private key encryption stock image. Image of diagram 244662239 Sign Message Using Private Key Encrypt with the public key, decrypt with the private key. This allows for the secure transmission of information between. When encrypting, you use their public key to write a message and they use their private key to read it. The hash function is selected with. Signing might superficially look similar to. A public key and a private key. Now, let's. Sign Message Using Private Key.
From www.youtube.com
How to generate csr,selfsigned certificate,private key YouTube Sign Message Using Private Key This allows for the secure transmission of information between. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. When encrypting, you use their public key to write a message and they use their. Sign Message Using Private Key.
From sick.codes
How To Make a PGP Keypair using GPG and Communicate In Absolute Privacy Sign Message Using Private Key Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. This allows for the secure transmission of information between. The hash function is selected with. When encrypting, you use their public key to write a message and they use their private key to read it. A public key and a private key.. Sign Message Using Private Key.
From mailtrap.io
Email Encryption AllinOne Guide Mailtrap Blog Sign Message Using Private Key Encrypt with the public key, decrypt with the private key. You sign a message using the private key (not encrypt under the private key). Signing might superficially look similar to. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. The hash function is selected with. To send you a secret message,. Sign Message Using Private Key.
From studylib.net
The combination of private key (symmetric) and public key Sign Message Using Private Key To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. The hash function is selected with. Encrypt with the public key, decrypt with the private key. Now, let's sign a message, using the rsa. Sign Message Using Private Key.
From weteachblockchain.org
Public and Private Keys Sign Message Using Private Key This allows for the secure transmission of information between. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. The hash function is selected with. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to. Sign Message Using Private Key.
From www.youtube.com
HowTo Creating a Private Key for Signing ID Tokens YouTube Sign Message Using Private Key The hash function is selected with. You sign a message using the private key (not encrypt under the private key). Signing might superficially look similar to. When encrypting, you use their public key to write a message and they use their private key to read it. Calculate its hash and raise the hash to the power d modulo n (encrypt. Sign Message Using Private Key.
From www.kindpng.com
Digital Signature Public Key Private Key, HD Png Download kindpng Sign Message Using Private Key Now, let's sign a message, using the rsa private key {n, d}. Gpg, or gnu privacy guard, is a public key cryptography implementation. This allows for the secure transmission of information between. Encrypt with the public key, decrypt with the private key. How can i get the signature of a string using sha1withrsa if i already have the private key. Sign Message Using Private Key.
From www.preveil.com
Public and private encryption keys PreVeil Sign Message Using Private Key Now, let's sign a message, using the rsa private key {n, d}. This allows for the secure transmission of information between. A public key and a private key. Gpg, or gnu privacy guard, is a public key cryptography implementation. To send you a secret message, i use a public key to lock the message so nobody can read it, and. Sign Message Using Private Key.
From www.sectigo.com
Public Key Cryptography Private vs Public Sectigo® Official Sign Message Using Private Key Signing might superficially look similar to. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. You sign a message using the private key (not encrypt under the private key). When encrypting, you use. Sign Message Using Private Key.
From www.webhi.com
How to use a Private key for SSH authentication Tutorial & Documentation Sign Message Using Private Key Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. A public key and a private key. Signing might superficially look similar to. The hash function is selected with. Now, let's sign a message, using the rsa private key {n, d}. Gpg, or gnu privacy guard, is a public key cryptography implementation.. Sign Message Using Private Key.
From bloxbytes.com
Blockchain Private Key QR Code Explained BloxBytes Sign Message Using Private Key The hash function is selected with. Encrypt with the public key, decrypt with the private key. Gpg, or gnu privacy guard, is a public key cryptography implementation. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you. Sign Message Using Private Key.
From sectigostore.com
What Is a Private Key? A 90Second Look at Secret Keys in Cybersecurity Sign Message Using Private Key Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. Encrypt with the public key, decrypt. Sign Message Using Private Key.
From slideplayer.com
PublicKey Cryptography and Message Authentication ppt download Sign Message Using Private Key This allows for the secure transmission of information between. To send you a secret message, i use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it. You sign a message using the private key (not encrypt under the private key). A. Sign Message Using Private Key.
From www.freepik.com
Premium Vector Private key Sign Message Using Private Key You sign a message using the private key (not encrypt under the private key). Encrypt with the public key, decrypt with the private key. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. The hash function is selected with. Signing might superficially look similar to. When encrypting, you use their public. Sign Message Using Private Key.
From bloxbytes.com
Blockchain Private Key QR Code Explained BloxBytes Sign Message Using Private Key This allows for the secure transmission of information between. A public key and a private key. Encrypt with the public key, decrypt with the private key. Calculate its hash and raise the hash to the power d modulo n (encrypt the hash by the. To send you a secret message, i use a public key to lock the message so. Sign Message Using Private Key.
From blog.mdaemon.com
Encrypting vs. Signing with OpenPGP. What’s the Difference? Sign Message Using Private Key Gpg, or gnu privacy guard, is a public key cryptography implementation. Now, let's sign a message, using the rsa private key {n, d}. The hash function is selected with. You sign a message using the private key (not encrypt under the private key). When encrypting, you use their public key to write a message and they use their private key. Sign Message Using Private Key.
From twitter.com
Binance on Twitter "Private keys, made simple. For cryptocurrencies, a Sign Message Using Private Key Gpg, or gnu privacy guard, is a public key cryptography implementation. Signing might superficially look similar to. Now, let's sign a message, using the rsa private key {n, d}. You sign a message using the private key (not encrypt under the private key). Encrypt with the public key, decrypt with the private key. To send you a secret message, i. Sign Message Using Private Key.
From p2panda.org
Entries p2panda Sign Message Using Private Key Now, let's sign a message, using the rsa private key {n, d}. The hash function is selected with. Encrypt with the public key, decrypt with the private key. How can i get the signature of a string using sha1withrsa if i already have the private key as byte[] or string? A public key and a private key. You sign a. Sign Message Using Private Key.