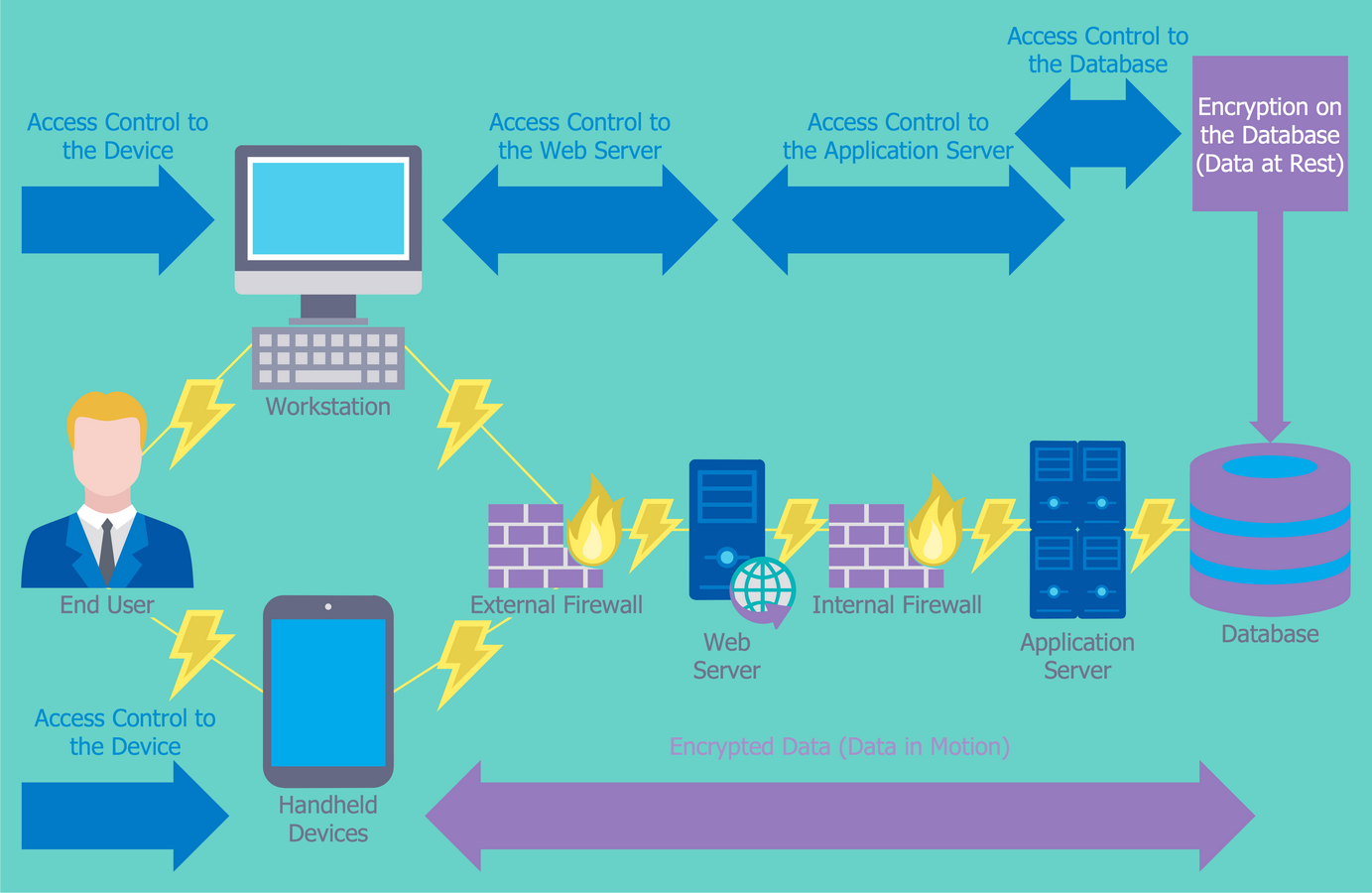
Security Engineering Access Control Models . 10k+ visitors in the past month Various access control models provide frameworks for implementing access control policies effectively. Access control is the process of mediating every request to resources and data maintained by a system and determining. Uncover the secrets of access control models in cybersecurity. Enhance your organization's security with dac, mac, rbac. There are several traditional and hybrid access control models that have various pros and cons. 10k+ visitors in the past month Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. The technical term for this is “access control”. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for.
from www.conceptdraw.com
10k+ visitors in the past month Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. There are several traditional and hybrid access control models that have various pros and cons. Enhance your organization's security with dac, mac, rbac. 10k+ visitors in the past month Uncover the secrets of access control models in cybersecurity. Various access control models provide frameworks for implementing access control policies effectively. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. The technical term for this is “access control”. Access control is the process of mediating every request to resources and data maintained by a system and determining.
Network Security Model
Security Engineering Access Control Models Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. There are several traditional and hybrid access control models that have various pros and cons. 10k+ visitors in the past month The technical term for this is “access control”. Access control is the process of mediating every request to resources and data maintained by a system and determining. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Various access control models provide frameworks for implementing access control policies effectively. 10k+ visitors in the past month Uncover the secrets of access control models in cybersecurity. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. Enhance your organization's security with dac, mac, rbac.
From sssengineeringbd.com
Access Control System with all type of Hardware and Software Solution Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. Various access control models provide frameworks for implementing access control policies effectively. The technical term for this is “access control”. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Role based access control (rbac) (also called role based security), as formalized in 1992 by. Security Engineering Access Control Models.
From study.com
Access Control Matrix Definition, Function & Examples Lesson Security Engineering Access Control Models The technical term for this is “access control”. 10k+ visitors in the past month Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. There are several traditional and hybrid access control models that have various pros and cons. Various access control models provide frameworks for implementing access control policies effectively. Enhance your. Security Engineering Access Control Models.
From cyberhoot.com
Access Control Mechanism CyberHoot Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. Uncover the secrets of access control models in cybersecurity. There are several traditional and hybrid access control models that have various pros and cons. 10k+ visitors in the past month 10k+ visitors in the past month Access control is the process of mediating every request to resources and data maintained by a. Security Engineering Access Control Models.
From www.fingerprint-access-control.com
Fingerprint Access Control Systems Security Systems by Borer Data Security Engineering Access Control Models Uncover the secrets of access control models in cybersecurity. Enhance your organization's security with dac, mac, rbac. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Access control is the process of mediating every request to resources and data maintained by a system and determining. There are several traditional and hybrid access. Security Engineering Access Control Models.
From thecyphere.com
Access Control Security Types Of Access Control Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. 10k+ visitors in the past month Uncover the secrets of access control models in cybersecurity. The technical term for this is “access control”. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. 10k+ visitors in. Security Engineering Access Control Models.
From www.strongdm.com
3 Types of Access Control IT Security Models Explained StrongDM Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. 10k+ visitors in the past month There are several traditional and hybrid access control models that have various pros and cons. 10k+ visitors in the past month Access control is the process of mediating every request to resources and data maintained by a system and determining. The technical term for this is. Security Engineering Access Control Models.
From www.conceptdraw.com
Network Security Model Security Engineering Access Control Models Various access control models provide frameworks for implementing access control policies effectively. Access control is the process of mediating every request to resources and data maintained by a system and determining. 10k+ visitors in the past month Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. 10k+ visitors in the past month. Security Engineering Access Control Models.
From www.bartleby.com
Types of Security Models bartleby Security Engineering Access Control Models Uncover the secrets of access control models in cybersecurity. Various access control models provide frameworks for implementing access control policies effectively. 10k+ visitors in the past month The technical term for this is “access control”. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model. Security Engineering Access Control Models.
From www.slideserve.com
PPT Chapter 3 Security Architecture and Models PowerPoint Security Engineering Access Control Models The technical term for this is “access control”. Uncover the secrets of access control models in cybersecurity. There are several traditional and hybrid access control models that have various pros and cons. Various access control models provide frameworks for implementing access control policies effectively. 10k+ visitors in the past month Access control is the process of mediating every request to. Security Engineering Access Control Models.
From michaelonsecurity.blogspot.com
Michael on Security Security Maturity Models (Part 1 of 2) Security Engineering Access Control Models There are several traditional and hybrid access control models that have various pros and cons. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Uncover the secrets of access control models in cybersecurity. Enhance your organization's security with dac, mac, rbac. The technical term for this is “access control”. 10k+ visitors in. Security Engineering Access Control Models.
From fpov.com
Integrated Security Model Future Point Of View Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. 10k+ visitors in the past month The technical term for this is “access control”. Uncover the secrets of access control models in cybersecurity. 10k+ visitors in the past month Role based access control (rbac) (also. Security Engineering Access Control Models.
From geraintw.blogspot.com
GeraintW Online Blog Access control Security Engineering Access Control Models Uncover the secrets of access control models in cybersecurity. 10k+ visitors in the past month 10k+ visitors in the past month Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become. Security Engineering Access Control Models.
From guidespecial.weebly.com
Analysis of dac mac rbac access control based models for security Security Engineering Access Control Models 10k+ visitors in the past month The technical term for this is “access control”. Uncover the secrets of access control models in cybersecurity. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn,. Security Engineering Access Control Models.
From www.gdata.pt
G DATA Layered Security thoroughly sophisticated IT security Security Engineering Access Control Models Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. Various access control models provide frameworks for implementing access control policies effectively. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Access control is the process. Security Engineering Access Control Models.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Security Engineering Access Control Models There are several traditional and hybrid access control models that have various pros and cons. Access control is the process of mediating every request to resources and data maintained by a system and determining. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for.. Security Engineering Access Control Models.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. There are several traditional and hybrid access control models that have various pros and cons. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. The technical term for this is “access control”. Various access control models provide frameworks for implementing access control policies effectively.. Security Engineering Access Control Models.
From www.conceptdraw.com
Network Security Model Security Engineering Access Control Models The technical term for this is “access control”. 10k+ visitors in the past month There are several traditional and hybrid access control models that have various pros and cons. 10k+ visitors in the past month Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Various access control models provide frameworks for implementing. Security Engineering Access Control Models.
From solatatech.com
The Security Operating Model A Strategic Approach For Building a More Security Engineering Access Control Models Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. There are several traditional and hybrid access control models that have various pros and cons. Various access control models provide frameworks for implementing access control policies effectively. Access control is a fundamental component of. Security Engineering Access Control Models.
From www.coresecurity.com
What is Privileged Access Management? Core Security Security Engineering Access Control Models 10k+ visitors in the past month Various access control models provide frameworks for implementing access control policies effectively. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. 10k+ visitors in the past month Uncover the secrets of access control models in cybersecurity. There are several traditional and hybrid access control models that. Security Engineering Access Control Models.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. 10k+ visitors in the past month There are several traditional and hybrid access control models that have various pros and cons. The technical term for this is “access control”. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Uncover the secrets of access control. Security Engineering Access Control Models.
From www.educba.com
Security engineering Learn the basic concepts of security Engineering Security Engineering Access Control Models The technical term for this is “access control”. 10k+ visitors in the past month Enhance your organization's security with dac, mac, rbac. Various access control models provide frameworks for implementing access control policies effectively. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for.. Security Engineering Access Control Models.
From www.youtube.com
Access Control Models CompTIA Security+ SY0501 4.3 YouTube Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Access control is the process of mediating every request to resources and data maintained by a system and determining. Uncover the secrets of access control models in cybersecurity. There are several traditional and hybrid access. Security Engineering Access Control Models.
From www.cipherspace.com
5 Steps for Implementing IT Security Controls What to do, and How to Security Engineering Access Control Models Various access control models provide frameworks for implementing access control policies effectively. There are several traditional and hybrid access control models that have various pros and cons. Access control is the process of mediating every request to resources and data maintained by a system and determining. Enhance your organization's security with dac, mac, rbac. 10k+ visitors in the past month. Security Engineering Access Control Models.
From www.appknox.com
Organizational Dynamics for Info Security & Security Models Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. 10k+ visitors in the past month Uncover the secrets of access control models in cybersecurity. Access control is the process of mediating every request to resources. Security Engineering Access Control Models.
From nocomplexity.com
Security Models — Security Reference Architecture Security Engineering Access Control Models 10k+ visitors in the past month Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. There are several traditional and hybrid access control models that have various pros and cons. Access control is the process of mediating every request to resources and data maintained by a system and determining. The technical term. Security Engineering Access Control Models.
From frontegg.com
What is RoleBased Access Control RBAC vs ABAC Security Engineering Access Control Models There are several traditional and hybrid access control models that have various pros and cons. Enhance your organization's security with dac, mac, rbac. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. Various access control models provide frameworks for implementing access control policies. Security Engineering Access Control Models.
From www.scribd.com
Comprehensive Overview of Key Access Control Models and Principles for Security Engineering Access Control Models Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Enhance your organization's security with dac, mac, rbac. Various access control models provide frameworks for implementing access control policies effectively. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the. Security Engineering Access Control Models.
From www.researchgate.net
Access Control and Other Security Services Download Scientific Diagram Security Engineering Access Control Models Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. 10k+ visitors in the past month Enhance your organization's security with dac, mac, rbac. 10k+ visitors in the past month Various access control models provide frameworks for implementing access control policies effectively. Role based access control (rbac) (also called role based security), as. Security Engineering Access Control Models.
From searchcloudcomputing.techtarget.com
Secure data in the cloud with encryption and access controls Security Engineering Access Control Models Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. The technical term for this is “access control”. Access control is the process of mediating every request to resources and data maintained by a system and determining. There are several traditional and hybrid access control models that have various pros and cons. Role. Security Engineering Access Control Models.
From www.harlingsecurity.com
Benefits of Access Control Systems Harling Security Security Engineering Access Control Models Various access control models provide frameworks for implementing access control policies effectively. 10k+ visitors in the past month Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. Access control is the process of mediating every request to resources and data maintained by a. Security Engineering Access Control Models.
From www.springboard.com
How To an Information Security Analyst [9 Step Guide] Security Engineering Access Control Models Enhance your organization's security with dac, mac, rbac. Uncover the secrets of access control models in cybersecurity. There are several traditional and hybrid access control models that have various pros and cons. 10k+ visitors in the past month Various access control models provide frameworks for implementing access control policies effectively. The technical term for this is “access control”. Access control. Security Engineering Access Control Models.
From people.cs.rutgers.edu
Access Control Security Engineering Access Control Models Uncover the secrets of access control models in cybersecurity. 10k+ visitors in the past month Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. There are. Security Engineering Access Control Models.
From www.slideserve.com
PPT Access Control PowerPoint Presentation, free download ID9716361 Security Engineering Access Control Models 10k+ visitors in the past month 10k+ visitors in the past month The technical term for this is “access control”. Various access control models provide frameworks for implementing access control policies effectively. Access control is a fundamental component of information security, ensuring that resources are accessed only by authorized. Role based access control (rbac) (also called role based security), as. Security Engineering Access Control Models.
From its-physec.com
Access Control Physical Security Solutions ITS Physec Security Engineering Access Control Models Uncover the secrets of access control models in cybersecurity. There are several traditional and hybrid access control models that have various pros and cons. 10k+ visitors in the past month Role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for. 10k+ visitors in the. Security Engineering Access Control Models.
From protechsecurity.com
commercial access control systems ProTech Security Security Engineering Access Control Models Various access control models provide frameworks for implementing access control policies effectively. Access control is the process of mediating every request to resources and data maintained by a system and determining. Enhance your organization's security with dac, mac, rbac. Uncover the secrets of access control models in cybersecurity. Role based access control (rbac) (also called role based security), as formalized. Security Engineering Access Control Models.