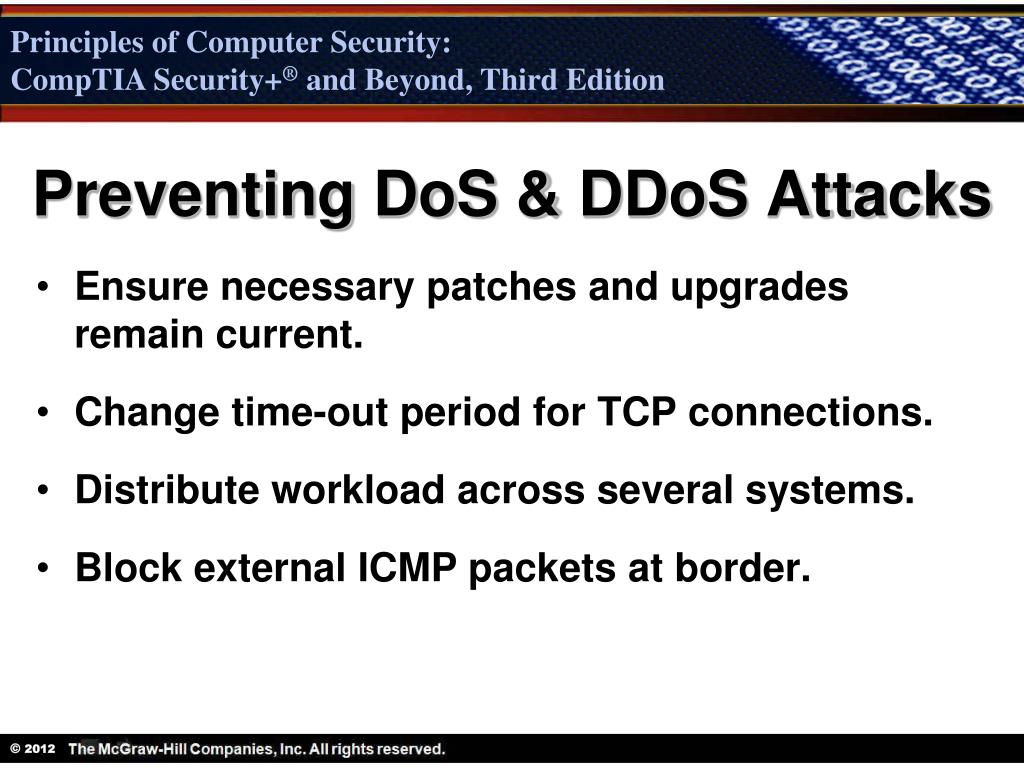
How To Stop Dos Attacks . This cheat sheet provides a methodology, analysis and guidance for designing and. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Read about the realities of ddos attack prevention. How to prevent dos attacks. Learn how to handle dos attacks on different layers of the osi model, from application to network. The following suggestions may help reduce the attack surface of an organization and temper the potential. Techniques like syn flood, teardrop, icmp flood, and. Learn the best ways to stop ddos domain name system amplification attacks.
from www.slideserve.com
Techniques like syn flood, teardrop, icmp flood, and. Learn the best ways to stop ddos domain name system amplification attacks. Read about the realities of ddos attack prevention. Learn how to handle dos attacks on different layers of the osi model, from application to network. How to prevent dos attacks. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. The following suggestions may help reduce the attack surface of an organization and temper the potential. This cheat sheet provides a methodology, analysis and guidance for designing and.
PPT Types of Attacks and Malicious Software PowerPoint Presentation
How To Stop Dos Attacks The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Read about the realities of ddos attack prevention. Learn the best ways to stop ddos domain name system amplification attacks. The following suggestions may help reduce the attack surface of an organization and temper the potential. How to prevent dos attacks. Learn how to handle dos attacks on different layers of the osi model, from application to network. This cheat sheet provides a methodology, analysis and guidance for designing and. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Techniques like syn flood, teardrop, icmp flood, and.
From ppt-online.org
DenialofService Attacks. Chapter 7. Computer Security Principles and How To Stop Dos Attacks This cheat sheet provides a methodology, analysis and guidance for designing and. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Techniques like syn flood, teardrop, icmp flood, and. Learn how to handle dos attacks on different layers of the osi model, from application to network. Learn the. How To Stop Dos Attacks.
From www.infojiniconsulting.com
How to stop DDoS Attacks A Complete Guide How To Stop Dos Attacks Read about the realities of ddos attack prevention. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Learn how to handle dos attacks on different layers of the osi model, from application to network. This cheat sheet provides a methodology, analysis and guidance for designing and. The following. How To Stop Dos Attacks.
From www.speedguide.net
SG How to Stop Denial of Service (DoS) Attacks How To Stop Dos Attacks This cheat sheet provides a methodology, analysis and guidance for designing and. The following suggestions may help reduce the attack surface of an organization and temper the potential. Techniques like syn flood, teardrop, icmp flood, and. Read about the realities of ddos attack prevention. Learn how to handle dos attacks on different layers of the osi model, from application to. How To Stop Dos Attacks.
From fineproxy.org
Ataque DOS Glosario FineProxy How To Stop Dos Attacks The following suggestions may help reduce the attack surface of an organization and temper the potential. Techniques like syn flood, teardrop, icmp flood, and. Learn how to handle dos attacks on different layers of the osi model, from application to network. This cheat sheet provides a methodology, analysis and guidance for designing and. The denial of service (dos) attack is. How To Stop Dos Attacks.
From www.youtube.com
Cybersecurity Detection Lab DOS (Attack vs Defense) Stop DOS attack How To Stop Dos Attacks Learn how to handle dos attacks on different layers of the osi model, from application to network. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. How to prevent dos attacks. Learn the best ways to stop ddos domain name system amplification attacks. The following suggestions may help. How To Stop Dos Attacks.
From www.vrogue.co
What Is Denial Of Service Attack Dos Definition And T vrogue.co How To Stop Dos Attacks Learn how to handle dos attacks on different layers of the osi model, from application to network. Techniques like syn flood, teardrop, icmp flood, and. The following suggestions may help reduce the attack surface of an organization and temper the potential. Read about the realities of ddos attack prevention. How to prevent dos attacks. Learn the best ways to stop. How To Stop Dos Attacks.
From www.a10networks.com
DDoS Attack Prevention and DDoS Protection Best Practices A10 Networks How To Stop Dos Attacks This cheat sheet provides a methodology, analysis and guidance for designing and. Techniques like syn flood, teardrop, icmp flood, and. The following suggestions may help reduce the attack surface of an organization and temper the potential. Learn how to handle dos attacks on different layers of the osi model, from application to network. Learn the best ways to stop ddos. How To Stop Dos Attacks.
From arzhost.com
How To Stop DOS Attack ACK Scan How To Stop Dos Attacks The following suggestions may help reduce the attack surface of an organization and temper the potential. Learn the best ways to stop ddos domain name system amplification attacks. Techniques like syn flood, teardrop, icmp flood, and. How to prevent dos attacks. Read about the realities of ddos attack prevention. Learn how to handle dos attacks on different layers of the. How To Stop Dos Attacks.
From www.youtube.com
How to Stop DOS attack / How to Stop DDOS attack with Blackmirror How To Stop Dos Attacks How to prevent dos attacks. This cheat sheet provides a methodology, analysis and guidance for designing and. Techniques like syn flood, teardrop, icmp flood, and. Read about the realities of ddos attack prevention. Learn how to handle dos attacks on different layers of the osi model, from application to network. Learn the best ways to stop ddos domain name system. How To Stop Dos Attacks.
From www.globalsign.com
What is DDoS Attack and How to Prevent It? How To Stop Dos Attacks Learn the best ways to stop ddos domain name system amplification attacks. Techniques like syn flood, teardrop, icmp flood, and. Read about the realities of ddos attack prevention. How to prevent dos attacks. The following suggestions may help reduce the attack surface of an organization and temper the potential. This cheat sheet provides a methodology, analysis and guidance for designing. How To Stop Dos Attacks.
From www.slideserve.com
PPT Types of Attacks and Malicious Software PowerPoint Presentation How To Stop Dos Attacks This cheat sheet provides a methodology, analysis and guidance for designing and. How to prevent dos attacks. Read about the realities of ddos attack prevention. Learn the best ways to stop ddos domain name system amplification attacks. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Techniques like. How To Stop Dos Attacks.
From theinsightpost.com
Preventing Denial of Service Attacks with Rate Limiting Techniques How To Stop Dos Attacks Techniques like syn flood, teardrop, icmp flood, and. Learn the best ways to stop ddos domain name system amplification attacks. How to prevent dos attacks. This cheat sheet provides a methodology, analysis and guidance for designing and. Learn how to handle dos attacks on different layers of the osi model, from application to network. Read about the realities of ddos. How To Stop Dos Attacks.
From news.nau.edu
Stay vigilant, be diligent How to protect yourself from phishing How To Stop Dos Attacks The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Read about the realities of ddos attack prevention. Learn the best ways to stop ddos domain name system amplification attacks. The following suggestions may help reduce the attack surface of an organization and temper the potential. This cheat sheet. How To Stop Dos Attacks.
From blogs.blackberry.com
DDoS Protection 8 Simple Tactics How To Stop Dos Attacks How to prevent dos attacks. This cheat sheet provides a methodology, analysis and guidance for designing and. Techniques like syn flood, teardrop, icmp flood, and. Read about the realities of ddos attack prevention. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Learn the best ways to stop. How To Stop Dos Attacks.
From rublon.com
10 Top Tips to Prevent Phishing Attacks Rublon How To Stop Dos Attacks Learn the best ways to stop ddos domain name system amplification attacks. This cheat sheet provides a methodology, analysis and guidance for designing and. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. How to prevent dos attacks. Learn how to handle dos attacks on different layers of. How To Stop Dos Attacks.
From www.thesecuritybuddy.com
How to protect servers from DoS and DDoS attacks? The Security Buddy How To Stop Dos Attacks Learn how to handle dos attacks on different layers of the osi model, from application to network. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. This cheat sheet provides a methodology, analysis and guidance for designing and. Learn the best ways to stop ddos domain name system. How To Stop Dos Attacks.
From arzhost.com
How to Stop DOS Attack ACK Scan How To Stop Dos Attacks The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Learn how to handle dos attacks on different layers of the osi model, from application to network. Learn the best ways to stop ddos domain name system amplification attacks. The following suggestions may help reduce the attack surface of. How To Stop Dos Attacks.
From www.veeble.org
5 Simple WordPress Security Issues Everybody Overlooks And How To Avoid How To Stop Dos Attacks Read about the realities of ddos attack prevention. The following suggestions may help reduce the attack surface of an organization and temper the potential. Learn the best ways to stop ddos domain name system amplification attacks. This cheat sheet provides a methodology, analysis and guidance for designing and. Learn how to handle dos attacks on different layers of the osi. How To Stop Dos Attacks.
From www.smartdnsproxy.com
How VPNs Prevent DDOS Attacks How To Stop Dos Attacks Learn how to handle dos attacks on different layers of the osi model, from application to network. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. The following suggestions may help reduce the attack surface of an organization and temper the potential. How to prevent dos attacks. This. How To Stop Dos Attacks.
From ar.inspiredpencil.com
Dos Attack How To Stop Dos Attacks Learn how to handle dos attacks on different layers of the osi model, from application to network. Learn the best ways to stop ddos domain name system amplification attacks. Techniques like syn flood, teardrop, icmp flood, and. This cheat sheet provides a methodology, analysis and guidance for designing and. Read about the realities of ddos attack prevention. How to prevent. How To Stop Dos Attacks.
From arzhost.com
How To Stop DOS Attack ACK Scan How To Stop Dos Attacks Techniques like syn flood, teardrop, icmp flood, and. The following suggestions may help reduce the attack surface of an organization and temper the potential. Learn the best ways to stop ddos domain name system amplification attacks. Read about the realities of ddos attack prevention. This cheat sheet provides a methodology, analysis and guidance for designing and. Learn how to handle. How To Stop Dos Attacks.
From us.norton.com
DDoS attacks A guide + DDoS attack protection tips Norton How To Stop Dos Attacks Learn the best ways to stop ddos domain name system amplification attacks. How to prevent dos attacks. The following suggestions may help reduce the attack surface of an organization and temper the potential. This cheat sheet provides a methodology, analysis and guidance for designing and. Read about the realities of ddos attack prevention. The denial of service (dos) attack is. How To Stop Dos Attacks.
From arzhost.com
[dos attack rst scan] How to Change How To Stop Dos Attacks Techniques like syn flood, teardrop, icmp flood, and. The following suggestions may help reduce the attack surface of an organization and temper the potential. This cheat sheet provides a methodology, analysis and guidance for designing and. Learn how to handle dos attacks on different layers of the osi model, from application to network. Read about the realities of ddos attack. How To Stop Dos Attacks.
From bogner.sh
Analysing a Denial of Service Attack Tool » bogner.sh How To Stop Dos Attacks This cheat sheet provides a methodology, analysis and guidance for designing and. Techniques like syn flood, teardrop, icmp flood, and. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. How to prevent dos attacks. The following suggestions may help reduce the attack surface of an organization and temper. How To Stop Dos Attacks.
From www.pynetlabs.com
Difference Between DoS and DDoS Attack Labs How To Stop Dos Attacks The following suggestions may help reduce the attack surface of an organization and temper the potential. Read about the realities of ddos attack prevention. Learn the best ways to stop ddos domain name system amplification attacks. How to prevent dos attacks. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose. How To Stop Dos Attacks.
From www.covertswarm.com
Denial Of Service (DoS) Attacks A Complete Guide CovertSwarm How To Stop Dos Attacks This cheat sheet provides a methodology, analysis and guidance for designing and. Read about the realities of ddos attack prevention. The following suggestions may help reduce the attack surface of an organization and temper the potential. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Learn how to. How To Stop Dos Attacks.
From www.slideserve.com
PPT CS101 Introduction to Computing Lecture 39 Cyber Crime PowerPoint How To Stop Dos Attacks How to prevent dos attacks. Techniques like syn flood, teardrop, icmp flood, and. Learn the best ways to stop ddos domain name system amplification attacks. This cheat sheet provides a methodology, analysis and guidance for designing and. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Learn how. How To Stop Dos Attacks.
From blog.totalprosource.com
Don't Get Hooked 6 Tips to Avoid Phishing Attacks How To Stop Dos Attacks Techniques like syn flood, teardrop, icmp flood, and. How to prevent dos attacks. Learn how to handle dos attacks on different layers of the osi model, from application to network. This cheat sheet provides a methodology, analysis and guidance for designing and. Read about the realities of ddos attack prevention. The denial of service (dos) attack is focused on making. How To Stop Dos Attacks.
From www.pinterest.com
How To Perform DOS Attacks Video Tutorials Magento, How To Stop Dos Attacks This cheat sheet provides a methodology, analysis and guidance for designing and. Learn the best ways to stop ddos domain name system amplification attacks. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. The following suggestions may help reduce the attack surface of an organization and temper the. How To Stop Dos Attacks.
From www.pinterest.com
Methods to Stop Denial of Service Attacks Ddos attack, Denial of How To Stop Dos Attacks This cheat sheet provides a methodology, analysis and guidance for designing and. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. The following suggestions may help reduce the attack surface of an organization and temper the potential. Read about the realities of ddos attack prevention. Learn the best. How To Stop Dos Attacks.
From www.alamy.com
Stop dos attack icon simple vector. Secured hacker. Secure gesture How To Stop Dos Attacks How to prevent dos attacks. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. The following suggestions may help reduce the attack surface of an organization and temper the potential. Read about the realities of ddos attack prevention. Techniques like syn flood, teardrop, icmp flood, and. Learn how. How To Stop Dos Attacks.
From www.vectorstock.com
Panic attack symptoms and ways to stop Royalty Free Vector How To Stop Dos Attacks Learn the best ways to stop ddos domain name system amplification attacks. Read about the realities of ddos attack prevention. Techniques like syn flood, teardrop, icmp flood, and. The following suggestions may help reduce the attack surface of an organization and temper the potential. This cheat sheet provides a methodology, analysis and guidance for designing and. How to prevent dos. How To Stop Dos Attacks.
From arzhost.com
Stop DOS Attack RST Scan With These Steps How To Stop Dos Attacks The following suggestions may help reduce the attack surface of an organization and temper the potential. Learn how to handle dos attacks on different layers of the osi model, from application to network. Read about the realities of ddos attack prevention. How to prevent dos attacks. This cheat sheet provides a methodology, analysis and guidance for designing and. Techniques like. How To Stop Dos Attacks.
From medium.com
Understanding DDOS Attack kapil sharma Medium How To Stop Dos Attacks The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. How to prevent dos attacks. Learn how to handle dos attacks on different layers of the osi model, from application to network. Techniques like syn flood, teardrop, icmp flood, and. The following suggestions may help reduce the attack surface. How To Stop Dos Attacks.
From www.pandasecurity.com
DDoS Meaning Distributed Denial of Service Panda Security How To Stop Dos Attacks Learn the best ways to stop ddos domain name system amplification attacks. Read about the realities of ddos attack prevention. The following suggestions may help reduce the attack surface of an organization and temper the potential. The denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was. Learn how to. How To Stop Dos Attacks.