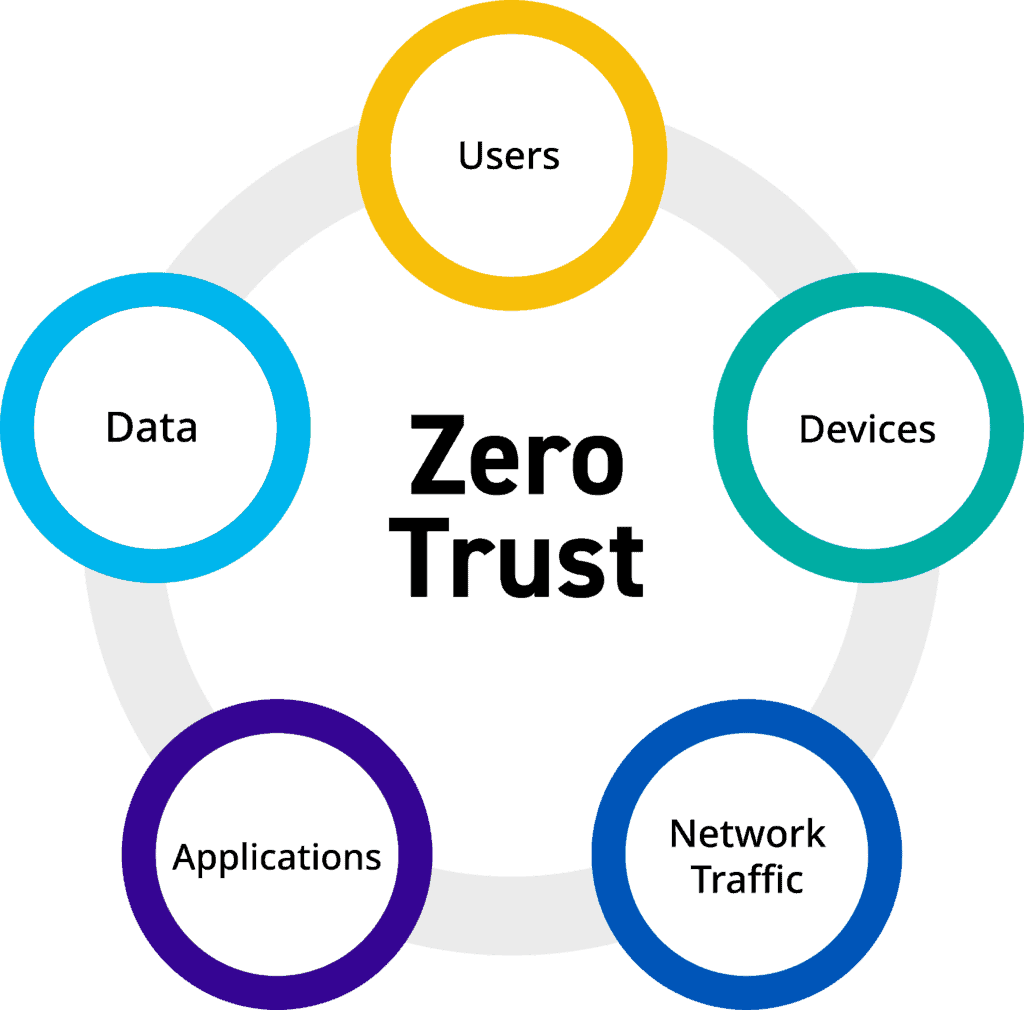
Architecture Zero Trust . A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Zero trust architecture (zta) is a security model based on the principle of least privilege. Instead of focusing on the network perimeter, a zero trust security model. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Least privilege means that users and. Instead of assuming everything behind the corporate. Zero trust is a security strategy for modern multicloud networks. Zero trust is a modern security strategy based on the principle never trust, always verify. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and.
from logrhythm.com
Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Zero trust is a modern security strategy based on the principle never trust, always verify. Instead of focusing on the network perimeter, a zero trust security model. Zero trust architecture (zta) is a security model based on the principle of least privilege. Zero trust is a security strategy for modern multicloud networks. Least privilege means that users and. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Instead of assuming everything behind the corporate.
Embracing a Zero Trust Security Model
Architecture Zero Trust A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Instead of assuming everything behind the corporate. Instead of focusing on the network perimeter, a zero trust security model. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Least privilege means that users and. Zero trust is a modern security strategy based on the principle never trust, always verify. Zero trust architecture (zta) is a security model based on the principle of least privilege. Zero trust is a security strategy for modern multicloud networks.
From oversitesentry.com
Is Zero Trust Architecture the Method of Future Cybersecurity Architecture Zero Trust Least privilege means that users and. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Instead of focusing on the network perimeter, a zero trust security model. Zero trust architecture (zta) is a security model based on the principle of least privilege. Zero trust is a modern security strategy based. Architecture Zero Trust.
From anchormydata.com
Zero Trust Architecture Framework for Modern Enterprise Architecture Zero Trust A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Zero trust is a security strategy for modern multicloud networks. Learn how zero trust architecture can help. Architecture Zero Trust.
From
Architecture Zero Trust Instead of focusing on the network perimeter, a zero trust security model. Zero trust is a security strategy for modern multicloud networks. Least privilege means that users and. Zero trust is a modern security strategy based on the principle never trust, always verify. Zero trust architecture (zta) is a security model based on the principle of least privilege. A zero. Architecture Zero Trust.
From pixelplex.io
How to Implement Zero Trust Architecture in 5 Steps [Checklist] Architecture Zero Trust Zero trust is a modern security strategy based on the principle never trust, always verify. Instead of assuming everything behind the corporate. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Least privilege means that users and. A zero trust architecture (zta) is an enterprise cybersecurity architecture that. Architecture Zero Trust.
From
Architecture Zero Trust Zero trust is a security strategy for modern multicloud networks. Zero trust is a modern security strategy based on the principle never trust, always verify. Instead of focusing on the network perimeter, a zero trust security model. Least privilege means that users and. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles. Architecture Zero Trust.
From www.nextlabs.com
Zero Trust Architecture (ZTA) NextLabs Architecture Zero Trust Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Zero trust is a security strategy for modern multicloud networks. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Instead of assuming everything behind the corporate. A zero. Architecture Zero Trust.
From www.zubairalexander.com
Zero Trust Security Model Alexander's Blog Architecture Zero Trust Zero trust is a security strategy for modern multicloud networks. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Zero trust architecture (zta) is a security model based on. Architecture Zero Trust.
From
Architecture Zero Trust Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Zero trust architecture (zta) is a security model based on the principle of least privilege. Least privilege means that users and. Instead of assuming everything behind the corporate. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based. Architecture Zero Trust.
From
Architecture Zero Trust Least privilege means that users and. Zero trust is a modern security strategy based on the principle never trust, always verify. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Zero trust architecture (zta) is a security model based on the principle of least privilege. Instead of. Architecture Zero Trust.
From
Architecture Zero Trust A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Instead of assuming everything behind the corporate. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Least privilege means that users and. Learn how zero trust. Architecture Zero Trust.
From www.redpiranha.net
Implement Zero Trust Architecture Framework Red Piranha Architecture Zero Trust Zero trust is a modern security strategy based on the principle never trust, always verify. Least privilege means that users and. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Instead of assuming everything behind the corporate. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based. Architecture Zero Trust.
From rhisac.org
RHISAC ZeroTrust Architecture (ZTA) How to Get Started Architecture Zero Trust Instead of assuming everything behind the corporate. Zero trust is a security strategy for modern multicloud networks. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Zero trust is a modern security strategy based on the principle never trust, always verify. Zero trust architecture (zta) is a security model based. Architecture Zero Trust.
From
Architecture Zero Trust Instead of focusing on the network perimeter, a zero trust security model. Zero trust is a security strategy for modern multicloud networks. Zero trust architecture (zta) is a security model based on the principle of least privilege. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Learn how. Architecture Zero Trust.
From
Architecture Zero Trust A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Zero trust is a security strategy for modern multicloud networks. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Instead of focusing on the network perimeter, a zero trust. Architecture Zero Trust.
From
Architecture Zero Trust Zero trust is a security strategy for modern multicloud networks. Instead of assuming everything behind the corporate. Zero trust architecture (zta) is a security model based on the principle of least privilege. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Instead of focusing on the network perimeter, a zero. Architecture Zero Trust.
From
Architecture Zero Trust Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Zero trust is a modern security strategy based on the principle never trust, always verify. Zero trust architecture (zta) is a security model based on the principle of least privilege. A zero trust architecture (zta) is an enterprise cybersecurity architecture that. Architecture Zero Trust.
From
Architecture Zero Trust Zero trust is a security strategy for modern multicloud networks. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Instead of focusing on the network perimeter, a zero trust security model. Zero trust architecture (zta) is a security model based on the principle of least privilege. Least privilege means that. Architecture Zero Trust.
From www.linkedin.com
Embracing Zero Trust Architecture Safeguarding Cybersecurity in the Architecture Zero Trust Zero trust architecture (zta) is a security model based on the principle of least privilege. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Zero trust is a security strategy for modern multicloud networks. Learn how zero trust architecture can help protect your organization’s resources and support remote. Architecture Zero Trust.
From mavink.com
Microsoft Zero Trust Architecture Diagram Architecture Zero Trust Zero trust architecture (zta) is a security model based on the principle of least privilege. Instead of focusing on the network perimeter, a zero trust security model. Zero trust is a modern security strategy based on the principle never trust, always verify. Least privilege means that users and. Learn how zero trust architecture can help protect your organization’s resources and. Architecture Zero Trust.
From
Architecture Zero Trust A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Zero trust is a modern security strategy based on the principle never trust, always verify. Zero trust is a security strategy for modern multicloud networks. Instead of focusing on the network perimeter, a zero trust security model. Learn how. Architecture Zero Trust.
From
Architecture Zero Trust Least privilege means that users and. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Zero trust is a modern security strategy based on the principle never trust, always verify. Zero trust architecture (zta) is a security model based on the principle of least privilege. Instead of focusing on the. Architecture Zero Trust.
From
Architecture Zero Trust Least privilege means that users and. Zero trust is a security strategy for modern multicloud networks. Instead of focusing on the network perimeter, a zero trust security model. Zero trust is a modern security strategy based on the principle never trust, always verify. Instead of assuming everything behind the corporate. Zero trust architecture (zta) is a security model based on. Architecture Zero Trust.
From www.tpsearchtool.com
Zero Trust Architecture Understanding The Nist Framework Of Zero Trust Architecture Zero Trust Zero trust is a security strategy for modern multicloud networks. Instead of assuming everything behind the corporate. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Instead of focusing on the network perimeter, a zero trust security model. Least privilege means that users and. A zero trust. Architecture Zero Trust.
From
Architecture Zero Trust Instead of focusing on the network perimeter, a zero trust security model. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Zero trust architecture (zta) is a security model based on the principle of least privilege. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on. Architecture Zero Trust.
From
Architecture Zero Trust Instead of assuming everything behind the corporate. Zero trust architecture (zta) is a security model based on the principle of least privilege. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Least privilege means that users and. Zero trust is a modern security strategy based on the principle never trust,. Architecture Zero Trust.
From bleuwire.com
How to Implement the ZeroTrust Architecture Bleuwire Architecture Zero Trust Zero trust is a security strategy for modern multicloud networks. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. Instead of assuming everything behind the corporate. Zero trust architecture (zta) is a security model based on the principle of least privilege. Zero trust is a modern security strategy based on. Architecture Zero Trust.
From www.cisco.com
Solutions Zero Trust Frameworks Architecture Guide Cisco Architecture Zero Trust Zero trust architecture (zta) is a security model based on the principle of least privilege. Zero trust is a modern security strategy based on the principle never trust, always verify. Instead of focusing on the network perimeter, a zero trust security model. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and. Architecture Zero Trust.
From
Architecture Zero Trust Instead of focusing on the network perimeter, a zero trust security model. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Zero trust is a modern. Architecture Zero Trust.
From
Architecture Zero Trust Least privilege means that users and. Zero trust is a modern security strategy based on the principle never trust, always verify. Instead of focusing on the network perimeter, a zero trust security model. A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Zero trust architecture (zta) is a. Architecture Zero Trust.
From
Architecture Zero Trust A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Zero trust is a security strategy for modern multicloud networks. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Instead of assuming everything behind the corporate.. Architecture Zero Trust.
From ardalyst.com
AllThreat™ (Zero Trust) Architecture Ardalyst Architecture Zero Trust A zero trust architecture is a structure based on the cybersecurity principle that all users must be continuously authenticated, authorized, and. Zero trust is a security strategy for modern multicloud networks. Least privilege means that users and. Zero trust architecture (zta) is a security model based on the principle of least privilege. Instead of assuming everything behind the corporate. A. Architecture Zero Trust.
From
Architecture Zero Trust Least privilege means that users and. Learn how zero trust architecture can help protect your organization’s resources and support remote work through authentication, encryption, and. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. A zero trust architecture is a structure based on the cybersecurity principle that. Architecture Zero Trust.
From
Architecture Zero Trust Least privilege means that users and. Zero trust architecture (zta) is a security model based on the principle of least privilege. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Zero trust is a modern security strategy based on the principle never trust, always verify. A zero. Architecture Zero Trust.
From
Architecture Zero Trust Least privilege means that users and. Instead of assuming everything behind the corporate. A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Zero trust is a security strategy for modern multicloud networks. Instead of focusing on the network perimeter, a zero trust security model. Learn how zero. Architecture Zero Trust.
From
Architecture Zero Trust A zero trust architecture (zta) is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data. Zero trust is a security strategy for modern multicloud networks. Zero trust is a modern security strategy based on the principle never trust, always verify. Least privilege means that users and. Learn how zero trust architecture can help. Architecture Zero Trust.