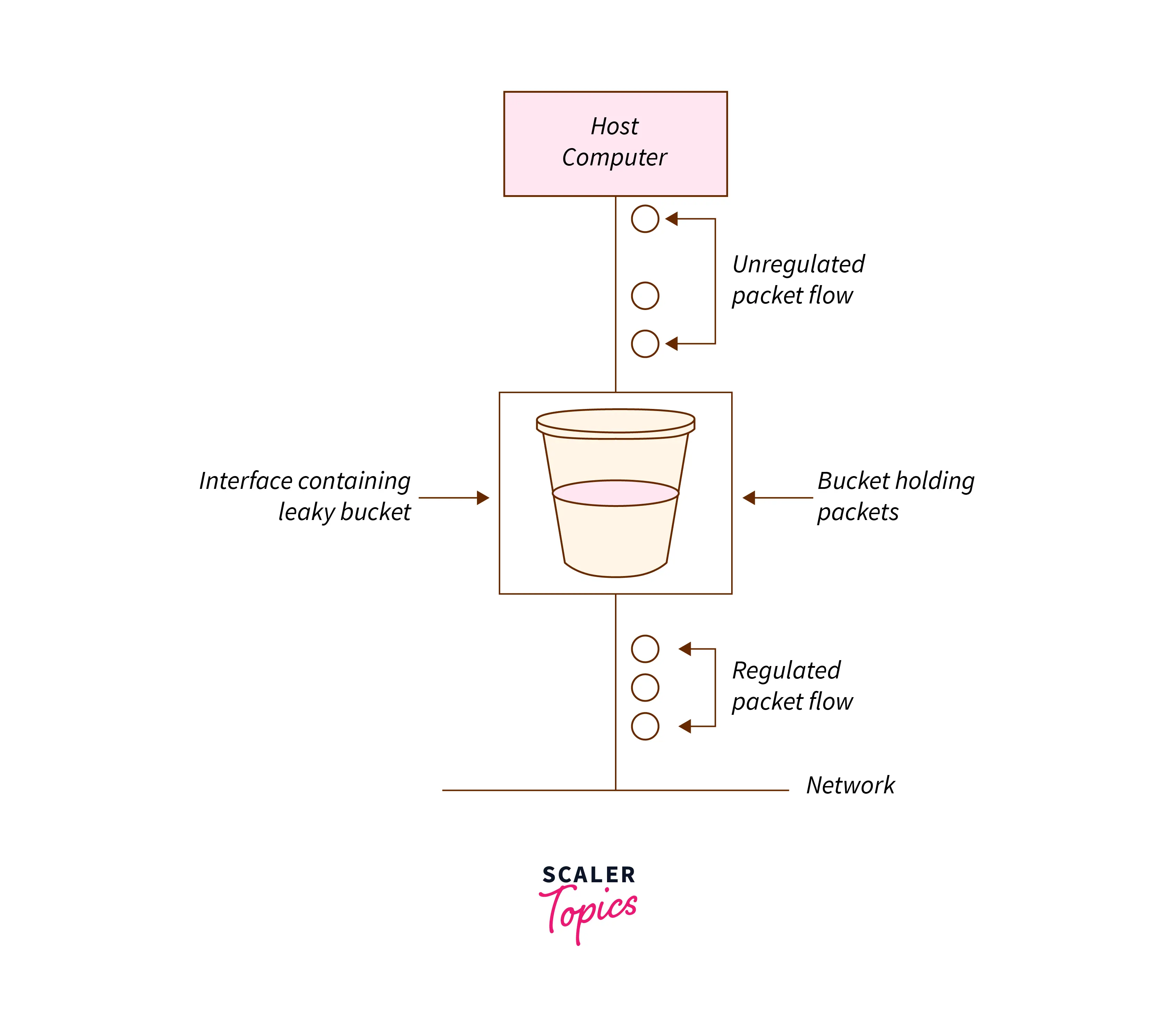
Leaky Bucket Algorithm Router . One can do very clever things. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic.
from www.scaler.com
the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket algorithm is implemented in the host operating system. One can do very clever things.
Leaky Bucket Algorithm Scalar Topics
Leaky Bucket Algorithm Router the leaky bucket algorithm is implemented in the host operating system. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. One can do very clever things. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate.
From www.youtube.com
Mastering the Leaky Bucket Algorithm A StepbyStep Guide? algorithm Leaky Bucket Algorithm Router the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. One can do very clever things. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. in class, we introduced. Leaky Bucket Algorithm Router.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Router the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket rate limiting algorithm. Leaky Bucket Algorithm Router.
From www.youtube.com
leaky bucket algorithm traffic shaping in computer networks 2021 Leaky Bucket Algorithm Router the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. One can do very clever things. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first. Leaky Bucket Algorithm Router.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Router the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket rate limiting algorithm utilizes a fifo (first in,. Leaky Bucket Algorithm Router.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Leaky Bucket Algorithm Router It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. One can do very clever things. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket is a traffic shaping algorithm used to control the flow of data in. Leaky Bucket Algorithm Router.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5856654 Leaky Bucket Algorithm Router the leaky bucket algorithm is implemented in the host operating system. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket. Leaky Bucket Algorithm Router.
From www.researchgate.net
Algorithm to Implement the Leaky Bucket and the Token Bucket Download Leaky Bucket Algorithm Router the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. One can do very clever things. the leaky bucket algorithm is implemented in the host operating system. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. in. Leaky Bucket Algorithm Router.
From www.linqz.io
Leaky/Token bucket algorithm for flow control Learn INQuiZitively Leaky Bucket Algorithm Router the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is implemented in the host operating system. One can do very clever things. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed. Leaky Bucket Algorithm Router.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm Router in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky. Leaky Bucket Algorithm Router.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Router It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket rate limiting algorithm utilizes a fifo (first. Leaky Bucket Algorithm Router.
From hxewrcjkt.blob.core.windows.net
Leaky Bucket Algorithm In C at Judy Thorpe blog Leaky Bucket Algorithm Router the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular. Leaky Bucket Algorithm Router.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID1753059 Leaky Bucket Algorithm Router the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular. Leaky Bucket Algorithm Router.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm Router the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. in class, we introduced the leaky bucket as a way to police. Leaky Bucket Algorithm Router.
From www.techtarget.com
What is the leaky bucket algorithm? TechTarget Definition Leaky Bucket Algorithm Router the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently.. Leaky Bucket Algorithm Router.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Router in class, we introduced the leaky bucket as a way to police the transmission rate of a session. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. One can do very clever things. the leaky bucket is a traffic shaping algorithm used. Leaky Bucket Algorithm Router.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Router the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. One. Leaky Bucket Algorithm Router.
From www.slideserve.com
PPT Chapter 10 Routing Algorithm , Congestion , QOS PowerPoint Leaky Bucket Algorithm Router It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. in class, we introduced the leaky bucket as a way. Leaky Bucket Algorithm Router.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5320728 Leaky Bucket Algorithm Router the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. One can do very clever things. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. It makes bursty traffic, smooth by storing the data packets temporarily and. Leaky Bucket Algorithm Router.
From www.geeksforgeeks.org
Leaky Bucket Algorithm Computer Networks Leaky Bucket Algorithm Router the leaky bucket algorithm is implemented in the host operating system. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket is a traffic shaping algorithm used to control the flow of data. Leaky Bucket Algorithm Router.
From www.youtube.com
Leaky bucket algorithm in congestion control algorithm YouTube Leaky Bucket Algorithm Router the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket rate limiting algorithm. Leaky Bucket Algorithm Router.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky Bucket Algorithm Router in class, we introduced the leaky bucket as a way to police the transmission rate of a session. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. . Leaky Bucket Algorithm Router.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket Algorithm Router in class, we introduced the leaky bucket as a way to police the transmission rate of a session. One can do very clever things. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket algorithm is often implemented. Leaky Bucket Algorithm Router.
From www.researchgate.net
Algorithm to Implement the Leaky Bucket and the Token Bucket Download Leaky Bucket Algorithm Router the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. One can do very clever things. the leaky bucket algorithm is. Leaky Bucket Algorithm Router.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Router the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky. Leaky Bucket Algorithm Router.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket Algorithm Router It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. in class, we introduced the leaky bucket as a way to. Leaky Bucket Algorithm Router.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Router One can do very clever things. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. It makes bursty traffic, smooth by storing the data packets temporarily and. Leaky Bucket Algorithm Router.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm Router the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket is a traffic shaping algorithm used. Leaky Bucket Algorithm Router.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm Router the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. One can do very clever things. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket rate limiting algorithm utilizes a fifo. Leaky Bucket Algorithm Router.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Router the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak. Leaky Bucket Algorithm Router.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Router One can do very clever things. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon. Leaky Bucket Algorithm Router.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm Router the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is implemented in the host operating system. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket rate. Leaky Bucket Algorithm Router.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Router One can do very clever things. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket rate. Leaky Bucket Algorithm Router.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Router the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the. Leaky Bucket Algorithm Router.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation ID3653615 Leaky Bucket Algorithm Router One can do very clever things. the leaky bucket algorithm is implemented in the host operating system. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. . Leaky Bucket Algorithm Router.
From www.semanticscholar.org
Figure 2 from Dimensioning and performance evaluation of an efficient Leaky Bucket Algorithm Router the leaky bucket algorithm is often implemented in routers and switches to manage outgoing traffic efficiently. It makes bursty traffic, smooth by storing the data packets temporarily and sending them into the network at regular intervals, depending upon the leak rate. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. in class,. Leaky Bucket Algorithm Router.