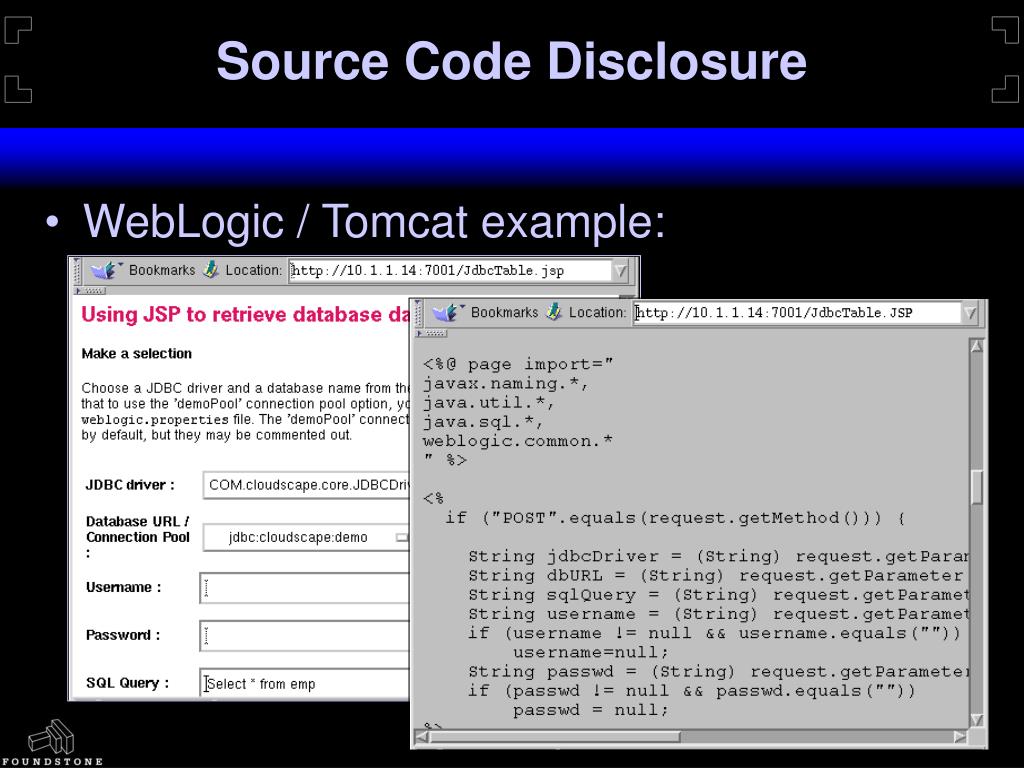
Server-Based Source Code Disclosures . One or more pages disclosing source code were found. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. Hinting at the existence or absence. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. when source code disclosure happens, sensitive or proprietary information contained within the source code.
from www.slideserve.com
this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. Hinting at the existence or absence. One or more pages disclosing source code were found. when source code disclosure happens, sensitive or proprietary information contained within the source code. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own.
PPT OneWay Hacking Futility of Firewalls in Hacking PowerPoint
Server-Based Source Code Disclosures in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. One or more pages disclosing source code were found. Hinting at the existence or absence. when source code disclosure happens, sensitive or proprietary information contained within the source code. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks.
From www.oracle.com
Installing and Configuring Disclosure Management 11.1.2 Server-Based Source Code Disclosures when source code disclosure happens, sensitive or proprietary information contained within the source code. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. . Server-Based Source Code Disclosures.
From appcheck-ng.com
Server Information Disclosure AppCheck Server-Based Source Code Disclosures in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. One or more pages disclosing source code were found. Hinting at the existence or absence. when source code disclosure. Server-Based Source Code Disclosures.
From jacobriggs.io
Source code disclosure via exposed .git Jacob Riggs Blog Server-Based Source Code Disclosures Hinting at the existence or absence. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. One or more pages disclosing source code were found. when source code disclosure happens, sensitive or proprietary information contained within the source code. with source code disclosure an attacker can use the information. Server-Based Source Code Disclosures.
From www.youtube.com
Source code disclosure via backup files (Video Solution) 2020 2021 Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. when source code disclosure happens, sensitive or proprietary information contained within the source code. with source code disclosure. Server-Based Source Code Disclosures.
From domiee13.github.io
Information Disclosure Labs Domiee13 Server-Based Source Code Disclosures in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. One or more pages disclosing source code were found. when source code disclosure happens, sensitive or proprietary information contained within the source code. with source code disclosure an attacker can use the information to discover logical flaws. Server-Based Source Code Disclosures.
From appcheck-ng.com
Server Information Disclosure AppCheck Server-Based Source Code Disclosures One or more pages disclosing source code were found. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. Hinting at the existence or absence. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. . Server-Based Source Code Disclosures.
From blog.projectdiscovery.io
PHP Development Server Server-Based Source Code Disclosures when source code disclosure happens, sensitive or proprietary information contained within the source code. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. Hinting at the. Server-Based Source Code Disclosures.
From anilcy.blogspot.com
Directory Traversal and Source code disclosure vulnerability Server-Based Source Code Disclosures in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. when source code disclosure happens, sensitive or proprietary information contained within the source code. One or more pages disclosing source code were found. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for. Server-Based Source Code Disclosures.
From appcheck-ng.com
Server Information Disclosure AppCheck Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. Hinting at the existence or absence. One or more pages disclosing source code were found. when source code disclosure happens, sensitive or proprietary information contained within the source code. this cheat sheet is intended to. Server-Based Source Code Disclosures.
From www.youtube.com
Source Code Disclosure vulnerability 2022 YouTube Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. Hinting at the existence or absence. with source code disclosure an attacker can use the information to discover logical. Server-Based Source Code Disclosures.
From www.youtube.com
Hack PHP CLI Builtin Server Source code disclosure YouTube Server-Based Source Code Disclosures One or more pages disclosing source code were found. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. when source code disclosure happens, sensitive or proprietary information contained within the source code. with source code disclosure an attacker can use the information to discover logical flaws. Server-Based Source Code Disclosures.
From slidetodoc.com
Revealing the Secrets Source Code Disclosure Techniques and Server-Based Source Code Disclosures Hinting at the existence or absence. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. One or more pages disclosing source code were found. in this. Server-Based Source Code Disclosures.
From appcheck-ng.com
Server Information Disclosure AppCheck Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. Hinting at the existence or absence. when source code disclosure happens, sensitive or proprietary information contained within the source code. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both. Server-Based Source Code Disclosures.
From chawdamrunal.medium.com
Source Code Disclosure. Source code often contains some form of… by Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. One or more pages disclosing source code were found. Hinting at the existence or absence. when source. Server-Based Source Code Disclosures.
From github.com
GitHub finbarcrago/cgiemailexploit Cgiemail Source Code Server-Based Source Code Disclosures Hinting at the existence or absence. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. with source code disclosure an attacker can use the information to discover logical. Server-Based Source Code Disclosures.
From appcheck-ng.com
Server Information Disclosure AppCheck Server-Based Source Code Disclosures Hinting at the existence or absence. One or more pages disclosing source code were found. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. when source. Server-Based Source Code Disclosures.
From kaniehuest.github.io
PortSwigger Source code disclosure via backup files (sin Burpsuite). Server-Based Source Code Disclosures One or more pages disclosing source code were found. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. with source code disclosure an attacker can use the information. Server-Based Source Code Disclosures.
From infinitelogins.com
Apps 101 Information Disclosure Vulnerabilities and PortSwigger Lab Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. when source code disclosure happens, sensitive or proprietary information contained within the source code. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. in this. Server-Based Source Code Disclosures.
From monovm.com
What is client server model? A Comprehensive Overview Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. when source code disclosure happens, sensitive or proprietary information contained within the source code. in this. Server-Based Source Code Disclosures.
From infosecwriteups.com
How I found 40+ Directory Listing Vulnerabilities of Source Code Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. One or more pages disclosing source code were found. Hinting at the existence or absence. . Server-Based Source Code Disclosures.
From anilcy.blogspot.com
Directory Traversal and Source code disclosure vulnerability Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. One or more pages disclosing source code were found. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. when source code disclosure happens, sensitive or proprietary information contained. Server-Based Source Code Disclosures.
From www.slideserve.com
PPT OneWay Hacking Futility of Firewalls in Hacking PowerPoint Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. Hinting at the existence or absence. One or more pages disclosing source code were found. when source code disclosure happens, sensitive or proprietary information contained within the source code. in this case, you can study. Server-Based Source Code Disclosures.
From appcheck-ng.com
Server Information Disclosure AppCheck Server-Based Source Code Disclosures Hinting at the existence or absence. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. when source code disclosure happens, sensitive or proprietary information contained within the source code. One or more pages disclosing source code were found. with source code disclosure an attacker can use. Server-Based Source Code Disclosures.
From www.percona.com
PostgreSQL Database Security External ServerBased Authentication Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. One or more pages disclosing source code were found. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. this cheat sheet is intended to. Server-Based Source Code Disclosures.
From blog.projectdiscovery.io
PHP Development Server Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. One or more pages disclosing source code were found. when source code disclosure happens, sensitive or proprietary. Server-Based Source Code Disclosures.
From www.aparat.com
Eclipse Help Server Source Code Disclosure Server-Based Source Code Disclosures in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. when source code disclosure happens, sensitive or proprietary information contained within the source code. Hinting at the existence or absence. One or more pages disclosing source code were found. with source code disclosure an attacker can use. Server-Based Source Code Disclosures.
From www.slideserve.com
PPT OneWay Hacking Futility of Firewalls in Hacking PowerPoint Server-Based Source Code Disclosures when source code disclosure happens, sensitive or proprietary information contained within the source code. Hinting at the existence or absence. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers. Server-Based Source Code Disclosures.
From www.slideserve.com
PPT Revealing the Secrets Source Code Disclosure, Techniques, and Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. Hinting at the existence or absence. when source code disclosure happens, sensitive or proprietary information contained within the source code. One or more pages disclosing source code were found. in this case, you can study. Server-Based Source Code Disclosures.
From threatmon.io
What is Server Header Information Disclosure? ThreatMon Blog Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. One or more pages disclosing source code were found. Hinting at the existence or absence. in this. Server-Based Source Code Disclosures.
From threatmon.io
What is Server Header Information Disclosure? ThreatMon Blog Server-Based Source Code Disclosures when source code disclosure happens, sensitive or proprietary information contained within the source code. this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. Hinting at the. Server-Based Source Code Disclosures.
From slidetodoc.com
Revealing the Secrets Source Code Disclosure Techniques and Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. One or more pages disclosing source code were found. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. with source code disclosure an attacker can use the information. Server-Based Source Code Disclosures.
From noorhomaid.medium.com
Apache HTTP Server /serverstatus information disclosure by Server-Based Source Code Disclosures with source code disclosure an attacker can use the information to discover logical flaws and escalate into a subsequent chain of attacks. when source code disclosure happens, sensitive or proprietary information contained within the source code. Hinting at the existence or absence. in this case, you can study the publicly available source code, which is an invaluable. Server-Based Source Code Disclosures.
From www.invicti.com
XMLRPC Protocol and IP Disclosure Attacks Invicti Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. Hinting at the existence or absence. One or more pages disclosing source code were found. with source code disclosure. Server-Based Source Code Disclosures.
From appcheck-ng.com
Server Information Disclosure Server-Based Source Code Disclosures when source code disclosure happens, sensitive or proprietary information contained within the source code. One or more pages disclosing source code were found. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. with source code disclosure an attacker can use the information to discover logical flaws. Server-Based Source Code Disclosures.
From www.slideserve.com
PPT Revealing the Secrets Source Code Disclosure, Techniques, and Server-Based Source Code Disclosures this cheat sheet is intended to provide guidance on the vulnerability disclosure process for both security researchers and. in this case, you can study the publicly available source code, which is an invaluable resource for constructing your own. Hinting at the existence or absence. with source code disclosure an attacker can use the information to discover logical. Server-Based Source Code Disclosures.