Power Bi Security Model . “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Learn two possible ways to implement the access control Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By the end of this module, you’ll be.
from radacad.com
By the end of this module, you’ll be. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Learn two possible ways to implement the access control “who sees what in the report?” is one of the key security questions in power bi.
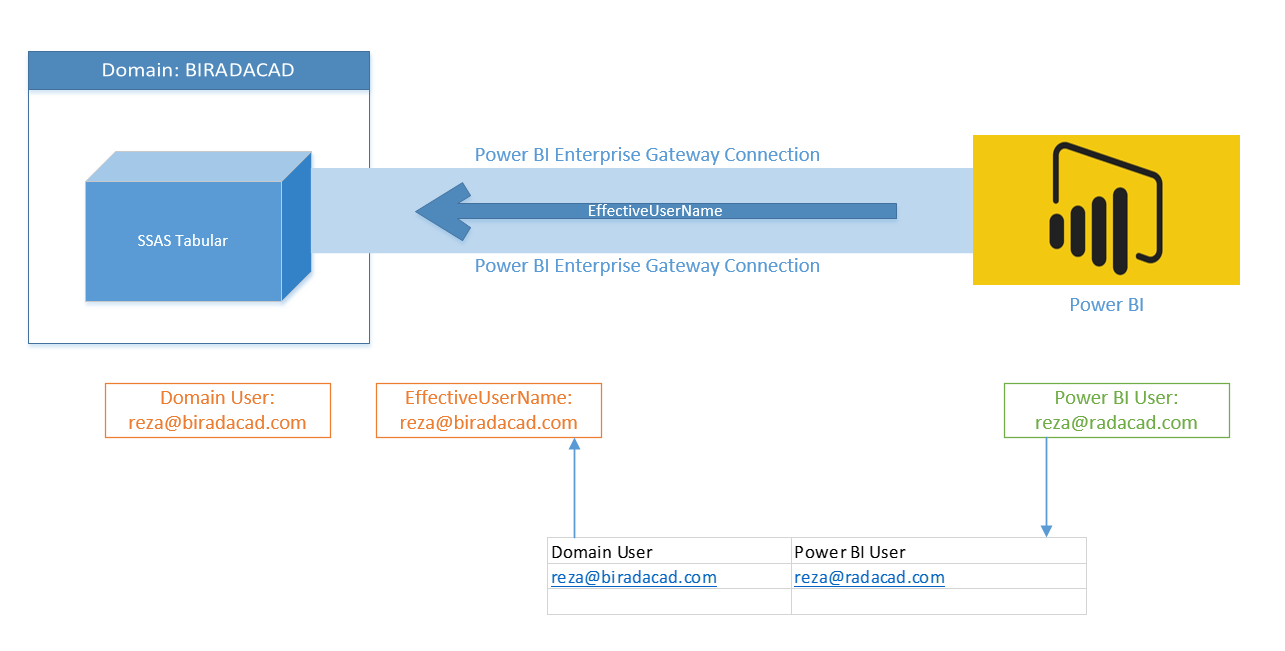
Row Level Security with SSAS Tabular Live Connection in Power BI RADACAD
Power Bi Security Model By the end of this module, you’ll be. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what in the report?” is one of the key security questions in power bi. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Learn two possible ways to implement the access control By the end of this module, you’ll be.
From success.planview.com
Power BI Security Setup Planview Customer Success Center Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Learn two possible ways to implement the access control While the power bi security white paper focuses on key technical topics such as authentication, data. Power Bi Security Model.
From medium.com
Dynamic Row Level Security with Organizational Hierarchy in PowerBI Power Bi Security Model By the end of this module, you’ll be. Learn two possible ways to implement the access control “who sees what in the report?” is one of the key security questions in power bi. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. While the power bi security white paper focuses. Power Bi Security Model.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Security Model Learn two possible ways to implement the access control By the end of this module, you’ll be. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses. Power Bi Security Model.
From www.youtube.com
Power BI Security Best Practices YouTube Power Bi Security Model By the end of this module, you’ll be. “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Learn two possible ways to implement the. Power Bi Security Model.
From powerbiconsulting.com
Row Level Security in Power BI Setup & Importance Power Bi Security Model Learn two possible ways to implement the access control “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. By the end of this module,. Power Bi Security Model.
From qmetrix.com.au
Power BI Architecture And Security What You Need To Know Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Learn two possible ways to implement the access control By the end of this module, you’ll be. While the power bi security white paper focuses. Power Bi Security Model.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Security Model Learn two possible ways to implement the access control Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what. Power Bi Security Model.
From www.journeyteam.com
9 Power BI Security Best Practices Power Bi Security Model Learn two possible ways to implement the access control Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. “who sees what in the report?” is one of the key security questions in power bi. By the end of this module, you’ll be. While the power bi security white paper focuses. Power Bi Security Model.
From www.youtube.com
Power BI Security architecture Power BI Adoption Framework YouTube Power Bi Security Model By the end of this module, you’ll be. Learn two possible ways to implement the access control While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what in the report?” is one of the key security questions in. Power Bi Security Model.
From learn.microsoft.com
Power BI Security Power BI Microsoft Learn Power Bi Security Model Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the. Power Bi Security Model.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Security Model While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Learn two possible ways to implement the access control “who sees what in the report?” is one of the key security questions in power bi. By the end of this module,. Power Bi Security Model.
From yodalearning.com
Power BI Architecture A Ultimate Guide on Power BI Security & BI Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. By the end of this module, you’ll be. Identify and analyze risky behavior patterns with. Power Bi Security Model.
From skypointcloud.com
How Do We Improve Power BI Security? SkyPoint Cloud Power Bi Security Model While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what in the report?” is one of the key security questions in power bi. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft. Power Bi Security Model.
From www.biconnector.com
Power BI Row Level Security RLS Setup Stepbystep guide Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft. Power Bi Security Model.
From k21academy.com
Data Security in Power BI How to Implement and Configure Power Bi Security Model By the end of this module, you’ll be. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Learn two possible ways. Power Bi Security Model.
From www.loginworks.com
How to implement RLS security with Filters in Power BI? Power Bi Security Model Learn two possible ways to implement the access control By the end of this module, you’ll be. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what in the report?” is one of the key security questions in. Power Bi Security Model.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Security Model Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By the end of this module, you’ll be. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Learn two possible ways. Power Bi Security Model.
From learn.microsoft.com
Notas del producto sobre la seguridad de Power BI Power BI Power Bi Security Model While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. By the end of this module, you’ll be. “who sees what in the report?” is one of the key security questions in power bi. Learn two possible ways to implement the. Power Bi Security Model.
From radacad.com
Row Level Security with SSAS Tabular Live Connection in Power BI RADACAD Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. By the end of this module, you’ll be. Learn two possible ways to implement the access control Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. While the power bi security white paper focuses. Power Bi Security Model.
From k21academy.com
Data Security in Power BI How to Implement and Configure Power Bi Security Model Learn two possible ways to implement the access control Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what. Power Bi Security Model.
From dbakevlar.com
Securing Data in Power BI an Interactive Diagram DBAKevlar Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By the end of this module, you’ll be. While the power bi security white paper focuses on key technical topics such as authentication, data residency,. Power Bi Security Model.
From www.dtonomy.com
Create Power BI Reporting for CrowdStrike AIDriven Security Operations Power Bi Security Model While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what in the report?” is one of the key security questions in power bi. By the end of this module, you’ll be. Learn two possible ways to implement the. Power Bi Security Model.
From www.youtube.com
Power BI Security YouTube Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. By the end of this module, you’ll be. Learn two possible ways to implement the. Power Bi Security Model.
From www.excelmojo.com
Power BI Security How to Create RowLevel Security? Power Bi Security Model By the end of this module, you’ll be. Learn two possible ways to implement the access control While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what in the report?” is one of the key security questions in. Power Bi Security Model.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Security Model While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Learn two possible ways to implement the access control By the end of this module, you’ll be. “who sees what in the report?” is one of the key security questions in. Power Bi Security Model.
From dataviz.boutique
Hybrid BI Power BI als Enterprise Reporting Tool Power Bi Security Model While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Learn two possible ways to implement the access control “who sees what. Power Bi Security Model.
From data-flair.training
Power BI Security What is Dynamic RowLevel Security DataFlair Power Bi Security Model By the end of this module, you’ll be. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Learn two possible ways. Power Bi Security Model.
From www.pk-anexcelexpert.com
Static and Dynamic Row Level Security in Power BI PK An Excel Expert Power Bi Security Model While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. “who sees what in the report?” is one of the key security questions in power bi. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft. Power Bi Security Model.
From alphabold.com
Power BI Security Roles Microsoft Dynamics Partner and CRM Consultant Power Bi Security Model Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. “who sees what in the report?” is one of the key security questions in power bi. By the end of this module, you’ll be. While the power bi security white paper focuses on key technical topics such as authentication, data residency,. Power Bi Security Model.
From www.vrogue.co
Dynamic Row Level Security With Power Bi Made Simple vrogue.co Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Learn two possible ways to implement the access control While the power bi security white paper focuses on key technical topics such as authentication, data. Power Bi Security Model.
From www.sqlcircuit.com
SQLCircuit Power BI Security Model Power Bi Security Model Learn two possible ways to implement the access control By the end of this module, you’ll be. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the. Power Bi Security Model.
From www.sqlchick.com
Groups in Power BI How Sharing and Security Works — SQL Chick Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. Learn two possible ways to implement the access control While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Identify and analyze risky behavior patterns. Power Bi Security Model.
From o365.vn
How to visualise security and threat information in Microsoft Power BI Power Bi Security Model Learn two possible ways to implement the access control By the end of this module, you’ll be. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. “who sees what in the report?” is one of the key security questions in power bi. While the power bi security white paper focuses. Power Bi Security Model.
From www.vrogue.co
Implementing Security In Power Bi Workspaces Using Us vrogue.co Power Bi Security Model Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. “who sees what in the report?” is one of the key security questions in power bi. By the end of this module, you’ll be. While the power bi security white paper focuses on key technical topics such as authentication, data residency,. Power Bi Security Model.
From www.ilink-digital.com
Microsoft Power BI Security 6 Best Practices iLink Digital Power Bi Security Model “who sees what in the report?” is one of the key security questions in power bi. By the end of this module, you’ll be. Learn two possible ways to implement the access control Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. While the power bi security white paper focuses. Power Bi Security Model.