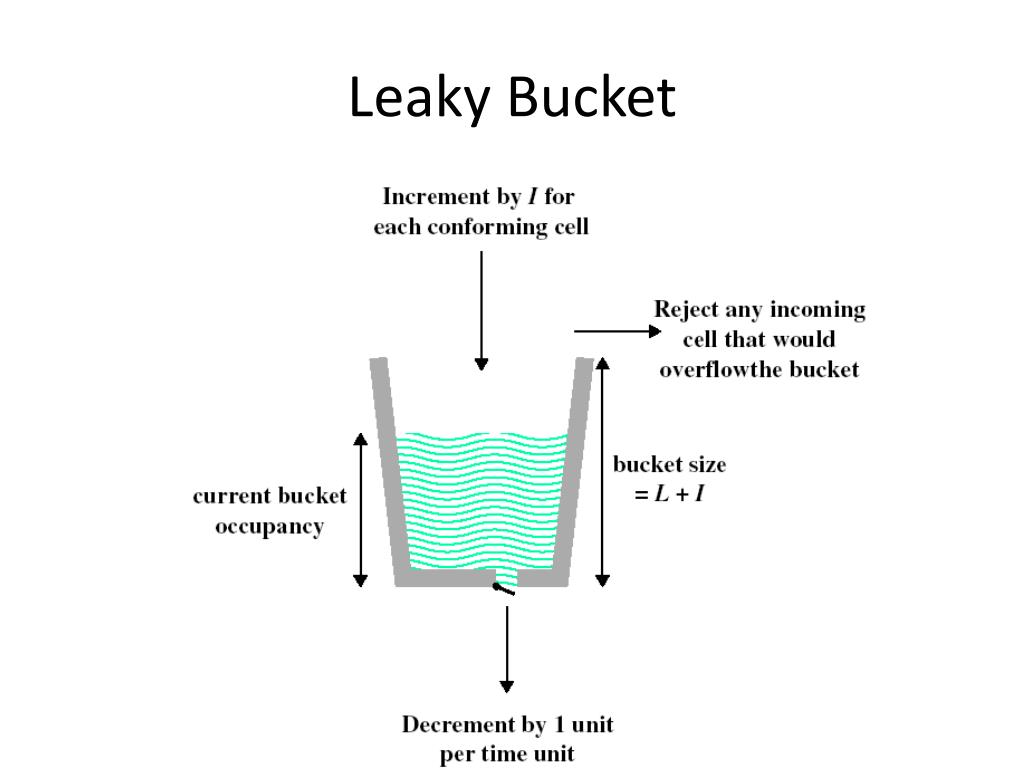
What Is Purpose Of Leaky Bucket . The leaky bucket algorithm is a network traffic management mechanism used to control the. What is the leaky bucket algorithm? The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. The leaky bucket theory explains how data moves around on the internet. Step 1 − let us imagine a. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. It works by allowing a certain. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Picture a bucket with holes, filling up with water. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a.
from www.slideserve.com
The leaky bucket algorithm is a network traffic management mechanism used to control the. Picture a bucket with holes, filling up with water. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. What is the leaky bucket algorithm? The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket theory explains how data moves around on the internet. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It works by allowing a certain. Step 1 − let us imagine a.
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download ID3429699
What Is Purpose Of Leaky Bucket Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It works by allowing a certain. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. What is the leaky bucket algorithm? The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The leaky bucket theory explains how data moves around on the internet. Step 1 − let us imagine a. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. Picture a bucket with holes, filling up with water. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket algorithm is a network traffic management mechanism used to control the.
From www.researchgate.net
The basic "leaky bucket" Economic inflows and outflows Download Scientific Diagram What Is Purpose Of Leaky Bucket What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us imagine a. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and. What Is Purpose Of Leaky Bucket.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download ID3429699 What Is Purpose Of Leaky Bucket The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us imagine a. It works by. What Is Purpose Of Leaky Bucket.
From slidemodel.com
Leaky Bucket PowerPoint Template SlideModel What Is Purpose Of Leaky Bucket It works by allowing a certain. The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The leaky bucket theory explains how data moves around on the. What Is Purpose Of Leaky Bucket.
From slidemodel.com
Leaky Bucket PowerPoint Template SlideModel What Is Purpose Of Leaky Bucket The leaky bucket theory explains how data moves around on the internet. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket is a traffic shaping and policing mechanism used in. What Is Purpose Of Leaky Bucket.
From awstip.com
AWS CDK & Leaky Bucket Manage Traffic Congestion AWS Tip What Is Purpose Of Leaky Bucket What is the leaky bucket algorithm? The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. It works by allowing a certain. Step 1 − let us imagine a. The leaky bucket algorithm is a network traffic management mechanism used to. What Is Purpose Of Leaky Bucket.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube What Is Purpose Of Leaky Bucket The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket theory explains how data moves around on the internet. Step 1 − let us imagine a. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It works by allowing a. What Is Purpose Of Leaky Bucket.
From www.engati.com
Leaky Bucket Theory Engati What Is Purpose Of Leaky Bucket The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket theory explains how data moves around on the internet. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. It. What Is Purpose Of Leaky Bucket.
From www.dreamstime.com
Leaky Bucket stock image. Image of waste, running, holes 5839431 What Is Purpose Of Leaky Bucket The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket theory explains how data moves around on the internet. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a. What Is Purpose Of Leaky Bucket.
From www.mikeperham.com
The Leaky Bucket rate limiter Mike Perham What Is Purpose Of Leaky Bucket It works by allowing a certain. The leaky bucket theory explains how data moves around on the internet. What is the leaky bucket algorithm? The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. The leaky bucket algorithm is a network traffic management mechanism used to control the. Leaky bucket. What Is Purpose Of Leaky Bucket.
From www.allbusiness.com
Patching the Leaky Bucket How Powerful CRM Data Can Reduce Customer Churn What Is Purpose Of Leaky Bucket Step 1 − let us imagine a. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Picture a bucket with. What Is Purpose Of Leaky Bucket.
From www.slideserve.com
PPT Bandwidth Management PowerPoint Presentation, free download ID3787281 What Is Purpose Of Leaky Bucket The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket theory explains how data moves around on the internet. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It works by allowing a certain. Step 1 − let us imagine. What Is Purpose Of Leaky Bucket.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram What Is Purpose Of Leaky Bucket It works by allowing a certain. Step 1 − let us imagine a. The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket theory explains how data moves around on the internet. What is the leaky bucket algorithm? The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with. What Is Purpose Of Leaky Bucket.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics What Is Purpose Of Leaky Bucket Picture a bucket with holes, filling up with water. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed. What Is Purpose Of Leaky Bucket.
From www.slideshare.net
Leaky bucket algorithm What Is Purpose Of Leaky Bucket The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. It works by allowing a certain. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity. What Is Purpose Of Leaky Bucket.
From www.slidegeeks.com
Leaky Bucket Approach For Job Problems And Financial Issues Ppt PowerPoint Presentation What Is Purpose Of Leaky Bucket The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow. What Is Purpose Of Leaky Bucket.
From www.youtube.com
Leaky Buckets and Integration YouTube What Is Purpose Of Leaky Bucket Step 1 − let us imagine a. The leaky bucket theory explains how data moves around on the internet. It works by allowing a certain. What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the. Picture a bucket with holes, filling up with water. The leaky bucket is used to. What Is Purpose Of Leaky Bucket.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? What Is Purpose Of Leaky Bucket The leaky bucket theory explains how data moves around on the internet. What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at. What Is Purpose Of Leaky Bucket.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? What Is Purpose Of Leaky Bucket Picture a bucket with holes, filling up with water. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. It works by allowing a certain. The leaky bucket theory explains how data moves around on the internet. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out). What Is Purpose Of Leaky Bucket.
From workology.com
The Leaky Bucket Theory Workology What Is Purpose Of Leaky Bucket Picture a bucket with holes, filling up with water. What is the leaky bucket algorithm? Step 1 − let us imagine a. The leaky bucket theory explains how data moves around on the internet. The leaky bucket algorithm is a network traffic management mechanism used to control the. It works by allowing a certain. The leaky bucket is used to. What Is Purpose Of Leaky Bucket.
From www.researchgate.net
The leaky bucket states (A) overflown, and (B) nonoverflown. Download Scientific Diagram What Is Purpose Of Leaky Bucket Picture a bucket with holes, filling up with water. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. Leaky bucket. What Is Purpose Of Leaky Bucket.
From www.youtube.com
Traffic Shaping Leaky Bucket Token Bucket Improve QoS Computer Networks Part 3 YouTube What Is Purpose Of Leaky Bucket The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The leaky bucket theory explains how data moves around on the internet. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data. What Is Purpose Of Leaky Bucket.
From www.engati.com
Leaky Bucket Theory Engati What Is Purpose Of Leaky Bucket Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. It works by allowing a certain. What is the leaky bucket algorithm? The. What Is Purpose Of Leaky Bucket.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram What Is Purpose Of Leaky Bucket The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Picture a bucket with holes, filling up with water. The leaky bucket algorithm is a network traffic management mechanism used to control the. Leaky bucket algorithm mainly controls the total amount. What Is Purpose Of Leaky Bucket.
From www.slideserve.com
PPT PLUGGING THE LEAKS PowerPoint Presentation, free download ID1458842 What Is Purpose Of Leaky Bucket The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The leaky bucket algorithm is a network traffic management mechanism used to control the. Step 1 − let us imagine a. The leaky bucket theory explains how data moves around on. What Is Purpose Of Leaky Bucket.
From www.engati.com
Leaky Bucket Theory Engati What Is Purpose Of Leaky Bucket The leaky bucket theory explains how data moves around on the internet. It works by allowing a certain. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Picture a bucket with holes, filling up with water. What is the leaky. What Is Purpose Of Leaky Bucket.
From redrouteinternational.com
How leaky is your bucket? RedRoute International What Is Purpose Of Leaky Bucket It works by allowing a certain. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Step 1 − let us imagine a. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a.. What Is Purpose Of Leaky Bucket.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID3009018 What Is Purpose Of Leaky Bucket It works by allowing a certain. Picture a bucket with holes, filling up with water. The leaky bucket theory explains how data moves around on the internet. The leaky bucket algorithm is a network traffic management mechanism used to control the. What is the leaky bucket algorithm? Step 1 − let us imagine a. The leaky bucket rate limiting algorithm. What Is Purpose Of Leaky Bucket.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download ID3033466 What Is Purpose Of Leaky Bucket The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Leaky bucket algorithm mainly controls the total amount and the rate of the. What Is Purpose Of Leaky Bucket.
From usewhale.io
The Leaky Bucket Syndrome and how to combat knowledge loss Whale What Is Purpose Of Leaky Bucket The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. It works by allowing a certain. The leaky bucket theory explains how data moves around on the internet. Step 1 − let us imagine a. What is the leaky bucket algorithm? The leaky bucket rate limiting algorithm utilizes a fifo. What Is Purpose Of Leaky Bucket.
From www.slideshare.net
The Leaky Bucket Principle What Is Purpose Of Leaky Bucket The leaky bucket algorithm is a network traffic management mechanism used to control the. Step 1 − let us imagine a. Picture a bucket with holes, filling up with water. It works by allowing a certain. What is the leaky bucket algorithm? The leaky bucket theory explains how data moves around on the internet. The leaky bucket is a traffic. What Is Purpose Of Leaky Bucket.
From www.engati.com
Leaky Bucket Theory Engati What Is Purpose Of Leaky Bucket Step 1 − let us imagine a. The leaky bucket is a traffic shaping and policing mechanism used in networking to control the flow of data packets. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent. What Is Purpose Of Leaky Bucket.
From www.freepik.com
Premium Photo Leaky bucket with water on blue background What Is Purpose Of Leaky Bucket What is the leaky bucket algorithm? The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The leaky bucket algorithm is a network traffic management mechanism used to control the. It works by allowing a certain. The leaky bucket is used. What Is Purpose Of Leaky Bucket.
From www.alamy.com
Studio shot of leaking bucket Stock Photo Alamy What Is Purpose Of Leaky Bucket Step 1 − let us imagine a. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. What is the leaky bucket algorithm? The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket algorithm is a network traffic management mechanism used. What Is Purpose Of Leaky Bucket.
From www.engati.com
What to do about your company's leaky bucket Engati What Is Purpose Of Leaky Bucket Picture a bucket with holes, filling up with water. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It works by allowing. What Is Purpose Of Leaky Bucket.
From aphrc.org
The Leaking Bucket Phenomenon in Family Planning APHRCAPHRC What Is Purpose Of Leaky Bucket Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Picture a bucket with holes, filling up with water. The leaky bucket theory explains how data moves around on the internet. The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket is a traffic shaping. What Is Purpose Of Leaky Bucket.