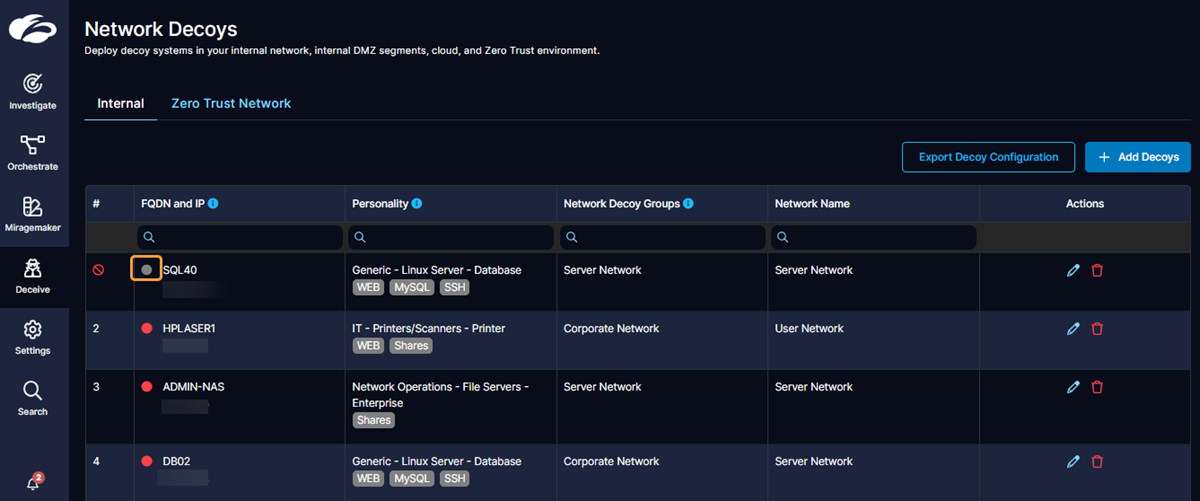
Zscaler Network Decoy . Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their.
from help.zscaler.com
Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal.
Disabling a Network Decoy Zscaler
Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments.
From help.zscaler.com
Disabling a Network Decoy Zscaler Zscaler Network Decoy Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. How to edit and delete a configured network decoy in the zscaler deception admin portal. Information about zscaler deception network decoys. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
Configuring Services on a Network Decoy Zscaler Zscaler Network Decoy Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler Network Decoy.
From www.zscaler.com
Zscaler for Users Empowering the Hybrid Workforce Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. Zscaler Network Decoy.
From help.zscaler.com
Configuring Services on a Network Decoy Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From help.zscaler.com
Decoy Connector Deployment Guide for Microsoft Azure Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. Zscaler Network Decoy.
From help.zscaler.com
Disabling a Network Decoy Zscaler Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. How to edit and delete a configured network decoy in the zscaler deception admin portal. Information about zscaler deception network decoys. Zscaler Network Decoy.
From help.zscaler.com
About Zscaler Deception Architecture Zscaler Zscaler Network Decoy Information about zscaler deception network decoys. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler Network Decoy.
From help.zscaler.com
Testing a Network Decoy Zscaler Zscaler Network Decoy Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From wirepartsuppresses.z22.web.core.windows.net
Zscaler Architecture Diagram Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From help.zscaler.com
Testing a Network Decoy Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From help.zscaler.com
About Zscaler Deception Architecture Zscaler Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. Zscaler Network Decoy.
From help.zscaler.com
About Network Decoy Personalities and Services Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From help.zscaler.com
Adding a Network Decoy to an Active Directory Zscaler Zscaler Network Decoy Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From mavink.com
Zscaler Architecture Diagram Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From help.zscaler.com
Decoy Connector Deployment Guide for Microsoft Azure Zscaler Zscaler Network Decoy Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
Decoy Connector Deployment Guide for Microsoft Azure Zscaler Zscaler Network Decoy Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler Network Decoy.
From help.zscaler.com
Testing a Threat Intelligence Decoy Zscaler Zscaler Network Decoy Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From www.zscaler.com
Network and UCaaS Partners Zscaler Zscaler Network Decoy Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler Network Decoy.
From help.zscaler.com
Configuring Services on a Network Decoy Zscaler Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. How to edit and delete a configured network decoy in the zscaler deception admin portal. Information about zscaler deception network decoys. Zscaler Network Decoy.
From help.zscaler.com
Decoy Connector Deployment Guide for Microsoft Azure Zscaler Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler Network Decoy.
From help.zscaler.com
Configuring Services on a Network Decoy Zscaler Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From help.zscaler.com
About Zscaler Enforcement Nodes Zscaler Zscaler Network Decoy Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. How to edit and delete a configured network decoy in the zscaler deception admin portal. Information about zscaler deception network decoys. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
Configuring Services on a Network Decoy Zscaler Zscaler Network Decoy Information about zscaler deception network decoys. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler Network Decoy.
From www.zscaler.com
Secure Your OT and IoT Systems with Zero Trust Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
Configuring a Threat Intelligence Decoy Personality Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
Configuring Services on a Network Decoy Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. Zscaler Network Decoy.
From help.zscaler.com
Deploying Private Service Edge Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
Configuring Services on a Network Decoy Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. Zscaler Network Decoy.
From help.zscaler.com
Configuring Services on a Network Decoy Zscaler Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. Zscaler Network Decoy.
From medium.com
Zscaler Architecture. Zscaler is a cloudbased security… by Ram Dixit Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
Understanding PAC Files Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Information about zscaler deception network decoys. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
About DNS Tunnel Detection Zscaler Zscaler Network Decoy Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler Network Decoy.
From help.zscaler.com
SIEM and ZIA Integration Deployment and Operations Guide Zscaler Zscaler Network Decoy How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. Zscaler Network Decoy.
From www.wanrise.com
Zscaler the best innovative cloud security system Wanrise Zscaler Network Decoy Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Zscaler Network Decoy.
From help.zscaler.com
Deploying Private Service Edge Zscaler Zscaler Network Decoy Zscaler deception creates a fake environment filled with decoy credentials and systems that trick attackers into revealing their. Zscaler deception is the easy button for detecting and stopping sophisticated threats that target zero trust environments. Information about zscaler deception network decoys. How to edit and delete a configured network decoy in the zscaler deception admin portal. Zscaler Network Decoy.