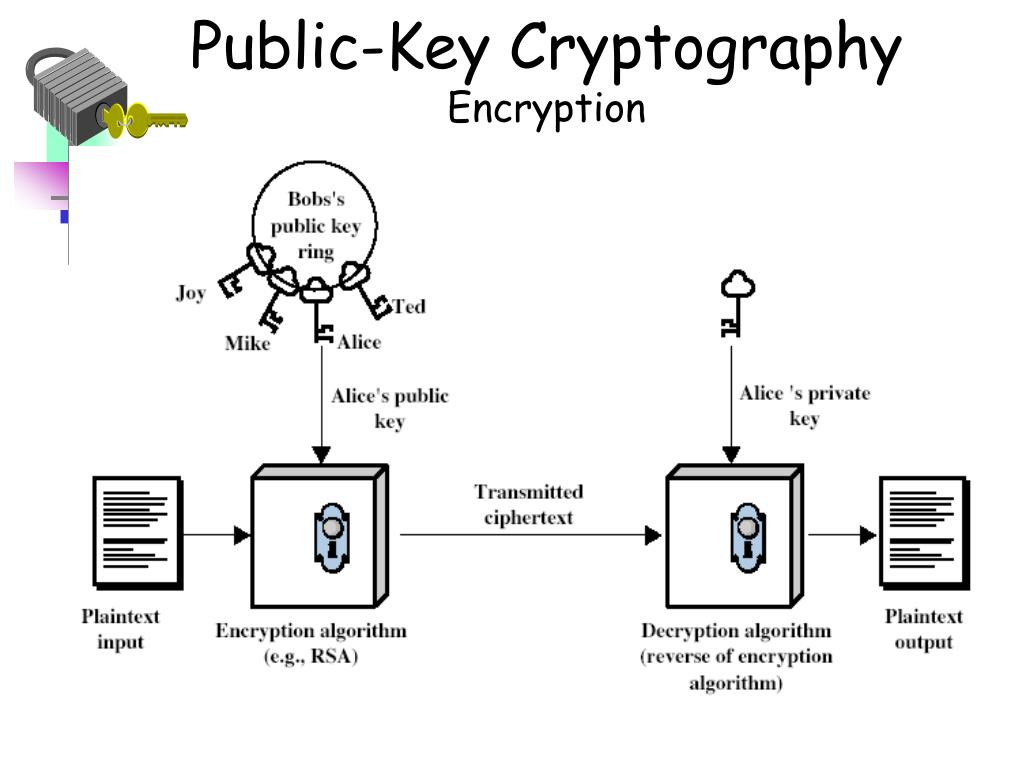
Key Ring Cryptography . A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. keyring is a directory of known encryption keys or public keys. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. Like a physical key, it. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. If you are sending a message to someone that doesn't have. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication).
from www.slideserve.com
public key cryptography (pkc) forms the backbone of various secure communication protocols, including. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. keyring is a directory of known encryption keys or public keys. Like a physical key, it. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. If you are sending a message to someone that doesn't have.
PPT Public key cryptography PowerPoint Presentation, free download
Key Ring Cryptography from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. Like a physical key, it. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. If you are sending a message to someone that doesn't have. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. keyring is a directory of known encryption keys or public keys. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network.
From www.slideserve.com
PPT Email Security Pretty Good Privacy (PGP) S/MIME PowerPoint Key Ring Cryptography in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. Like a physical key, it. If you are sending a message to someone that doesn't have. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for. Key Ring Cryptography.
From www.appsealing.com
How AES Encryption is Used in Cybersecurity and Why it Matters AppSealing Key Ring Cryptography from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. If you are sending a message to someone that doesn't have. Like a physical key, it. if you think. Key Ring Cryptography.
From courses.javacodegeeks.com
Asymmetric Cryptography and Key Management Reviews & Coupon Java Key Ring Cryptography If you are sending a message to someone that doesn't have. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. from des to captain midnight's secret decoder ring, the persistent problem. Key Ring Cryptography.
From www.edureka.co
What is Cryptography? Cryptographic Algorithms Types of Key Ring Cryptography Like a physical key, it. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. If you are sending a message to someone that doesn't have. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it. Key Ring Cryptography.
From jsis.washington.edu
Cryptography, Quantum Computing, and Paths Forward The Henry M Key Ring Cryptography in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. If you are sending a message to someone that doesn't have. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). from des to. Key Ring Cryptography.
From slideplayer.com
ELECTRONIC MAIL SECURITY ppt download Key Ring Cryptography keyring is a directory of known encryption keys or public keys. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. public key. Key Ring Cryptography.
From wiki.st.com
SecurityIntroduction to Cryptography stm32mcu Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). Like a physical key, it. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. keyring is a directory of known encryption keys or. Key Ring Cryptography.
From usemynotes.com
Advantages and Disadvantages of PGP encryption UseMyNotes Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). keyring is a directory of known encryption keys or public keys. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. in cryptography, a key is a string of characters used within. Key Ring Cryptography.
From deepai.org
Public key cryptography based on skew dihedral group rings DeepAI Key Ring Cryptography keyring is a directory of known encryption keys or public keys. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. A key ring is a file that contains the. Key Ring Cryptography.
From blog.elmah.io
CryptographicException The key was not found in the key ring Key Ring Cryptography public key cryptography (pkc) forms the backbone of various secure communication protocols, including. Like a physical key, it. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. keyring is a directory of known encryption keys or public keys. in cryptography, a key is. Key Ring Cryptography.
From www.encryptionconsulting.com
What is the difference between Encryption and Tokenization? Which is Key Ring Cryptography in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. Like a physical key, it. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. . Key Ring Cryptography.
From pnghut.com
Digital Signature RSA Publickey Cryptography Algorithm Ring Key Ring Cryptography from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. keyring is a directory of known encryption keys or public keys. if you think about integers, they are. Key Ring Cryptography.
From www.mdpi.com
Cryptography Free FullText Revisiting Multiple Ring Oscillator Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). If you are sending a message to someone that doesn't have. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. public key cryptography (pkc) forms the backbone of various. Key Ring Cryptography.
From cyberblogindia.in
A Beginner's Guide to Cryptography The Cyber Blog India Key Ring Cryptography Like a physical key, it. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. If you are sending a message to someone that doesn't have. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. A key ring is a file that. Key Ring Cryptography.
From demonstrations.wolfram.com
Kids' Cryptography with a Key from a Propositional Puzzle Wolfram Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. . Key Ring Cryptography.
From www.thesslstore.com
Symmetric Encryption Algorithms Live Long & Encrypt Hashed Out by Key Ring Cryptography public key cryptography (pkc) forms the backbone of various secure communication protocols, including. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). Like a physical key, it. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys. Key Ring Cryptography.
From demonstrations.wolfram.com
Kids' Cryptography with a Key from a Wallpaper Group Wolfram Key Ring Cryptography public key cryptography (pkc) forms the backbone of various secure communication protocols, including. Like a physical key, it. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. in. Key Ring Cryptography.
From www.dreamstime.com
Key Ring stock image. Image of knob, opportunity, entrance 99691483 Key Ring Cryptography keyring is a directory of known encryption keys or public keys. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. from des. Key Ring Cryptography.
From demonstrations.wolfram.com
Kids' Cryptography with a Key from a Wallpaper Group Wolfram Key Ring Cryptography Like a physical key, it. If you are sending a message to someone that doesn't have. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. keyring is a directory of known encryption keys or public keys. in cryptography, a key is a string of characters used within an encryption algorithm. Key Ring Cryptography.
From www.slideserve.com
PPT Email Security PowerPoint Presentation, free download ID5800146 Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. If you are sending a message to someone that doesn't have. in cryptography, a key is a string of characters. Key Ring Cryptography.
From www.prc68.com
Crypto Machines Key Ring Cryptography Like a physical key, it. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. If you are sending a message to someone that doesn't have. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. in cryptography, a key is a string of characters used within an. Key Ring Cryptography.
From www.slideserve.com
PPT Public key cryptography PowerPoint Presentation, free download Key Ring Cryptography If you are sending a message to someone that doesn't have. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. from des to. Key Ring Cryptography.
From jayendrapatil.com
Google Cloud KMS Key Management Service Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. If you are sending a message to someone that doesn't have. from des to. Key Ring Cryptography.
From www.slideserve.com
PPT Public Key RSA & Diffie Hellman Key Exchange PowerPoint Key Ring Cryptography If you are sending a message to someone that doesn't have. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. if you think about integers, they are a ring, which is a group (for addition) and a. Key Ring Cryptography.
From www.mdpi.com
Cryptography Free FullText Revisiting Multiple Ring Oscillator Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. If you are sending a message to. Key Ring Cryptography.
From www.printables.com
PrintinPlace Rotary Caesar Cipher Ring Cryptographic Decoder Key Ring Cryptography keyring is a directory of known encryption keys or public keys. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. If you are sending a message to someone that doesn't have. public key cryptography (pkc) forms the backbone of various secure communication protocols, including.. Key Ring Cryptography.
From www.slideserve.com
PPT Email Security Pretty Good Privacy (PGP) S/MIME PowerPoint Key Ring Cryptography public key cryptography (pkc) forms the backbone of various secure communication protocols, including. keyring is a directory of known encryption keys or public keys. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted. Key Ring Cryptography.
From www.slideserve.com
PPT Lecture 07 PGP and S/MIME PowerPoint Presentation, free download Key Ring Cryptography keyring is a directory of known encryption keys or public keys. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. public. Key Ring Cryptography.
From www.printables.com
PrintinPlace Rotary Caesar Cipher Ring Cryptographic Decoder Key Ring Cryptography If you are sending a message to someone that doesn't have. keyring is a directory of known encryption keys or public keys. Like a physical key, it. if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). A key ring is a file that contains the digital. Key Ring Cryptography.
From www.slideserve.com
PPT Cryptography and Network Security Chapter 18 PowerPoint Key Ring Cryptography in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. keyring is a directory of known encryption keys or public keys. Like a physical key, it. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used. Key Ring Cryptography.
From medium.com
What is cryptography ?. Cryptography is a method of protecting… by Key Ring Cryptography keyring is a directory of known encryption keys or public keys. Like a physical key, it. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. public key cryptography (pkc) forms the backbone of various secure communication protocols, including. If you are sending a message. Key Ring Cryptography.
From www.slideserve.com
PPT Email Security PowerPoint Presentation, free download ID5800146 Key Ring Cryptography public key cryptography (pkc) forms the backbone of various secure communication protocols, including. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. Like a physical key, it. in cryptography, a key is a string of characters used within an encryption algorithm for altering data. Key Ring Cryptography.
From anniebryan109rumor.blogspot.com
Cryptography Definition And Types Key Ring Cryptography A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. keyring is a directory of known encryption keys or public keys. from des to captain midnight's secret decoder ring, the persistent problem with conventional encryption is key. Like a physical key, it. If you are. Key Ring Cryptography.
From www.researchgate.net
(PDF) Special ideal ring A3 and cryptography Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). If you are sending a message to someone that doesn't have. in cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. Like a physical key,. Key Ring Cryptography.
From www.youtube.com
PGP Cryptographic Keys and Keys Rings, PGP Message Format CST409NSP Key Ring Cryptography if you think about integers, they are a ring, which is a group (for addition) and a semi group (for multiplication). public key cryptography (pkc) forms the backbone of various secure communication protocols, including. A key ring is a file that contains the digital certificates, public keys, private keys, and trusted root keys used by a network. . Key Ring Cryptography.