Protection Risks Examples . a protection risk analysis allows crs and partner project teams to: If groups or individuals with specific needs are not identified early in an emergency, they may. Is each protection risk specific to cbi? 1) gather data on existing protection risks; — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). each type of risk may demonstrate a different risk pattern: Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. Different perpetrators, different contributory and underlying factors; — protection risks.
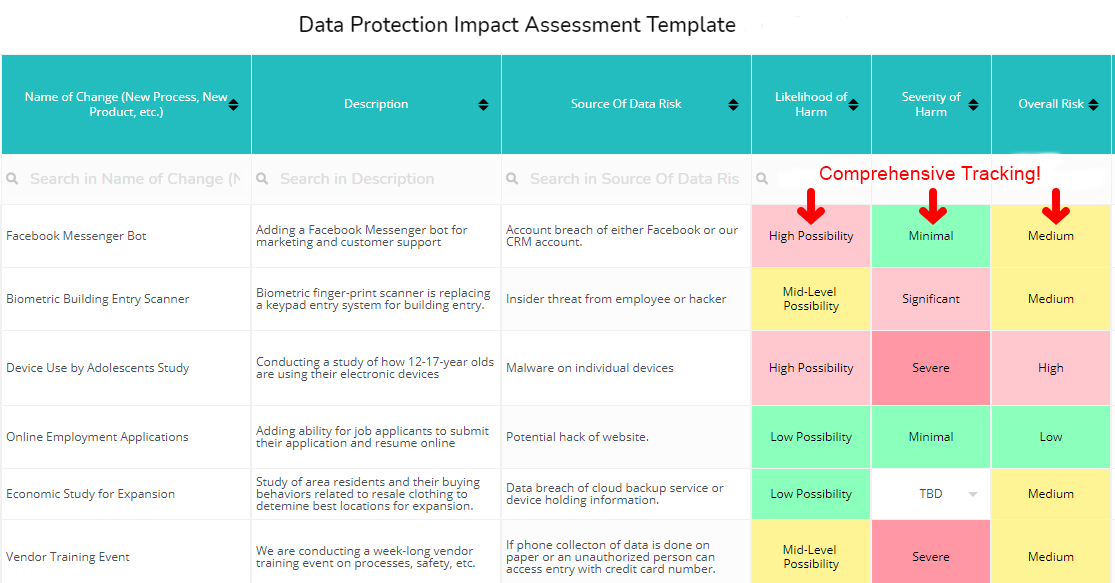
from www.ocmsolution.com
Is each protection risk specific to cbi? If groups or individuals with specific needs are not identified early in an emergency, they may. 1) gather data on existing protection risks; a protection risk analysis allows crs and partner project teams to: each type of risk may demonstrate a different risk pattern: Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. — protection risks. Different perpetrators, different contributory and underlying factors; — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020).
Best Data Protection Impact Assessment Toolkit Templates, Dashboards
Protection Risks Examples Different perpetrators, different contributory and underlying factors; Is each protection risk specific to cbi? — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). — protection risks. Different perpetrators, different contributory and underlying factors; each type of risk may demonstrate a different risk pattern: a protection risk analysis allows crs and partner project teams to: Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. If groups or individuals with specific needs are not identified early in an emergency, they may. 1) gather data on existing protection risks;
From blog.qatestlab.com
How to Identify and Manage Testing Risks? QATestLab Blog Protection Risks Examples Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. If groups or individuals with specific needs are not identified early in an emergency, they may. — protection risks. each type of risk may demonstrate a different risk pattern: Is each protection risk specific to cbi? a protection risk analysis allows crs and partner project teams to:. Protection Risks Examples.
From www.issuesonline.co.uk
Risk and protective factors Mental Health Issues Online Protection Risks Examples Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. If groups or individuals with specific needs are not identified early in an emergency, they may. — protection risks. a protection risk analysis allows crs and partner project teams to: each type of risk may demonstrate a different risk pattern: — protective factors are elements that. Protection Risks Examples.
From felicitblog2005.blogspot.com
COMMON HAZARDS AT WORK PLACE Protection Risks Examples — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). If groups or individuals with specific needs are not identified early in an emergency, they may. each type of risk may demonstrate a different risk pattern: Is each protection risk specific to cbi? Different perpetrators, different contributory and underlying. Protection Risks Examples.
From ctb.ku.edu
Chapter 19. Choosing and Adapting Community Interventions Section 2 Protection Risks Examples a protection risk analysis allows crs and partner project teams to: — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). — protection risks. each type of risk may demonstrate a different risk pattern: 1) gather data on existing protection risks; If groups or individuals with specific. Protection Risks Examples.
From www.scribd.com
13Information Security Risk Assessment Procedure example.docx Protection Risks Examples 1) gather data on existing protection risks; Is each protection risk specific to cbi? Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. If groups or individuals with specific needs are not identified early in an emergency, they may. Different perpetrators, different contributory and underlying factors; — protective factors are elements that decrease the likelihood of negative outcomes. Protection Risks Examples.
From www.saferspaces.org.za
Understanding Risks for Violence Victimization and Perpetration Protection Risks Examples If groups or individuals with specific needs are not identified early in an emergency, they may. a protection risk analysis allows crs and partner project teams to: Different perpetrators, different contributory and underlying factors; — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). Is each protection risk specific. Protection Risks Examples.
From helpfulprofessor.com
38 Protective Factors Examples (2024) Protection Risks Examples Different perpetrators, different contributory and underlying factors; each type of risk may demonstrate a different risk pattern: 1) gather data on existing protection risks; a protection risk analysis allows crs and partner project teams to: — protection risks. Is each protection risk specific to cbi? If groups or individuals with specific needs are not identified early in. Protection Risks Examples.
From www.vrogue.co
Child Protection Risk Assessment Template Sampletempl vrogue.co Protection Risks Examples If groups or individuals with specific needs are not identified early in an emergency, they may. Different perpetrators, different contributory and underlying factors; Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. each type of risk may demonstrate a different risk pattern: — protection risks. — protective factors are elements that decrease the likelihood of negative. Protection Risks Examples.
From studylib.net
Adult Safeguarding Risk Assessment Matrix Protection Risks Examples each type of risk may demonstrate a different risk pattern: Different perpetrators, different contributory and underlying factors; — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). If groups or individuals with specific needs are not identified early in an emergency, they may. Consider different cbi modalities (cash, voucher). Protection Risks Examples.
From ssaform.com
Hazard Classifications / Risk Assessment FFRP Site Safety Assessment Protection Risks Examples a protection risk analysis allows crs and partner project teams to: each type of risk may demonstrate a different risk pattern: Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. Different perpetrators, different contributory and underlying factors; Is each protection risk specific to cbi? — protection risks. — protective factors are elements that decrease the. Protection Risks Examples.
From www.researchgate.net
Example of Protective and Risk Factors for two contrasting students Protection Risks Examples Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. If groups or individuals with specific needs are not identified early in an emergency, they may. Different perpetrators, different contributory and underlying factors; a protection risk analysis allows crs and partner project teams to: 1) gather data on existing protection risks; — protective factors are elements that decrease. Protection Risks Examples.
From www.compasscyber.com
A Risk Manager's Approach to Cyber Security Compass Cyber Security Protection Risks Examples each type of risk may demonstrate a different risk pattern: a protection risk analysis allows crs and partner project teams to: — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). If groups or individuals with specific needs are not identified early in an emergency, they may. . Protection Risks Examples.
From www.vrogue.co
5 Steps To An Effective Risk Management Process vrogue.co Protection Risks Examples Different perpetrators, different contributory and underlying factors; Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. Is each protection risk specific to cbi? a protection risk analysis allows crs and partner project teams to: 1) gather data on existing protection risks; — protection risks. each type of risk may demonstrate a different risk pattern: —. Protection Risks Examples.
From www.naturalhigh.org
Risk factor vs Protective Factor Natural High Protection Risks Examples a protection risk analysis allows crs and partner project teams to: each type of risk may demonstrate a different risk pattern: Different perpetrators, different contributory and underlying factors; — protection risks. Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. Is each protection risk specific to cbi? If groups or individuals with specific needs are not. Protection Risks Examples.
From sitemate.com
Risk monitoring and control Here's how to do it better and safer Protection Risks Examples each type of risk may demonstrate a different risk pattern: — protection risks. Different perpetrators, different contributory and underlying factors; 1) gather data on existing protection risks; a protection risk analysis allows crs and partner project teams to: Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. Is each protection risk specific to cbi? —. Protection Risks Examples.
From www.slideteam.net
Data Security Risk Assessment Matrix Presentation Graphics Protection Risks Examples — protection risks. each type of risk may demonstrate a different risk pattern: Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. Is each protection risk specific to cbi? a protection risk analysis allows crs and partner project teams to: 1) gather data on existing protection risks; Different perpetrators, different contributory and underlying factors; —. Protection Risks Examples.
From www.securingpeople.com
Security Risk Assessment Business Protection Specialists Protection Risks Examples each type of risk may demonstrate a different risk pattern: Different perpetrators, different contributory and underlying factors; Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. 1) gather data on existing protection risks; a protection risk analysis allows crs and partner project teams to: If groups or individuals with specific needs are not identified early in an. Protection Risks Examples.
From www.pinterest.de
This infographic illustrates the elements of a hazard control program Protection Risks Examples Different perpetrators, different contributory and underlying factors; Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. — protection risks. 1) gather data on existing protection risks; Is each protection risk specific to cbi? — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). each type of risk. Protection Risks Examples.
From www.sampletemplates.com
FREE 11+ Risk Assessment Templates in PDF MS Word Pages Protection Risks Examples If groups or individuals with specific needs are not identified early in an emergency, they may. Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). a protection risk analysis allows crs and partner project teams to: —. Protection Risks Examples.
From www.isaca.org
Privacy Risk Management Protection Risks Examples Different perpetrators, different contributory and underlying factors; a protection risk analysis allows crs and partner project teams to: If groups or individuals with specific needs are not identified early in an emergency, they may. 1) gather data on existing protection risks; — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone &. Protection Risks Examples.
From www.researchgate.net
Visualization of some indicative risk and protective factors across Protection Risks Examples Different perpetrators, different contributory and underlying factors; — protection risks. a protection risk analysis allows crs and partner project teams to: Is each protection risk specific to cbi? 1) gather data on existing protection risks; each type of risk may demonstrate a different risk pattern: — protective factors are elements that decrease the likelihood of negative. Protection Risks Examples.
From www.tpsearchtool.com
The Risk Matrix And Sample Risk Assessment Tables Images Protection Risks Examples a protection risk analysis allows crs and partner project teams to: each type of risk may demonstrate a different risk pattern: Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. Is each protection risk specific to cbi? — protection risks. 1) gather data on existing protection risks; — protective factors are elements that decrease the. Protection Risks Examples.
From www.ocmsolution.com
Best Data Protection Impact Assessment Toolkit Templates, Dashboards Protection Risks Examples — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). a protection risk analysis allows crs and partner project teams to: Different perpetrators, different contributory and underlying factors; — protection risks. If groups or individuals with specific needs are not identified early in an emergency, they may. Is. Protection Risks Examples.
From www.cbspmitchelstown.com
Child Safeguarding Risk Assessment Protection Risks Examples Is each protection risk specific to cbi? — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). a protection risk analysis allows crs and partner project teams to: If groups or individuals with specific needs are not identified early in an emergency, they may. each type of risk. Protection Risks Examples.
From martincountyfl.sites.thrillshare.com
Risk Mitigation Strategies MARTIN COUNTY SCHOOL DISTRICT Protection Risks Examples a protection risk analysis allows crs and partner project teams to: — protection risks. 1) gather data on existing protection risks; Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. each type of risk may demonstrate a different risk pattern: If groups or individuals with specific needs are not identified early in an emergency, they may.. Protection Risks Examples.
From www.slideteam.net
Data Privacy Compliance Risk Assessment And Solution Framework Protection Risks Examples If groups or individuals with specific needs are not identified early in an emergency, they may. — protection risks. a protection risk analysis allows crs and partner project teams to: 1) gather data on existing protection risks; each type of risk may demonstrate a different risk pattern: Different perpetrators, different contributory and underlying factors; — protective. Protection Risks Examples.
From nbhc.ca
Protective and Risk Factors Explained New Brunswick Health Council Protection Risks Examples — protection risks. — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). a protection risk analysis allows crs and partner project teams to: Is each protection risk specific to cbi? If groups or individuals with specific needs are not identified early in an emergency, they may. 1). Protection Risks Examples.
From www.youtube.com
Video 2 Risk and Protective Factors YouTube Protection Risks Examples Different perpetrators, different contributory and underlying factors; If groups or individuals with specific needs are not identified early in an emergency, they may. each type of risk may demonstrate a different risk pattern: 1) gather data on existing protection risks; Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. Is each protection risk specific to cbi? —. Protection Risks Examples.
From www.studocu.com
Child Safe Standard 6 Risk Assessment CHILD SAFE STANDARD 6 RISK Protection Risks Examples Different perpetrators, different contributory and underlying factors; each type of risk may demonstrate a different risk pattern: — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). If groups or individuals with specific needs are not identified early in an emergency, they may. Consider different cbi modalities (cash, voucher). Protection Risks Examples.
From www.bernsteincrisismanagement.com
5 Common Workplace Safety Hazards Bernstein Crisis Management Protection Risks Examples Different perpetrators, different contributory and underlying factors; If groups or individuals with specific needs are not identified early in an emergency, they may. — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). each type of risk may demonstrate a different risk pattern: Is each protection risk specific to. Protection Risks Examples.
From www.riskpal.com
Risk Assessment Matrices Tools to Visualise Risk Protection Risks Examples Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. a protection risk analysis allows crs and partner project teams to: 1) gather data on existing protection risks; Is each protection risk specific to cbi? — protection risks. each type of risk may demonstrate a different risk pattern: Different perpetrators, different contributory and underlying factors; —. Protection Risks Examples.
From www.assessor.com.au
How to read a risk matrix used in a risk analysis Protection Risks Examples 1) gather data on existing protection risks; Different perpetrators, different contributory and underlying factors; each type of risk may demonstrate a different risk pattern: Is each protection risk specific to cbi? Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone &. Protection Risks Examples.
From www.pinterest.com.au
Risk and protective factors that influence children's wellbeing Protection Risks Examples Different perpetrators, different contributory and underlying factors; — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). If groups or individuals with specific needs are not identified early in an emergency, they may. Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. 1) gather data on existing protection risks;. Protection Risks Examples.
From dxofeotiz.blob.core.windows.net
Child Protection Risk Assessment Framework at Sandra Rodriguez blog Protection Risks Examples Different perpetrators, different contributory and underlying factors; — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). Consider different cbi modalities (cash, voucher) and delivery mechanisms (cash,. If groups or individuals with specific needs are not identified early in an emergency, they may. each type of risk may demonstrate. Protection Risks Examples.
From www.mentallyhealthyschools.org.uk
Risks and protective factors Mentally Healthy Schools Protection Risks Examples If groups or individuals with specific needs are not identified early in an emergency, they may. — protection risks. — protective factors are elements that decrease the likelihood of negative outcomes and bolster resilience (hewstone & stroebe, 2020). a protection risk analysis allows crs and partner project teams to: each type of risk may demonstrate a. Protection Risks Examples.