What Is Access Control Threats . Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. In the context of web. Inadequate access control measures that could leave your organization open to cyberattacks. Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. By controlling who or what has. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control is the application of constraints on who or what is authorized to perform actions or access resources.
from www.scanvis-ai.com
Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. Access control is the application of constraints on who or what is authorized to perform actions or access resources. In the context of web. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Inadequate access control measures that could leave your organization open to cyberattacks. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. By controlling who or what has.
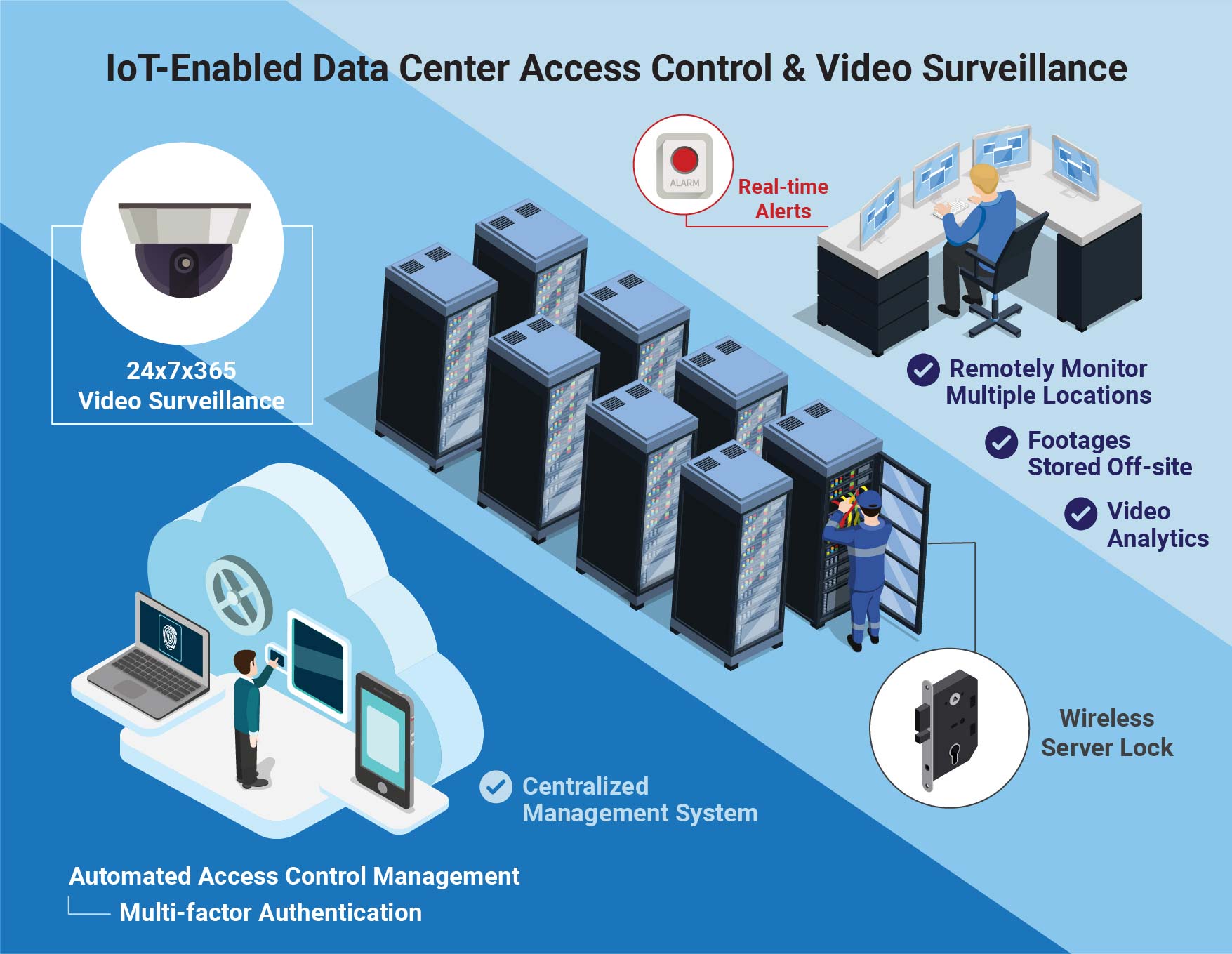
Key elements of IoTenabled physical access control solutions for data
What Is Access Control Threats Access control is the application of constraints on who or what is authorized to perform actions or access resources. Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. Inadequate access control measures that could leave your organization open to cyberattacks. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is the application of constraints on who or what is authorized to perform actions or access resources. In the context of web. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. By controlling who or what has. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to.
From www.cdvi.co.uk
What is access control? Access control explained CDVI UK What Is Access Control Threats Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a proactive security measure that helps deter,. What Is Access Control Threats.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download What Is Access Control Threats Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. In the context of web. Access control mitigates the risk of insider threats by enforcing. What Is Access Control Threats.
From cloudkul.com
Comprehension The Risk of "Broken Authentication & Broken Access What Is Access Control Threats In the context of web. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is the application of constraints on who or what is authorized to perform actions or access resources. Inadequate access control measures that could leave your organization open to. What Is Access Control Threats.
From slideplayer.com
ISA 400 Management of Information Security ppt download What Is Access Control Threats In the context of web. Inadequate access control measures that could leave your organization open to cyberattacks. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can. What Is Access Control Threats.
From securetriad.io
Internal vs External Threats Here’s All You Need to Know What Is Access Control Threats In the context of web. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. By controlling who or what has. Inadequate access control measures that could leave your organization open to cyberattacks. Access control is a data security process that enables organizations to manage. What Is Access Control Threats.
From slideplayer.com
Security network management ppt download What Is Access Control Threats Access control is the application of constraints on who or what is authorized to perform actions or access resources. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. By controlling who or what has. Access control minimizes the risk of authorized access to physical and computer systems, forming. What Is Access Control Threats.
From liquidvideotechnologies.com
What is Access Control Liquid Video Technologies What Is Access Control Threats Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control minimizes the risk of authorized access to physical and computer systems, forming. What Is Access Control Threats.
From www.strongdm.com
3 Types of Access Control IT Security Models Explained StrongDM What Is Access Control Threats Inadequate access control measures that could leave your organization open to cyberattacks. In the context of web. By controlling who or what has. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control is a security process that determines who. What Is Access Control Threats.
From www.researchgate.net
Threat tree showing missing Function Level Access Control threats What Is Access Control Threats By controlling who or what has. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. Access control mitigates the risk of insider threats by enforcing the principle of least. What Is Access Control Threats.
From www.gotyoursixcyber.com
Access Control Got Your Six Cybersecurity What Is Access Control Threats Inadequate access control measures that could leave your organization open to cyberattacks. In the context of web. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. By controlling who or what has. Access control is a data security process that enables. What Is Access Control Threats.
From dallasmeowgiles.blogspot.com
Which of the Following Correctly Describes a Security Patch What Is Access Control Threats Access control is the application of constraints on who or what is authorized to perform actions or access resources. Inadequate access control measures that could leave your organization open to cyberattacks. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. In the context of web. In a world. What Is Access Control Threats.
From www.sysvoot.com
What is Access Control and Why is it Important for Cybersecurity? What Is Access Control Threats Access control is the application of constraints on who or what is authorized to perform actions or access resources. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what. What Is Access Control Threats.
From identitymanagementinstitute.org
Identity and Access Management Threats Identity Management Institute® What Is Access Control Threats Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is the application of constraints on who or. What Is Access Control Threats.
From www.g2.com
Access Control Technology Glossary Definitions G2 What Is Access Control Threats Access control is the application of constraints on who or what is authorized to perform actions or access resources. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. In the context of web. By controlling who or what has. Inadequate access control measures that could leave your organization open to cyberattacks. Access control is. What Is Access Control Threats.
From slidetodoc.com
Access Control Authentication and Public Key Infrastructure Lesson What Is Access Control Threats Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control minimizes the risk of authorized access to physical and computer. What Is Access Control Threats.
From www.youtube.com
Information Security Management What is Access Control What is What Is Access Control Threats Inadequate access control measures that could leave your organization open to cyberattacks. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. By controlling who or what has. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. Access. What Is Access Control Threats.
From www.slideteam.net
Types Network Security Threats Ppt Powerpoint Presentation Infographic What Is Access Control Threats In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. In the context of web. Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. Access control. What Is Access Control Threats.
From www.researchgate.net
3 Threats in Access Control Download Scientific Diagram What Is Access Control Threats Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Inadequate access control measures that could leave your organization open to cyberattacks. Access control mitigates the risk of insider threats by enforcing the principle of. What Is Access Control Threats.
From www.realtimenetworks.com
BattleTested 7 Access Control Best Practices What Is Access Control Threats Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. In the context of web. By controlling who or what has. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control is the application of. What Is Access Control Threats.
From accelerationeconomy.com
Why Is Broken Access Control OWASP's 1 Threat? What Is Access Control Threats Access control is the application of constraints on who or what is authorized to perform actions or access resources. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become. What Is Access Control Threats.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye What Is Access Control Threats Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control is the application of constraints on who or what is. What Is Access Control Threats.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know What Is Access Control Threats In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Inadequate access control measures that could leave your organization open to cyberattacks.. What Is Access Control Threats.
From cyberhoot.com
Access Control Mechanism CyberHoot What Is Access Control Threats Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Inadequate access control measures that could leave your organization open to cyberattacks. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. In a world where cyberattacks aren’t a matter. What Is Access Control Threats.
From slideplayer.com
ISA 400 Management of Information Security ppt download What Is Access Control Threats Access control is the application of constraints on who or what is authorized to perform actions or access resources. In the context of web. By controlling who or what has. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control minimizes the risk of authorized access to physical and computer systems, forming a. What Is Access Control Threats.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 What Is Access Control Threats Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is the application of constraints on who or what is authorized to perform actions or access resources. In the context of web. Access. What Is Access Control Threats.
From www.serviceasap.com
Is Your Commercial Access Control System Safe from Cyber Threats? What Is Access Control Threats Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is the application of constraints on who or what is authorized to perform actions or access resources. By controlling who or what has. Inadequate access control measures that could leave your organization open to cyberattacks. In a world where cyberattacks aren’t a matter. What Is Access Control Threats.
From thecyphere.com
Access Control Security Types Of Access Control What Is Access Control Threats Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is the application of constraints on who or what is authorized to perform actions or access resources. By controlling who or what has. Inadequate access control measures that could leave your organization open. What Is Access Control Threats.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model What Is Access Control Threats In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. By controlling who or what has. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Inadequate access control measures that could. What Is Access Control Threats.
From www.allblogthings.com
These 12 Cyber Threats Can Ruin Your Tech Company What Is Access Control Threats Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. In the context of web. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control minimizes the risk of authorized. What Is Access Control Threats.
From identitymanagementinstitute.org
System Access and Compliance Threats Identity Management Institute® What Is Access Control Threats In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access to. Inadequate access control measures that could leave your organization open to. What Is Access Control Threats.
From www.lockmanage.com
Types of Access Control Exploring Different Approaches to Security What Is Access Control Threats Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control is a security process that determines who can access certain. What Is Access Control Threats.
From www.slideshare.net
Asset, Vulnerability, Threat, Risk & Control What Is Access Control Threats Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. In the context of web. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control mitigates the risk of insider threats by enforcing the principle of least privilege,. What Is Access Control Threats.
From www.serviceasap.com
4 Security Threats Your Access Control System Helps Mitigate What Is Access Control Threats Inadequate access control measures that could leave your organization open to cyberattacks. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control mitigates. What Is Access Control Threats.
From www.scanvis-ai.com
Key elements of IoTenabled physical access control solutions for data What Is Access Control Threats Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what. What Is Access Control Threats.
From www.researchgate.net
Cybersecurity threats and concerns in the cloud platform. The major What Is Access Control Threats Inadequate access control measures that could leave your organization open to cyberattacks. In a world where cyberattacks aren’t a matter of “if” but “when,” access control has become the frontline defense against unauthorized access, data leaks, and it compliance nightmares. Access control mitigates the risk of insider threats by enforcing the principle of least privilege, ensuring users only have access. What Is Access Control Threats.