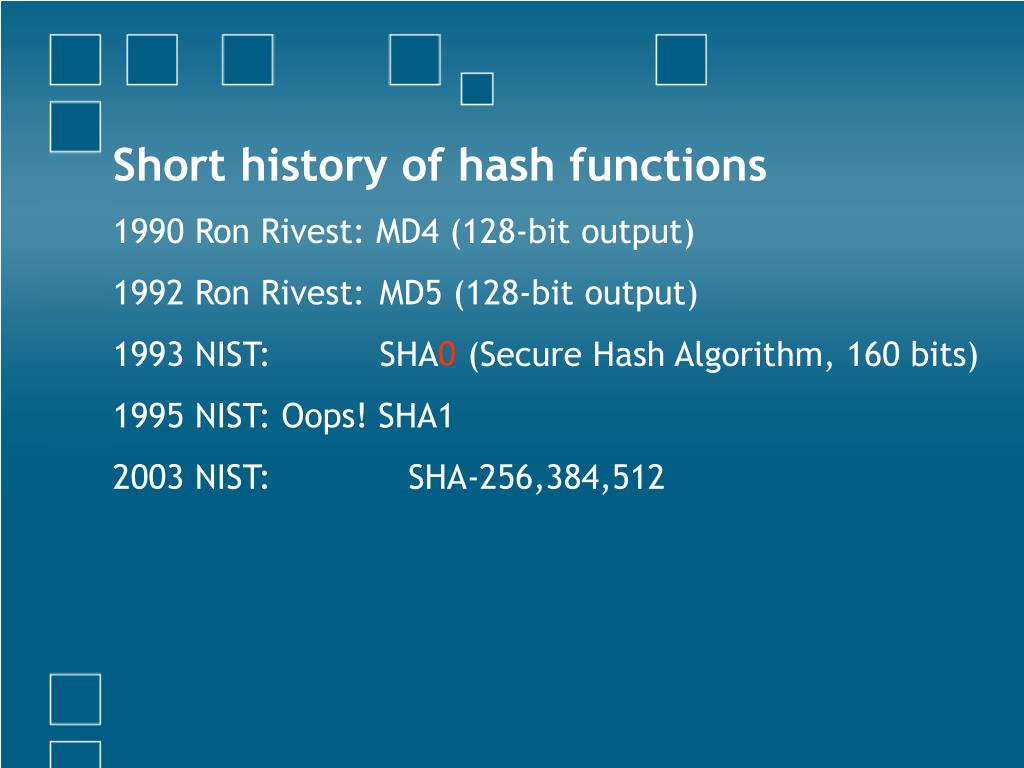
History Of Hash Functions . The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. Passwords), hash maps, bloom filters, and probably a few more. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. The years following world war ii were formative ones for electronic. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. This paper presents a brief overview of the. From the 64 candidates submitted by october 2008, 14 have made it to the second round. File integrity, verification of a secret without revealing the secret (i.e. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function.
from www.slideserve.com
The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. From the 64 candidates submitted by october 2008, 14 have made it to the second round. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. File integrity, verification of a secret without revealing the secret (i.e. Passwords), hash maps, bloom filters, and probably a few more. This paper presents a brief overview of the. The years following world war ii were formative ones for electronic. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging.
PPT Applications of SAT Solvers to Cryptanalysis of Hash Functions
History Of Hash Functions This paper presents a brief overview of the. This paper presents a brief overview of the. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. Passwords), hash maps, bloom filters, and probably a few more. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. File integrity, verification of a secret without revealing the secret (i.e. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. The years following world war ii were formative ones for electronic. From the 64 candidates submitted by october 2008, 14 have made it to the second round.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions File integrity, verification of a secret without revealing the secret (i.e. Passwords), hash maps, bloom filters, and probably a few more. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. From the. History Of Hash Functions.
From www.researchgate.net
Cryptographic hash function.... Download Scientific Diagram History Of Hash Functions This paper presents a brief overview of the. The years following world war ii were formative ones for electronic. File integrity, verification of a secret without revealing the secret (i.e. From the 64 candidates submitted by october 2008, 14 have made it to the second round. They excel at converting data into a hash, but reversing the hash to retrieve. History Of Hash Functions.
From www.slideserve.com
PPT Dictionaries and Hash Tables PowerPoint Presentation, free History Of Hash Functions Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. Passwords), hash maps, bloom filters, and probably a few more. The years following world war ii were formative ones. History Of Hash Functions.
From electriccoin.co
History of Hash Function Attacks Electric Coin Company History Of Hash Functions Passwords), hash maps, bloom filters, and probably a few more. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. File integrity, verification of a secret without revealing the secret (i.e. This paper presents a brief overview of the. From the 64 candidates submitted by october 2008, 14 have made. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. From the 64 candidates submitted by october 2008, 14 have made it to the second round. Passwords), hash maps, bloom filters, and probably. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions Passwords), hash maps, bloom filters, and probably a few more. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. They excel at converting data into a hash, but reversing the hash. History Of Hash Functions.
From medium.com
Generalities Of The Hash Functions (Part I) ALTCOIN MAGAZINE Medium History Of Hash Functions From the 64 candidates submitted by october 2008, 14 have made it to the second round. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. This paper presents a brief overview. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. File integrity, verification of a secret without revealing the secret (i.e. Passwords), hash maps, bloom filters, and probably a few more. The years following world war ii were formative ones for electronic. They excel at converting data into a. History Of Hash Functions.
From www.youtube.com
Hash Function YouTube History Of Hash Functions This paper presents a brief overview of the. Passwords), hash maps, bloom filters, and probably a few more. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. They excel at converting data. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions From the 64 candidates submitted by october 2008, 14 have made it to the second round. Passwords), hash maps, bloom filters, and probably a few more. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. File integrity, verification of a secret without revealing the secret (i.e. Here i’ll explore what led luhn. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions This paper presents a brief overview of the. Passwords), hash maps, bloom filters, and probably a few more. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. File integrity, verification of a. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions File integrity, verification of a secret without revealing the secret (i.e. This paper presents a brief overview of the. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function.. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions File integrity, verification of a secret without revealing the secret (i.e. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. Passwords), hash maps, bloom filters, and probably a few more. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly. History Of Hash Functions.
From www.slideserve.com
PPT Hash Table PowerPoint Presentation, free download ID3569725 History Of Hash Functions The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. Passwords), hash maps, bloom filters, and probably a few more. File integrity, verification of a secret without revealing the secret (i.e. The years. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. File integrity, verification of a secret without revealing the secret (i.e. This paper presents a brief overview of the. The years following world. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. Passwords), hash maps, bloom filters, and probably a few more. This paper presents a brief overview of the. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. File integrity, verification of. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions Passwords), hash maps, bloom filters, and probably a few more. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. This paper presents a brief overview of the. File integrity,. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions The years following world war ii were formative ones for electronic. File integrity, verification of a secret without revealing the secret (i.e. This paper presents a brief overview of the. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. From the 64 candidates submitted by october 2008, 14 have made it to. History Of Hash Functions.
From blog.pantherprotocol.io
What are cryptographic hash functions and how do they work? History Of Hash Functions They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. The years following world war ii were formative ones for electronic. Passwords), hash maps, bloom filters, and probably a few more. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the. History Of Hash Functions.
From cryptobook.nakov.com
Hash Functions GitBook History Of Hash Functions From the 64 candidates submitted by october 2008, 14 have made it to the second round. This paper presents a brief overview of the. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. The values returned by a hash function are called hash values, hash codes, digests, or. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions The years following world war ii were formative ones for electronic. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. Passwords), hash maps, bloom filters, and probably a few more. The disconnect. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. This paper presents a brief overview of the. The years following world war ii were formative ones for electronic.. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. From the 64 candidates submitted by october 2008, 14 have made it to the second round. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. Passwords), hash maps,. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. File integrity, verification of a secret without revealing the secret (i.e. This paper presents a brief overview of the. Passwords), hash maps, bloom. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. The years following world war ii were formative ones for electronic. From the 64 candidates submitted by october 2008, 14 have made it to the second round. Passwords), hash maps, bloom filters, and probably a few more. They excel at converting data into. History Of Hash Functions.
From www.researchgate.net
Classification of attacks on Hash Functions Download Scientific Diagram History Of Hash Functions Passwords), hash maps, bloom filters, and probably a few more. File integrity, verification of a secret without revealing the secret (i.e. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. From the 64 candidates submitted by october 2008, 14 have made it to the second round. The disconnect between theory and practice. History Of Hash Functions.
From www.youtube.com
Hash function YouTube History Of Hash Functions The years following world war ii were formative ones for electronic. They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. Passwords), hash maps, bloom filters, and probably a few more. File integrity, verification of a secret without revealing the secret (i.e. The disconnect between theory and practice of cryptographic. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. The years following world war ii were formative ones for electronic. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. They excel at converting data into a hash,. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. The years following world war ii were formative ones for electronic. File integrity, verification of a secret without revealing the secret (i.e. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. From. History Of Hash Functions.
From slideplayer.com
Lecture 4.1 Hash Functions Introduction ppt download History Of Hash Functions The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. The years following world war ii were formative ones for electronic. File integrity, verification of a secret without revealing the secret (i.e. Passwords), hash maps, bloom filters, and probably a few more. This paper presents a brief overview of the.. History Of Hash Functions.
From mavink.com
Types Of Hash Functions History Of Hash Functions This paper presents a brief overview of the. File integrity, verification of a secret without revealing the secret (i.e. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. From the 64 candidates submitted by october 2008, 14 have made it to the second round. The years following world war ii were formative. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. This paper presents a brief overview of the. The years following world war ii were formative ones for electronic. File integrity, verification of a secret without revealing the secret (i.e. From the 64 candidates submitted by october 2008, 14 have. History Of Hash Functions.
From www.slideserve.com
PPT SHA Hash Functions History & Current State PowerPoint History Of Hash Functions Passwords), hash maps, bloom filters, and probably a few more. File integrity, verification of a secret without revealing the secret (i.e. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. The years following world war ii were formative ones for electronic. From the 64 candidates submitted by october 2008,. History Of Hash Functions.
From www.slideserve.com
PPT Chapter 3 (C) Message Authentication and Hash Functions History Of Hash Functions The years following world war ii were formative ones for electronic. This paper presents a brief overview of the. Here i’ll explore what led luhn to the solution of a problem that didn’t yet exist—a solution called the hash function. Passwords), hash maps, bloom filters, and probably a few more. The values returned by a hash function are called hash. History Of Hash Functions.
From www.slideserve.com
PPT Applications of SAT Solvers to Cryptanalysis of Hash Functions History Of Hash Functions They excel at converting data into a hash, but reversing the hash to retrieve the original data is exceedingly challenging. This paper presents a brief overview of the. The years following world war ii were formative ones for electronic. The disconnect between theory and practice of cryptographic hash functions starts right in the beginning—in the very definition of hash. From. History Of Hash Functions.