Security Scan Qualys . app scanning (was) automate scanning in ci/cd. Find, fix security holes in web apps, apis. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Schedule web application scans to run automatically, on a regular basis. Scan your systems to identify vulnerabilities and understand your security posture. Consolidate & translate security & vulnerability findings from 3rd party tools. Quickly scan for known vulnerabilities.
from www.qualys.com
Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Quickly scan for known vulnerabilities. app scanning (was) automate scanning in ci/cd. Find, fix security holes in web apps, apis. Consolidate & translate security & vulnerability findings from 3rd party tools. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Schedule web application scans to run automatically, on a regular basis. Scan your systems to identify vulnerabilities and understand your security posture.
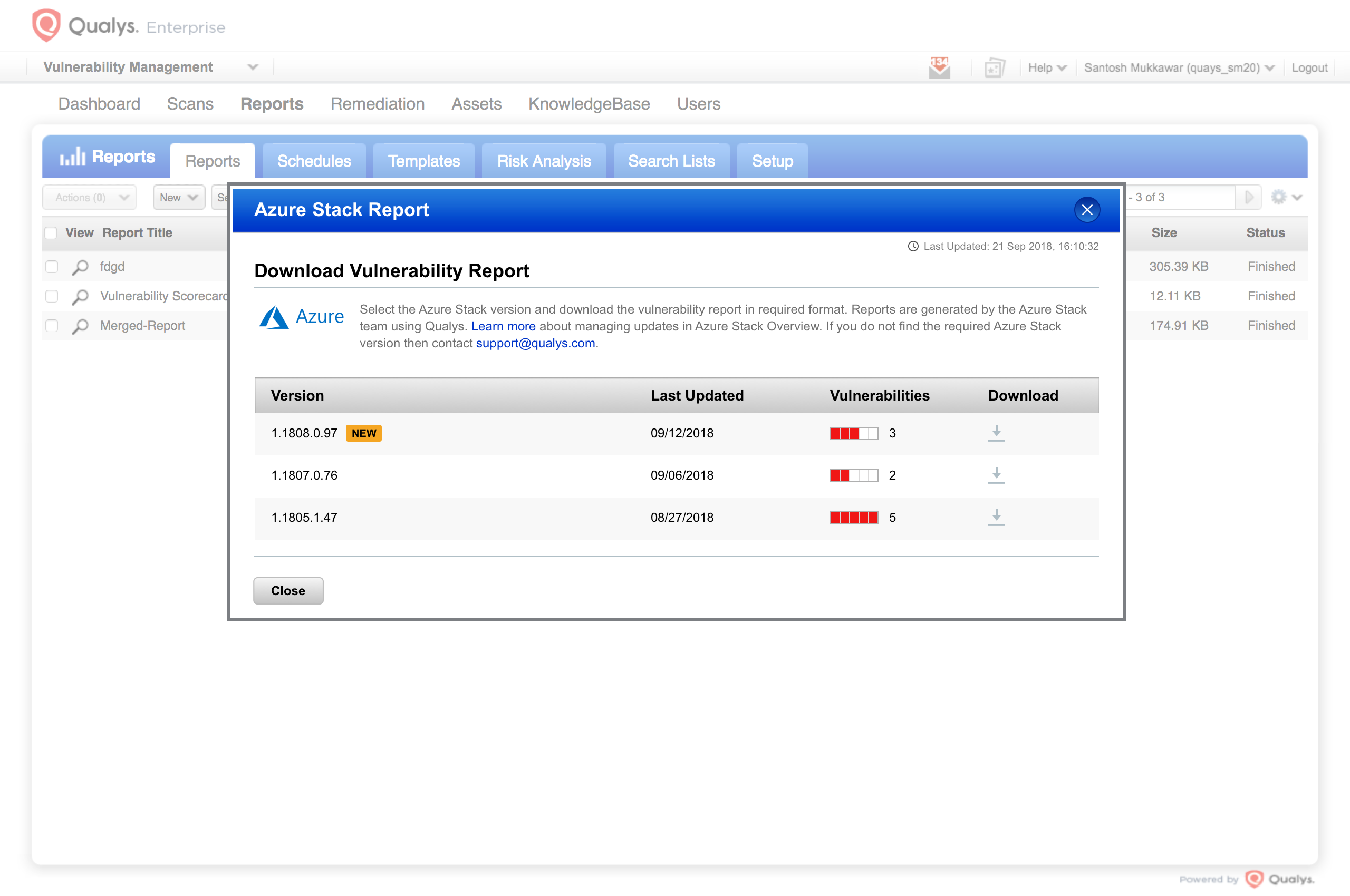
Qualys Delivers Security Built into Microsoft Azure’s Hybrid Cloud
Security Scan Qualys app scanning (was) automate scanning in ci/cd. app scanning (was) automate scanning in ci/cd. Scan your systems to identify vulnerabilities and understand your security posture. Schedule web application scans to run automatically, on a regular basis. Find, fix security holes in web apps, apis. Quickly scan for known vulnerabilities. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Consolidate & translate security & vulnerability findings from 3rd party tools.
From vimeo.com
Deploying Qualys Container Security in Build, Ship and Run phases on Vimeo Security Scan Qualys Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Scan your systems to identify vulnerabilities and understand your security posture. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Quickly scan for known vulnerabilities. app scanning (was) automate scanning in ci/cd. Schedule web application scans to. Security Scan Qualys.
From blog.qualys.com
New QualysGuard Express Lite for Small Businesses Qualys Security Blog Security Scan Qualys Consolidate & translate security & vulnerability findings from 3rd party tools. app scanning (was) automate scanning in ci/cd. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Scan your systems to identify vulnerabilities and understand your security posture. Quickly scan for known vulnerabilities. Schedule web application scans to run automatically, on a regular basis. Find, fix. Security Scan Qualys.
From www.real-sec.com
How to Install the Qualys Cloud Agent for Remote Workforce REAL security Security Scan Qualys Scan your systems to identify vulnerabilities and understand your security posture. Quickly scan for known vulnerabilities. Consolidate & translate security & vulnerability findings from 3rd party tools. app scanning (was) automate scanning in ci/cd. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Vulnerability scanning allows you to continuously. Security Scan Qualys.
From blog.qualys.com
Fingerprinting Applications and APIs using Qualys Application Scanning Qualys Security Security Scan Qualys Scan your systems to identify vulnerabilities and understand your security posture. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. app scanning (was) automate scanning in ci/cd. Schedule web application scans to run automatically, on a regular basis. Find, fix security holes in web apps, apis. Quickly scan for known vulnerabilities. Consolidate & translate security &. Security Scan Qualys.
From marketplace.visualstudio.com
Qualys IaC Security Visual Studio Marketplace Security Scan Qualys app scanning (was) automate scanning in ci/cd. Quickly scan for known vulnerabilities. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Consolidate & translate security & vulnerability findings from 3rd party tools. Find, fix security holes in web apps, apis. Schedule web application scans to run automatically, on a regular basis. Scan your systems to identify. Security Scan Qualys.
From www.qualys.com
Qualys Policy Compliance IT policy compliance app Qualys Security Scan Qualys Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Quickly scan for known vulnerabilities. Consolidate & translate security & vulnerability findings from 3rd party tools. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Scan your systems to identify vulnerabilities and understand your security posture. Schedule web. Security Scan Qualys.
From qualys.com
Application Security Scanning Qualys, Inc. Security Scan Qualys Schedule web application scans to run automatically, on a regular basis. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. app scanning (was) automate scanning in ci/cd. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Consolidate & translate security & vulnerability findings from 3rd party. Security Scan Qualys.
From www.qualys.com
Qualys Continuous Monitoring Network Security Tool Qualys, Inc. Security Scan Qualys Schedule web application scans to run automatically, on a regular basis. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Find, fix security holes in web apps, apis. Consolidate & translate security & vulnerability findings from 3rd party tools. Vulnerability scanning allows you to continuously detect software vulnerabilities across your. Security Scan Qualys.
From www.qualys.com
Qualys Application Scanning Qualys Security Scan Qualys Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Find, fix security holes in web apps, apis. app scanning (was) automate scanning in ci/cd. Scan your systems to identify vulnerabilities and understand your security posture. Schedule web application scans to run automatically, on a regular basis. Quickly scan for. Security Scan Qualys.
From www.qualys.com
Qualys Delivers Security Built into Microsoft Azure’s Hybrid Cloud Security Scan Qualys Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Schedule web application scans to run automatically, on a regular basis. Scan your systems to identify vulnerabilities and understand your security posture. app scanning (was) automate scanning in ci/cd. Consolidate & translate security & vulnerability findings from 3rd party tools. Find, fix security holes in web apps,. Security Scan Qualys.
From hackingviral.blogspot.com
Qualys BrowserCheck An Online Security Scanner HaViral Security Scan Qualys Schedule web application scans to run automatically, on a regular basis. Consolidate & translate security & vulnerability findings from 3rd party tools. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Find, fix security holes in web apps, apis. Quickly scan for known vulnerabilities. Scan your systems to identify vulnerabilities. Security Scan Qualys.
From www.qualys.com
Qualys Security Configuration Assessment (SCA) Qualys Security Scan Qualys Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Schedule web application scans to run automatically, on a regular basis. Find, fix security holes in web apps, apis. Quickly scan for known vulnerabilities. Consolidate & translate security & vulnerability findings from 3rd party tools. Scan your systems to identify vulnerabilities and understand your security posture. app. Security Scan Qualys.
From www.qualys.com
SECURE Seal Qualys, Inc. Security Scan Qualys Consolidate & translate security & vulnerability findings from 3rd party tools. Scan your systems to identify vulnerabilities and understand your security posture. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Schedule web application scans to run automatically, on a regular basis. app scanning (was) automate scanning in ci/cd.. Security Scan Qualys.
From blog.qualys.com
Builtin Runtime Security for Containers Qualys Security Blog Security Scan Qualys app scanning (was) automate scanning in ci/cd. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Schedule web application scans to run automatically, on a regular basis. Find, fix security holes in web apps, apis. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Consolidate &. Security Scan Qualys.
From www.qualys.com
Qualys Container Security (CS) Qualys, Inc. Security Scan Qualys Scan your systems to identify vulnerabilities and understand your security posture. Consolidate & translate security & vulnerability findings from 3rd party tools. Quickly scan for known vulnerabilities. Find, fix security holes in web apps, apis. app scanning (was) automate scanning in ci/cd. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their. Security Scan Qualys.
From msandbu.org
Azure Security Center and Qualys vulnerability scanning service Security Scan Qualys Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Find, fix security holes in web apps, apis. Consolidate & translate security & vulnerability findings from 3rd party tools. Quickly scan for known vulnerabilities. app scanning (was) automate scanning in ci/cd. Vulnerability scanning allows you to continuously detect software vulnerabilities. Security Scan Qualys.
From www.qualys.com
PCI ASV Compliance Application Qualys Security Scan Qualys app scanning (was) automate scanning in ci/cd. Schedule web application scans to run automatically, on a regular basis. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Consolidate & translate security & vulnerability findings from 3rd party. Security Scan Qualys.
From www.qualys.com
Qualys Application Scanning Qualys Security Scan Qualys Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Find, fix security holes in web apps, apis. Schedule web application scans to run automatically, on a regular basis. Consolidate & translate security & vulnerability findings from 3rd party tools. app scanning (was) automate scanning in ci/cd. Quickly scan for known vulnerabilities. Scan your systems to identify. Security Scan Qualys.
From www.qualys.com
Qualys Container Security (CS) Qualys, Inc. Security Scan Qualys Find, fix security holes in web apps, apis. Quickly scan for known vulnerabilities. Consolidate & translate security & vulnerability findings from 3rd party tools. app scanning (was) automate scanning in ci/cd. Schedule web application scans to run automatically, on a regular basis. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their. Security Scan Qualys.
From technofaq.org
Online Security Tools for Small Businesses Techno FAQ Security Scan Qualys app scanning (was) automate scanning in ci/cd. Find, fix security holes in web apps, apis. Consolidate & translate security & vulnerability findings from 3rd party tools. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Scan your systems to identify vulnerabilities and understand your security posture. Vulnerability scanning allows. Security Scan Qualys.
From docs.paloaltonetworks.com
Integrate IoT Security with Qualys Security Scan Qualys Scan your systems to identify vulnerabilities and understand your security posture. app scanning (was) automate scanning in ci/cd. Consolidate & translate security & vulnerability findings from 3rd party tools. Find, fix security holes in web apps, apis. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Automate the process of managing your saas apps, including global. Security Scan Qualys.
From blog.qualys.com
Expand Your Vulnerability & Patch Management Program to Mobile Devices with Qualys VMDR Qualys Security Scan Qualys Schedule web application scans to run automatically, on a regular basis. Consolidate & translate security & vulnerability findings from 3rd party tools. Find, fix security holes in web apps, apis. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Quickly scan for known vulnerabilities. Vulnerability scanning allows you to continuously. Security Scan Qualys.
From blog.qualys.com
Securing your Cloud and Container DevOps Pipeline Qualys Blog Security Scan Qualys Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Scan your systems to identify vulnerabilities and understand your security posture. Schedule web application scans to run automatically, on a regular basis. Find, fix security holes in web apps, apis. app scanning (was) automate scanning in ci/cd. Quickly scan for. Security Scan Qualys.
From blog.qualys.com
New QualysGuard Express Lite for Small Businesses Qualys Security Blog Security Scan Qualys Scan your systems to identify vulnerabilities and understand your security posture. Schedule web application scans to run automatically, on a regular basis. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Quickly scan for known vulnerabilities. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. app. Security Scan Qualys.
From blog.qualys.com
Extending your FedRAMP Program to Container Infrastructure with the Qualys Cloud Platform Security Scan Qualys Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. app scanning (was) automate scanning in ci/cd. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Quickly scan for known vulnerabilities. Schedule web application scans to run automatically, on a regular basis. Consolidate & translate security &. Security Scan Qualys.
From www.qualys.com
Qualys Security Configuration Assessment (SCA) Qualys Security Scan Qualys Schedule web application scans to run automatically, on a regular basis. Scan your systems to identify vulnerabilities and understand your security posture. app scanning (was) automate scanning in ci/cd. Quickly scan for known vulnerabilities. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Find, fix security holes in web apps, apis. Automate the process of managing. Security Scan Qualys.
From www.qualys.com
Qualys Application Scanning Qualys Security Scan Qualys Quickly scan for known vulnerabilities. Consolidate & translate security & vulnerability findings from 3rd party tools. Find, fix security holes in web apps, apis. app scanning (was) automate scanning in ci/cd. Schedule web application scans to run automatically, on a regular basis. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their. Security Scan Qualys.
From www.qualys.com
Qualys KCS A TotalCloud™ 2.0 Cloud Security Tool Security Posture Management (KSPM) Security Scan Qualys Quickly scan for known vulnerabilities. Schedule web application scans to run automatically, on a regular basis. Consolidate & translate security & vulnerability findings from 3rd party tools. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Scan your systems to identify vulnerabilities and understand your security posture. app scanning (was) automate scanning in ci/cd. Find, fix. Security Scan Qualys.
From blog.qualys.com
Securing Container Deployments with Qualys Qualys Security Blog Security Scan Qualys Schedule web application scans to run automatically, on a regular basis. Consolidate & translate security & vulnerability findings from 3rd party tools. Quickly scan for known vulnerabilities. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Find, fix. Security Scan Qualys.
From www.qualys.com
Application Security Scanning Qualys, Inc. Security Scan Qualys Consolidate & translate security & vulnerability findings from 3rd party tools. Schedule web application scans to run automatically, on a regular basis. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Quickly scan for known vulnerabilities. Find, fix security holes in web apps, apis. Automate the process of managing your saas apps, including global settings, user privileges,. Security Scan Qualys.
From www.cronup.com
Qualys Context XDR CronUp Ciberseguridad Security Scan Qualys Scan your systems to identify vulnerabilities and understand your security posture. Consolidate & translate security & vulnerability findings from 3rd party tools. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Find, fix security holes in web apps,. Security Scan Qualys.
From qualys.com
Application Security Scanning Qualys, Inc. Security Scan Qualys Quickly scan for known vulnerabilities. Scan your systems to identify vulnerabilities and understand your security posture. Consolidate & translate security & vulnerability findings from 3rd party tools. Find, fix security holes in web apps, apis. app scanning (was) automate scanning in ci/cd. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their. Security Scan Qualys.
From avleonov.com
Qualys authenticated scanning Alexander V. Leonov Security Scan Qualys Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Quickly scan for known vulnerabilities. app scanning (was) automate scanning in ci/cd. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Find, fix security holes in web apps, apis. Scan your systems to identify vulnerabilities and understand. Security Scan Qualys.
From avleonov.com
Using Qualys Virtual Scanner Appliance Alexander V. Leonov Security Scan Qualys Quickly scan for known vulnerabilities. Find, fix security holes in web apps, apis. Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. Scan your systems to identify vulnerabilities and understand your security posture. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Consolidate & translate security &. Security Scan Qualys.
From www.qualys.com
PCI ASV Compliance Application Qualys Security Scan Qualys Vulnerability scanning allows you to continuously detect software vulnerabilities across your network. app scanning (was) automate scanning in ci/cd. Automate the process of managing your saas apps, including global settings, user privileges, licenses, files, and their security and. Find, fix security holes in web apps, apis. Consolidate & translate security & vulnerability findings from 3rd party tools. Schedule web. Security Scan Qualys.