Mac Access List . Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. This chapter includes the following sections: You can use acls to control which. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls are acls that filter traffic using information in the layer 2 header of each packet.
from cypol.weebly.com
You can use acls to control which. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. This chapter includes the following sections: Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet.
How to get microsoft access on a mac cypol
Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. This chapter includes the following sections:
From support.apple.com
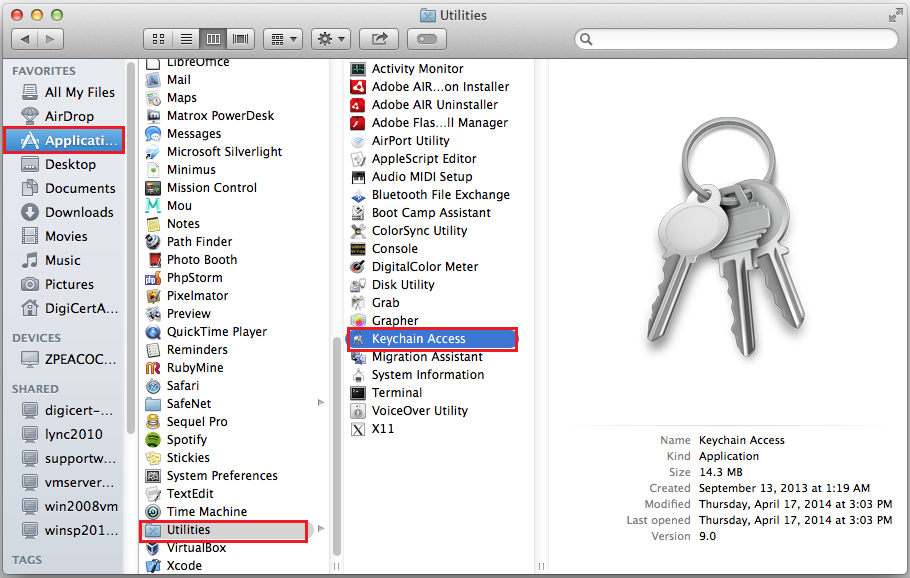
What is Keychain Access on Mac? Apple Support Mac Access List You can use acls to control which. This chapter includes the following sections: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls have the following prerequisites: Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls. Mac Access List.
From superuser.com
macos Connect to another Mac via Terminal? Super User Mac Access List This chapter includes the following sections: You can use acls to control which. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of. Mac Access List.
From support.intego.com
VirusBarrier Full Disk Access Not Granted in macOS and RealTime Scanner Fails to Load Intego Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. This chapter includes the following sections: Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac access lists help control access based. Mac Access List.
From support.apple.com
What is Keychain Access on Mac? Apple Support Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. You can use acls. Mac Access List.
From setapp.com
How to access your Mac remotely Complete tutorial Mac Access List This chapter includes the following sections: Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls. Mac Access List.
From rtsracing.weebly.com
Mac access list for mikrotik rtsracing Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. You can use acls to control which. Mac acls are acls that filter traffic using information in the layer 2 header. Mac Access List.
From travelerroom.weebly.com
Add permissions for mac to launch program travelerroom Mac Access List Mac acls have the following prerequisites: This chapter includes the following sections: Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac acls. Mac Access List.
From www.idownloadblog.com
5 ways to access system report on your Mac Mac Access List You can use acls to control which. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls have the following prerequisites: Mac acls are acls that filter traffic using. Mac Access List.
From www.youtube.com
8 6 3 MAC Access List YouTube Mac Access List Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. This chapter includes the following sections: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls have the following prerequisites: You can use acls to control which. Mac acls. Mac Access List.
From www.youtube.com
mac access list lec9 YouTube Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access. Mac Access List.
From www.scribd.com
11MAC Access Table Configuration Commands PDF Network Architecture Protocols Mac Access List Mac acls have the following prerequisites: You can use acls to control which. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. This chapter includes the following sections: Mac acls. Mac Access List.
From www.idownloadblog.com
How to use Voice Control to navigate your Mac Mac Access List Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. This chapter includes the following sections: Mac access lists help control access based on the unique mac addresses of devices,. Mac Access List.
From www.howtoisolve.com
How to Give Full Disk Access & Full Permissions on Mac (Sonoma) Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. This chapter includes the. Mac Access List.
From appleinsider.com
The macOS Monterey user's guide to Keychain Access password management AppleInsider Mac Access List This chapter includes the following sections: Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. You can use acls to control which. Mac acls. Mac Access List.
From australiadelta.weebly.com
Cisco mac address access list australiadelta Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. This chapter includes the following sections: You can use acls to control which. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls are acls that filter traffic using. Mac Access List.
From cypol.weebly.com
How to get microsoft access on a mac cypol Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls have the following prerequisites: This chapter includes the following sections: You can use acls to control which. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls. Mac Access List.
From mcgrp.ru
DLink DGS6608 [471/1106] mac accesslist Mac Access List Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. This chapter includes the following sections: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac acls have the following prerequisites: Mac acls. Mac Access List.
From tecnomaquia.qualitypoolsboulder.com
How to List Every Terminal Command on Mac OS Mac Access List This chapter includes the following sections: Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac acls are acls that filter traffic using. Mac Access List.
From iboysoft.com
Access & Customize Context Menu (Rightclick Menu) on Mac Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. This chapter includes the following sections: You can use acls to control which. Mac acls have the following prerequisites: Mac access lists help control access based. Mac Access List.
From macpaw.com
Steps to access your Mac remotely Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. This chapter includes the following sections: Mac acls have the following prerequisites: You can use acls to control which. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls. Mac Access List.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download ID2786600 Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. This chapter includes the following sections: Mac acls are acls that filter traffic using information in the layer 2 header of. Mac Access List.
From www.macworld.com
How to use file sharing on your Mac Macworld Mac Access List You can use acls to control which. This chapter includes the following sections: Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using. Mac Access List.
From support.apple.com
Check your Apple ID device list to find where you're signed in Apple Support Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. You can use acls to control which. This chapter includes the following sections: Mac acls have the following prerequisites: Mac acls. Mac Access List.
From support.apple.com
Use network locations on Mac Apple Support Mac Access List Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac acls are acls that filter traffic using information in the layer 2 header. Mac Access List.
From webxpertzone.com
How to Enable Screen Sharing Permissions on a Mac XpertZone Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac access lists help control access based on the unique mac addresses of. Mac Access List.
From mikrotik-training.ru
Access листы в RouterOS курсы Романа Козлова Mac Access List You can use acls to control which. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls have the following prerequisites: This chapter includes the following sections: Mac access lists help control access based. Mac Access List.
From 9to5mac.com
Mac How to check app permissions for camera, mic, Photos 9to5Mac Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls have the following prerequisites: You can use acls to control which. This chapter includes the following sections: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based. Mac Access List.
From mcgrp.ru
TpLink T1700X16TS V3 [680/916] Mac access list 10 name acl_10 Mac Access List Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls are acls that filter traffic using information in the layer 2 header of. Mac Access List.
From www.howtoisolve.com
How to Give Full Disk Access & Full Permissions on Mac (Sonoma) Mac Access List This chapter includes the following sections: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as. Mac Access List.
From www.intego.com
Mac and iOS Keychain Tutorial How Apple's iCloud Keychain Works The Mac Security Blog Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac access lists help control access based on the unique mac addresses of. Mac Access List.
From www.cisco.com
Configure MACBased Access Control List (ACL) and Access Control Entry (ACE) on a Managed Switch Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls have the. Mac Access List.
From www.howtoisolve.com
How to Give Full Disk Access & Full Permissions on Mac (Sonoma) Mac Access List You can use acls to control which. This chapter includes the following sections: Mac acls have the following prerequisites: Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls. Mac Access List.
From budibase.com
RoleBased Access Control Ultimate Guide Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. This chapter includes the following sections: Mac acls have the following prerequisites: Mac access lists help control access based on the unique mac addresses of devices, allowing or denying network access as per predefined. Mac acls. Mac Access List.
From support.keriocontrol.gfi.com
Import MAC address to Permit list KerioControl Support Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. This chapter includes the following sections: Mac access lists help control access based on the unique mac addresses of. Mac Access List.
From support.keriocontrol.gfi.com
Import MAC address to Permit list KerioControl Support Mac Access List Mac acls are acls that filter traffic using information in the layer 2 header of each packet. You can use acls to control which. Mac acls are acls that filter traffic using information in the layer 2 header of each packet. Mac acls have the following prerequisites: Mac access lists help control access based on the unique mac addresses of. Mac Access List.