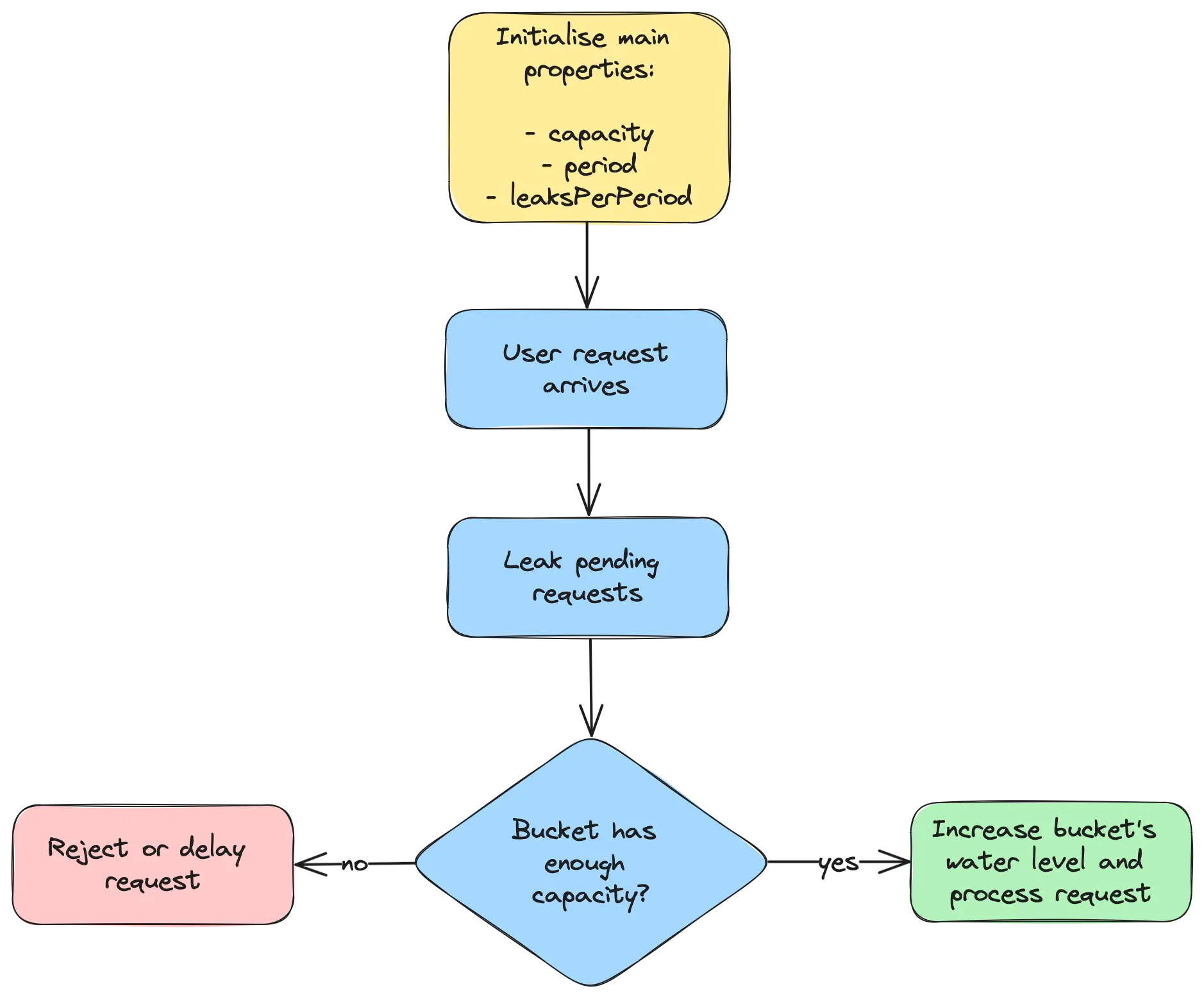
Leaky Bucket Algorithm Approach . a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm is a network traffic management mechanism. what is the leaky bucket algorithm? It ensures that the flow of.
from www.rdiachenko.com
the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. It ensures that the flow of. what is the leaky bucket algorithm? a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic.
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm
Leaky Bucket Algorithm Approach a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It ensures that the flow of. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. what is the leaky bucket algorithm?
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Approach The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket. Leaky Bucket Algorithm Approach.
From www.researchgate.net
Selectivity of the conventional leaky bucket algorithm, the fuzzy leaky Leaky Bucket Algorithm Approach It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. The leaky bucket algorithm is a network traffic management mechanism. what. Leaky Bucket Algorithm Approach.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Approach It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm is a traffic. Leaky Bucket Algorithm Approach.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Approach a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. what is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism. . Leaky Bucket Algorithm Approach.
From www.studocu.com
Leaky Bucket Algorithm Leaky Bucket A leaking bucket is a simple Leaky Bucket Algorithm Approach It ensures that the flow of. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. The leaky. Leaky Bucket Algorithm Approach.
From www.youtube.com
Traffic Shaping Leaky Bucket Token Bucket Improve QoS Computer Leaky Bucket Algorithm Approach the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. The leaky bucket algorithm is a network traffic. Leaky Bucket Algorithm Approach.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Approach the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky. Leaky Bucket Algorithm Approach.
From www.youtube.com
leaky bucket algorithm congestion control networking Bhanu Priya Leaky Bucket Algorithm Approach what is the leaky bucket algorithm? the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm is a network traffic management mechanism. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out. Leaky Bucket Algorithm Approach.
From www.youtube.com
Leaky bucket algorithm in congestion control algorithm YouTube Leaky Bucket Algorithm Approach what is the leaky bucket algorithm? the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket rate. Leaky Bucket Algorithm Approach.
From www.youtube.com
12. Leaky Bucket Algorithm Program VTU 5th Sem Computer Network Lab Leaky Bucket Algorithm Approach what is the leaky bucket algorithm? the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket, where data is added at a. Leaky Bucket Algorithm Approach.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Approach the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket rate limiting algorithm utilizes. Leaky Bucket Algorithm Approach.
From www.researchgate.net
Responsiveness of the conventional leaky bucket algorithm, the fuzzy Leaky Bucket Algorithm Approach The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. what is the leaky bucket algorithm? the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the. Leaky Bucket Algorithm Approach.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Approach It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage. Leaky Bucket Algorithm Approach.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID3009018 Leaky Bucket Algorithm Approach the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket, where data is added at a. Leaky Bucket Algorithm Approach.
From www.youtube.com
leaky bucket algorithm traffic shaping in computer networks 2021 Leaky Bucket Algorithm Approach what is the leaky bucket algorithm? the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm provides an elegant solution to the problem. Leaky Bucket Algorithm Approach.
From in.pinterest.com
Leaky Bucket Algorithm educlick Algorithm, Computer network Leaky Bucket Algorithm Approach It ensures that the flow of. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm provides an elegant solution to the problem of. Leaky Bucket Algorithm Approach.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm Approach the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. what is the leaky bucket algorithm? the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. . Leaky Bucket Algorithm Approach.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Approach It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket rate limiting algorithm utilizes a fifo (first in,. Leaky Bucket Algorithm Approach.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Approach the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is. Leaky Bucket Algorithm Approach.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm Approach It ensures that the flow of. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the. Leaky Bucket Algorithm Approach.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm Approach It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm provides an elegant solution to the problem. Leaky Bucket Algorithm Approach.
From www.geeksforgeeks.org
Leaky Bucket Algorithm Computer Networks Leaky Bucket Algorithm Approach the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is a traffic shaping. Leaky Bucket Algorithm Approach.
From www.linqz.io
Leaky/Token bucket algorithm for flow control Learn INQuiZitively Leaky Bucket Algorithm Approach a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. It ensures that the flow of. The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket rate limiting algorithm. Leaky Bucket Algorithm Approach.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky Bucket Algorithm Approach the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket. Leaky Bucket Algorithm Approach.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Approach the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a network traffic management mechanism. what is the leaky bucket algorithm? a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. . Leaky Bucket Algorithm Approach.
From www.techtarget.com
What is the leaky bucket algorithm? TechTarget Definition Leaky Bucket Algorithm Approach the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. It ensures that the flow of. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm provides an elegant solution to the problem. Leaky Bucket Algorithm Approach.
From giosfbamr.blob.core.windows.net
Leaky Bucket Algorithm Advantages at Annie Jackson blog Leaky Bucket Algorithm Approach The leaky bucket algorithm is a network traffic management mechanism. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. what is the leaky bucket algorithm? a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. It. Leaky Bucket Algorithm Approach.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Approach The leaky bucket algorithm is a network traffic management mechanism. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky. Leaky Bucket Algorithm Approach.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Leaky Bucket Algorithm Approach what is the leaky bucket algorithm? the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. a leaky bucket algorithm is a method used. Leaky Bucket Algorithm Approach.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Approach The leaky bucket algorithm is a network traffic management mechanism. what is the leaky bucket algorithm? the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady. Leaky Bucket Algorithm Approach.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Approach the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity. Leaky Bucket Algorithm Approach.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm Approach It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm is a traffic shaping mechanism used in. Leaky Bucket Algorithm Approach.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky Bucket Algorithm Approach It ensures that the flow of. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket, where data is added at a variable. Leaky Bucket Algorithm Approach.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Approach a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. the leaky bucket algorithm is a simple yet effective way to. Leaky Bucket Algorithm Approach.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm Approach the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. It ensures that the flow of. the leaky bucket algorithm provides an elegant solution to the problem of. Leaky Bucket Algorithm Approach.