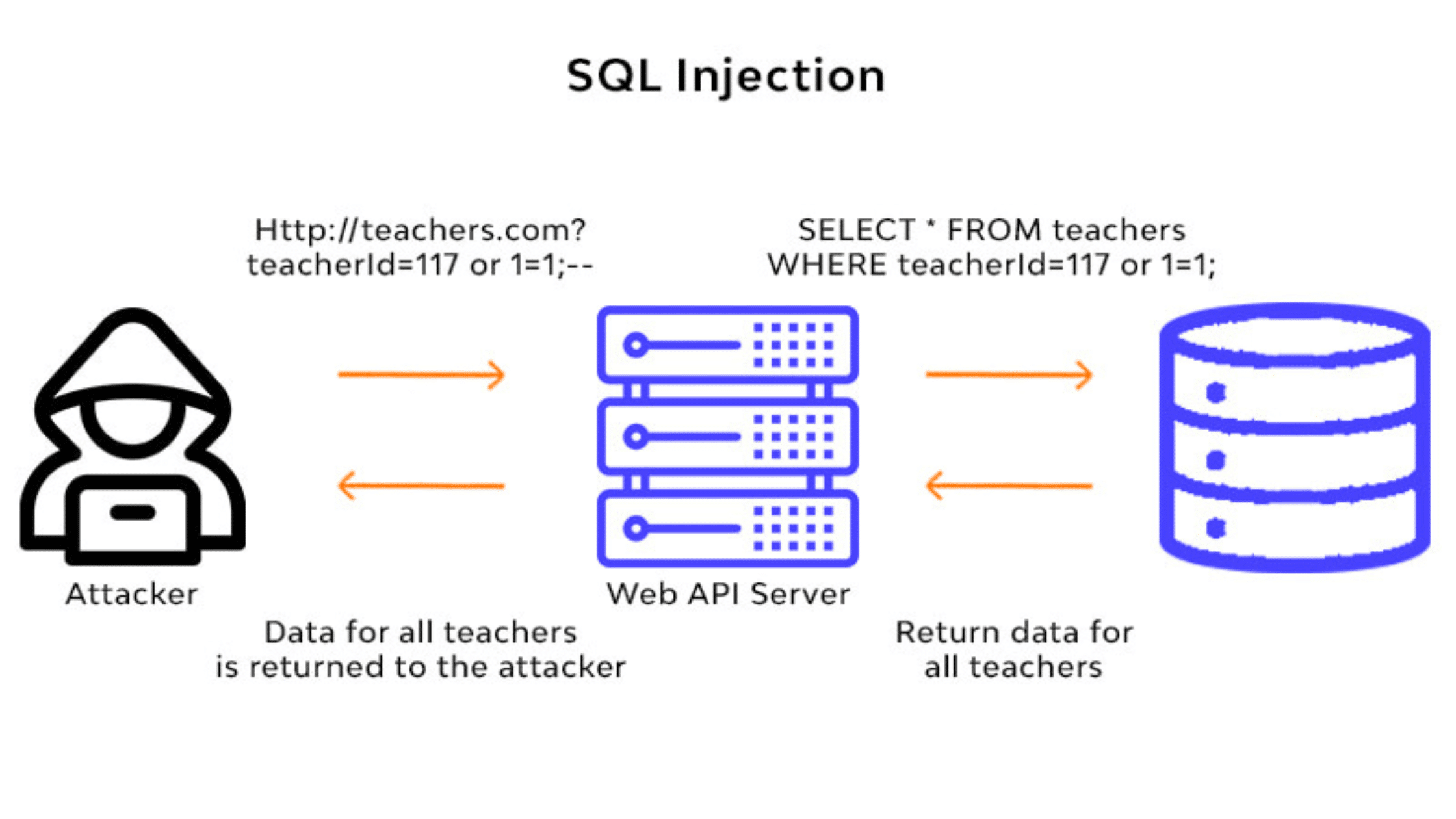
Injection Types Hacking . A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. injection attacks can allow hackers to gain access to the internals of your system. We'll show you exactly how they work and how to prevent them. The following are some examples of distinct kinds of injection attacks: injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the.
from demonblack.fr
code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. The following are some examples of distinct kinds of injection attacks: A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. injection attacks can allow hackers to gain access to the internals of your system. We'll show you exactly how they work and how to prevent them. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts.
Injection SQL Tous savoir sur cette technique de hacking
Injection Types Hacking in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. The following are some examples of distinct kinds of injection attacks: We'll show you exactly how they work and how to prevent them. injection attacks can allow hackers to gain access to the internals of your system. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended.
From buranprofessor.weebly.com
Database Hacking Using Sql Injection Attack buranprofessor Injection Types Hacking in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. The following are some examples of distinct kinds of injection attacks: We'll show. Injection Types Hacking.
From www.youtube.com
Ethical hacking for beginners SQL Injections YouTube Injection Types Hacking The following are some examples of distinct kinds of injection attacks: We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. injection attacks can allow hackers to gain access to the internals of your system. code injection is the general term for attack types which consist of injecting code that. Injection Types Hacking.
From www.youtube.com
What is SQL injection? How it Works How to Hack site Using SQL Injection Types Hacking injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. code injection is the general term for attack types which consist of. Injection Types Hacking.
From hakin9.org
SQL Injection Attacks Preview Hakin9 IT Security Magazine Injection Types Hacking We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they. Injection Types Hacking.
From www.youtube.com
Injection Attacks Types and how to prevent them YouTube Injection Types Hacking We'll show you exactly how they work and how to prevent them. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. The following are some examples of distinct kinds of injection attacks:. Injection Types Hacking.
From codecrypt76.com
SQL Injection Attack Hacker Challenge Injection Types Hacking code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. A large part of vulnerabilities that exist in web applications can. Injection Types Hacking.
From www.youtube.com
SQL Injection Hack Explained Better WordPress Security WP Learning Injection Types Hacking injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. injection attacks can allow hackers to gain access to the internals of your system. A large part of vulnerabilities. Injection Types Hacking.
From www.sectigo.com
Understanding SQL Injection Attacks Sectigo® Official Injection Types Hacking A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. We'll show you exactly how they work and how to prevent them. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. in this post, we covered the essentials of injection attacks, from their. Injection Types Hacking.
From techsphinx.com
Hacking for Beginners Command Injection Vulnerability TechSphinx Injection Types Hacking The following are some examples of distinct kinds of injection attacks: injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. injection attacks can allow hackers to gain access to the internals of your system. in this post, we covered the essentials of injection attacks, from their types and. Injection Types Hacking.
From www.homage.sg
Injection 101 Overview, Types, Common Uses & Risks Homage Injection Types Hacking We'll show you exactly how they work and how to prevent them. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. A large. Injection Types Hacking.
From www.youtube.com
SQL Injection hacking tutorial (Hack / Counter Hack) YouTube Injection Types Hacking A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. injection attacks can allow hackers to gain access to the internals of your system. . Injection Types Hacking.
From www.youtube.com
ethical hacking injections in website hacking YouTube Injection Types Hacking injection attacks can allow hackers to gain access to the internals of your system. The following are some examples of distinct kinds of injection attacks: We'll show you exactly how they work and how to prevent them. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can. Injection Types Hacking.
From www.youtube.com
Hacking a game with DLL injection [Game Hacking 101] YouTube Injection Types Hacking A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. injection attacks can allow hackers to gain access to the internals of your system. The following are some examples of distinct kinds of injection attacks: injection attacks refer to a range of tactics used by hackers to trick web applications into performing. Injection Types Hacking.
From www.insecure.in
SQL Injection Attack Types, Examples and Prevention Injection Types Hacking code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. injection attacks can allow hackers to gain access to the internals of your system. We'll show you exactly how they work and how to prevent them. injection attacks refer to a range of tactics used by hackers. Injection Types Hacking.
From mavink.com
Types Of Injection Sites Injection Types Hacking in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. injection attacks can allow hackers to gain access to the internals of. Injection Types Hacking.
From www.louisbouchard.ai
What is Prompt Injection? "Prompt Hacking" Explained Injection Types Hacking injection attacks can allow hackers to gain access to the internals of your system. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on. Injection Types Hacking.
From hakin9.org
Hacking with SQL Injections (W8) Hakin9 IT Security Magazine Injection Types Hacking We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. injection attacks can allow hackers to gain access to the internals of your system. We'll show you exactly how they work and. Injection Types Hacking.
From www.youtube.com
HACKING WEBSITES WITH PHP CODE INJECTION (beginners tutorial) YouTube Injection Types Hacking We'll show you exactly how they work and how to prevent them. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by. Injection Types Hacking.
From appsecco.com
Hacking apps using NoSQL Injection Injection Types Hacking in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. code injection is the general term for attack types which consist of injecting. Injection Types Hacking.
From desklib.com
SQL Injection Types, Prevention Techniques and Countermeasures Injection Types Hacking A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. The following are some examples of distinct kinds of injection attacks: We'll show you exactly how they work and how to prevent them. code injection. Injection Types Hacking.
From www.youtube.com
Ethical hacking concepts SQL Injections Demonstrated YouTube Injection Types Hacking in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. injection attacks can allow hackers to gain access to the internals of your system. The following are some examples of distinct kinds of injection attacks: We also outlined effective prevention and. Injection Types Hacking.
From avxhm.se
Complete SQL Injection Hacking Course Beginner to Advanced! / AvaxHome Injection Types Hacking in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. We'll show you exactly how they work and how to prevent them. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. injection. Injection Types Hacking.
From www.vecteezy.com
Types of Injections on White Background 363582 Vector Art at Vecteezy Injection Types Hacking injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. injection attacks can allow hackers to gain access to the internals of your system. The following are some examples of distinct kinds of injection. Injection Types Hacking.
From systemweakness.com
SQL Injection Attacks. What is a SQL Injection attack? by ADITYA Injection Types Hacking injection attacks can allow hackers to gain access to the internals of your system. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. The following are some examples of distinct kinds of injection attacks: We'll show you exactly how they work and how to prevent them. in this. Injection Types Hacking.
From msatechnosoft.in
Hacking Types Purpose Hackers SQL Injection SQLMAP Injection Types Hacking The following are some examples of distinct kinds of injection attacks: in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. We'll show you. Injection Types Hacking.
From www.freecodecamp.org
How to Crack Hashes with Hashcat — a Practical Pentesting Guide Injection Types Hacking We'll show you exactly how they work and how to prevent them. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. The following are some. Injection Types Hacking.
From infosecwriteups.com
Hack With SQL Injection Attacks! DVWA medium security — StackZero by Injection Types Hacking We'll show you exactly how they work and how to prevent them. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. in this post, we covered the essentials. Injection Types Hacking.
From www.youtube.com
Injection Attacks Ethical Hacking Beginner To advance Machinery Injection Types Hacking injection attacks can allow hackers to gain access to the internals of your system. We'll show you exactly how they work and how to prevent them. A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity. Injection Types Hacking.
From www.youtube.com
site hacking though Android SQL Injection With Proof YouTube Injection Types Hacking injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. The following are some examples of distinct kinds of injection attacks: injection attacks can allow hackers to gain access to the internals of your system. in this post, we covered the essentials of injection attacks, from their types and. Injection Types Hacking.
From www.pinterest.com
Injection types coolguides Medical assistant student, Medical Injection Types Hacking code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. The following are some examples of distinct kinds of injection attacks: A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. in this post, we covered the essentials of injection attacks, from. Injection Types Hacking.
From www.youtube.com
Hack CRLF Injection Demonstration YouTube Injection Types Hacking A large part of vulnerabilities that exist in web applications can be classified as injection vulnerabilities. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. The following are some examples of distinct kinds of injection attacks: We also outlined effective prevention and mitigation strategies, noting the critical role. Injection Types Hacking.
From www.youtube.com
Types Of Injection and Their Site Route of Injection Injection Injection Types Hacking injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. The following are some examples of distinct kinds of injection attacks: in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. We'll show. Injection Types Hacking.
From www.youtube.com
[Security] SQL Injection Hacking 1 YouTube Injection Types Hacking injection attacks can allow hackers to gain access to the internals of your system. We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. code injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the. A large part of vulnerabilities that. Injection Types Hacking.
From demonblack.fr
Injection SQL Tous savoir sur cette technique de hacking Injection Types Hacking injection attacks can allow hackers to gain access to the internals of your system. We'll show you exactly how they work and how to prevent them. injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended. code injection is the general term for attack types which consist of injecting. Injection Types Hacking.
From thehackingguide.blogspot.com
Hacking Guide and Tips and Tricks Hacking a website with SQL injection Injection Types Hacking We also outlined effective prevention and mitigation strategies, noting the critical role of ai in enhancing cybersecurity efforts. We'll show you exactly how they work and how to prevent them. in this post, we covered the essentials of injection attacks, from their types and targets to the devastating impacts they can have on data and system security. injection. Injection Types Hacking.