Network Command And Control . A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. In this attack, the attacker. Command and control (c2) servers are used by attackers to communicate with compromised systems. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. 42 rows command and control. The adversary is trying to communicate with compromised systems to control them. To profit for as long as possible from a malware. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation.
from www.codingninjas.com
The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. 42 rows command and control. To profit for as long as possible from a malware. A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. Command and control (c2) servers are used by attackers to communicate with compromised systems. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. In this attack, the attacker. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation.
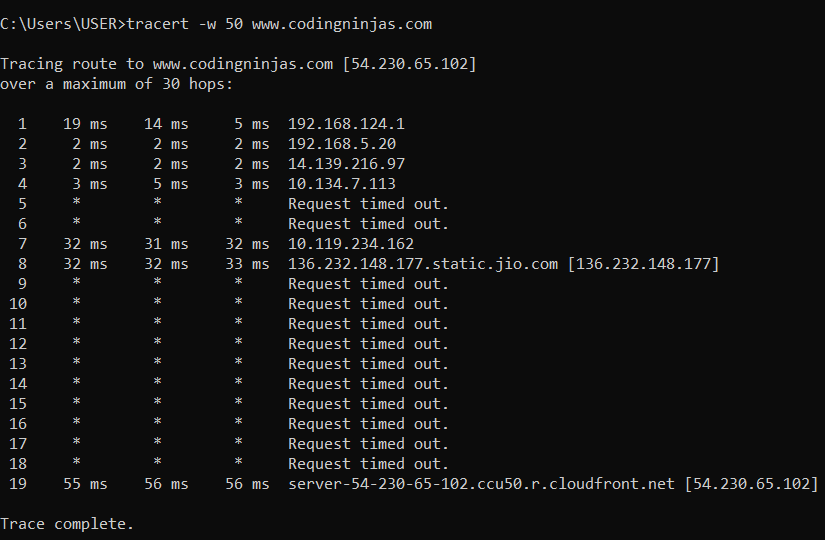
Basic Commands for Networking Coding Ninjas
Network Command And Control To profit for as long as possible from a malware. Command and control (c2) servers are used by attackers to communicate with compromised systems. A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. To profit for as long as possible from a malware. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. In this attack, the attacker. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. The adversary is trying to communicate with compromised systems to control them. 42 rows command and control. A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network.
From warriormaven.com
Joint All Domain Command & Control Powers Unified Army, Navy, Air Force Network Command And Control Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. A. Network Command And Control.
From www.n-study.com
BGP Route Summary network command How the BGP works NStudy Network Command And Control Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. 42 rows command and control. The adversary is trying to communicate with compromised systems to control them. The specific mechanisms vary greatly between attacks, but c2 generally consists of one. Network Command And Control.
From www.moralepatcharmory.com
IBCS Northrop Delivers New Army Missile Defense Command Post Morale Network Command And Control C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. The adversary is trying to communicate with compromised systems to control them. Command and control (c2) servers are used by attackers to communicate with compromised systems. 42 rows command and control. In this attack, the attacker. A command and control attack is a. Network Command And Control.
From dev.to
Top 5 Basic Networking Commands In Windows DEV Community Network Command And Control In this attack, the attacker. 42 rows command and control. Command and control (c2) servers are used by attackers to communicate with compromised systems. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. Command and control infrastructure, also known. Network Command And Control.
From www.definethecloud.net
SDN Centralized Network Command and Control Define The Cloud Network Command And Control A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. Command and control (c2) servers are used by attackers to communicate with compromised systems. 42 rows command and control. In this attack, the attacker. The adversary is trying to communicate with compromised systems to control them. C&c. Network Command And Control.
From www.educba.com
Networking Commands Top 9 Commands of Networking Network Command And Control A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. Command and control infrastructure, also known as c2 or c&c, is the set of tools. Network Command And Control.
From www.kinaxis.com
Intelligent, EndtoEnd Supply Chain Control I Kinaxis [en] Network Command And Control A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. 42 rows command and control. To. Network Command And Control.
From www.myxxgirl.com
Basic Networking Commands Explained With Examples My XXX Hot Girl Network Command And Control A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. C&c (also known as c2) is a method that cybercriminals use to communicate. Network Command And Control.
From www.pinterest.com
The tracert command is a Command Prompt command which is used to get Network Command And Control Command and control (c2) servers are used by attackers to communicate with compromised systems. 42 rows command and control. A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. The adversary is trying to communicate with compromised systems to control them. To profit for as. Network Command And Control.
From www.geeksforgeeks.org
Networking Commands For Troubleshooting Windows Network Command And Control A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. The adversary is trying to communicate with compromised systems to control them. 42 rows command and control. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that. Network Command And Control.
From www.nationstates.net
NationStates Dispatch Islamican Army Modernization Program Network Command And Control A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. 42 rows command and control. In this attack, the attacker. C&c (also. Network Command And Control.
From www.youtube.com
Top 5 basic networking commands YouTube Network Command And Control Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. To. Network Command And Control.
From www.studocu.com
Basic Network Commands Basic Network Commands TRACEPATH • Displays Network Command And Control Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. To profit for as long as possible from a malware. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use. Network Command And Control.
From javarevisited.blogspot.com
Top 10 basic networking commands in linux/unix Examples Network Command And Control To profit for as long as possible from a malware. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. 42 rows command and control. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. A command and control attack is. Network Command And Control.
From study.com
Networking CommandLine Tools Types & Uses Lesson Network Command And Control The adversary is trying to communicate with compromised systems to control them. Command and control (c2) servers are used by attackers to communicate with compromised systems. 42 rows command and control. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. To profit for as long as possible from a malware. The specific. Network Command And Control.
From www.studypool.com
SOLUTION 10 basic networking commands explained with examples Studypool Network Command And Control 42 rows command and control. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. C&c. Network Command And Control.
From www.scribd.com
Understanding Network Commands PDF Protocols Network Command And Control A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. The adversary is trying to communicate with compromised systems to control them. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised. Network Command And Control.
From cheatography.com
Windows Command Cheat Sheet by boogie Download free Network Command And Control To profit for as long as possible from a malware. Command and control (c2) servers are used by attackers to communicate with compromised systems. The adversary is trying to communicate with compromised systems to control them. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue. Network Command And Control.
From www.lockheedmartin.com
3 Keys to Enabling MultiDomain Operations for a Secure Future Network Command And Control C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. 42 rows command and control. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. A c2 attack is a cyberattack that allows. Network Command And Control.
From gridinsoft.com
Command and Control [C&C] Server Definition Gridinsoft Network Command And Control The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. In this attack, the attacker. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. The adversary is trying to communicate with compromised systems to control them. A command and control. Network Command And Control.
From www.atatus.com
15 Best Linux Networking Commands and Scripts You Should Know Network Command And Control A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. To profit for as long as possible from a malware. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. The adversary is. Network Command And Control.
From www.securityinformed.com
Modern CommandAndControl Systems For Event Monitoring, Data Storage Network Command And Control Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. To profit for as long as possible from a malware. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices. Network Command And Control.
From mungfali.com
Windows Command Cheat Sheet PDF Network Command And Control A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. 42 rows command and control. To profit for as long as possible from a malware. In this attack, the attacker. Command and control attacks, also known as c2 and c&c attacks, are a form of. Network Command And Control.
From www.definethecloud.net
SDN Centralized Network Command and Control Define The Cloud Network Command And Control 42 rows command and control. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. To profit for as long as possible from. Network Command And Control.
From www.softpost.org
Network commands in windows command prompt Network Command And Control Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. In this attack, the attacker. 42 rows command and control. Command and control (c2) servers are used by attackers to communicate with compromised systems. To profit for as long as possible. Network Command And Control.
From surajmukhia.blogspot.com
Basic Networking Commands in Linux Network Command And Control Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. Command and control (c2) servers. Network Command And Control.
From www.youtube.com
Basic Networking commands Beginners commands for Network Network Command And Control To profit for as long as possible from a malware. A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. 42 rows command and control. Command and control (c2) servers are used by attackers to communicate with compromised systems. Command and control infrastructure, also known. Network Command And Control.
From www.researchgate.net
SDN Centralized Network Command and Control Download Scientific Diagram Network Command And Control A c2 attack is a cyberattack that allows an attacker to take control of a compromised machine and use it to carry out malicious activities. Command and control (c2) servers are used by attackers to communicate with compromised systems. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in. Network Command And Control.
From www.codingninjas.com
Basic Commands for Networking Coding Ninjas Network Command And Control A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. Command and control (c2) servers are used by attackers to communicate with compromised systems. 42 rows command and control. Command. Network Command And Control.
From www.networkingsignal.com
Network Troubleshooting Commands 14 Useful Commands Network Command And Control 42 rows command and control. Command and control (c2) servers are used by attackers to communicate with compromised systems. In this attack, the attacker. A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. The specific mechanisms vary greatly between attacks, but c2 generally consists of one. Network Command And Control.
From www.youtube.com
Some CMD Commands Every Windows User Should Know Basic Networking Network Command And Control Command and control attacks, also known as c2 and c&c attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. Command. Network Command And Control.
From www.codingninjas.com
Basic Commands for Networking Coding Ninjas Network Command And Control To profit for as long as possible from a malware. C&c (also known as c2) is a method that cybercriminals use to communicate with compromised devices within. The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. Command and control infrastructure, also known as c2 or c&c, is. Network Command And Control.
From www.comparitech.com
Network Troubleshooting Commands Guide Windows, Mac & Linux Network Command And Control The specific mechanisms vary greatly between attacks, but c2 generally consists of one or more covert communication channels between devices in a. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. The adversary is trying to communicate with compromised systems. Network Command And Control.
From www.codingninjas.com
Basic Commands for Networking Coding Ninjas Network Command And Control Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. In this attack, the attacker. The adversary is. Network Command And Control.
From www.neoti.com
Control Room Displays Command Center Video Walls Network Command And Control 42 rows command and control. A command and control attack is a type of attack that involves tools to communicate with and control an infected machine or network. Command and control infrastructure, also known as c2 or c&c, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. To profit for. Network Command And Control.