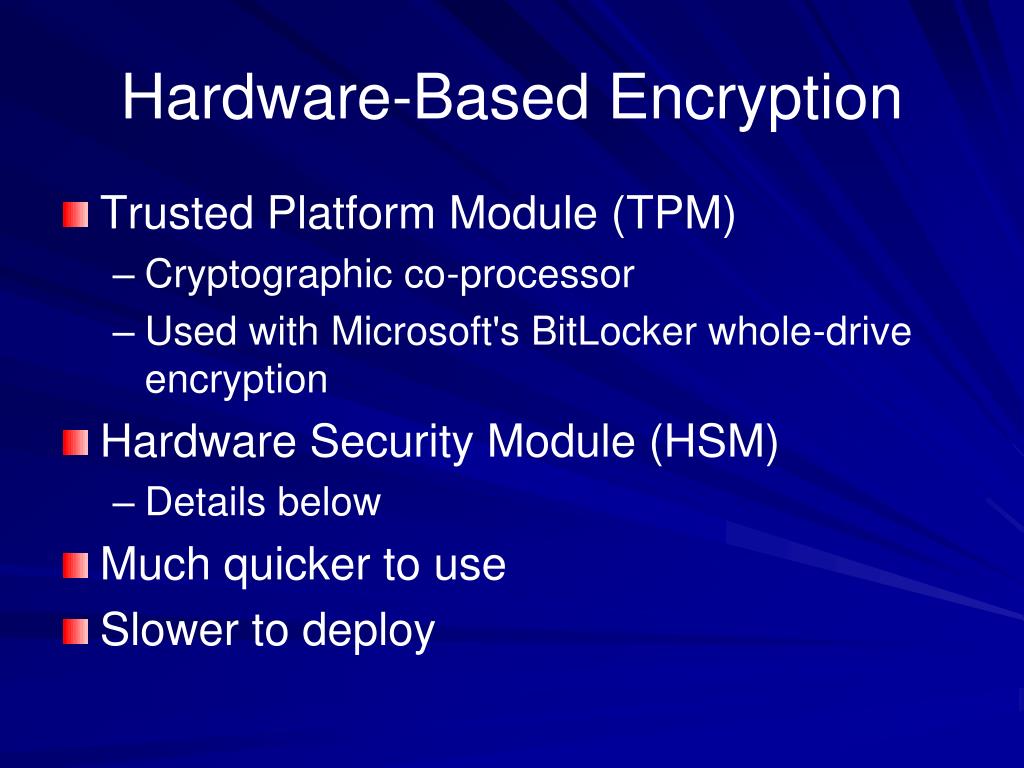
Hardware-Based Encryption Example . in today’s digital age, data security is more critical than ever. Seds have an onboard aes. At the heart of hardware, encryption is a separate processor dedicated to the task of. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption.
from www.slideserve.com
hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. Seds have an onboard aes. At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals alike are turning to encryption.
PPT Ch 5 Securing Hosts and Data PowerPoint Presentation, free
Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor dedicated to the task of.
From jessicaletitia.blogspot.com
Cryptography JessicaLetitia Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From gitlabcommitvirtual2021.com
Hardware encryption LabVirtual 2.0 Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals alike are turning to encryption. Seds have an onboard aes. in today’s digital age, data security. Hardware-Based Encryption Example.
From dxofweczu.blob.core.windows.net
How Does Hardware Encryption Work at Emilia Cox blog Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security is more critical than ever. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. Seds have an onboard aes. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From us.norton.com
What is encryption? How it works + types of encryption Norton Hardware-Based Encryption Example Seds have an onboard aes. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From www.youtube.com
Hardwarebased Encryption CompTIA Security+ SY0401 4.4 YouTube Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor. Hardware-Based Encryption Example.
From www.youtube.com
28 Hardware Based Encryption YouTube Hardware-Based Encryption Example in today’s digital age, data security is more critical than ever. Seds have an onboard aes. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption. At the heart of hardware, encryption is a separate processor. Hardware-Based Encryption Example.
From www.simplilearn.com
AES Encryption Secure Data with Advanced Encryption Standard Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. in today’s digital age, data security is more critical than ever. Seds have an onboard aes. At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From www.slideserve.com
PPT Comptia Security+ PowerPoint Presentation, free download ID9270633 Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. Seds have an onboard aes. With cyber threats looming large, businesses and individuals alike are turning to encryption. in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor. Hardware-Based Encryption Example.
From geekflare.com
Hardware Encryption What It Is and Why You Need It Geekflare Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. At the heart of hardware, encryption is a separate processor dedicated to the task of. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From m2pfintech.com
Cryptographic Keys and Hardware Security Modules An IntroductionM2P Hardware-Based Encryption Example in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor dedicated to the task of. Seds have an onboard aes. With cyber threats looming large, businesses and individuals alike are turning to encryption. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices. Hardware-Based Encryption Example.
From brightlineit.com
Understanding Encryption Key Management for Businesses Brightline Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption. At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security is more critical than ever.. Hardware-Based Encryption Example.
From www.trentonsystems.com
Your AllinOne Guide to SelfEncrypting Drives (SEDs) Hardware-Based Encryption Example With cyber threats looming large, businesses and individuals alike are turning to encryption. Seds have an onboard aes. At the heart of hardware, encryption is a separate processor dedicated to the task of. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. in today’s digital age, data security. Hardware-Based Encryption Example.
From everydaycyber.net
What is 256 Bit Encryption? EveryDayCyber Hardware-Based Encryption Example With cyber threats looming large, businesses and individuals alike are turning to encryption. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security is more critical than ever.. Hardware-Based Encryption Example.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals alike are turning to encryption. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices. Hardware-Based Encryption Example.
From www.certauri.com
Unveiling the Best HardwareBased Encryption Devices Hardware-Based Encryption Example Seds have an onboard aes. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals alike are turning to encryption. At the heart of hardware, encryption is a separate processor dedicated to the task of. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices. Hardware-Based Encryption Example.
From www.researchgate.net
(PDF) Hardware based encryption for wireless networks Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security is more critical than ever. Seds have an onboard aes. With cyber threats looming large, businesses and individuals alike are turning to encryption. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices. Hardware-Based Encryption Example.
From www.stratign.com
Hardware Based Encryption Device Stratign Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From thecustomizewindows.com
Methods of Encryption in Cloud Object Storage OpenStack & IBM Cloud Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals alike are turning to encryption. in today’s digital age, data security is more critical than ever. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data.. Hardware-Based Encryption Example.
From nl.transcend-info.com
AES Encryption Transcend Information, Inc. Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. in today’s digital age, data security is more critical than ever. Seds have an onboard aes. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From www.youtube.com
Software Vs Hardware Based Encryption DIY in 5 Ep 156 YouTube Hardware-Based Encryption Example in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals alike are turning to encryption. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data.. Hardware-Based Encryption Example.
From learn.g2.com
What Does Encryption Mean and Why Is It Important? Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security is more critical than ever. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption.. Hardware-Based Encryption Example.
From www.youtube.com
Understanding Hardwarebased Encryption CompTIA Security+ SY0301 4 Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From vpn-investigation.com
What is AES256 bit encryption VPN Investigate Hardware-Based Encryption Example Seds have an onboard aes. in today’s digital age, data security is more critical than ever. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From www.highgo.ca
The difference in five modes in the AES encryption algorithm Highgo Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals alike are turning to encryption.. Hardware-Based Encryption Example.
From www.slideserve.com
PPT Ch 5 Securing Hosts and Data PowerPoint Presentation, free Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption. in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor dedicated to the task of.. Hardware-Based Encryption Example.
From www.nepalshovit.com.np
CryptographyIntroduction 5OBIT Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. Seds have an onboard aes. At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals alike are turning to encryption. in today’s digital age, data security. Hardware-Based Encryption Example.
From dxofweczu.blob.core.windows.net
How Does Hardware Encryption Work at Emilia Cox blog Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals alike are turning to encryption. Seds have an onboard aes. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices. Hardware-Based Encryption Example.
From omninet.io
Hardware Encryption Modules for the SMB My Digital Shield Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption. Seds have an onboard aes. in today’s digital age, data security. Hardware-Based Encryption Example.
From carreersupport.com
What is Symmetric Key Encryption? A Simple Explanation Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals alike are turning to encryption. At the heart of hardware, encryption is a separate processor. Hardware-Based Encryption Example.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Hardware-Based Encryption Example hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. Seds have an onboard aes. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals alike are turning to encryption. At the heart of hardware, encryption is a separate processor. Hardware-Based Encryption Example.
From www.proofpoint.com
What is Encryption? Definition, Types & More Proofpoint US Hardware-Based Encryption Example in today’s digital age, data security is more critical than ever. Seds have an onboard aes. With cyber threats looming large, businesses and individuals alike are turning to encryption. At the heart of hardware, encryption is a separate processor dedicated to the task of. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices. Hardware-Based Encryption Example.
From www.youtube.com
aes tutorial, advanced encryption standard, fips 197 YouTube Hardware-Based Encryption Example Seds have an onboard aes. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor dedicated to the task of. With cyber threats looming large, businesses and individuals. Hardware-Based Encryption Example.
From www.pufsecurity.com
The Advanced Encryption Standard(AES) Technology PUFsecurity Hardware-Based Encryption Example Seds have an onboard aes. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. With cyber threats looming large, businesses and individuals alike are turning to encryption. At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security. Hardware-Based Encryption Example.
From www.otherarticles.com
Hardware Encryption Vs Software Encryption A Comprehensive Guide Hardware-Based Encryption Example With cyber threats looming large, businesses and individuals alike are turning to encryption. Seds have an onboard aes. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices to encrypt and decrypt data. in today’s digital age, data security is more critical than ever. At the heart of hardware, encryption is a separate processor. Hardware-Based Encryption Example.
From www.thesslstore.com
Cryptographic Keys 101 What They Are & How They Secure Data Hashed Hardware-Based Encryption Example At the heart of hardware, encryption is a separate processor dedicated to the task of. in today’s digital age, data security is more critical than ever. With cyber threats looming large, businesses and individuals alike are turning to encryption. Seds have an onboard aes. hardware encryption refers to using specialized cryptographic processors or modules built into hardware devices. Hardware-Based Encryption Example.