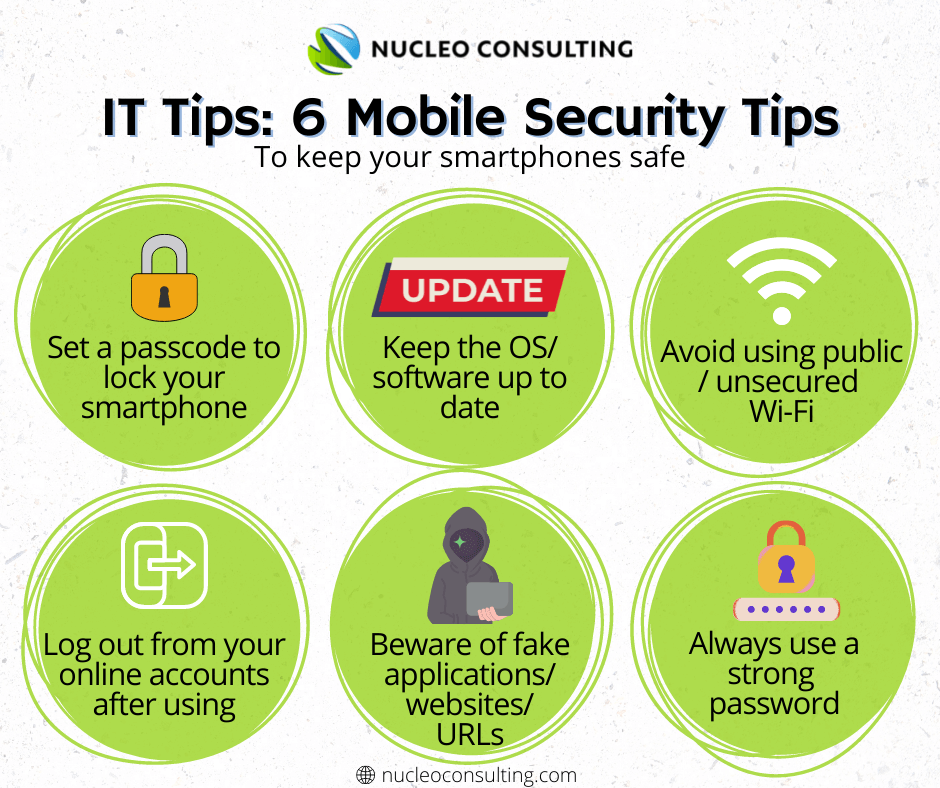
Security Controls For Mobile Devices . When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide covers the ins and outs of mobile device usage in the. This guide offers a consistent. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures.
from www.nucleoconsulting.com
Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide covers the ins and outs of mobile device usage in the. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide offers a consistent.
Keeping I.T. Safe Mobile Devices Nucleo Consulting
Security Controls For Mobile Devices This guide covers the ins and outs of mobile device usage in the. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide offers a consistent. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. This guide covers the ins and outs of mobile device usage in the. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist.
From www.f5.com
What Are Security Controls? Security Controls For Mobile Devices This guide offers a consistent. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and.. Security Controls For Mobile Devices.
From dbapress.org
A Look at the Mobile Devices and Mobile Security DBA Press Security Controls For Mobile Devices While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. This guide covers the ins and outs of mobile device usage in the. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. Security concerns inherent to the usage of. Security Controls For Mobile Devices.
From today.duke.edu
How to Secure Your Mobile Device Duke Today Security Controls For Mobile Devices This guide offers a consistent. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. While many of the core security concerns. Security Controls For Mobile Devices.
From thecyphere.com
What Is Mobile Device Security? Securing Your Mobile Devices Security Controls For Mobile Devices This guide offers a consistent. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide covers the ins and outs of mobile device usage in the. While many of the core security concerns of enterprise. Security Controls For Mobile Devices.
From blog.totalprosource.com
Five Threats to Your Mobile Device Security & How to Protect Your Data Security Controls For Mobile Devices When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide covers the ins and outs of mobile device usage in the. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. While many of the core security concerns of enterprise it systems are shared by mobile devices. Security Controls For Mobile Devices.
From www.securitymagazine.com
Mobile Credentials for Access Control—Everything Has Changed 20191007 Security Magazine Security Controls For Mobile Devices When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. This guide offers a. Security Controls For Mobile Devices.
From purplesec.us
Types Of Security Controls Explained Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. This guide offers a consistent. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. To. Security Controls For Mobile Devices.
From blog.abt.com
Best Practices for Mobile Device Security The Bolt Security Controls For Mobile Devices When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide covers the ins and outs of mobile device usage in. Security Controls For Mobile Devices.
From www.pinterest.com
Mobile Security Best Practices Mobile security, Security training, Byod Security Controls For Mobile Devices To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide covers the ins and outs of mobile device usage in the. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. This guide offers a consistent. When it. Security Controls For Mobile Devices.
From blog.techliance.com
Best App Security Practices to Follow in 2023 Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. This guide offers a consistent.. Security Controls For Mobile Devices.
From betanews.com
Five best practices for securing mobile devices and everything they touch Security Controls For Mobile Devices This guide covers the ins and outs of mobile device usage in the. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide offers a consistent. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. While many of the core security concerns of enterprise. Security Controls For Mobile Devices.
From www.trainerbubble.com
Mobile Device Security Training Video Download Now IT Security Security Controls For Mobile Devices While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. When it comes to mobile. Security Controls For Mobile Devices.
From www.compuquip.com
3 Ways to Improve Mobile Device Security to Protect Your Enterprise Security Controls For Mobile Devices This guide offers a consistent. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. To. Security Controls For Mobile Devices.
From dokumen.tips
(PDF) Guidelines for Managing and Securing Mobile Devices in Security Controls For Mobile Devices This guide offers a consistent. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures.. Security Controls For Mobile Devices.
From www.le-vpn.com
Best Mobile Security App for Android, iOS, Windows. Le VPN Security Controls For Mobile Devices To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. This guide offers a consistent. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. While many of the core security concerns. Security Controls For Mobile Devices.
From www.headspin.io
Essential Steps For Mobile Application Security Testing Security Controls For Mobile Devices To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide offers a consistent. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges. Security Controls For Mobile Devices.
From www.infoguardsecurity.com
How to Ensure Mobile Device Security in Your Organization Cyber Security Solutions, Compliance Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. This guide offers a consistent. To. Security Controls For Mobile Devices.
From www.device42.com
Network Security Critical Security Controls Security Controls For Mobile Devices To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. This guide covers the ins and outs of mobile device usage in the. While many of the core security concerns of enterprise it systems are shared by mobile. Security Controls For Mobile Devices.
From mobilityhelpdesk.com
Mobility Device Security Best Practices Mobility Help Desk Security Controls For Mobile Devices This guide offers a consistent. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide covers the ins and outs of mobile device usage in the. While many of the core security concerns of enterprise. Security Controls For Mobile Devices.
From anthillonline.com
Mobile security and how to protect yourself Security Controls For Mobile Devices To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide covers the ins and outs of mobile device usage in. Security Controls For Mobile Devices.
From www.dexlabanalytics.com
Cyber Security Today Curing Big Mobile Security Holes with Small Steps Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. To address these threats, this publication. Security Controls For Mobile Devices.
From www.slideserve.com
PPT Mobile Device Security PowerPoint Presentation, free download ID6907116 Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. This guide covers the ins and outs of mobile device usage in the. This guide offers a consistent. To address these threats,. Security Controls For Mobile Devices.
From www.slidemake.com
Mobile Device Security Presentation Security Controls For Mobile Devices This guide offers a consistent. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide covers the ins and outs. Security Controls For Mobile Devices.
From uniserveit.com
Mobile Security Best Practices Uniserve IT Solutions Security Controls For Mobile Devices To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide covers the ins and outs of mobile device usage in the. This guide offers a consistent. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. Security concerns inherent to the usage of mobile devices. Security Controls For Mobile Devices.
From www.techbusket.com
Mobile Security The Essential Steps to Take Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. This guide offers a consistent. This. Security Controls For Mobile Devices.
From consultancybrown318.weebly.com
Lookout Mobile Security Premium Key consultancybrown Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. This guide covers the ins and outs of mobile device usage in the. This guide offers a consistent. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. To address these threats, this publication describes technologies and strategies that. Security Controls For Mobile Devices.
From www.slideserve.com
PPT Mobile Device Security PowerPoint Presentation, free download ID3482794 Security Controls For Mobile Devices To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide covers the ins and outs of mobile device usage in the. This guide offers a consistent. While many of the core security concerns of enterprise. Security Controls For Mobile Devices.
From www.nucleoconsulting.com
Keeping I.T. Safe Mobile Devices Nucleo Consulting Security Controls For Mobile Devices This guide covers the ins and outs of mobile device usage in the. This guide offers a consistent. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. Security concerns. Security Controls For Mobile Devices.
From cguit.blogspot.com
CGU Tech Buzz Mobile Security Best Practices Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. While many of the core security concerns of enterprise it systems are. Security Controls For Mobile Devices.
From www.letsbemates.com.au
Mobile Security Tips How to Secure Your Network & Device Security Controls For Mobile Devices While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide offers a consistent. Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures.. Security Controls For Mobile Devices.
From www.fortinet.com
Significance of Endpoint Security for Mobile Devices Security Controls For Mobile Devices This guide covers the ins and outs of mobile device usage in the. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. This guide offers a consistent. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. Security concerns inherent. Security Controls For Mobile Devices.
From www.vectorstock.com
Mobile security infographic 10 steps concept Vector Image Security Controls For Mobile Devices This guide offers a consistent. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. When it comes to mobile devices, however, there are unique security challenges for organizations to. Security Controls For Mobile Devices.
From www.nogentech.org
10 Mobile Device Security Best Practices for Businesses Security Controls For Mobile Devices This guide covers the ins and outs of mobile device usage in the. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide offers a consistent. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. When it. Security Controls For Mobile Devices.
From slideplayer.com
Chapter 10. Mobile Device Security ppt download Security Controls For Mobile Devices Security concerns inherent to the usage of mobile devices are explored alongside mitigations and countermeasures. When it comes to mobile devices, however, there are unique security challenges for organizations to mitigate. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. This guide covers the ins and outs of mobile device usage in. Security Controls For Mobile Devices.
From www.zimperium.com
Mobile Is Another Endpoint CIS Critical Security Controls for Mobile Zimperium Security Controls For Mobile Devices This guide covers the ins and outs of mobile device usage in the. While many of the core security concerns of enterprise it systems are shared by mobile devices and their management systems, unique challenges exist. To address these threats, this publication describes technologies and strategies that can be used as countermeasures and. When it comes to mobile devices, however,. Security Controls For Mobile Devices.