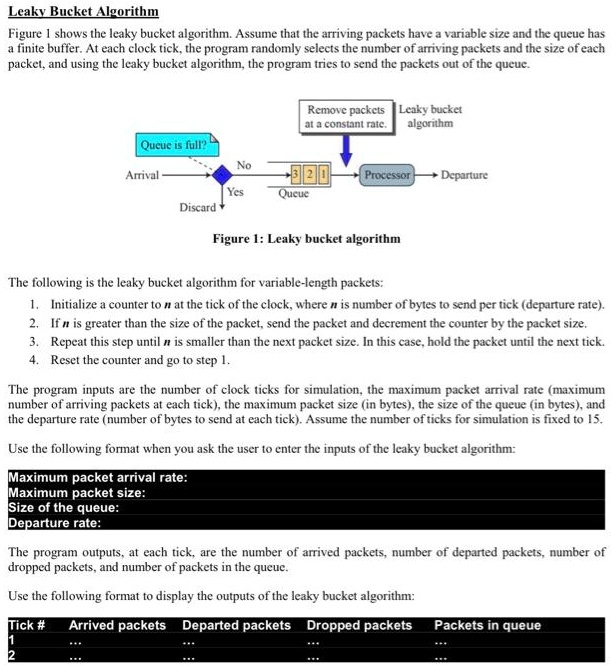
Leaky Bucket Algorithm Simulation . Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us imagine a. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The algorithm can also be used. Summarize findings in a report. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic.
from www.numerade.com
Summarize findings in a report. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Step 1 − let us imagine a. The algorithm can also be used. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic.
SOLVED Write a C++ program to simulate the behavior of the leaky bucket. Leaky Bucket Algorithm
Leaky Bucket Algorithm Simulation We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. The algorithm can also be used. Step 1 − let us imagine a. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Summarize findings in a report.
From www.slideserve.com
PPT Principles of Congestion Control PowerPoint Presentation, free download ID8677065 Leaky Bucket Algorithm Simulation Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The algorithm can also be used. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Step 1 − let us imagine a. The leaky bucket rate limiting algorithm. Leaky Bucket Algorithm Simulation.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and closed loop) YouTube Leaky Bucket Algorithm Simulation Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. We use fast simulation methods, based on importance sampling, to efficiently estimate. Leaky Bucket Algorithm Simulation.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Simulation The algorithm can also be used. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Step 1 − let us imagine a. Summarize findings in a report. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first. Leaky Bucket Algorithm Simulation.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Simulation Step 1 − let us imagine a. The algorithm can also be used. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Summarize findings in a report. The. Leaky Bucket Algorithm Simulation.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Simulation We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Step 1. Leaky Bucket Algorithm Simulation.
From www.youtube.com
Leaky And Token Bucket Algorithms YouTube Leaky Bucket Algorithm Simulation Step 1 − let us imagine a. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes.. Leaky Bucket Algorithm Simulation.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Algorithms API7.ai Leaky Bucket Algorithm Simulation The algorithm can also be used. Step 1 − let us imagine a. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic.. Leaky Bucket Algorithm Simulation.
From slideplayer.com
Congestion Control Algorithms ppt download Leaky Bucket Algorithm Simulation Summarize findings in a report. The algorithm can also be used. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us imagine a. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. We use fast simulation methods, based. Leaky Bucket Algorithm Simulation.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Simulation We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Leaky bucket algorithm mainly controls the total. Leaky Bucket Algorithm Simulation.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Simulation Step 1 − let us imagine a. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network.. Leaky Bucket Algorithm Simulation.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Simulation Summarize findings in a report. Step 1 − let us imagine a. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The algorithm can also be used. Analyze. Leaky Bucket Algorithm Simulation.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky Bucket Algorithm Simulation Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Step 1 − let us imagine a.. Leaky Bucket Algorithm Simulation.
From www.geeksforgeeks.org
Rate Limiting Algorithms System Design Leaky Bucket Algorithm Simulation Summarize findings in a report. The algorithm can also be used. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket is used to implement traffic. Leaky Bucket Algorithm Simulation.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Simulation Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Summarize findings in a report. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Leaky bucket algorithm mainly controls the total amount. Leaky Bucket Algorithm Simulation.
From www.numerade.com
SOLVED Write a C++ program to simulate the behavior of the leaky bucket. Leaky Bucket Algorithm Leaky Bucket Algorithm Simulation Step 1 − let us imagine a. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Summarize findings in a report. The algorithm can also be used. Analyze how the leaky bucket algorithm controls. Leaky Bucket Algorithm Simulation.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm Simulation Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The algorithm can also be used. Summarize findings in a report. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. The. Leaky Bucket Algorithm Simulation.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5856654 Leaky Bucket Algorithm Simulation Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The algorithm can also be used. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Summarize findings in a report. Analyze how the leaky bucket algorithm controls congestion. Leaky Bucket Algorithm Simulation.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Leaky Bucket Algorithm Simulation The algorithm can also be used. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Summarize. Leaky Bucket Algorithm Simulation.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Difference YouTube Leaky Bucket Algorithm Simulation The algorithm can also be used. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Analyze. Leaky Bucket Algorithm Simulation.
From www.youtube.com
Traffic Shaping Leaky Bucket Token Bucket Improve QoS Computer Networks Part 3 YouTube Leaky Bucket Algorithm Simulation The algorithm can also be used. Step 1 − let us imagine a. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Summarize findings in a report. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. The leaky bucket is used to implement. Leaky Bucket Algorithm Simulation.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Simulation Summarize findings in a report. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Analyze how. Leaky Bucket Algorithm Simulation.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket Algorithm Simulation Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Summarize findings in a report. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Step 1 − let us imagine a.. Leaky Bucket Algorithm Simulation.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Simulation Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Step 1 − let us imagine a.. Leaky Bucket Algorithm Simulation.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Simulation The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Step 1 − let us imagine a. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm.. Leaky Bucket Algorithm Simulation.
From medium.com
Decoding Complexity — Leaky Bucket Algorithm in Golang by Ameya Sinha Dec, 2023 Medium Leaky Bucket Algorithm Simulation The algorithm can also be used. Summarize findings in a report. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Step 1 − let us imagine a. The leaky bucket is used to implement. Leaky Bucket Algorithm Simulation.
From towardsdev.com
Leaky Bucket vs Token Bucket in Rate Limiting Algorithms by David Lee Towards Dev Leaky Bucket Algorithm Simulation The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. The algorithm can also be used. Summarize. Leaky Bucket Algorithm Simulation.
From www.researchgate.net
Algorithm to Implement the Leaky Bucket and the Token Bucket Download Scientific Diagram Leaky Bucket Algorithm Simulation Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The algorithm can also be used. Step 1 − let us imagine a. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing. Leaky Bucket Algorithm Simulation.
From www.slideserve.com
PPT Chapter 18 Frame Relay PowerPoint Presentation, free download ID4121487 Leaky Bucket Algorithm Simulation Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Summarize findings in a report. The algorithm can also be used. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue. Leaky Bucket Algorithm Simulation.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm Simulation The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. The leaky bucket is used to implement traffic policing and traffic shaping in. Leaky Bucket Algorithm Simulation.
From awstip.com
AWS CDK & Leaky Bucket Manage Traffic Congestion AWS Tip Leaky Bucket Algorithm Simulation Summarize findings in a report. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The algorithm can also be used. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Leaky bucket algorithm mainly controls the total amount. Leaky Bucket Algorithm Simulation.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Simulation Step 1 − let us imagine a. Summarize findings in a report. The algorithm can also be used. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Leaky. Leaky Bucket Algorithm Simulation.
From www.youtube.com
Mastering the Leaky Bucket Algorithm A StepbyStep Guide? algorithm systemdesign Leaky Bucket Algorithm Simulation The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. Summarize findings in a report. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The algorithm can also be used. Step 1 − let us imagine a. Leaky. Leaky Bucket Algorithm Simulation.
From www.slideserve.com
PPT Quality of Service Support PowerPoint Presentation, free download ID6577623 Leaky Bucket Algorithm Simulation The leaky bucket is used to implement traffic policing and traffic shaping in ethernet and cellular data networks. We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. Summarize findings in a report. The algorithm can also be used. Leaky bucket algorithm mainly controls the total amount. Leaky Bucket Algorithm Simulation.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Simulation The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a constant rate regardless of traffic spikes. Summarize findings in a report. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Leaky bucket algorithm mainly controls the total amount. Leaky Bucket Algorithm Simulation.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Simulation We use fast simulation methods, based on importance sampling, to efficiently estimate cell loss probability in queueing models of the leaky bucket algorithm. The algorithm can also be used. Step 1 − let us imagine a. Analyze how the leaky bucket algorithm controls congestion and regulates outgoing traffic. Summarize findings in a report. Leaky bucket algorithm mainly controls the total. Leaky Bucket Algorithm Simulation.