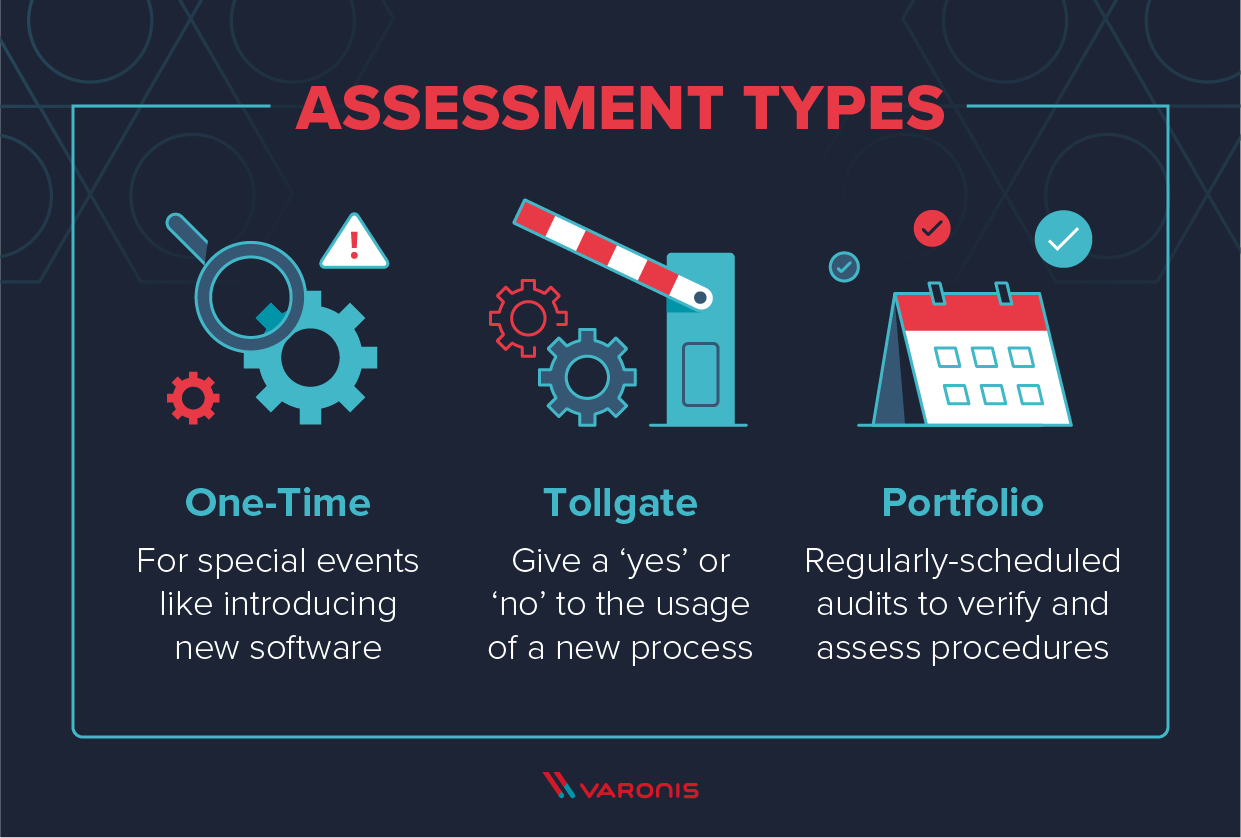
Security Audit Access Controls . By controlling who or what. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. — this publication provides a methodology and set of procedures for conducting assessments of security and. — this article provides some basic it audit procedures for security over data, including logical access over the. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.
from www.varonis.com
— this article provides some basic it audit procedures for security over data, including logical access over the. — this publication provides a methodology and set of procedures for conducting assessments of security and. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. By controlling who or what. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,.
What is an IT Security Audit? The Basics
Security Audit Access Controls — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. — this article provides some basic it audit procedures for security over data, including logical access over the. By controlling who or what. — this publication provides a methodology and set of procedures for conducting assessments of security and. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Security Audit Access Controls — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. By controlling who or what. — this article provides some basic it audit procedures for security over data, including logical access over the. — management of user identities, roles, and permissions, as well as. Security Audit Access Controls.
From securityboulevard.com
Internal Audit Training How to Test Access Controls Security Boulevard Security Audit Access Controls the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s. Security Audit Access Controls.
From www.hex64.net
How Information Security Audit Services Benefits Your Business Process Security Audit Access Controls — this publication provides a methodology and set of procedures for conducting assessments of security and. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security. Security Audit Access Controls.
From www.sampletemplates.com
FREE 8+ Access Audit Report Samples in PDF MS Word Security Audit Access Controls By controlling who or what. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. the consolidated control catalog addresses security and privacy from a functionality perspective. Security Audit Access Controls.
From www.f5.com
What Is Access Control? F5 Labs Security Audit Access Controls — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — this article provides some basic it audit procedures for security over data, including logical access over the. — in. Security Audit Access Controls.
From www.army.mil
Controlling access one element of cybersecurity Article The United Security Audit Access Controls — this article provides some basic it audit procedures for security over data, including logical access over the. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — management of user identities,. Security Audit Access Controls.
From phoenixnap.com
Network Security Audit How to Perform an Audit {Checklist} Security Audit Access Controls the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. — in. Security Audit Access Controls.
From www.pinterest.com
Browse Our Example of It Security Audit Checklist Template for Free Security Audit Access Controls the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — this article provides some basic it audit procedures for security over data, including logical access over the. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — this publication provides a. Security Audit Access Controls.
From www.varonis.com
What is an IT Security Audit? The Basics Security Audit Access Controls — this article provides some basic it audit procedures for security over data, including logical access over the. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. By controlling who or what. — access control is a proactive security measure that helps deter,. Security Audit Access Controls.
From www.strongpoint.io
Building Effective Access Controls in NetSuite Strategies for Security Audit Access Controls — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — this publication provides a methodology and set of procedures for conducting assessments of security and. — this article provides some basic it audit procedures for security over data, including logical access over the. — security controls—during this part of. Security Audit Access Controls.
From www.dnsstuff.com
IT Security Audit Standards, Best Practices, and Tools DNSstuff Security Audit Access Controls — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — security controls—during this part of the audit, the auditor looks at the. Security Audit Access Controls.
From www.midlandinfosys.com
AS400 Security Software Access Controls and Auditing Security Audit Access Controls — this publication provides a methodology and set of procedures for conducting assessments of security and. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. By controlling who or what. — management of user identities, roles, and permissions, as well as monitoring and. Security Audit Access Controls.
From www.slideteam.net
Cloud Security Audit Assessment Process PPT Template Security Audit Access Controls — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. — this article provides some basic it audit procedures for security over data, including logical access over the. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. By. Security Audit Access Controls.
From sprinto.com
Security Audit Checklist [2024] Sprinto Security Audit Access Controls By controlling who or what. — this publication provides a methodology and set of procedures for conducting assessments of security and. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — in addition to typical controls around access management and network security to protects databases in a way to. Security Audit Access Controls.
From blueteamresources.in
2023 Cyber Security Audit Checklist Strengthen Your Defense Security Audit Access Controls — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — this publication provides a methodology and set of procedures for conducting assessments of security and. — in addition to typical. Security Audit Access Controls.
From study.com
Auditing System Security Settings Steps & Purpose Security Audit Access Controls — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. By controlling who or what. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength. Security Audit Access Controls.
From wittenbach.com
Security The Three Major Benefits of Auditing Access Control Security Audit Access Controls — this publication provides a methodology and set of procedures for conducting assessments of security and. — this article provides some basic it audit procedures for security over data, including logical access over the. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — security controls—during this part of. Security Audit Access Controls.
From wittenbach.com
Security The Three Major Benefits of Auditing Access Control Security Audit Access Controls — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. By controlling who or what. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength. Security Audit Access Controls.
From ezddies.com
ISO 27001 Controls Explained A Detailed Guide Secureframe (2022) Security Audit Access Controls the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — this publication provides a methodology and set of procedures for conducting assessments of security and. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. . Security Audit Access Controls.
From www.dochub.com
Security checklist example Fill out & sign online DocHub Security Audit Access Controls By controlling who or what. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — this publication provides a methodology and set of procedures for conducting assessments of security and. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is. Security Audit Access Controls.
From www.leapmanagedit.com
11+ Security Audit Checklist for Businesses Leap Managed IT Security Audit Access Controls — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — this article provides some basic it audit procedures for security over data, including logical. Security Audit Access Controls.
From securityboulevard.com
Comprehensive Cyber Security Audit Checklist for 2024 Security Boulevard Security Audit Access Controls — this article provides some basic it audit procedures for security over data, including logical access over the. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. By controlling who or what. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e.,. Security Audit Access Controls.
From www.itaf.eu
Crucial steps of security audit ITAF IT Partner Security Audit Access Controls — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — this article provides some basic it audit procedures for security over data, including logical access over the. By controlling who or what. — security controls—during this part of the audit, the auditor looks. Security Audit Access Controls.
From www.studypool.com
SOLUTION Access control self audit Studypool Security Audit Access Controls — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. By controlling who or what. — this publication provides a methodology and set of procedures for conducting assessments of security and. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e.,. Security Audit Access Controls.
From www.infosec4tc.com
How to Plan and Conduct a Successful Information Security Audit Security Audit Access Controls — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — this article provides some basic it audit procedures for security over data, including logical. Security Audit Access Controls.
From www.slideteam.net
Aspects Of Information System Access Control Security Audit Security Audit Access Controls By controlling who or what. — this article provides some basic it audit procedures for security over data, including logical access over the. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s. Security Audit Access Controls.
From desklib.com
Challenges in Identification, Authentication and Access Control in Security Audit Access Controls — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. . Security Audit Access Controls.
From www.securityinfowatch.com
Access Control Encryption 101 Security Info Watch Security Audit Access Controls the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — this publication provides a methodology and set of procedures for conducting assessments of security and. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. — management of user. Security Audit Access Controls.
From www.edgemiddleeast.com
How to audit access controls across environments Edge Middle East Security Audit Access Controls — this article provides some basic it audit procedures for security over data, including logical access over the. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs,. Security Audit Access Controls.
From www.techtarget.com
What is RoleBased Access Control (RBAC)? Definition from TechTarget Security Audit Access Controls — this article provides some basic it audit procedures for security over data, including logical access over the. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. By controlling who or what. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s. Security Audit Access Controls.
From wittenbach.com
Security The Three Major Benefits of Auditing Access Control Security Audit Access Controls — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. By controlling who or what. — management of user identities, roles, and permissions, as well as monitoring and reviewing access logs, is crucial to your organization’s. — access control is a proactive security measure. Security Audit Access Controls.
From www.varonis.com
What is an IT Security Audit? The Basics Security Audit Access Controls — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. — this publication provides a methodology and set of procedures for conducting assessments of security and. By controlling who or what. — security controls—during this part of the audit, the auditor looks at the effectiveness of an organization’s security controls. . Security Audit Access Controls.
From moditech.ca
IT Security Audits Security Audit Access Controls — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. — this article provides some basic it audit procedures for security over data, including logical access over the. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of. Security Audit Access Controls.
From www.scribd.com
Audit Checklist on Logical Access Access Control Password Security Audit Access Controls — this publication provides a methodology and set of procedures for conducting assessments of security and. — this article provides some basic it audit procedures for security over data, including logical access over the. — access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. the consolidated control catalog addresses security. Security Audit Access Controls.
From www.linkedin.com
Auditing the Logical Access Security A Crucial Step in Data Protection Security Audit Access Controls — this publication provides a methodology and set of procedures for conducting assessments of security and. the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions. — in addition to typical controls around access management and network security to protects databases in a way to reduce the attack surface,. . Security Audit Access Controls.