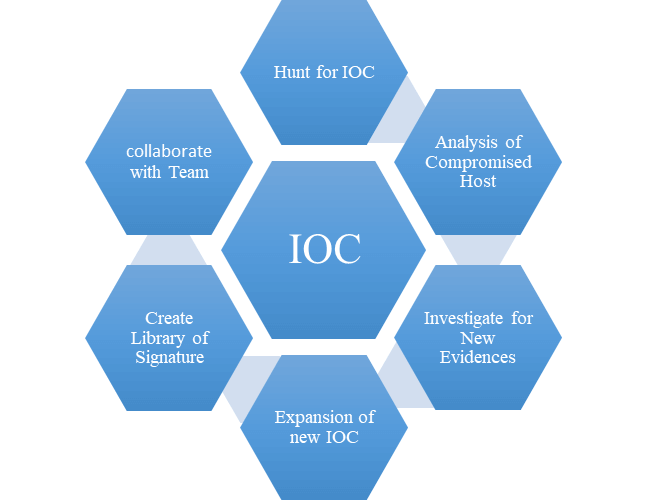
Indicators Of Compromise Vs Threat Intelligence . What is the difference between indicators of attack and indicators of compromise? What are the warning signs that the security team is looking for when investigating cyber threats and. This guide explores the types of iocs, their. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Examples of indicators of compromise. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise is digital evidence that an.
from loemgtuou.blob.core.windows.net
Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. This guide explores the types of iocs, their. Examples of indicators of compromise. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. What are the warning signs that the security team is looking for when investigating cyber threats and. An indicator of compromise is digital evidence that an. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Effective monitoring systems are vital for swift ioc detection and threat mitigation. What is the difference between indicators of attack and indicators of compromise?
Defender Indicators Of Compromise at Laura Gonzalez blog
Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (ioc) are clues that a network or endpoint has been breached. What is the difference between indicators of attack and indicators of compromise? This guide explores the types of iocs, their. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Examples of indicators of compromise. An indicator of compromise is digital evidence that an. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. What are the warning signs that the security team is looking for when investigating cyber threats and. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has.
From www.scribd.com
Sharing Machine Learning Models As Indicators of Compromise For Cyber Indicators Of Compromise Vs Threat Intelligence An indicator of compromise is digital evidence that an. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. What is the difference between indicators of attack and indicators of compromise? What are the. Indicators Of Compromise Vs Threat Intelligence.
From flare.io
What are Indicators of Compromise in Threat Intelligence? Flare Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise is digital evidence that an. What are the warning signs that the security team is looking for when investigating cyber threats and. This guide explores the types of iocs, their. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Indicators of compromise. Indicators Of Compromise Vs Threat Intelligence.
From www.mdpi.com
JCP Free FullText Sharing Machine Learning Models as Indicators of Indicators Of Compromise Vs Threat Intelligence What is the difference between indicators of attack and indicators of compromise? An indicator of compromise is digital evidence that an. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Effective monitoring systems are. Indicators Of Compromise Vs Threat Intelligence.
From www.lepide.com
What are Indicators of Compromise? Indicators Of Compromise Vs Threat Intelligence An indicator of compromise is digital evidence that an. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Effective monitoring systems are vital. Indicators Of Compromise Vs Threat Intelligence.
From www.armordot.com
Indicators of Compromise in Threat Intelligence Let's speak some Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. What is the difference. Indicators Of Compromise Vs Threat Intelligence.
From www.youtube.com
Threat Intelligence and Indicators of Compromise cybrerse Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (ioc) are clues that a network or endpoint has been breached. An indicator of compromise is digital evidence that an. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. What are the warning signs that. Indicators Of Compromise Vs Threat Intelligence.
From fineproxy.org
Indicator of Compromise (IOC) FineProxy Glossary Indicators Of Compromise Vs Threat Intelligence An indicator of compromise is digital evidence that an. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a. Indicators Of Compromise Vs Threat Intelligence.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Indicators Of Compromise Vs Threat Intelligence What is the difference between indicators of attack and indicators of compromise? An indicator of compromise is digital evidence that an. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. Indicators of compromise. Indicators Of Compromise Vs Threat Intelligence.
From www.reversinglabs.com
How to Use Threat Intelligence Indicator Feeds with Microsoft Sentinel Indicators Of Compromise Vs Threat Intelligence Examples of indicators of compromise. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. What are the warning signs that the security team is looking for when investigating cyber threats and. Indicators of compromise (ioc) are clues that a network or endpoint has been breached.. Indicators Of Compromise Vs Threat Intelligence.
From www.armordot.com
Indicators of Compromise in Threat Intelligence Let's speak some Indicators Of Compromise Vs Threat Intelligence Examples of indicators of compromise. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Effective monitoring systems are vital for swift ioc detection and threat mitigation. An indicator of compromise is digital evidence that an. This guide explores the types of iocs, their. Indicators of compromise (iocs) are information about a specific security breach that can help security. Indicators Of Compromise Vs Threat Intelligence.
From www.studocu.com
Threat Prevention Indicators of Compromise Management THREAT Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise is digital evidence that an. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Effective monitoring systems are vital for swift ioc detection and threat mitigation. This guide explores the types of iocs, their. What is the difference between indicators. Indicators Of Compromise Vs Threat Intelligence.
From blog.threat.zone
Glossary Indicator of Compromise VS Indicator of Attack Indicators Of Compromise Vs Threat Intelligence This guide explores the types of iocs, their. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Examples of indicators of compromise. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live. Indicators Of Compromise Vs Threat Intelligence.
From fourtrezz.co.id
Peran Indicator of Compromise dan Threat Intelligence dalam Memperkuat Indicators Of Compromise Vs Threat Intelligence What is the difference between indicators of attack and indicators of compromise? Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. What are the warning signs that the security team is looking for when investigating cyber threats and. Indicators of compromise (iocs) are information. Indicators Of Compromise Vs Threat Intelligence.
From www.youtube.com
What is IOC and IOA Indicator of Attack and Indicator of Compromise Indicators Of Compromise Vs Threat Intelligence An indicator of compromise is digital evidence that an. Effective monitoring systems are vital for swift ioc detection and threat mitigation. This guide explores the types of iocs, their. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Whereas threat feeds simply collect vast quantities of data and. Indicators Of Compromise Vs Threat Intelligence.
From www.sentinelone.com
What are Indicators of Compromise (IoCs)? An Easy Guide Indicators Of Compromise Vs Threat Intelligence Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. Examples of indicators of compromise. This guide explores the types of iocs, their. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Effective monitoring systems are vital for swift ioc detection. Indicators Of Compromise Vs Threat Intelligence.
From www.mdpi.com
JCP Free FullText Sharing Machine Learning Models as Indicators of Indicators Of Compromise Vs Threat Intelligence What is the difference between indicators of attack and indicators of compromise? Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. An indicator of compromise is digital evidence that an. What are the warning signs that the security team is looking for when investigating cyber threats and. Indicators. Indicators Of Compromise Vs Threat Intelligence.
From www.mdpi.com
Electronics Free FullText Key Requirements for the Detection and Indicators Of Compromise Vs Threat Intelligence Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. What are the warning signs that the security team is looking for when investigating cyber threats and. An indicator of compromise is digital evidence that an. What is the difference between indicators of attack and indicators. Indicators Of Compromise Vs Threat Intelligence.
From defensys.com
Defensys Threat Intelligence Platform (TIP) v. 3.0 MITRE ATT&CK Indicators Of Compromise Vs Threat Intelligence What is the difference between indicators of attack and indicators of compromise? Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. What are the warning signs that the security team is looking for when investigating cyber threats and. Indicators of compromise (iocs) are information about a specific security breach that. Indicators Of Compromise Vs Threat Intelligence.
From techcommunity.microsoft.com
Search, Investigate, & Respond to Indicators of Compromise with the Indicators Of Compromise Vs Threat Intelligence Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. Examples of indicators of compromise. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Effective monitoring systems are vital for swift ioc detection and. Indicators Of Compromise Vs Threat Intelligence.
From www.lepide.com
What are Indicators of Compromise? Indicators Of Compromise Vs Threat Intelligence What are the warning signs that the security team is looking for when investigating cyber threats and. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view. Indicators Of Compromise Vs Threat Intelligence.
From www.socinvestigation.com
What is Threat Intelligence Importance , CTI Lifecycle & Pyramid of Indicators Of Compromise Vs Threat Intelligence This guide explores the types of iocs, their. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Effective monitoring systems are vital for swift ioc detection and threat mitigation. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Examples of indicators of compromise.. Indicators Of Compromise Vs Threat Intelligence.
From www.youtube.com
What are the Indicators of compromise YouTube Indicators Of Compromise Vs Threat Intelligence An indicator of compromise is digital evidence that an. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. What is the difference between indicators of attack and indicators of compromise? This guide explores the. Indicators Of Compromise Vs Threat Intelligence.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Indicators Of Compromise Vs Threat Intelligence An indicator of compromise is digital evidence that an. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. This guide explores the types of iocs, their. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Whereas threat feeds simply collect vast quantities of. Indicators Of Compromise Vs Threat Intelligence.
From loemgtuou.blob.core.windows.net
Defender Indicators Of Compromise at Laura Gonzalez blog Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. An indicator of compromise is digital evidence that an. Effective monitoring systems are vital. Indicators Of Compromise Vs Threat Intelligence.
From www.youtube.com
Find Indicators of Compromise Using MISP / Threat Intelligence Indicators Of Compromise Vs Threat Intelligence Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. Effective monitoring systems are vital for swift ioc detection and threat mitigation. What is the difference between indicators of attack and indicators of compromise? An indicator of compromise is digital evidence that an. Examples of indicators. Indicators Of Compromise Vs Threat Intelligence.
From www.armordot.com
Indicators of Compromise in Threat Intelligence Let's speak some Indicators Of Compromise Vs Threat Intelligence Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. What is the difference between indicators of attack and indicators of compromise? Indicators of compromise (iocs) are information about a specific security breach that can. Indicators Of Compromise Vs Threat Intelligence.
From www.youtube.com
Belajar Memahami Indicators of Compromise (IoC) Belajar Online Threat Indicators Of Compromise Vs Threat Intelligence Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view of the. This guide explores the types of iocs, their. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. What is the difference between indicators of. Indicators Of Compromise Vs Threat Intelligence.
From loemgtuou.blob.core.windows.net
Defender Indicators Of Compromise at Laura Gonzalez blog Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. Effective monitoring systems are vital for swift ioc detection and threat mitigation. An indicator of compromise is digital evidence that an. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or. Indicators Of Compromise Vs Threat Intelligence.
From socradar.io
Importance of Indicators of Compromise (IoCs) in CTI for Actionable Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Effective monitoring systems are vital for swift ioc detection and threat mitigation. An indicator of compromise is digital evidence that an. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Whereas threat feeds simply. Indicators Of Compromise Vs Threat Intelligence.
From www.youtube.com
What is Threat Intelligence Types of Threat Intelligence Common Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. An indicator of compromise is digital evidence that an. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Effective monitoring systems are vital for swift ioc detection and threat mitigation. This guide explores the types of iocs,. Indicators Of Compromise Vs Threat Intelligence.
From www2.mdpi.com
JCP Free FullText Sharing Machine Learning Models as Indicators of Indicators Of Compromise Vs Threat Intelligence This guide explores the types of iocs, their. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Examples of indicators of compromise. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or live view. Indicators Of Compromise Vs Threat Intelligence.
From www.mimecast.com
Understanding Threat Intelligence Seeing Beyond Indicators of Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. What are the warning signs that the security team is looking for when investigating cyber threats and. Effective monitoring systems are vital for swift ioc. Indicators Of Compromise Vs Threat Intelligence.
From www.mdpi.com
JCP Free FullText Sharing Machine Learning Models as Indicators of Indicators Of Compromise Vs Threat Intelligence Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. Effective monitoring systems are vital for swift ioc detection and threat mitigation. An indicator of compromise is digital evidence that an. Whereas threat feeds simply collect vast quantities of data and make it available to security teams via a report or. Indicators Of Compromise Vs Threat Intelligence.
From defensys.com
Indicators of compromise Lifecycle management Defensys Indicators Of Compromise Vs Threat Intelligence What are the warning signs that the security team is looking for when investigating cyber threats and. Indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an attack has. An indicator of compromise is digital evidence that an. Examples of indicators of compromise. Indicators of compromise (ioc) are clues that a. Indicators Of Compromise Vs Threat Intelligence.
From arcticwolf.com
Understanding Indicators of Compromise I Arctic Wolf Indicators Of Compromise Vs Threat Intelligence What are the warning signs that the security team is looking for when investigating cyber threats and. Indicators of compromise (ioc) are clues that a network or endpoint has been breached. What is the difference between indicators of attack and indicators of compromise? Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of. Indicators Of Compromise Vs Threat Intelligence.