Access Control Information Security . It is a fundamental concept in security that minimizes risk to the. Access control is a security policy that restricts access to places and/or data. The technical term for this is “access control”. Examples include virtual private networks (vpns) and zero trust. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a security technique that regulates who or what can view or use resources in a computing environment. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. By controlling who or what has access to a resource, it.
from www.gotyoursixcyber.com
Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. By controlling who or what has access to a resource, it. Access control is a security policy that restricts access to places and/or data. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Examples include virtual private networks (vpns) and zero trust. It is a fundamental concept in security that minimizes risk to the. Access control is a security technique that regulates who or what can view or use resources in a computing environment. The technical term for this is “access control”. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.
Access Control Got Your Six Cybersecurity
Access Control Information Security By controlling who or what has access to a resource, it. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Examples include virtual private networks (vpns) and zero trust. The technical term for this is “access control”. By controlling who or what has access to a resource, it. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a security technique that regulates who or what can view or use resources in a computing environment. Access control is a security policy that restricts access to places and/or data. It is a fundamental concept in security that minimizes risk to the. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.
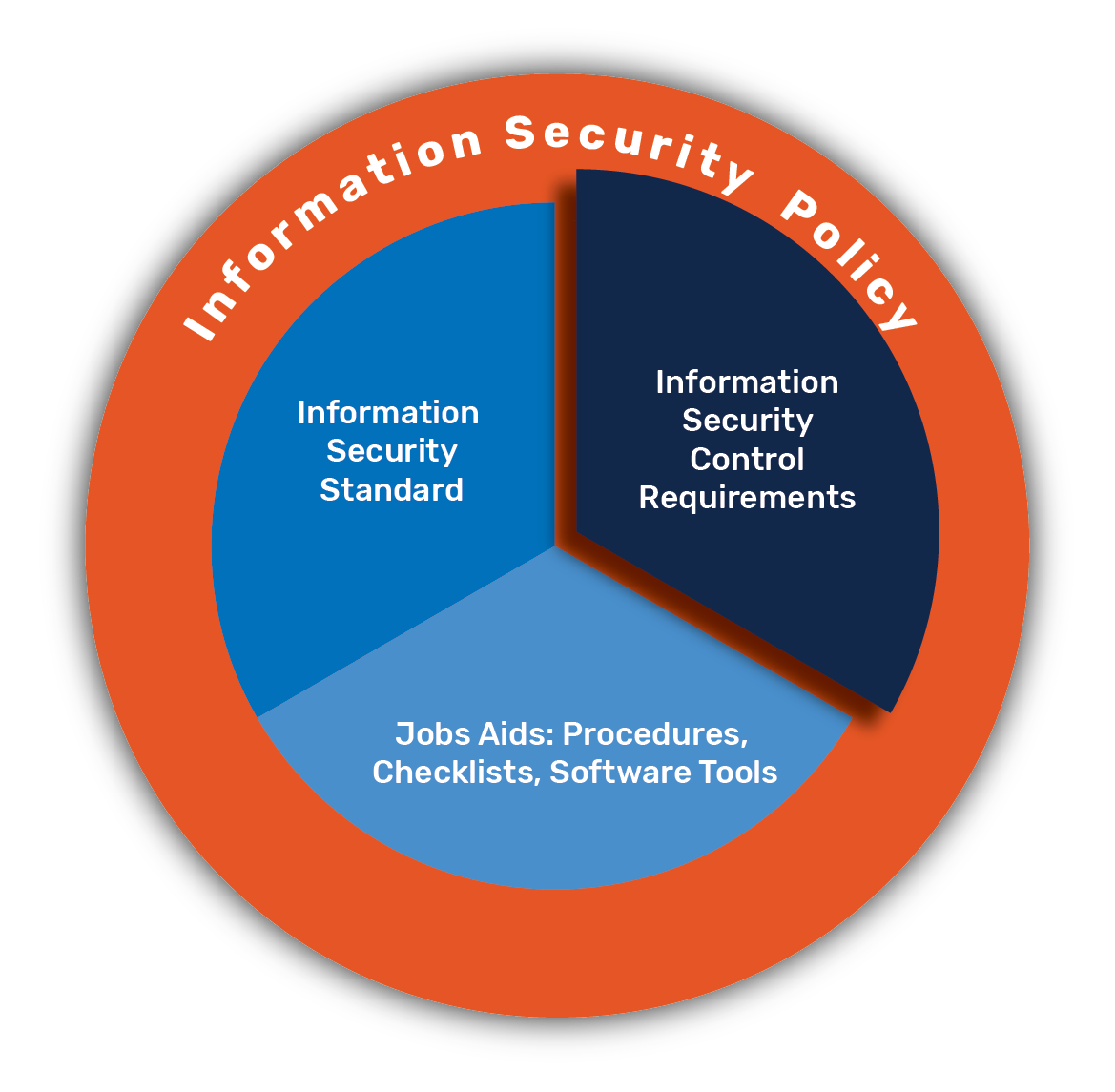
From www.slideteam.net
Aspects Of Information System Access Control Security Audit Access Control Information Security Access control is a security technique that regulates who or what can view or use resources in a computing environment. By controlling who or what has access to a resource, it. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a data security process that. Access Control Information Security.
From www.strongdm.com
3 Types of Access Control IT Security Models Explained StrongDM Access Control Information Security Access control is a security policy that restricts access to places and/or data. Access control is a security technique that regulates who or what can view or use resources in a computing environment. The technical term for this is “access control”. Access control is a type of security measure that limits the visibility, access, and use of resources in a. Access Control Information Security.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Access Control Information Security Access control is a security technique that regulates who or what can view or use resources in a computing environment. Access control is a security policy that restricts access to places and/or data. Examples include virtual private networks (vpns) and zero trust. Access control is a type of security measure that limits the visibility, access, and use of resources in. Access Control Information Security.
From www.scribd.com
Access Control For Security Management PDF Access Control Access Control Information Security Access control is a security technique that regulates who or what can view or use resources in a computing environment. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a type of security measure that limits the visibility, access, and use of resources. Access Control Information Security.
From threeo.ca
Purchase the Access Control & Information Security Course Access Control Information Security Access control is a security policy that restricts access to places and/or data. It is a fundamental concept in security that minimizes risk to the. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. The technical term for this is “access control”. Access control is a type of security. Access Control Information Security.
From www.scanvis-ai.com
Key elements of IoTenabled physical access control solutions for data Access Control Information Security It is a fundamental concept in security that minimizes risk to the. By controlling who or what has access to a resource, it. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a data security process that enables organizations to manage who is authorized to. Access Control Information Security.
From www.touchstar-atc.com
Access Control Systems, Turnstiles & Biometric Devices TouchStar Access Control Information Security Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. It is a fundamental concept in security that minimizes risk to the. Examples include virtual private networks (vpns) and zero trust. The technical term for this is “access control”. Access control is a security technique that regulates. Access Control Information Security.
From blog.soliditech.com
Five Best Practices for Access Control Access Control Information Security Access control is a security policy that restricts access to places and/or data. Access control is a security technique that regulates who or what can view or use resources in a computing environment. By controlling who or what has access to a resource, it. Examples include virtual private networks (vpns) and zero trust. The technical term for this is “access. Access Control Information Security.
From searchcloudcomputing.techtarget.com
Secure data in the cloud with encryption and access controls Access Control Information Security Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. The technical term for this is “access control”. Access control is a security technique that regulates. Access Control Information Security.
From didlakeimaging.com
Are Access Controls Needed for Data Security? Didlake Imaging Access Control Information Security Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security technique that regulates who or what can view or use resources in a computing environment. By controlling who or what has access to a resource, it. Access control is a security policy that restricts access to places and/or data. Network. Access Control Information Security.
From www.gotyoursixcyber.com
Access Control Got Your Six Cybersecurity Access Control Information Security It is a fundamental concept in security that minimizes risk to the. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. By controlling who or what has access to a resource, it. Access control. Access Control Information Security.
From www.rechenberg.com.au
EKA CyberKeys convenient & secure access control Rechenberg Access Control Information Security Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. By controlling who or what has access to a resource, it. The technical term for this is “access control”. Access control is a security technique that regulates who or what can view or use resources in a computing environment. Examples. Access Control Information Security.
From mgiaccess.com
Access Control System 2023 A Guide from Basics to Advanced Techniques Access Control Information Security It is a fundamental concept in security that minimizes risk to the. Access control is a security technique that regulates who or what can view or use resources in a computing environment. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security policy that restricts access to places and/or data.. Access Control Information Security.
From www.openpath.com
Importance of Access Control Security for your Business Access Control Information Security The technical term for this is “access control”. Access control is a security technique that regulates who or what can view or use resources in a computing environment. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Examples include virtual private networks (vpns) and zero trust.. Access Control Information Security.
From www.springboard.com
How To an Information Security Analyst [9 Step Guide] Access Control Information Security Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a security policy that restricts access to places and/or data. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Network access control is a security. Access Control Information Security.
From www.magnum.org.in
How to manage access control in office buildings? Access Control Information Security Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a security technique that regulates who or what can view or use resources in a computing environment. Access control is a data security process that enables organizations to manage who is authorized to access. Access Control Information Security.
From cie-group.com
How to design an Access Control system Access Control Information Security By controlling who or what has access to a resource, it. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security policy that restricts access to places and/or data. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of. Access Control Information Security.
From www.csoonline.com
What is access control? A key component of data security CSO Online Access Control Information Security Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control. Access Control Information Security.
From www.lepide.com
Top 10 Data Security Measures Every Organization Should Have Access Control Information Security Access control is a security policy that restricts access to places and/or data. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. The technical term for this is “access control”. By controlling who or what has access to a resource, it. It is a fundamental concept. Access Control Information Security.
From hanatech.ca
Access Control Systems in Smart Buildings HanatechIoT Solutions Access Control Information Security Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a security policy that restricts access to places and/or data. Access control is a security technique that regulates who or what can view or use resources in a computing environment. By controlling who or what has. Access Control Information Security.
From www.synergyitcybersecurity.com
Identity and Access Management (IAM) in your Organization with MSP Access Control Information Security Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Examples include virtual private networks (vpns) and zero trust. It is a fundamental concept in security that minimizes risk to the. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access. Access Control Information Security.
From getsafeandsound.com
Access Control Systems The Complete Guide for 2023 Access Control Information Security Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a security policy that restricts access to places and/or data. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a. Access Control Information Security.
From integratedtechnics.com
Integrated Technics Integrated Security Solutions Access Control Information Security By controlling who or what has access to a resource, it. Access control is a security policy that restricts access to places and/or data. It is a fundamental concept in security that minimizes risk to the. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access. Access Control Information Security.
From www.securitycameras-stlouis.com
Benefits of Access Control Access Control Information Security Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security policy that restricts access to places and/or data. Examples include virtual private networks (vpns) and zero trust. It is a fundamental concept in security that minimizes risk to the. By controlling who or what has access to a resource, it.. Access Control Information Security.
From its-physec.com
Access Control Physical Security Solutions ITS Physec Access Control Information Security Examples include virtual private networks (vpns) and zero trust. The technical term for this is “access control”. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. By controlling who or what has access. Access Control Information Security.
From www.fingerprint-access-control.com
Fingerprint Access Control Systems Security Systems by Borer Data Access Control Information Security Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control. Access Control Information Security.
From cyberhoot.com
Access Control Mechanism CyberHoot Access Control Information Security Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. The technical term for this is “access control”. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. It is a fundamental concept in security that minimizes risk to the. Examples include virtual private. Access Control Information Security.
From www.thesslstore.com
The Role of Access Control in Information Security Hashed Out by The Access Control Information Security Access control is a security technique that regulates who or what can view or use resources in a computing environment. Examples include virtual private networks (vpns) and zero trust. Access control is a security policy that restricts access to places and/or data. It is a fundamental concept in security that minimizes risk to the. By controlling who or what has. Access Control Information Security.
From www.citytalkgroup.co.uk
Access Control Systems Access Control Security Access Control Information Security The technical term for this is “access control”. It is a fundamental concept in security that minimizes risk to the. By controlling who or what has access to a resource, it. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Examples include virtual private networks (vpns) and zero trust. Access control is a security. Access Control Information Security.
From thecyphere.com
Access Control Security Types Of Access Control Access Control Information Security Access control is a security technique that regulates who or what can view or use resources in a computing environment. Examples include virtual private networks (vpns) and zero trust. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a data security process that enables organizations to manage who is authorized to. Access Control Information Security.
From purplesec.us
Types Of Security Controls Explained Access Control Information Security Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Examples include. Access Control Information Security.
From www.agecctv.co.uk
Access Control Age CCTV security Nationwide Access Control Information Security Network access control is a security solution that uses a set of protocols to keep unauthorized users and devices out of a private. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access. Access Control Information Security.
From eskills.academy
Mastering Access Control in Data Security Eskills Academy Access Control Information Security Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a. Access Control Information Security.
From www.upguard.com
What is Access Control? The Essential Cybersecurity Practice UpGuard Access Control Information Security Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Examples include virtual private networks (vpns) and zero trust. The technical term for this is “access control”. It is a fundamental concept in security that minimizes risk to the. Access control is a security policy that restricts access to. Access Control Information Security.
From protechsecurity.com
Commercial Access Control Systems Letting People in With Access Access Control Information Security Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. By controlling who or what has access to a resource, it. It is a fundamental concept in security that minimizes risk to the. Access control is a security policy that restricts access to places and/or data. Network access control is. Access Control Information Security.