Security Scan Cve . Scan every device that connects your. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Trivy has scanners that look for security. Its capabilities include unauthenticated and authenticated testing,. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. consistent scanning helps identify and address potential security flaws before they can be exploited. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner.
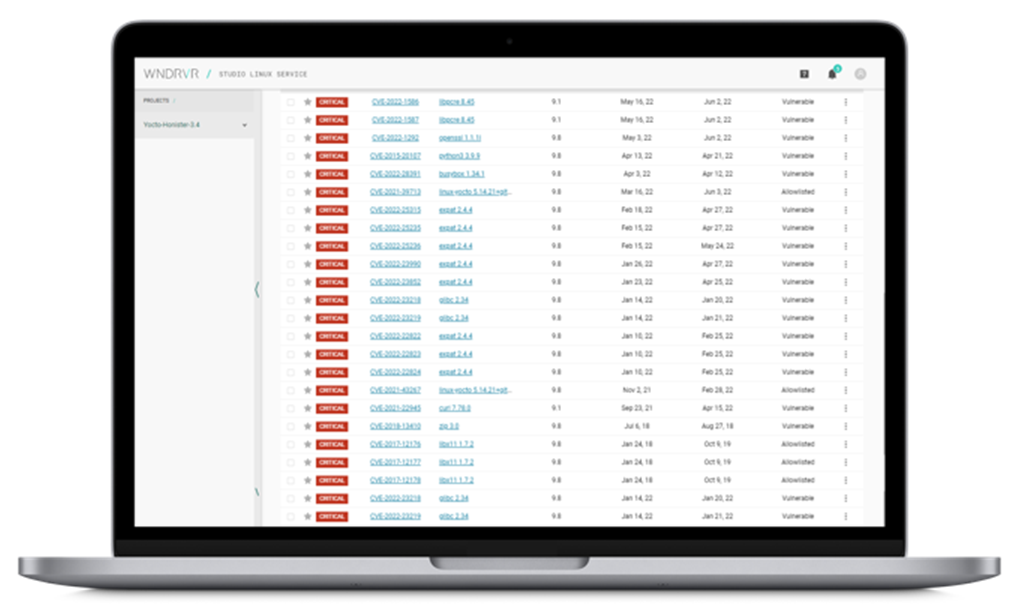
from www.windriver.com
the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Scan every device that connects your. Trivy has scanners that look for security. Its capabilities include unauthenticated and authenticated testing,. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. consistent scanning helps identify and address potential security flaws before they can be exploited.
10 CVE Scanner MustHaves for Security Success Wind River
Security Scan Cve consistent scanning helps identify and address potential security flaws before they can be exploited. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. Its capabilities include unauthenticated and authenticated testing,. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Scan every device that connects your. Trivy has scanners that look for security. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. consistent scanning helps identify and address potential security flaws before they can be exploited.
From www.codiga.io
What is CVE in cyber security? Everything you need to know. Security Scan Cve Trivy has scanners that look for security. consistent scanning helps identify and address potential security flaws before they can be exploited. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Its capabilities include unauthenticated and authenticated testing,. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify. Security Scan Cve.
From www.redlinecybersecurity.com
text4shellscan A fully automated scanner for finding CVE202242889 Redline Cyber Security Security Scan Cve consistent scanning helps identify and address potential security flaws before they can be exploited. Scan every device that connects your. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. cve, short for common vulnerabilities and exposures, is. Security Scan Cve.
From latesthackingnews.com
How to Scan for Vulnerabilities Using Nessus Latest Hacking News Cyber Security News Security Scan Cve Scan every device that connects your. Trivy has scanners that look for security. Its capabilities include unauthenticated and authenticated testing,. consistent scanning helps identify and address potential security flaws before they can be exploited. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. the common vulnerabilities and exposures (cve) program’s. Security Scan Cve.
From www.securitynewspaper.com
Free Citrix ADC ZeroDay Scanner Tool allows discovering CVE20233519 vulnerable servers Security Scan Cve cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Scan every device that connects your. Trivy has scanners that look for security. . Security Scan Cve.
From cybersecurityworks.com
CVE Program Names Cyber Security Works as a CVE Numbering Authority Security Scan Cve Its capabilities include unauthenticated and authenticated testing,. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. consistent scanning helps identify and. Security Scan Cve.
From virtualarmour.com
7 Common Types of Cybersecurity Scans (& What They Tell You) Security Scan Cve Scan every device that connects your. consistent scanning helps identify and address potential security flaws before they can be exploited. Trivy has scanners that look for security. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Its capabilities. Security Scan Cve.
From www.blackhatethicalhacking.com
Offensive Security Tool CVE Binary Tool by Intel Black Hat Ethical Hacking Security Scan Cve cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Trivy has scanners that look for security. Scan every device that connects your. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Its. Security Scan Cve.
From apps-cloudmgmt.techzone.vmware.com
How VEX leverages SBoMs and CVE scan results for an efficient vulnerability assessment VMware Security Scan Cve cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. Scan every device that connects your. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Its capabilities include unauthenticated and authenticated testing,.. Security Scan Cve.
From witekio.com
Linux CVE monitoring Yocto cybersecurity Witekio software Security Scan Cve consistent scanning helps identify and address potential security flaws before they can be exploited. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. Trivy has scanners that look for security. Its capabilities include unauthenticated and authenticated testing,. Scan every device that connects your. the mission of the cve® program is. Security Scan Cve.
From safetycli.com
Safety Cybersecurity Libwebp Special Vulnerability Advisory (CVE20234863) Security Scan Cve Scan every device that connects your. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. consistent scanning helps identify and address potential security flaws before they can be exploited. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. 40 rows trivy. Security Scan Cve.
From www.windriver.com
10 CVE Scanner MustHaves for Security Success Wind River Security Scan Cve consistent scanning helps identify and address potential security flaws before they can be exploited. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Trivy has scanners that look for security. the common vulnerabilities and exposures (cve) program’s primary. Security Scan Cve.
From www.reddit.com
Unleash Your EC2 Instances CVE Scanning with ++ RedDetector AWS EC2 CVE Scanner Open Source Security Scan Cve consistent scanning helps identify and address potential security flaws before they can be exploited. Trivy has scanners that look for security. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Scan every device that connects your. the common. Security Scan Cve.
From www.youtube.com
Nuclei The BEST Vulnerability Scanner Tools for Bug Bounty Security Awareness YouTube Security Scan Cve Scan every device that connects your. Its capabilities include unauthenticated and authenticated testing,. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. consistent scanning helps identify and address potential security flaws before they can be exploited. Trivy has scanners. Security Scan Cve.
From apps-cloudmgmt.techzone.vmware.com
How VEX leverages SBoMs and CVE scan results for an efficient vulnerability assessment VMware Security Scan Cve the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. 40 rows trivy (pronunciation) is a comprehensive. Security Scan Cve.
From apps-cloudmgmt.techzone.vmware.com
How VEX leverages SBoMs and CVE scan results for an efficient vulnerability assessment VMware Security Scan Cve the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. consistent scanning helps identify and address potential security flaws before they can. Security Scan Cve.
From www.youtube.com
[Hacking Course] 14. Nessus advanced scan. Overview of CVE, CWE, CVSS and Windows catalog update Security Scan Cve cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. 40 rows trivy (pronunciation) is a comprehensive. Security Scan Cve.
From learncybers.com
What is CVE in cyber security? Security Scan Cve the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Trivy has scanners that look for security. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. consistent scanning helps identify and address potential security flaws before they can be exploited. Scan every device. Security Scan Cve.
From www.codiga.io
What is CVE in cyber security? Everything you need to know. Security Scan Cve Its capabilities include unauthenticated and authenticated testing,. Scan every device that connects your. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. consistent scanning helps identify and address potential security flaws before they can be exploited. the mission of the cve® program is to identify, define, and catalog publicly disclosed. Security Scan Cve.
From www.youtube.com
Cyber Security Tips for Beginners to Experts What Is the ‘CVE’ Code? YouTube Security Scan Cve consistent scanning helps identify and address potential security flaws before they can be exploited. Trivy has scanners that look for security. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. cve, short. Security Scan Cve.
From vulners.com
What is a CVE Meaning & Common Vulnerabilities and Exposures in Security Vulners Security Scan Cve 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. Scan every device that connects your. Trivy has scanners that look for security. Its capabilities include unauthenticated and authenticated testing,. cve, short for common vulnerabilities and exposures, is a. Security Scan Cve.
From cvgenius.com
Cyber Security CV Free Example, Template, & Guide Security Scan Cve Its capabilities include unauthenticated and authenticated testing,. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Trivy has scanners that look for security. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to. Security Scan Cve.
From app.codiga.io
CVE vs. CWE Vulnerability What's The Difference? Security Scan Cve cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Trivy has scanners that look for security. Scan every device that connects your. Its capabilities include unauthenticated and authenticated testing,. consistent scanning helps identify and address potential security flaws before. Security Scan Cve.
From www.picussecurity.com
ProxyNotShell CVE202241040 and CVE202241082 Exploits Explained Security Scan Cve consistent scanning helps identify and address potential security flaws before they can be exploited. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Trivy has scanners that look for security. cve, short for common vulnerabilities and exposures, is. Security Scan Cve.
From witekio.com
Linux CVE monitoring Yocto cybersecurity Witekio software Security Scan Cve the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. consistent scanning helps identify and address potential security flaws before they can be exploited. Scan every device that connects your. 40 rows trivy. Security Scan Cve.
From github.com
GitHub jiansiting/CVE20200796Scanner CVE20200796Scanner Security Scan Cve Scan every device that connects your. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. Its capabilities include unauthenticated and authenticated testing,. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. consistent scanning helps identify and address potential security flaws before they can. Security Scan Cve.
From bishopfox.com
CVE202327997 Vulnerability Scanner for FortiGate… Fox Security Scan Cve the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Scan every device that connects your. consistent scanning helps identify and address potential security flaws before they can be exploited. Its capabilities include unauthenticated and authenticated testing,. Trivy has scanners. Security Scan Cve.
From github.com
GitHub NorthernSec/CVEScan Scan systems with NMap and parse the output to a list of CVE's Security Scan Cve Scan every device that connects your. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Its capabilities include unauthenticated and authenticated testing,. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.. Security Scan Cve.
From wott.io
of Trusted Things How to Do a CVE Scan of Your Linux System Security Scan Cve cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. Trivy has scanners that look for security. Its capabilities include unauthenticated and authenticated testing,. the mission of the cve® program is to identify, define,. Security Scan Cve.
From github.com
GitHub ruppde/rdg_scanner_cve20200609 Scanning for Remote Desktop Gateways (Potentially Security Scan Cve consistent scanning helps identify and address potential security flaws before they can be exploited. Its capabilities include unauthenticated and authenticated testing,. Trivy has scanners that look for security. Scan every device that connects your. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and to associate. 40 rows trivy (pronunciation) is a. Security Scan Cve.
From www.picussecurity.com
CVE202324880 Vulnerability Exploited by Magniber Ransomware Group Security Scan Cve the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Its capabilities include unauthenticated and authenticated testing,. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. consistent scanning helps identify and address potential security flaws before they can be exploited. the common vulnerabilities. Security Scan Cve.
From www.youtube.com
How to scan for vulnerabilities(CVE) using nmap YouTube Security Scan Cve Trivy has scanners that look for security. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. Scan every device that connects your. Its capabilities include unauthenticated and authenticated testing,. the common vulnerabilities and exposures (cve) program’s primary purpose is. Security Scan Cve.
From grafana.com
How to manage CVE security vulnerabilities with Grafana, MergeStat, and OSVScanner Grafana Labs Security Scan Cve Scan every device that connects your. consistent scanning helps identify and address potential security flaws before they can be exploited. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Its capabilities include unauthenticated and authenticated testing,. the mission. Security Scan Cve.
From www.akamai.com
CVEs What They Are, and Ways to Mitigate Their Impact Akamai Security Scan Cve Its capabilities include unauthenticated and authenticated testing,. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. Trivy has scanners that look for security. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner.. Security Scan Cve.
From www.youtube.com
CVE and CVSS explained Security Detail YouTube Security Scan Cve 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. consistent scanning helps identify and address potential security flaws before they can be exploited. the common vulnerabilities and exposures (cve) program’s primary purpose is to uniquely identify vulnerabilities and. Security Scan Cve.
From sysdig.com
Critical Vulnerability in Spring Core CVE202222965 a.k.a. Spring4Shell Sysdig Security Scan Cve cve, short for common vulnerabilities and exposures, is a list of publicly disclosed computer security flaws. the mission of the cve® program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. consistent scanning helps identify and address potential security flaws before they can be exploited. Its capabilities include unauthenticated and authenticated testing,. Trivy has scanners that. Security Scan Cve.