Security Controls For Remote Access . In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. It ensures that data transmitted over the connection is encrypted and that only authorized users can access the system. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. All the components of telework and remote access solutions, including client devices, remote access servers, and internal resources accessed through remote access, should be. 10k+ visitors in the past month These activities help evaluate risks that could impact remote access security. The term secure remote access covers all security policies, processes, and solutions that protect your network from. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized.
from www.remote-accesss.com
Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. 10k+ visitors in the past month Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. All the components of telework and remote access solutions, including client devices, remote access servers, and internal resources accessed through remote access, should be. The term secure remote access covers all security policies, processes, and solutions that protect your network from. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. These activities help evaluate risks that could impact remote access security.
Privileged Remote Access Software
Security Controls For Remote Access Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The term secure remote access covers all security policies, processes, and solutions that protect your network from. These activities help evaluate risks that could impact remote access security. All the components of telework and remote access solutions, including client devices, remote access servers, and internal resources accessed through remote access, should be. 10k+ visitors in the past month Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. It ensures that data transmitted over the connection is encrypted and that only authorized users can access the system. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized.
From medium.com
Authentication Controls. An access control system is the set of… by Security Controls For Remote Access Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. 10k+ visitors in the past month Secure remote. Security Controls For Remote Access.
From www.pinterest.com
Remote Access The control unit allows you to control your system Security Controls For Remote Access Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. It ensures that data transmitted over the connection is encrypted and that only authorized users can access the system. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. These. Security Controls For Remote Access.
From www.remote-accesss.com
Privileged Remote Access Software Security Controls For Remote Access Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Remote access security acts as something of a virtual barrier, preventing. Security Controls For Remote Access.
From www.identificationsystemsgroup.com
Remote Access Control for Physical Security The ISG Security Controls For Remote Access All the components of telework and remote access solutions, including client devices, remote access servers, and internal resources accessed through remote access, should be. Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. These activities help evaluate risks that could impact remote access security. Focus on critical aspects like. Security Controls For Remote Access.
From icma.org
Checklist Keep Your Remote Workforce Safe from Cyberthreats Security Controls For Remote Access Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. These activities help evaluate risks that could impact remote access security. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Secure remote access refers to the methods and technologies that allow users. Security Controls For Remote Access.
From www.cr-t.com
What is Secure Remote Access? IT Services in Utah CRT Security Controls For Remote Access These activities help evaluate risks that could impact remote access security. Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The term secure remote access. Security Controls For Remote Access.
From its-physec.com
Access Control Physical Security Solutions ITS Physec Security Controls For Remote Access Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. In this guide, we examine. Security Controls For Remote Access.
From industrial.omron.co.uk
Remote Access Solution OMRON, UK Security Controls For Remote Access In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. 10k+ visitors in the past. Security Controls For Remote Access.
From www.epssecurity.com
Remote Security Zwave Technology, Honeywell Total Connect Security Controls For Remote Access These activities help evaluate risks that could impact remote access security. All the components of telework and remote access solutions, including client devices, remote access servers, and internal resources accessed through remote access, should be. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Remote. Security Controls For Remote Access.
From texadiasystems.com
4 Ways to Approach Remote Access Control Blog Security Controls For Remote Access Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. It ensures that data transmitted over the connection is encrypted and that only authorized users can access the system. All the components of telework and remote access solutions, including client devices, remote access servers, and internal resources accessed through remote. Security Controls For Remote Access.
From www.banggood.com
Remote control antitheft door lock home wireless security access Security Controls For Remote Access 10k+ visitors in the past month Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The term secure remote access covers all security policies, processes,. Security Controls For Remote Access.
From duo.com
The Essential Guide to Securing Remote Access Duo Security Security Controls For Remote Access Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. All the components of telework and remote access solutions, including client devices, remote access servers, and internal resources accessed through remote access, should be. In this guide, we examine how businesses should rethink key aspects of their. Security Controls For Remote Access.
From www.realvnc.com
Why Your Remote Access Solution’s Own Security Really Matters RealVNC® Security Controls For Remote Access Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Secure remote access refers to the methods and technologies that allow users to access. Security Controls For Remote Access.
From www.grainger.com
ALARM CONTROLS Remote, Access Control For Use With 48ZW66RT1 Grainger Security Controls For Remote Access Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The term secure remote access covers all security policies, processes, and solutions that protect your network from. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Security Controls For Remote Access.
From iebmedia.com
Five key considerations for secure remote access solutions Industrial Security Controls For Remote Access Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. These activities help evaluate risks that could impact remote access security. 10k+ visitors in the past month Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. All the components of telework and. Security Controls For Remote Access.
From securedebug.com
Best Practices for Remote Access Security Controls Secure Debug Security Controls For Remote Access Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Here are five top security risks that teams must deal with, as well as. Security Controls For Remote Access.
From www.eztcp.com
Security Remote Access Control System Security Controls For Remote Access The term secure remote access covers all security policies, processes, and solutions that protect your network from. These activities help evaluate risks that could impact remote access security. It ensures that data transmitted over the connection is encrypted and that only authorized users can access the system. 10k+ visitors in the past month Remote access security (sometimes called “secure remote. Security Controls For Remote Access.
From www.fingerprint-access-control.com
Fingerprint Access Control Systems Security Systems by Borer Data Security Controls For Remote Access Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. 10k+ visitors in the past month In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access. Security Controls For Remote Access.
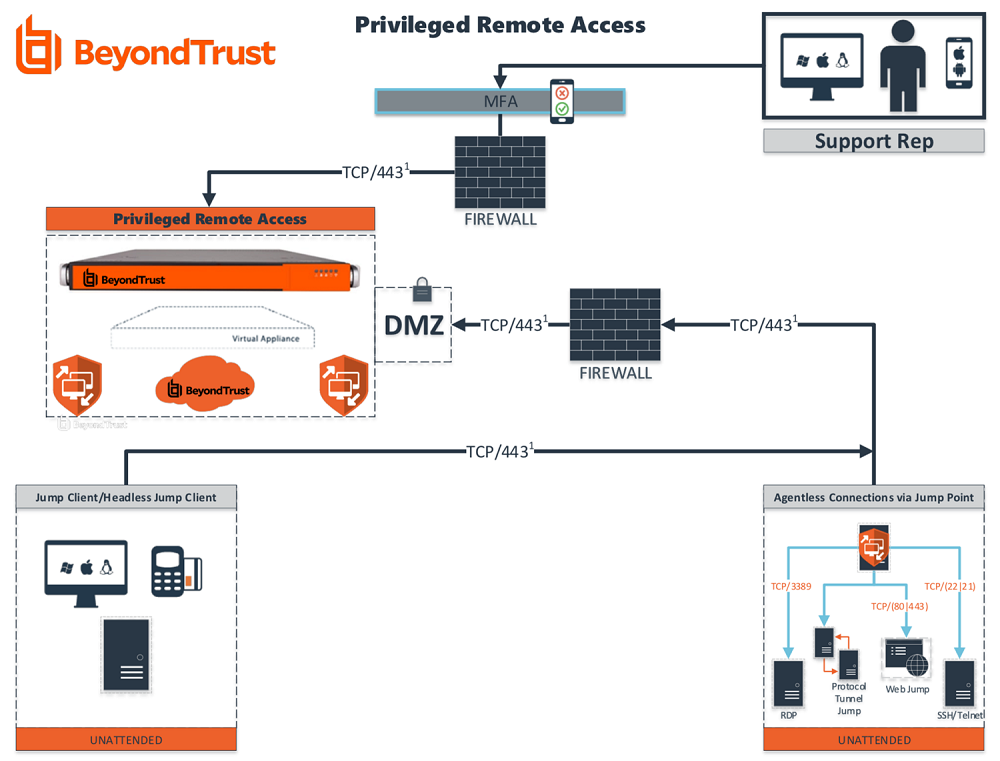
From www.beyondtrust.com
Architecture of Secure Remote Access (OnPremises) Security Controls For Remote Access These activities help evaluate risks that could impact remote access security. The term secure remote access covers all security policies, processes, and solutions that protect your network from. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Focus on critical aspects like vpn logins, network. Security Controls For Remote Access.
From pngtree.com
Car Key With Remote Security Functions Control Remote Access Vector Security Controls For Remote Access Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. These activities help evaluate risks that could impact remote access security. The term secure remote access covers all security policies, processes, and solutions that protect your network from. Remote access security acts as something of a. Security Controls For Remote Access.
From www.ccivoice.com
Business Video Surveillance & Access Control Security Controls For Remote Access In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. It ensures that data transmitted over the connection is encrypted and. Security Controls For Remote Access.
From bleuwire.com
How to Set up Secure Remote Network Access Bleuwire Security Controls For Remote Access Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. It ensures that data transmitted over the connection is encrypted and that only authorized users can. Security Controls For Remote Access.
From slideplayer.com
Operating System Security ppt download Security Controls For Remote Access The term secure remote access covers all security policies, processes, and solutions that protect your network from. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Remote access security acts as something of a virtual barrier, preventing. Security Controls For Remote Access.
From purplesec.us
Types Of Security Controls Explained Security Controls For Remote Access Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. Secure remote access refers to the methods and technologies that allow. Security Controls For Remote Access.
From getsafeandsound.com
How To Setup a NVR for Remote Viewing Safe and Sound Security Security Controls For Remote Access Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. These activities help evaluate risks that could impact remote access security. All the components of telework and remote access solutions, including client devices, remote access servers,. Security Controls For Remote Access.
From www.kaseya.com
What Is Remote Access and How Does It Work? Kaseya Security Controls For Remote Access The term secure remote access covers all security policies, processes, and solutions that protect your network from. These activities help evaluate risks that could impact remote access security. 10k+ visitors in the past month Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. It ensures that data transmitted over the connection is encrypted and that. Security Controls For Remote Access.
From www.smartsheet.com
How to Implement an Effective Remote Access Policy Smartsheet Security Controls For Remote Access Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. All the components of telework and remote access solutions,. Security Controls For Remote Access.
From tinkerman.cat
Secure Remote Access to Your IoT Devices Tinkerman Security Controls For Remote Access These activities help evaluate risks that could impact remote access security. The term secure remote access covers all security policies, processes, and solutions that protect your network from. Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set. Security Controls For Remote Access.
From www.boydsecurity.com
How to Secure Your Remote Access Security Camera System 𝗕𝗼𝘆𝗱 & 𝗔𝘀𝘀𝗼𝗰𝗶𝗮𝘁𝗲𝘀 Security Controls For Remote Access Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. 10k+ visitors in the past month These activities help evaluate risks that could impact remote access security. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to. Security Controls For Remote Access.
From blog.techprognosis.com
Secure Remote Access Keeping Business Going with Remote Work Security Controls For Remote Access 10k+ visitors in the past month Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Secure remote access refers to the methods and technologies that allow users to access. Security Controls For Remote Access.
From www.securityfive.com
Best Remote Access Devices Security Five Security Controls For Remote Access It ensures that data transmitted over the connection is encrypted and that only authorized users can access the system. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. All the components of telework and remote access solutions,. Security Controls For Remote Access.
From info.verkada.com
Remote Access Surveillance Security Features & Best Practices Security Controls For Remote Access The term secure remote access covers all security policies, processes, and solutions that protect your network from. Remote access security acts as something of a virtual barrier, preventing unauthorized access to data and assets beyond the traditional. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. It ensures that data transmitted over. Security Controls For Remote Access.
From www.securelockandalarm.com
Upgrade Your Business Remote Access Control to Stay Protected! Secure Security Controls For Remote Access The term secure remote access covers all security policies, processes, and solutions that protect your network from. Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users. All the components of telework and remote access solutions, including client devices, remote access servers, and internal resources accessed through. Security Controls For Remote Access.
From www.gravityusa.com
Top 3 Remote Access Tools Keep You Productive Security Controls For Remote Access Focus on critical aspects like vpn logins, network ports, user permissions, and cloud security. The term secure remote access covers all security policies, processes, and solutions that protect your network from. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. All the components of telework and remote access solutions, including client devices,. Security Controls For Remote Access.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Security Controls For Remote Access Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. 10k+ visitors in the past month In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem. All the components of telework. Security Controls For Remote Access.