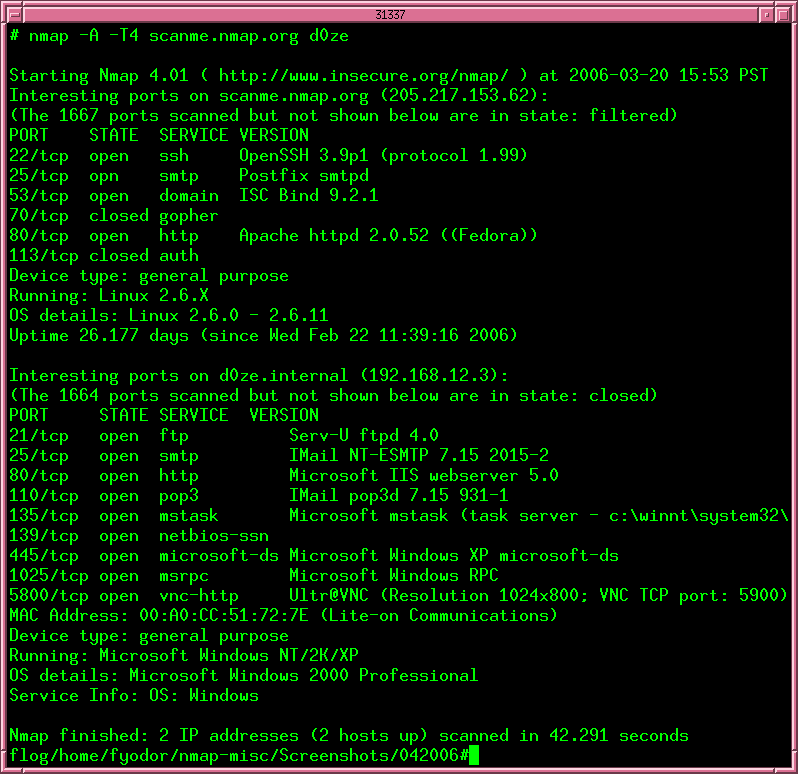
Port Scanning Example . Each listening service provides attack surface which could potentially be abused by attackers. A port scan is a common technique hackers use to discover open doors or weak points in a network. Scan the first 1000 ports on a cidr range. Port scanning is generally done in stages: A port scanner is an application which is made to probe a host or server to identify open ports. Port scanning is a technique used to identify open ports on a network or server. One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. It involves sending packets to specific ports and analyzing the. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. Scan the first 1000 udp ports on responding devices. Horizontal port scanning is scanning a set of ip addresses for a specific port address;. Port scanning is done to try determine which services we can connect to. A quick port scanning tutorial. A port scan attack helps cyber criminals find open ports and figure out. There are two types of port scanning:
from nmap.org
Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. There are two types of port scanning: Horizontal port scanning is scanning a set of ip addresses for a specific port address;. Port scanning is done to try determine which services we can connect to. A port scan is a common technique hackers use to discover open doors or weak points in a network. Scan the first 1000 ports on a cidr range. Each listening service provides attack surface which could potentially be abused by attackers. A port scanner is an application which is made to probe a host or server to identify open ports. Port scanning is generally done in stages: A port scan attack helps cyber criminals find open ports and figure out.
Nmap The Art of Port Scanning
Port Scanning Example There are two types of port scanning: Scan the first 1000 udp ports on responding devices. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. Horizontal port scanning is scanning a set of ip addresses for a specific port address;. There are two types of port scanning: Scan the first 1000 ports on a cidr range. A quick port scanning tutorial. Each listening service provides attack surface which could potentially be abused by attackers. Port scanning is done to try determine which services we can connect to. Port scanning is a technique used to identify open ports on a network or server. A port scan is a common technique hackers use to discover open doors or weak points in a network. A port scan attack helps cyber criminals find open ports and figure out. It involves sending packets to specific ports and analyzing the. A port scanner is an application which is made to probe a host or server to identify open ports. Port scanning is generally done in stages: One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for.
From www.slideserve.com
PPT Port Scanning PowerPoint Presentation, free download ID1449384 Port Scanning Example Horizontal port scanning is scanning a set of ip addresses for a specific port address;. Port scanning is generally done in stages: A quick port scanning tutorial. Scan the first 1000 udp ports on responding devices. Port scanning is done to try determine which services we can connect to. Port scanning is a technique used to identify open ports on. Port Scanning Example.
From www.advanced-port-scanner.com
Advanced Port Scanner 무료 고속 포트 스캐너 Port Scanning Example A port scanner is an application which is made to probe a host or server to identify open ports. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. Each listening service provides attack surface which could potentially be abused by attackers. Port scanning is generally done in stages: Scan the first 1000 udp. Port Scanning Example.
From www.slideserve.com
PPT Port Scanning PowerPoint Presentation, free download ID4633948 Port Scanning Example One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. Scan the first 1000 ports on a cidr range. A port scan attack helps cyber criminals find open ports and figure out. A port scan is a common technique hackers use to discover open doors or weak points in a. Port Scanning Example.
From www.hackercoolmagazine.com
Port scanning techniques for beginners Hackercool Magazine Port Scanning Example Each listening service provides attack surface which could potentially be abused by attackers. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. Port scanning is a technique used to identify open ports on a network or server. Scan the first 1000 udp ports on responding devices. A port scan is a common technique. Port Scanning Example.
From www.manageengine.com
What is Port Scanner? Scanning Ports ManageEngine OpUtils Port Scanning Example Port scanning is generally done in stages: Port scanning is done to try determine which services we can connect to. Horizontal port scanning is scanning a set of ip addresses for a specific port address;. There are two types of port scanning: A port scan attack helps cyber criminals find open ports and figure out. It involves sending packets to. Port Scanning Example.
From hackertarget.com
Online Port Scanner Powered by Nmap Port Scanning Example Port scanning is done to try determine which services we can connect to. Port scanning is generally done in stages: It involves sending packets to specific ports and analyzing the. Scan the first 1000 udp ports on responding devices. Scan the first 1000 ports on a cidr range. A port scan attack helps cyber criminals find open ports and figure. Port Scanning Example.
From whatismyipaddress.com
What is a Port Scan? Port Scanning Example There are two types of port scanning: Each listening service provides attack surface which could potentially be abused by attackers. Scan the first 1000 ports on a cidr range. Scan the first 1000 udp ports on responding devices. Horizontal port scanning is scanning a set of ip addresses for a specific port address;. A port scan is a common technique. Port Scanning Example.
From www.youtube.com
Port Scanning Its types Methods used YouTube Port Scanning Example Scan the first 1000 ports on a cidr range. It involves sending packets to specific ports and analyzing the. There are two types of port scanning: A quick port scanning tutorial. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. Port scanning is generally done in stages: Scan the first 1000 udp ports. Port Scanning Example.
From www.gdatasoftware.com
Simple security tests using Metasploit and nmap G DATA Port Scanning Example Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. Scan the first 1000 udp ports on responding devices. Port scanning is a technique used to identify open ports on a network or server. A port scanner is an application which is made to probe a host or server to identify open ports. Port. Port Scanning Example.
From www.paloaltonetworks.com
What is a Port Scan? Palo Alto Networks Port Scanning Example One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. A quick port scanning tutorial. A port scan attack helps cyber criminals find open ports and figure out. Scan the first 1000 ports on a cidr range. Port scanning is a technique used to identify open ports on a network. Port Scanning Example.
From www.eccouncil.org
What Are Network Ports and Port Scanning Techniques? ECCouncil Port Scanning Example It involves sending packets to specific ports and analyzing the. Horizontal port scanning is scanning a set of ip addresses for a specific port address;. Port scanning is generally done in stages: A quick port scanning tutorial. A port scan attack helps cyber criminals find open ports and figure out. A port scanner is an application which is made to. Port Scanning Example.
From www.slideserve.com
PPT Scanning, Sniffing, Spoofing and Maninthemiddle Attacks Port Scanning Example Each listening service provides attack surface which could potentially be abused by attackers. Horizontal port scanning is scanning a set of ip addresses for a specific port address;. A port scan attack helps cyber criminals find open ports and figure out. Scan the first 1000 udp ports on responding devices. Bad actors can use port scanners to exploit vulnerabilities by. Port Scanning Example.
From nmap.org
Nmap The Art of Port Scanning Port Scanning Example Port scanning is generally done in stages: Horizontal port scanning is scanning a set of ip addresses for a specific port address;. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. Scan the first 1000 ports on a cidr range. A port scan attack helps cyber criminals find open ports and figure out.. Port Scanning Example.
From www.researchgate.net
The example of the process of scenario generation port scanning chosen Port Scanning Example A port scan is a common technique hackers use to discover open doors or weak points in a network. A port scan attack helps cyber criminals find open ports and figure out. There are two types of port scanning: One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. A. Port Scanning Example.
From www.tech-faq.com
Port Scanner TechFAQ Port Scanning Example Scan the first 1000 ports on a cidr range. A port scan attack helps cyber criminals find open ports and figure out. A port scanner is an application which is made to probe a host or server to identify open ports. A port scan is a common technique hackers use to discover open doors or weak points in a network.. Port Scanning Example.
From www.nsauditor.com
Port Scanner Free Port Scanner for Scan Ports on Port Ranges Port Scanning Example Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. There are two types of port scanning: Port scanning is generally done in stages: Port scanning is a technique used to identify open ports on a network or server. Scan the first 1000 udp ports on responding devices. One of my goals in developing. Port Scanning Example.
From www.geeksforgeeks.org
Nmap Command in Linux with Examples Port Scanning Example Scan the first 1000 ports on a cidr range. A quick port scanning tutorial. It involves sending packets to specific ports and analyzing the. Port scanning is a technique used to identify open ports on a network or server. There are two types of port scanning: A port scanner is an application which is made to probe a host or. Port Scanning Example.
From b.hatena.ne.jp
[B! network] Best Port Scanning Software & Tools for Windows, Linux and Port Scanning Example Port scanning is done to try determine which services we can connect to. Scan the first 1000 ports on a cidr range. One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. A port scan attack helps cyber criminals find open ports and figure out. Port scanning is generally done. Port Scanning Example.
From www.slideserve.com
PPT Footprinting Scanning Enumeration PowerPoint Presentation, free Port Scanning Example Port scanning is done to try determine which services we can connect to. Scan the first 1000 ports on a cidr range. One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. It involves sending packets to specific ports and analyzing the. A port scan is a common technique hackers. Port Scanning Example.
From www.slideserve.com
PPT Cyber Operation and Testing Scanning Cliff Zou Port Scanning Example There are two types of port scanning: Scan the first 1000 ports on a cidr range. Scan the first 1000 udp ports on responding devices. A quick port scanning tutorial. Port scanning is a technique used to identify open ports on a network or server. A port scan attack helps cyber criminals find open ports and figure out. Bad actors. Port Scanning Example.
From stackdiary.com
A Simple Guide to Port Scanning with Netcat Port Scanning Example One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. Port scanning is a technique used to identify open ports on a network or server. Port scanning is done to try determine which services we can connect to. Bad actors can use port scanners to exploit vulnerabilities by finding network. Port Scanning Example.
From blackethicalhathacking.blogspot.com
Blackhat hacking Nmap Port Scanning Techniques Explained Port Scanning Example Scan the first 1000 udp ports on responding devices. A quick port scanning tutorial. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. Each listening service provides attack surface which could potentially be. Port Scanning Example.
From knowledgewithblogs.blogspot.com
Port scanning Cyber security & Technology Port Scanning Example There are two types of port scanning: Horizontal port scanning is scanning a set of ip addresses for a specific port address;. A port scanner is an application which is made to probe a host or server to identify open ports. Port scanning is done to try determine which services we can connect to. Port scanning is a technique used. Port Scanning Example.
From www.paloaltonetworks.sg
What is a Port Scan? Palo Alto Networks Port Scanning Example There are two types of port scanning: Scan the first 1000 udp ports on responding devices. Scan the first 1000 ports on a cidr range. It involves sending packets to specific ports and analyzing the. One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. Each listening service provides attack. Port Scanning Example.
From www.youtube.com
How to Scan IP address and find all open ports YouTube Port Scanning Example It involves sending packets to specific ports and analyzing the. Each listening service provides attack surface which could potentially be abused by attackers. A port scanner is an application which is made to probe a host or server to identify open ports. Port scanning is done to try determine which services we can connect to. A port scan is a. Port Scanning Example.
From www.juniper.net
IP Address Sweep and Port Scan Junos OS Juniper Networks Port Scanning Example A port scan attack helps cyber criminals find open ports and figure out. Port scanning is a technique used to identify open ports on a network or server. Horizontal port scanning is scanning a set of ip addresses for a specific port address;. It involves sending packets to specific ports and analyzing the. Bad actors can use port scanners to. Port Scanning Example.
From www.computertechreviews.com
What is Port Scanning (Port Scan)? Definition, Types and More Port Scanning Example There are two types of port scanning: Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. Port scanning is a technique used to identify open ports on a network or server. A port scan is a common technique hackers use to discover open doors or weak points in a network. A quick port. Port Scanning Example.
From www.youtube.com
3.2 Network port scanning YouTube Port Scanning Example Port scanning is a technique used to identify open ports on a network or server. Port scanning is done to try determine which services we can connect to. Each listening service provides attack surface which could potentially be abused by attackers. It involves sending packets to specific ports and analyzing the. A port scanner is an application which is made. Port Scanning Example.
From www.beyondtrust.com
What is an Open Port & What are the Security… BeyondTrust Port Scanning Example Scan the first 1000 udp ports on responding devices. A port scanner is an application which is made to probe a host or server to identify open ports. There are two types of port scanning: Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. A port scan is a common technique hackers use. Port Scanning Example.
From linuxhint.com
Nmap Version Scan, determining the version and available services Port Scanning Example Port scanning is generally done in stages: One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. A quick port scanning tutorial. Scan the first 1000 udp ports on responding devices. Port scanning is done to try determine which services we can connect to. There are two types of port. Port Scanning Example.
From digiflare.pages.dev
10 Port Scanner Tools For Advanced Scanning By Network Administrators Port Scanning Example Horizontal port scanning is scanning a set of ip addresses for a specific port address;. Port scanning is generally done in stages: Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. It involves sending packets to specific ports and analyzing the. A port scanner is an application which is made to probe a. Port Scanning Example.
From www.stationx.net
List of Common Ports Cheat Sheet Port Scanning Example Scan the first 1000 ports on a cidr range. One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a. A quick port scanning tutorial. A port scan attack helps cyber criminals find open ports. Port Scanning Example.
From tvasherbrooke.com
What is a Port Scanner and How Does it Work? (2023) Port Scanning Example One of my goals in developing nmap is to keep the most common usage simple, while retaining the flexibility for. Scan the first 1000 ports on a cidr range. A quick port scanning tutorial. Each listening service provides attack surface which could potentially be abused by attackers. A port scan attack helps cyber criminals find open ports and figure out.. Port Scanning Example.
From phaseisland17.gitlab.io
How To Detect Port Scanning Phaseisland17 Port Scanning Example A quick port scanning tutorial. It involves sending packets to specific ports and analyzing the. A port scan attack helps cyber criminals find open ports and figure out. A port scan is a common technique hackers use to discover open doors or weak points in a network. Scan the first 1000 ports on a cidr range. Each listening service provides. Port Scanning Example.
From www.codecademy.com
Cybersecurity Nmap TCP Connect Scan Codecademy Port Scanning Example A port scan is a common technique hackers use to discover open doors or weak points in a network. Port scanning is generally done in stages: Port scanning is done to try determine which services we can connect to. A port scanner is an application which is made to probe a host or server to identify open ports. Each listening. Port Scanning Example.