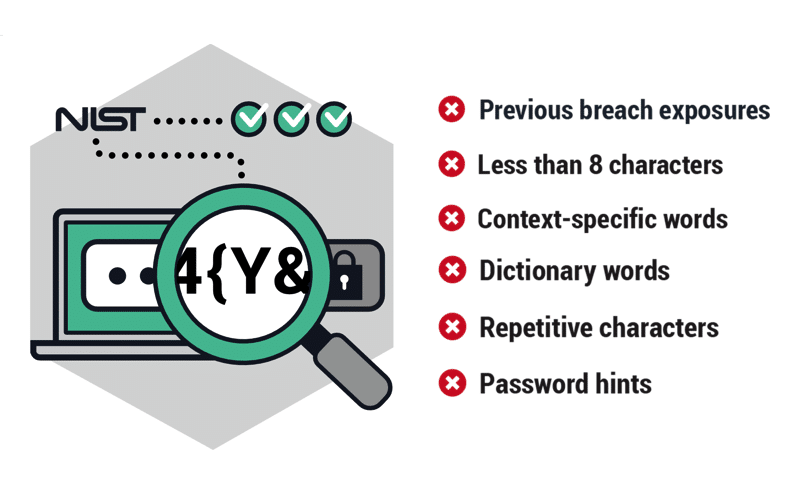
Authentication Security Requirements . In cyber security, authentication is the process of verifying someone's or something's identity. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from.
from spycloud.com
Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In cyber security, authentication is the process of verifying someone's or something's identity. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors.
Modernize Your Password Security Policy with Latest NIST Guidelines
Authentication Security Requirements Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. In cyber security, authentication is the process of verifying someone's or something's identity.
From cyberblogindia.in
Employed All Security Measures Yet? Let's Recapitulate Things TheCBI Authentication Security Requirements Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. A message authentication. Authentication Security Requirements.
From www.enisa.europa.eu
Security guidelines on the appropriate use of qualified website Authentication Security Requirements In cyber security, authentication is the process of verifying someone's or something's identity. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. Authentication requirements are. Authentication Security Requirements.
From spycloud.com
Modernize Your Password Security Policy with Latest NIST Guidelines Authentication Security Requirements Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. Authentication is important because it helps organizations protect. Authentication Security Requirements.
From www.authlete.com
OAuth 2.0 Stepup Authentication Challenge Protocol Authlete Authentication Security Requirements They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. Authentication requirements are important. Authentication Security Requirements.
From www.techtarget.com
What is user authentication? Authentication Security Requirements In cyber security, authentication is the process of verifying someone's or something's identity. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. Authentication is important because it helps organizations. Authentication Security Requirements.
From www.okta.com
Multifactor Authentication Deployment Guide Okta Authentication Security Requirements In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. In cyber security, authentication is the process of verifying someone's or something's identity. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. A message authentication code is a security code that the user of a. Authentication Security Requirements.
From purplesec.us
How To Develop & Implement A Network Security Plan Authentication Security Requirements Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim. Authentication Security Requirements.
From medevel.com
Top 10 Opensource Security testing frameworks Authentication Security Requirements A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. They define technical requirements in each of the areas of identity proofing, registration,. Authentication Security Requirements.
From www.duosecurity.com
August 2015 Deadline for TwoFactor Authentication in the European Authentication Security Requirements They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. In order to authenticate. Authentication Security Requirements.
From www.researchgate.net
IoT Architecture and security requirements. Download Table Authentication Security Requirements Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. In cyber security, authentication is the process of verifying someone's or something's identity. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. Authentication is the process of determining if. Authentication Security Requirements.
From medium.com
Authentication Controls. An access control system is the set of… by Authentication Security Requirements In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. A message authentication code. Authentication Security Requirements.
From www.strongdm.com
What is AAA Security? Authentication, Authorization, and Accounting Authentication Security Requirements In cyber security, authentication is the process of verifying someone's or something's identity. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. In order to authenticate at aal3, claimants. Authentication Security Requirements.
From www.slideserve.com
PPT Common Criteria PowerPoint Presentation, free download ID5661844 Authentication Security Requirements Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors.. Authentication Security Requirements.
From www.slideserve.com
PPT Securing a Telework Infrastructure Smart.IS Objectives and Authentication Security Requirements In cyber security, authentication is the process of verifying someone's or something's identity. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes,. Authentication Security Requirements.
From acodez.in
The Process of Authentication In Information Security Authentication Security Requirements A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. In cyber security, authentication is the process of verifying someone's or something's identity. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. Authentication is important. Authentication Security Requirements.
From learn.microsoft.com
認証方法と機能 Microsoft Entra Microsoft Learn Authentication Security Requirements Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. In cyber security, authentication is the process of verifying someone's. Authentication Security Requirements.
From www.spiceworks.com
What Is MultiFactor Authentication? Definition, Key Components, and Authentication Security Requirements Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. Authentication is important because it helps organizations protect their systems, data, networks, websites,. Authentication Security Requirements.
From www.conceptdraw.com
IT Security Solutions Authentication Security Requirements Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. A message authentication code is a security code that the user. Authentication Security Requirements.
From www.researchgate.net
Security Requirements Process Overview (Activity Diagram) Download Authentication Security Requirements They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In cyber security, authentication. Authentication Security Requirements.
From learn.microsoft.com
Memo 2209 multifactor authentication requirements overview Microsoft Authentication Security Requirements In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. A message authentication code is a security. Authentication Security Requirements.
From rublon.com
FTC Safeguards Rule Updates Its Security Requirements Rublon Authentication Security Requirements They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. Authentication is the process of determining if the person or entity. Authentication Security Requirements.
From www.slideserve.com
PPT Securing Passwords Against Dictionary Attacks PowerPoint Authentication Security Requirements A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors.. Authentication Security Requirements.
From www.slideserve.com
PPT Network Security Threats and Goals PowerPoint Presentation, free Authentication Security Requirements In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In cyber security, authentication is the process of verifying someone's. Authentication Security Requirements.
From www.progress.com
Data Security Authentication, Authorization & Encryption Authentication Security Requirements In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. A message authentication code is a security. Authentication Security Requirements.
From layots.com
Cloud Security Understanding the Shared Responsibility Model Layots Authentication Security Requirements Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal.. Authentication Security Requirements.
From www.thesslstore.com
What Is a Message Authentication Code (MAC)? Hashed Out by The SSL Store™ Authentication Security Requirements They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. A message authentication code is a security code that the user of a computer has to type in order to access any account. Authentication Security Requirements.
From www.isdecisions.com
MultiFactor Authentication for a Large Manufacturing Company to Meet Authentication Security Requirements In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes,. Authentication Security Requirements.
From www.techtarget.com
What is a password (OTP)? Definition from SearchSecurity Authentication Security Requirements Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. They define technical requirements. Authentication Security Requirements.
From www.slideserve.com
PPT Engineering Security Requirement PowerPoint Presentation, free Authentication Security Requirements They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. A message authentication code is a security code that the user of a computer has to type in order to access any account or portal. Authentication is. Authentication Security Requirements.
From www.geeksforgeeks.org
What is AAA (Authentication, Authorization, and Accounting Authentication Security Requirements In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. Authentication is important because. Authentication Security Requirements.
From www.collidu.com
Requirement Validation PowerPoint Presentation Slides PPT Template Authentication Security Requirements In cyber security, authentication is the process of verifying someone's or something's identity. Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In order to authenticate at aal3, claimants are required. Authentication Security Requirements.
From blog.unloq.io
The New NIST Digital Identity Guidelines Passwordless Security UNLOQ Authentication Security Requirements Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In cyber security, authentication is the process. Authentication Security Requirements.
From www.csoonline.com
Managing identity and access management in uncertain times CSO Online Authentication Security Requirements In order to authenticate at aal3, claimants are required to prove possession and control of two distinct authentication factors. In cyber security, authentication is the process of verifying someone's or something's identity. Authentication requirements are important because they help to fulfill many compliance requirements, including pci dss. A message authentication code is a security code that the user of a. Authentication Security Requirements.
From www.okta.com
Authentication vs. Authorization Okta Authentication Security Requirements Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In order to authenticate. Authentication Security Requirements.
From tnt.co.bw
What is TwoFactor Authentication (2FA)? Triton Tech Authentication Security Requirements They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols,. Authentication is important because it helps organizations protect their systems, data, networks, websites, and applications from. In cyber security, authentication is the process of verifying someone's or something's identity. Authentication is the process of determining if the person or entity accessing a. Authentication Security Requirements.