Access Control Security Protocol . Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control systems define the rules and policies that. By controlling who or what has. Only those that have had their identity verified can access company data through an access control gateway. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security policy that restricts access to places and/or data. Access control is a method of restricting access to sensitive data. Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Examples include virtual private networks (vpns) and zero trust. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them.
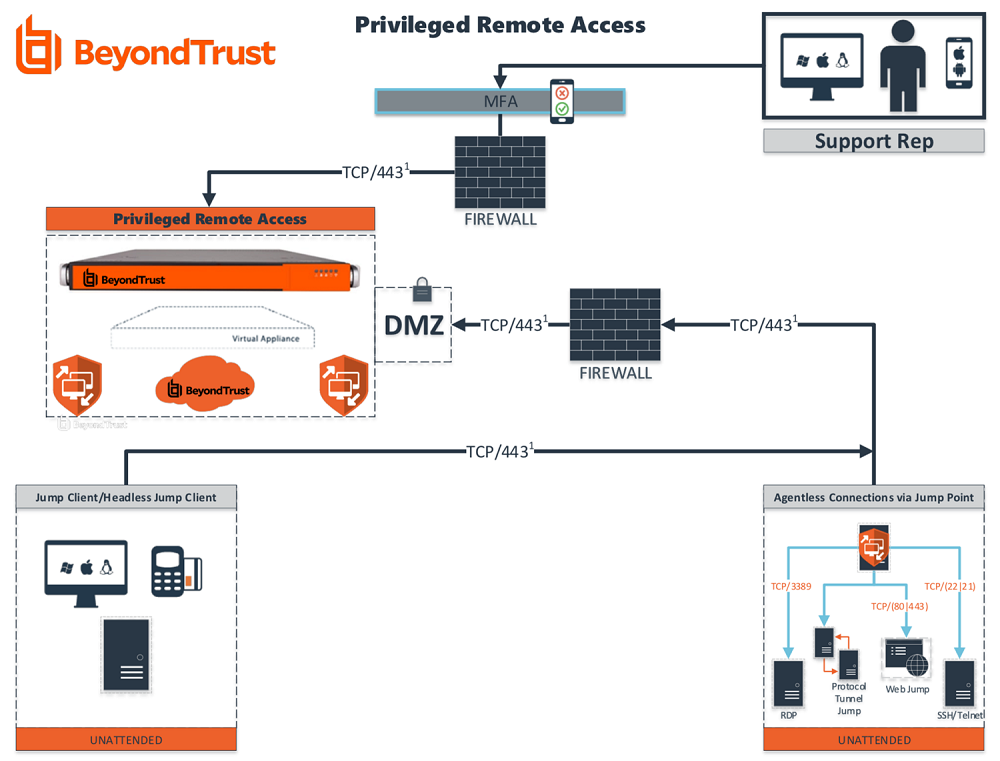
from www.beyondtrust.com
By controlling who or what has. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Only those that have had their identity verified can access company data through an access control gateway. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a method of restricting access to sensitive data. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a security policy that restricts access to places and/or data. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control systems define the rules and policies that.
How the Right Secure Remote Access Solution can Help You Reduce Costs & IT Security Risks
Access Control Security Protocol Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. By controlling who or what has. Access control is a security policy that restricts access to places and/or data. Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a method of restricting access to sensitive data. Examples include virtual private networks (vpns) and zero trust. Access control systems define the rules and policies that. Only those that have had their identity verified can access company data through an access control gateway.
From medium.com
Choosing the right access control strategy by Warren Parad Authress Oct, 2020 Medium Access Control Security Protocol Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a method of restricting access to sensitive data. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. By controlling who or. Access Control Security Protocol.
From getsafeandsound.com
Access Control System An Overview Access Control Security Protocol Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a security policy that restricts access to places and/or data. Access control is a method of restricting. Access Control Security Protocol.
From conciseservicesolutionsgroup.com
Security/Access Control Concise Service Solutions Group Access Control Security Protocol Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a security policy that restricts access to places and/or data. By controlling who or what has. Access control is a type of security measure that limits the visibility, access, and use of. Access Control Security Protocol.
From www.upguard.com
What is Access Control? The Essential Cybersecurity Practice UpGuard Access Control Security Protocol Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Only those that have had their identity verified can access company data through an access control gateway. Access control systems define the rules and policies that. By controlling who or what has. Access control is a method of restricting access. Access Control Security Protocol.
From homesecuritycamp.com
Essential Security Protocols in Access Control Systems Access Control Security Protocol Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.. Access Control Security Protocol.
From homesecuritycamp.com
Essential Security Protocols in Access Control Systems Access Control Security Protocol Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a method of restricting access to sensitive data. Access control is a security process that determines who can access certain resources (files, folders, apps, programs,. Access Control Security Protocol.
From cie-group.com
How to design an Access Control system Access Control Security Protocol Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Examples include virtual private networks (vpns) and zero trust. Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a method of restricting access to sensitive data. Access control is a type of security measure. Access Control Security Protocol.
From www.conceptdraw.com
Network Security Access Control Security Protocol Access control systems define the rules and policies that. Examples include virtual private networks (vpns) and zero trust. By controlling who or what has. Access control is a method of restricting access to sensitive data. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a type. Access Control Security Protocol.
From www.clearsoundsecurity.co.uk
Access Control Coventry Access Control Systems Clear Sound Security Access Control Security Protocol Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is. Access Control Security Protocol.
From issuu.com
Maintain Your Access Control Security System With These 10 Tips And Tricks! by iDLink Systems Access Control Security Protocol Access control is a security policy that restricts access to places and/or data. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a security process that determines who can access. Access Control Security Protocol.
From www.ateneodemontevideo.com
A Basic Guide To Door Access Control Systems in Accrington Ateneodemonte Video Access Control Security Protocol Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Examples include virtual private networks (vpns) and zero trust. Access control security encompasses the tools and processes that restrict. Access Control Security Protocol.
From www.csoonline.com
What is access control? A key component of data security CSO Online Access Control Security Protocol Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control systems define the rules and policies that. Access control is a method of restricting access to sensitive data. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.. Access Control Security Protocol.
From www.educba.com
Multiple Access Protocol Complete Guide on Multiple Access Protocol Access Control Security Protocol Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a method of restricting access to sensitive data. Only those that have had their identity verified can access company data through an access control gateway. Access control is a type of security measure that limits the visibility, access, and use of resources. Access Control Security Protocol.
From www.openpath.com
Importance of Access Control Security for your Business Access Control Security Protocol Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Examples include virtual private networks (vpns) and zero. Access Control Security Protocol.
From www.varonis.com
What is RoleBased Access Control (RBAC)? Access Control Security Protocol Access control is a security policy that restricts access to places and/or data. Access control systems define the rules and policies that. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a data security process that enables organizations to manage who is authorized to access. Access Control Security Protocol.
From www.gotyoursixcyber.com
Access Control Got Your Six Cybersecurity Access Control Security Protocol Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a type of security measure that limits the visibility, access, and use of resources in. Access Control Security Protocol.
From wentzwu.com
Discretionary and NonDiscretionary Access Control Policies by Wentz Wu, ISSAP, ISSEP, ISSMP Access Control Security Protocol Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control systems define the rules and policies that. Access control is a security policy that restricts access to places and/or data. Examples include virtual private networks (vpns) and zero trust. Only those that have had their identity verified. Access Control Security Protocol.
From www.ir.com
Understanding Network Security Tools & Protection IR Access Control Security Protocol Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Examples include virtual private networks (vpns) and zero trust. By controlling who or what has. Only those that have had their identity verified. Access Control Security Protocol.
From embetronicx.com
Diagnostics and Communication Management UDS Protocol Guide Access Control Security Protocol Only those that have had their identity verified can access company data through an access control gateway. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Examples include virtual private networks (vpns) and zero trust. Access control is a security policy that restricts access to places and/or data.. Access Control Security Protocol.
From lionsgate.io
3D Secure Authentication Protocol Lions Gate Access Control Security Protocol Examples include virtual private networks (vpns) and zero trust. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a security process that determines who can. Access Control Security Protocol.
From its-physec.com
Access Control Physical Security Solutions ITS Physec Access Control Security Protocol Access control systems define the rules and policies that. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. By controlling who or what has. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a security process that determines who. Access Control Security Protocol.
From medium.com
CSMA/CA — Wireless Medium Access Control Protocol by Geeky much! Networks & Security Medium Access Control Security Protocol Access control is a method of restricting access to sensitive data. Examples include virtual private networks (vpns) and zero trust. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.. Access Control Security Protocol.
From searchcloudcomputing.techtarget.com
Secure data in the cloud with encryption and access controls Access Control Security Protocol Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Only those that. Access Control Security Protocol.
From www.youtube.com
VPNs and Remote Access Protocols CompTIA Security+ Performance Based Question YouTube Access Control Security Protocol Examples include virtual private networks (vpns) and zero trust. Access control is a security policy that restricts access to places and/or data. Only those that have had their identity verified can access company data through an access control gateway. Access control is a method of restricting access to sensitive data. Access control is a type of security measure that limits. Access Control Security Protocol.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Access Control Security Protocol Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control systems define the rules and policies that. Access control is a proactive. Access Control Security Protocol.
From www.slideshare.net
Multiple access control protocol Access Control Security Protocol Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a data security process that enables organizations to manage who is authorized to access corporate data and.. Access Control Security Protocol.
From www.beyondtrust.com
How the Right Secure Remote Access Solution can Help You Reduce Costs & IT Security Risks Access Control Security Protocol Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Only those that have had their identity verified can access company data through an access control gateway. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can. Access Control Security Protocol.
From gogetsecure.com
Network Security Archives GoGet Secure Access Control Security Protocol Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control systems define the rules and policies that. Examples include virtual private networks (vpns) and zero trust. Access control is a data security process that enables organizations to manage who is authorized to access. Access Control Security Protocol.
From wittenbach.com
Branch Security Access Control Access Control Security Protocol Only those that have had their identity verified can access company data through an access control gateway. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control systems define the rules and policies that. Access control is a type of security measure that limits the visibility, access, and use of resources in a. Access Control Security Protocol.
From www.linkedin.com
Multiple access protocols Access Control Security Protocol Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control systems define the rules and policies that. Access control is a security policy that restricts access to places and/or data. Only those that have had their identity verified can access company data through an access control gateway.. Access Control Security Protocol.
From dallasmeowgiles.blogspot.com
Which of the Following Correctly Describes a Security Patch Access Control Security Protocol Access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Only those that have. Access Control Security Protocol.
From www.bitdefender.com
Types of Security Protocols Bitdefender Cyberpedia Access Control Security Protocol Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Examples include virtual private networks (vpns) and zero trust. Access control systems define the. Access Control Security Protocol.
From www.slideserve.com
PPT IS3340 Windows Security Unit 2 Setting up Windows Systems with Secure Access Controls Access Control Security Protocol Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Only those that have had their identity verified can access company data through an access control gateway. Access control systems define the rules and policies that. Access control is a method of restricting access to. Access Control Security Protocol.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Access Control Security Protocol Access control is a security policy that restricts access to places and/or data. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control security encompasses the tools and processes that restrict access to resources in an it infrastructure. Only those that have had their identity verified can. Access Control Security Protocol.
From homesecuritycamp.com
Essential Security Protocols in Access Control Systems Access Control Security Protocol By controlling who or what has. Access control is a method of restricting access to sensitive data. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Only those that have had their identity verified can access company data through an access control gateway. Access control is a security policy that restricts access to places. Access Control Security Protocol.