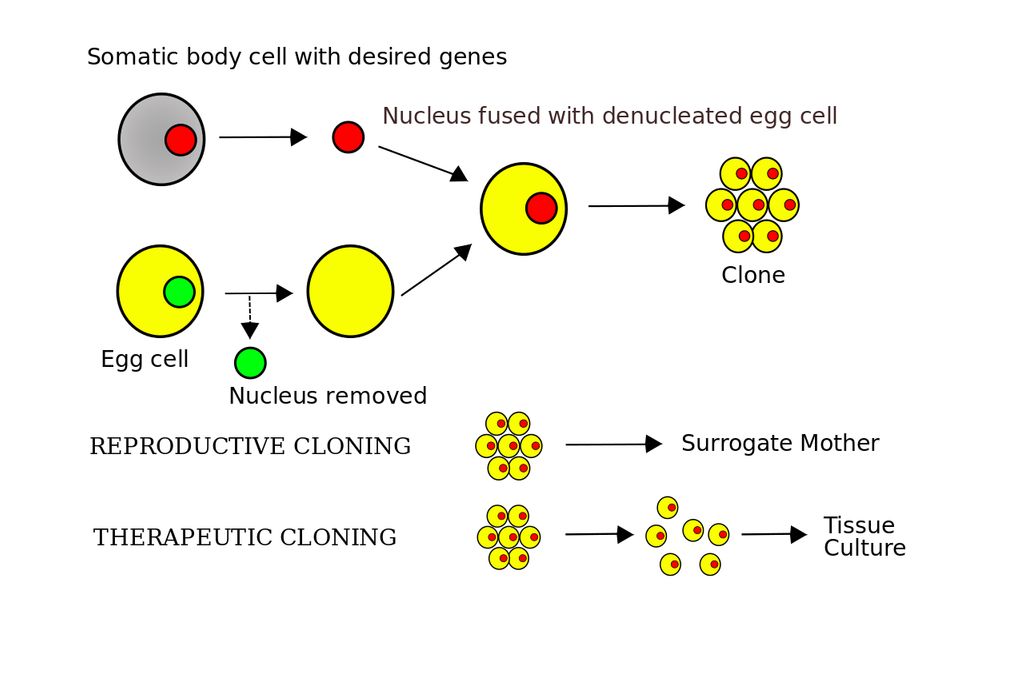
What Is Cloning In It . Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Now, you might wonder, that is what we did while forking the repository!! Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into.
from wrytin.com
Now, you might wonder, that is what we did while forking the repository!! Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning is a process of creating an identical copy of a git remote repository to the local machine. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data.
Human Cloning Wrytin
What Is Cloning In It Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Now, you might wonder, that is what we did while forking the repository!! Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository.
From www.discovermagazine.com
Cloning's Long Legacy — And Why It'll Never Be Used on Humans What Is Cloning In It Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning. What Is Cloning In It.
From geneticeducation.co.in
Gene cloning Definitions, Steps, Procedure, Applications and What Is Cloning In It Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a. What Is Cloning In It.
From www.biologyexams4u.com
5 Steps in Gene cloning What Is Cloning In It Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and. What Is Cloning In It.
From microbenotes.com
DNA Cloning Principle, Steps, Components, Methods, Uses What Is Cloning In It Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Now, you might wonder, that is what we did while forking the repository!! Cloning is a. What Is Cloning In It.
From www.slideserve.com
PPT Cloning PowerPoint Presentation, free download ID228029 What Is Cloning In It Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Now, you might wonder, that is what we did while forking the repository!! Learn about the different cloning techniques, their. What Is Cloning In It.
From www.slideserve.com
PPT Cloning PowerPoint Presentation, free download ID2632240 What Is Cloning In It A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Now, you might wonder, that is what we did while forking the repository!! Learn about the different cloning techniques, their advantages,. What Is Cloning In It.
From thealevelbiologist.co.uk
cloning The A Level Biologist Your Hub What Is Cloning In It Cloning is a process of creating an identical copy of a git remote repository to the local machine. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Now, you. What Is Cloning In It.
From byjus.com
DNA Cloning Steps and Importance of DNA Cloning What Is Cloning In It Now, you might wonder, that is what we did while forking the repository!! Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Learn about the different cloning techniques, their. What Is Cloning In It.
From worldmedicinefoundation.com
The Biochemistry of Cloning worldmedicinefoundation What Is Cloning In It Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Learn. What Is Cloning In It.
From wrytin.com
Human Cloning Wrytin What Is Cloning In It Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks. What Is Cloning In It.
From www.slideserve.com
PPT Engineering and Cloning PowerPoint Presentation, free What Is Cloning In It A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Now, you might wonder, that. What Is Cloning In It.
From www.shalom-education.com
Cloning in Animals GCSE Biology Revision What Is Cloning In It Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Now, you might wonder, that is what we did while forking the repository!! Cloning in cyber security is a tactic used. What Is Cloning In It.
From shania-has-atkinson.blogspot.com
Describe How Cloning Works in Your Own Words ShaniahasAtkinson What Is Cloning In It Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. A. What Is Cloning In It.
From microbenotes.com
Gene Cloning Requirements, Principle, Steps, Applications What Is Cloning In It Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning. What Is Cloning In It.
From study.com
DNA Cloning Definition and Process Video & Lesson Transcript What Is Cloning In It Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick. What Is Cloning In It.
From www.vectorstock.com
Animal cloning charts infographic Royalty Free Vector Image What Is Cloning In It Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email. What Is Cloning In It.
From www.slideserve.com
PPT Introduction to Human Cloning PowerPoint Presentation, free What Is Cloning In It Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning in. What Is Cloning In It.
From study.com
Human Cloning Definition, Pros & Cons Lesson What Is Cloning In It Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a process of creating an identical copy of a git remote repository to the local. What Is Cloning In It.
From byjus.com
What is cloning? List the basic steps involved in this process. What Is Cloning In It A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Learn. What Is Cloning In It.
From primadonablog.blogspot.com
Did You Know About Cloning Development of Science. What Is Cloning In It Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks. What Is Cloning In It.
From courses.lumenlearning.com
Cloning Biology for NonMajors I What Is Cloning In It Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Learn how. What Is Cloning In It.
From eduinput.com
What is cloning? Types, process, advantages, and disadvantages What Is Cloning In It Now, you might wonder, that is what we did while forking the repository!! Cloning is a process of creating an identical copy of a git remote repository to the local machine. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Cloning is a technique that creates a duplicate of an object,. What Is Cloning In It.
From www.genome.gov
Cloning Fact Sheet What Is Cloning In It Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Now, you might wonder, that is what we did while forking the repository!! A clone is. What Is Cloning In It.
From commons.wikimedia.org
FileCloning diagram english.png What Is Cloning In It Now, you might wonder, that is what we did while forking the repository!! Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning in cyber security is a. What Is Cloning In It.
From bio.libretexts.org
10.1 Cloning and Engineering Biology LibreTexts What Is Cloning In It Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users. What Is Cloning In It.
From www.slideserve.com
PPT Different types of cloning PowerPoint Presentation, free download What Is Cloning In It A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Now, you might wonder, that is what we did while forking the repository!! Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Learn about the different cloning techniques, their advantages,. What Is Cloning In It.
From civilspedia.com
Cloning What Is Cloning In It Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users. What Is Cloning In It.
From www.youtube.com
DNA cloning (overview) gene cloning What is the purpose of DNA What Is Cloning In It Cloning is a process of creating an identical copy of a git remote repository to the local machine. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard. What Is Cloning In It.
From courses.lumenlearning.com
Cloning Biology for Majors I What Is Cloning In It Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Now, you might wonder, that is what we did while forking the repository!! Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. Cloning is a technique that creates. What Is Cloning In It.
From www.slideserve.com
PPT Introduction to Human Cloning PowerPoint Presentation, free What Is Cloning In It Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Now, you might wonder, that is what we did while forking the repository!! Learn how to use the ‘git clone’. What Is Cloning In It.
From www.youtube.com
Steps in Gene Cloning A Complete Comprehensive Concept Video YouTube What Is Cloning In It Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Learn how. What Is Cloning In It.
From rajusbiology.com
Gene Cloning Definition, Steps, Applications and Diagram Rajus Biology What Is Cloning In It Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning is a technique that creates a duplicate of an object, system, or network to prevent cyber attacks and safeguard sensitive data. Now, you might wonder, that is what we did while forking the repository!! Learn how to use the ‘git. What Is Cloning In It.
From lozierinstitute.org
Cloning is Cloning is Cloning Lozier Institute What Is Cloning In It A clone is where you have proper duplication, and separation between, two (possibly different) versions of a repository. Learn how to use the ‘git clone’ command to copy a git repository from a remote server to your local machine. Now, you might wonder, that is what we did while forking the repository!! Cloning is a technique that creates a duplicate. What Is Cloning In It.
From www.biologyonline.com
Cloning Definition and Examples Biology Online Dictionary What Is Cloning In It Now, you might wonder, that is what we did while forking the repository!! Learn about the different cloning techniques, their advantages, and how to detect and prevent cloning attacks in cyber security. Cloning is a process of creating an identical copy of a git remote repository to the local machine. Learn how to use the ‘git clone’ command to copy. What Is Cloning In It.
From www.genome.gov
Cloning Fact Sheet What Is Cloning In It Now, you might wonder, that is what we did while forking the repository!! Cloning is a process of creating an identical copy of a git remote repository to the local machine. Cloning in cyber security is a tactic used by malicious actors to replicate legitimate websites or email addresses to trick users into. A clone is where you have proper. What Is Cloning In It.