How To Prove Hacking . Good security and firewall will stop all but the best of hackers from using. The primary federal law enforcement agencies that. Check out these expert tips to identify risk and. Check out these 12 signs that you may have been hacked and what. If you see messages you did not send,. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Enter your zip code to see attorneys available in your area. Here are 9 steps to figuring out. Learn common signs of phone hackings to see if your device is compromised. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Concerned that someone may be hacking into your device?
from community.gamedev.tv
Here are 9 steps to figuring out. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Concerned that someone may be hacking into your device? Check out these expert tips to identify risk and. Learn common signs of phone hackings to see if your device is compromised. Good security and firewall will stop all but the best of hackers from using. The primary federal law enforcement agencies that. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. If you see messages you did not send,. Enter your zip code to see attorneys available in your area.
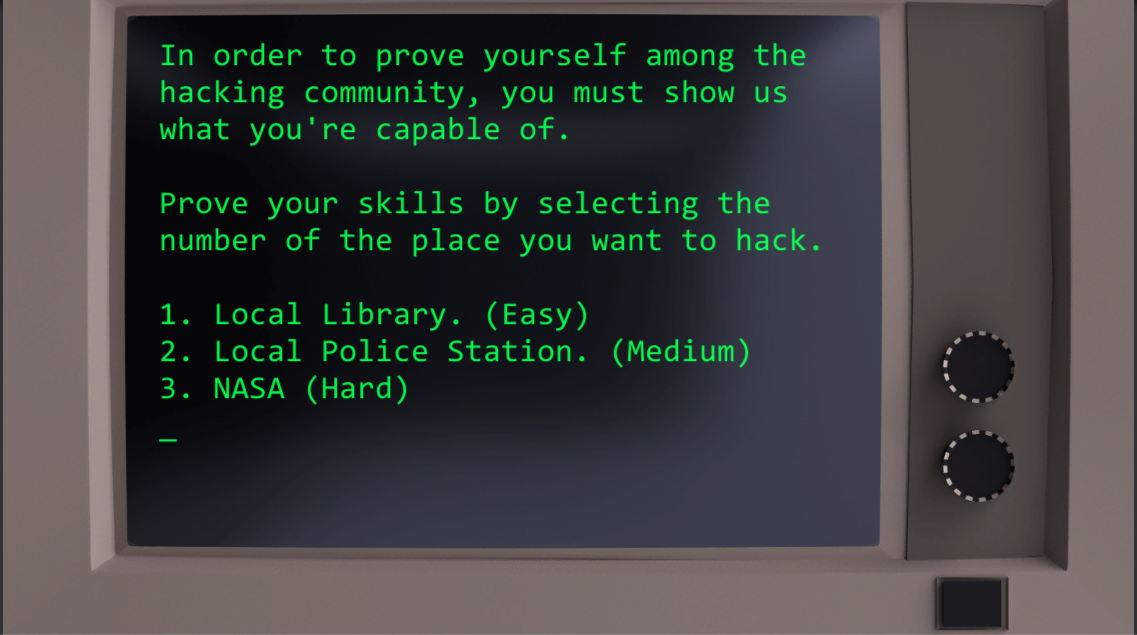
Prove your hacking skills Show GameDev.tv
How To Prove Hacking Good security and firewall will stop all but the best of hackers from using. Check out these 12 signs that you may have been hacked and what. Good security and firewall will stop all but the best of hackers from using. Check out these expert tips to identify risk and. The primary federal law enforcement agencies that. Here are 9 steps to figuring out. Enter your zip code to see attorneys available in your area. If you see messages you did not send,. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Learn common signs of phone hackings to see if your device is compromised. Concerned that someone may be hacking into your device? Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns.
From www.picswallpaper.com
79 How To Hack Hackers Back For FREE My How To Prove Hacking Good security and firewall will stop all but the best of hackers from using. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Check out these expert tips to identify risk and. If you see messages you did not send,. The best way to narrow down the field of suspects is. How To Prove Hacking.
From medium.com
What hackers use for hacking?. The Tools of the Trade What Hackers How To Prove Hacking Learn common signs of phone hackings to see if your device is compromised. Check out these 12 signs that you may have been hacked and what. Check out these expert tips to identify risk and. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Good security and firewall will. How To Prove Hacking.
From null-byte.wonderhowto.com
Advice from a Real Hacker How to Protect Yourself from Being Hacked How To Prove Hacking Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. The primary federal law enforcement agencies that. If you see messages you did not send,. Check out these expert tips to identify risk and. Check out these 12 signs that you may have been hacked and what. Concerned that someone may be. How To Prove Hacking.
From plmleisure.weebly.com
Ethical hacking tools online plmleisure How To Prove Hacking Enter your zip code to see attorneys available in your area. Check out these expert tips to identify risk and. Concerned that someone may be hacking into your device? Good security and firewall will stop all but the best of hackers from using. If you see messages you did not send,. Hackers take control of accounts to breach friends and. How To Prove Hacking.
From www.huffingtonpost.com
Hacking For A Cure Innovative Scientists Fill Federal Research Gaps How To Prove Hacking Check out these 12 signs that you may have been hacked and what. The primary federal law enforcement agencies that. Concerned that someone may be hacking into your device? Learn common signs of phone hackings to see if your device is compromised. Check out these expert tips to identify risk and. If you see messages you did not send,. Good. How To Prove Hacking.
From www.eccouncil.org
Best Ethical Hacking Tools 100 Hacking Tools & Software How To Prove Hacking Learn common signs of phone hackings to see if your device is compromised. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. The primary federal law enforcement agencies that. Check out these expert tips to identify risk and. Concerned that someone may be hacking into your device? Check out. How To Prove Hacking.
From tryhardguides.com
A Hacker To Prove Dad Wrong Tycoon Codes Try Hard Guides How To Prove Hacking Check out these 12 signs that you may have been hacked and what. Check out these expert tips to identify risk and. Learn common signs of phone hackings to see if your device is compromised. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. The primary federal law enforcement. How To Prove Hacking.
From www.sdgyoungleaders.org
The Different Types of Hacking Techniques Explained A Helpful Guide How To Prove Hacking Enter your zip code to see attorneys available in your area. Here are 9 steps to figuring out. Good security and firewall will stop all but the best of hackers from using. Check out these expert tips to identify risk and. Learn common signs of phone hackings to see if your device is compromised. Check out these 12 signs that. How To Prove Hacking.
From theruntime.com
10 Best Ethical Hacking Tools in 2023 The Run Time How To Prove Hacking Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Check out these 12 signs that you may have been hacked and what. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Here are 9 steps to figuring out. Concerned that. How To Prove Hacking.
From www.droidgamers.com
A Hacker To Prove Dad Wrong Tycoon Codes Droid Gamers How To Prove Hacking Check out these expert tips to identify risk and. Good security and firewall will stop all but the best of hackers from using. If you see messages you did not send,. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Enter your zip code to see attorneys available in your area.. How To Prove Hacking.
From store.pothi.com
Hacking For Beginners a beginners guide for learning hacking How To Prove Hacking Here are 9 steps to figuring out. If you see messages you did not send,. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Enter your zip code to see attorneys available in your area. Check out these 12 signs that you may have been hacked and what. The best way. How To Prove Hacking.
From community.gamedev.tv
Prove your hacking skills Show GameDev.tv How To Prove Hacking Enter your zip code to see attorneys available in your area. Learn common signs of phone hackings to see if your device is compromised. If you see messages you did not send,. The primary federal law enforcement agencies that. Concerned that someone may be hacking into your device? The best way to narrow down the field of suspects is to. How To Prove Hacking.
From www.knowledgehut.com
Ethical Hacking Techniques and Tools How To Prove Hacking Check out these expert tips to identify risk and. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Check out these 12 signs that you may have been hacked and what. Good security and firewall will stop all but the best of hackers from using. Here are 9 steps. How To Prove Hacking.
From techtechnik.com
How to get started with HACKING (Beginner's Hacking Guide 2018) Tech How To Prove Hacking Enter your zip code to see attorneys available in your area. Check out these expert tips to identify risk and. If you see messages you did not send,. Good security and firewall will stop all but the best of hackers from using. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns.. How To Prove Hacking.
From www.cyberwiki.in
Phases of Hacking CyberWiki Encyclopedia of Cybersecurity How To Prove Hacking Check out these expert tips to identify risk and. Here are 9 steps to figuring out. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Learn common signs of phone hackings. How To Prove Hacking.
From fossbytes.com
Top 10 Common Hacking Techniques You Should Know About How To Prove Hacking Enter your zip code to see attorneys available in your area. The primary federal law enforcement agencies that. Concerned that someone may be hacking into your device? Check out these expert tips to identify risk and. Here are 9 steps to figuring out. Learn common signs of phone hackings to see if your device is compromised. The best way to. How To Prove Hacking.
From ebook-hunter.org
Hacking Hacking For Beginners Guide On How To Hack Computer Hacking How To Prove Hacking The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Here are 9 steps to figuring out. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Good security and firewall will stop all but the best of hackers from using. The. How To Prove Hacking.
From www.geeksforgeeks.org
5 Phases of Hacking How To Prove Hacking Check out these 12 signs that you may have been hacked and what. Good security and firewall will stop all but the best of hackers from using. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Concerned that someone may be hacking into your device? Hackers take control of. How To Prove Hacking.
From www.ms4security.com
How To do Ethical Hacking [Process Guide] How To Prove Hacking Learn common signs of phone hackings to see if your device is compromised. The primary federal law enforcement agencies that. Here are 9 steps to figuring out. If you see messages you did not send,. Check out these 12 signs that you may have been hacked and what. Check out these expert tips to identify risk and. Concerned that someone. How To Prove Hacking.
From www.desertcart.com.au
Buy HACKING WITH KALI LINUX A StepByStep Beginners Learning Guide On How To Prove Hacking The primary federal law enforcement agencies that. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. If you see messages you did not send,. Check out these 12 signs that you may have been hacked and what. Hackers take control of accounts to breach friends and family and, most. How To Prove Hacking.
From www.programmingcube.com
10 Best Ethical Hacking Software & Tools for Hackers [2022 How To Prove Hacking Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. If you see messages you did not send,. Check out these 12 signs that you may have been hacked and what. Concerned that someone may be hacking into your device? The primary federal law enforcement agencies that. Good security and firewall will. How To Prove Hacking.
From www.pymnts.com
Simple Hacking Techniques Prove Successful in 2023 Cyberattacks How To Prove Hacking The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Learn common signs of phone hackings to see if your device is compromised. If you see messages you did not send,. The primary federal law enforcement agencies that. Hackers take control of accounts to breach friends and family and, most. How To Prove Hacking.
From mertqzoo.weebly.com
Hacking tools online mertqzoo How To Prove Hacking Here are 9 steps to figuring out. Check out these 12 signs that you may have been hacked and what. The primary federal law enforcement agencies that. Concerned that someone may be hacking into your device? Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Good security and firewall will stop. How To Prove Hacking.
From www.phambano.org.za
Hacking Learn How to Avoid Being Hacked Phambano Technology How To Prove Hacking If you see messages you did not send,. Check out these 12 signs that you may have been hacked and what. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. The. How To Prove Hacking.
From www.digitaltrends.com
How to Hack WiFi Digital Trends How To Prove Hacking Check out these 12 signs that you may have been hacked and what. The primary federal law enforcement agencies that. Here are 9 steps to figuring out. If you see messages you did not send,. Good security and firewall will stop all but the best of hackers from using. Learn common signs of phone hackings to see if your device. How To Prove Hacking.
From www.wikihow.com
The 4 Best Ways to Hack a site wikiHow How To Prove Hacking Check out these 12 signs that you may have been hacked and what. Concerned that someone may be hacking into your device? The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. The primary federal law enforcement agencies that. Good security and firewall will stop all but the best of. How To Prove Hacking.
From www.ccsipro.com
Tips to Prevent Hacking Creative Computer Solutions, Inc How To Prove Hacking Here are 9 steps to figuring out. Good security and firewall will stop all but the best of hackers from using. Learn common signs of phone hackings to see if your device is compromised. The primary federal law enforcement agencies that. Concerned that someone may be hacking into your device? The best way to narrow down the field of suspects. How To Prove Hacking.
From www.cnabiera.com
Account hacking techniques you should be aware of How To Prove Hacking If you see messages you did not send,. Check out these 12 signs that you may have been hacked and what. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Enter your zip code to see attorneys available in your area. Hackers take control of accounts to breach friends. How To Prove Hacking.
From www.vpnmentor.com
The Ultimate Guide to Ethical Hacking What You Need to Know in 2024 How To Prove Hacking Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Check out these 12 signs that you may have been hacked and what. Check out these expert tips to identify risk and. Good security and firewall will stop all but the best of hackers from using. Learn common signs of phone hackings. How To Prove Hacking.
From www.fraud.com
What is hacking? Understanding the risks and prevention techniques How To Prove Hacking The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. The primary federal law enforcement agencies that. Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Learn common signs of phone hackings to see if your device is compromised. Here are. How To Prove Hacking.
From us.norton.com
What is a hacker? + how to protect yourself Norton How To Prove Hacking The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Learn common signs of phone hackings to see if your device is compromised. The primary federal law enforcement agencies that. Enter your zip code to see attorneys available in your area. Concerned that someone may be hacking into your device?. How To Prove Hacking.
From www.globaltechcouncil.org
Hacking Vs Ethical Hacking All You Need To Know How To Prove Hacking The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Good security and firewall will stop all but the best of hackers from using. Check out these expert tips to identify risk and. Learn common signs of phone hackings to see if your device is compromised. Here are 9 steps. How To Prove Hacking.
From www.youtube.com
5 Common Hacking Techniques Explain ? How to Be Safe YouTube How To Prove Hacking Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Learn common signs of phone hackings to see if your device is compromised. The primary federal law enforcement agencies that. Check out these 12 signs that you may have been hacked and what. The best way to narrow down the field of. How To Prove Hacking.
From www.hackersecret.com
The Most Authoritative Site in the World on the How To Prove Hacking Enter your zip code to see attorneys available in your area. Here are 9 steps to figuring out. Good security and firewall will stop all but the best of hackers from using. Learn common signs of phone hackings to see if your device is compromised. Check out these 12 signs that you may have been hacked and what. If you. How To Prove Hacking.
From www.techradar.com
How to recover from a hacking attack TechRadar How To Prove Hacking Hackers take control of accounts to breach friends and family and, most commonly, to launch spam malware campaigns. Enter your zip code to see attorneys available in your area. If you see messages you did not send,. The best way to narrow down the field of suspects is to determine exactly how your phone is being compromised. Concerned that someone. How To Prove Hacking.