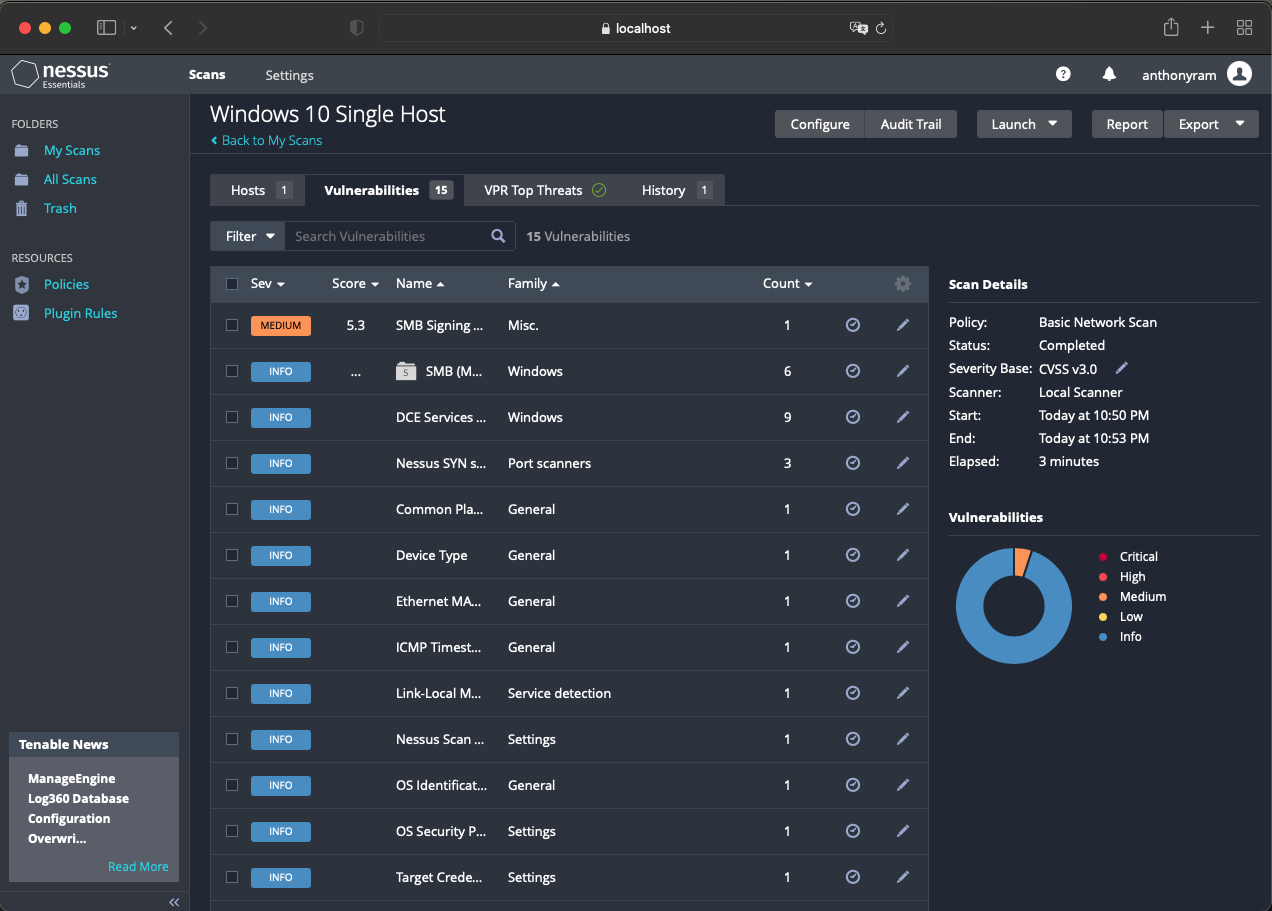
Security Scan Dashboard . Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. This article covers the basics of vulnerability scanning, the six step process, the types of. Tenable recommends configuring several data sources to optimize the data you see in. Dashboards display vulnerability, event, and other scan data. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Browse and download dashboard templates for. By increasing visibility into the vulnerability status of their network, security teams can. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use.
from www.anthonyram.com
Dashboards display vulnerability, event, and other scan data. Browse and download dashboard templates for. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. By increasing visibility into the vulnerability status of their network, security teams can. Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Tenable recommends configuring several data sources to optimize the data you see in. This article covers the basics of vulnerability scanning, the six step process, the types of. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use.
A Guide to installing and using the Nessus Vulnerability scanner
Security Scan Dashboard This article covers the basics of vulnerability scanning, the six step process, the types of. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Dashboards display vulnerability, event, and other scan data. Browse and download dashboard templates for. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Tenable recommends configuring several data sources to optimize the data you see in. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. This article covers the basics of vulnerability scanning, the six step process, the types of. Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. By increasing visibility into the vulnerability status of their network, security teams can.
From wpastra.com
15 Best Online Security Scanners for Detecting Malware Security Scan Dashboard Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Browse and download dashboard templates for. By increasing visibility into the vulnerability status of their network, security teams can. Tenable recommends configuring several data sources to optimize the data you see in. Dashboards display vulnerability, event, and other. Security Scan Dashboard.
From www.tenable.com
Nessus Scan Summary Dashboards SC Dashboard Tenable® Security Scan Dashboard Dashboards display vulnerability, event, and other scan data. By increasing visibility into the vulnerability status of their network, security teams can. Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Tenable recommends configuring several data sources to optimize the data you see in. Learn what vulnerability scanning. Security Scan Dashboard.
From www.isaca.org
Cyberrisk Governance A Practical Guide for Implementation Security Scan Dashboard Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Tenable recommends configuring several data sources to optimize the data you see in. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Browse and download dashboard templates for. This article covers the basics of vulnerability scanning, the. Security Scan Dashboard.
From www.qualys.com
Integrations for Public Cloud Security and Compliance Qualys Security Scan Dashboard Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Browse. Security Scan Dashboard.
From laptrinhx.com
How To Run Your First Vulnerability Scan with Nessus LaptrinhX Security Scan Dashboard By increasing visibility into the vulnerability status of their network, security teams can. This article covers the basics of vulnerability scanning, the six step process, the types of. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk.. Security Scan Dashboard.
From purplesec.us
Network Vulnerability Scanning & Assessment Services PurpleSec Security Scan Dashboard This article covers the basics of vulnerability scanning, the six step process, the types of. Dashboards display vulnerability, event, and other scan data. By increasing visibility into the vulnerability status of their network, security teams can. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. The vulnerability trend dashboard monitors detected vulnerabilities on. Security Scan Dashboard.
From mavink.com
Cyber Security Metrics Dashboard Security Scan Dashboard Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. This article covers the basics of vulnerability scanning, the six step process, the types of. Tenable recommends configuring several data sources to optimize the data you see in. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s. Security Scan Dashboard.
From www.qualys.com
Qualys Security Configuration Assessment (SCA) Qualys Security Scan Dashboard The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Learn how to use nessus scanners to audit your network for security. Security Scan Dashboard.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Security Scan Dashboard By increasing visibility into the vulnerability status of their network, security teams can. Browse and download dashboard templates for. Tenable recommends configuring several data sources to optimize the data you see in. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Dashboards display vulnerability, event, and other scan data. Learn how to use nessus scanners to audit your. Security Scan Dashboard.
From www.anthonyram.com
A Guide to installing and using the Nessus Vulnerability scanner Security Scan Dashboard Tenable recommends configuring several data sources to optimize the data you see in. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Browse and download dashboard templates for. Learn what vulnerability scanning is, how it works, why. Security Scan Dashboard.
From dribbble.com
Security Scans Dashboard by Astrid Kadel for SAP The Tools Team on Security Scan Dashboard Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Tenable recommends configuring several data sources to optimize the data you see in. Learn what vulnerability scanning. Security Scan Dashboard.
From community.splunk.com
Nessus security scans dashboard and drilldown Splunk Community Security Scan Dashboard By increasing visibility into the vulnerability status of their network, security teams can. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Dashboards display vulnerability, event, and other scan data. This article covers the basics of vulnerability scanning, the six step process,. Security Scan Dashboard.
From blog.qualys.com
Introducing CyberSecurity Asset Management 2.0 with Natively Integrated Security Scan Dashboard Tenable recommends configuring several data sources to optimize the data you see in. By increasing visibility into the vulnerability status of their network, security teams can. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Learn what vulnerability scanning is, how it works, why it's important, and what. Security Scan Dashboard.
From www.tenable.com
PCI Scan Monitoring Dashboard SC Dashboard Tenable® Security Scan Dashboard The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Tenable recommends configuring several data sources to optimize the data you see in. Dashboards display vulnerability, event, and other scan data. Learn how to use nessus scanners to. Security Scan Dashboard.
From lywand.com
lywand's Produktneuheit Der interne Audit lywand Security Scan Dashboard The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Tenable recommends configuring several data sources to optimize the data you see in. Dashboards display vulnerability, event, and other scan data. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. By increasing visibility into the vulnerability status of their network, security teams. Security Scan Dashboard.
From www.slideteam.net
MustHave Operational Risk Dashboard Templates with Samples and Examples Security Scan Dashboard Tenable recommends configuring several data sources to optimize the data you see in. Dashboards display vulnerability, event, and other scan data. Browse and download dashboard templates for. By increasing visibility into the vulnerability status of their network, security teams can. This article covers the basics of vulnerability scanning, the six step process, the types of. The vulnerability trend dashboard monitors. Security Scan Dashboard.
From grafana.com
How to manage CVE security vulnerabilities with Grafana, MergeStat, and Security Scan Dashboard Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. This article covers the basics of vulnerability scanning, the six step process, the types of. Browse and. Security Scan Dashboard.
From www.tenable.com
Council on CyberSecurity 20 Critical Security Controls Dashboard Security Scan Dashboard Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Tenable recommends configuring several data sources to optimize the data you see in. This article covers the basics of vulnerability scanning, the six step process, the types of. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s. Security Scan Dashboard.
From about.gitlab.com
How GitLab improves cloud native application security and protection Security Scan Dashboard Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Dashboards display vulnerability, event, and other scan data. This article covers the basics of vulnerability scanning, the six step process, the types of. By increasing visibility into the vulnerability status of their network, security teams can. The vulnerability. Security Scan Dashboard.
From www.tenable.com
Endpoint Security with Nessus® Agents Blog Tenable® Security Scan Dashboard Dashboards display vulnerability, event, and other scan data. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. This article covers the basics of vulnerability scanning, the six step process, the types of. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Browse and download dashboard templates for. By increasing visibility into. Security Scan Dashboard.
From www.n-able.com
CloudBased Antivirus Solution Nable Security Scan Dashboard This article covers the basics of vulnerability scanning, the six step process, the types of. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Dashboards display vulnerability, event, and other scan data. Browse and download dashboard templates for. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and. Security Scan Dashboard.
From www.thesmartscanner.com
Scan Dashboard SmartScanner Security Scan Dashboard Dashboards display vulnerability, event, and other scan data. Browse and download dashboard templates for. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn what vulnerability scanning is, how it works, why it's important, and what tools. Security Scan Dashboard.
From www.infosecmatter.com
Detailed Overview of Nessus Professional InfosecMatter Security Scan Dashboard Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Tenable recommends configuring several data sources to optimize the data you see in. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. By increasing visibility into the vulnerability status of their network, security teams can. Learn. Security Scan Dashboard.
From www.crowdstrike.com
What is Container Security? CrowdStrike Security Scan Dashboard Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. By increasing visibility into the vulnerability status of their network, security teams can. Dashboards display vulnerability, event, and other scan data. The vulnerability. Security Scan Dashboard.
From www.qualys.com
Qualys Expands Its Endpoint Security Solution with RealTime Malware Security Scan Dashboard Tenable recommends configuring several data sources to optimize the data you see in. This article covers the basics of vulnerability scanning, the six step process, the types of. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their. Security Scan Dashboard.
From www.openrmf.io
OpenRMF An Open Source Risk Management Framework tool Security Scan Dashboard Dashboards display vulnerability, event, and other scan data. Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Browse and download dashboard templates for. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. By increasing visibility into the vulnerability status of. Security Scan Dashboard.
From www.tenable.com
ACAS Scan Quick Credential Debug Scan Tenable® Security Scan Dashboard By increasing visibility into the vulnerability status of their network, security teams can. Browse and download dashboard templates for. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Dashboards display vulnerability, event, and other scan data. This. Security Scan Dashboard.
From help.sumologic.com
CrowdStrike Falcon Endpoint Protection Sumo Logic Docs Security Scan Dashboard Tenable recommends configuring several data sources to optimize the data you see in. By increasing visibility into the vulnerability status of their network, security teams can. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of. Security Scan Dashboard.
From blog.qualys.com
Unified Dashboard Preview for Enhanced Security Visualization Qualys Security Scan Dashboard Tenable recommends configuring several data sources to optimize the data you see in. By increasing visibility into the vulnerability status of their network, security teams can. Browse and download dashboard templates for. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. This article covers the basics of vulnerability scanning, the six step process,. Security Scan Dashboard.
From about.gitlab.com
How GitLab's application security dashboard helps AppSec engineers GitLab Security Scan Dashboard The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. By increasing visibility into the vulnerability status of their network, security teams. Security Scan Dashboard.
From www.trendmicro.com
Snyk Opensource Security Partners with Trend Micro Security Scan Dashboard Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Tenable recommends configuring several data sources to optimize the data you see in. Browse and download dashboard templates for. Learn how to use. Security Scan Dashboard.
From www.qualys.com
Qualys Application Scanning Qualys Security Scan Dashboard Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Dashboards display vulnerability, event, and other scan data. Browse and download dashboard templates for. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. By increasing visibility into the vulnerability status of their network, security teams can. Learn. Security Scan Dashboard.
From www.pcworld.idg.com.au
Bitdefender Total Security (2021) review An already capable suite gets Security Scan Dashboard Learn the top 10 cybersecurity dashboard metrics that every cio needs to know to monitor their organization's security posture and risk. Browse and download dashboard templates for. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Dashboards display vulnerability, event, and other scan data. Learn how to use nessus scanners to audit your. Security Scan Dashboard.
From www.wiz.io
Wiz Product Security Scan Dashboard This article covers the basics of vulnerability scanning, the six step process, the types of. By increasing visibility into the vulnerability status of their network, security teams can. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. Learn what vulnerability scanning is, how it works, why it's important, and what tools to use. Learn the top 10 cybersecurity. Security Scan Dashboard.
From www.acunetix.com
Online Vulnerability Scanner Security Scan Dashboard Dashboards display vulnerability, event, and other scan data. The vulnerability trend dashboard monitors detected vulnerabilities on an organization’s network. This article covers the basics of vulnerability scanning, the six step process, the types of. Learn how to use nessus scanners to audit your network for security vulnerabilities and get a summary of scan activities and attributes. Learn what vulnerability scanning. Security Scan Dashboard.