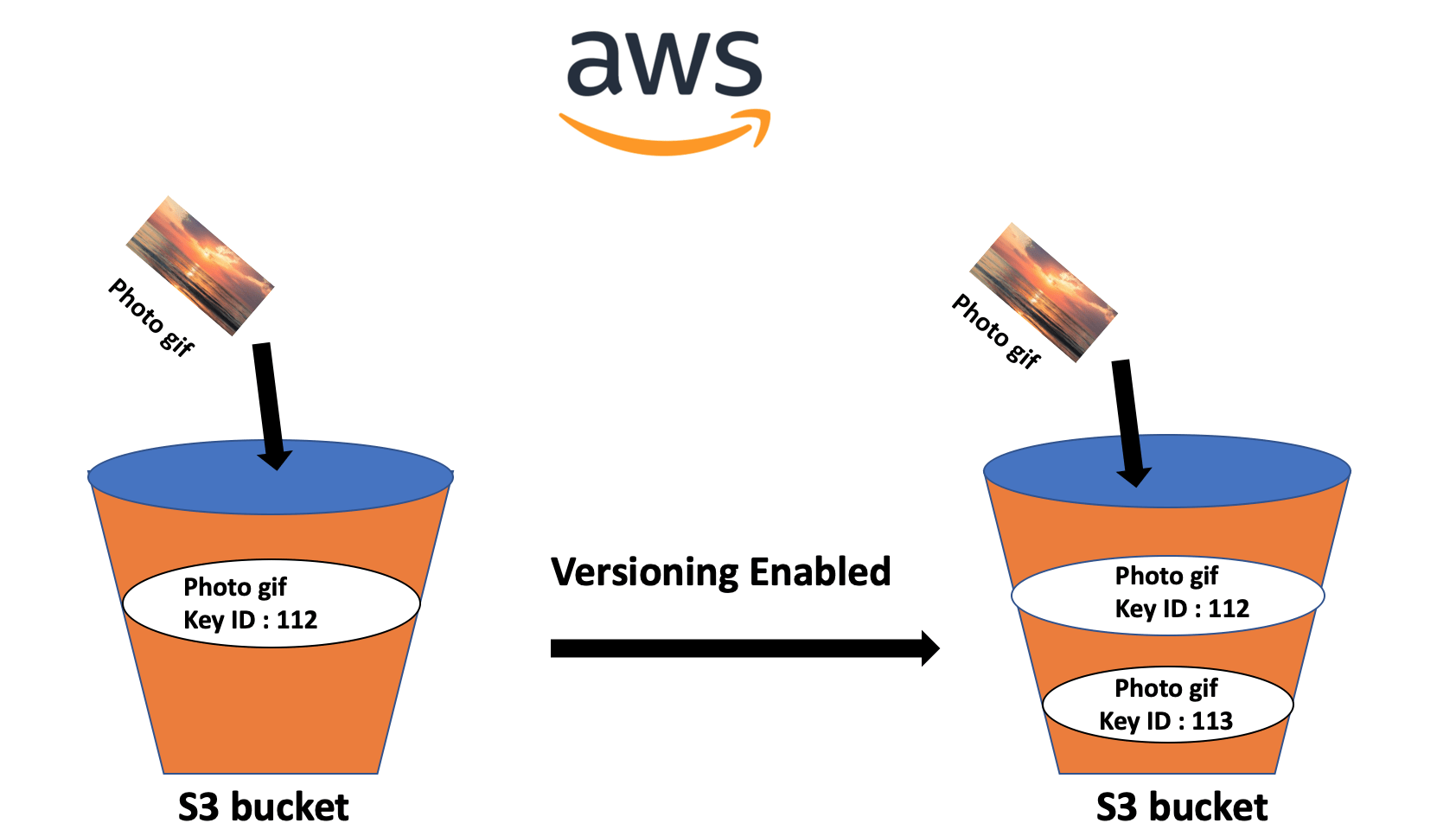
Amazon S3 Bucket Enumeration . Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Misconfigurations in these buckets can.
from buddymantra.com
In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. Misconfigurations in these buckets can. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket.
Amazon S3 Bucket Everything You Need to Know About Cloud Storage
Amazon S3 Bucket Enumeration Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. Misconfigurations in these buckets can. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. However, misconfigured s3 buckets can be a gateway to sensitive data exposure.
From buddymantra.com
Amazon S3 Bucket Everything You Need to Know About Cloud Storage Amazon S3 Bucket Enumeration However, misconfigured s3 buckets can be a gateway to sensitive data exposure. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. Misconfigurations in these buckets can. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. S3 buckets, a popular storage solution provided by. Amazon S3 Bucket Enumeration.
From hacklido.com
AWS S3 Bucket's & Object's Enumeration using Lambda HACKLIDO Amazon S3 Bucket Enumeration This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Misconfigurations in these buckets can. In this guide, we. Amazon S3 Bucket Enumeration.
From www.youtube.com
How to create S3 bucket in AWS AWS Tutorial For Beginners AWS S3 Amazon S3 Bucket Enumeration Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket.. Amazon S3 Bucket Enumeration.
From aws.amazon.com
How to use AWS DataSync to migrate data between Amazon S3 buckets AWS Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Misconfigurations in these buckets can. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets,. Amazon S3 Bucket Enumeration.
From k21academy.com
Amazon S3 Bucket Overview & Steps to Create Cloud Training Program Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Misconfigurations in these buckets can. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. However, misconfigured s3. Amazon S3 Bucket Enumeration.
From kodyaz.com
S3 Browser Tool for Accessing and Managing Amazon S3 Buckets Amazon S3 Bucket Enumeration This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. Misconfigurations in these buckets can. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Navigating the complexities of. Amazon S3 Bucket Enumeration.
From docs.aws.amazon.com
Naming S3 buckets in your data layers AWS Prescriptive Guidance Amazon S3 Bucket Enumeration Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. Implement activity monitoring. Amazon S3 Bucket Enumeration.
From pronteff.com
How does Angular configuration for Amazon S3 buckets works? Amazon S3 Bucket Enumeration Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and.. Amazon S3 Bucket Enumeration.
From www.vrogue.co
Aws S3 Bucket A Complete Guide To Create And Access D vrogue.co Amazon S3 Bucket Enumeration Misconfigurations in these buckets can. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and. Amazon S3 Bucket Enumeration.
From kinsta.com
How To Set Up an Amazon S3 Bucket for External Backups Amazon S3 Bucket Enumeration Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Misconfigurations in these buckets can. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying. Amazon S3 Bucket Enumeration.
From docs.aws.amazon.com
Step 1 Create an Amazon S3 Bucket AWS Quick Start Guide Back Up Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Misconfigurations in these buckets can. This report provides. Amazon S3 Bucket Enumeration.
From www.learnwebtech.in
how to setup amazon s3 bucket in drupal 9 Amazon S3 Bucket Amazon S3 Bucket Enumeration S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Misconfigurations in these buckets can. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Navigating the complexities. Amazon S3 Bucket Enumeration.
From www.geeksforgeeks.org
Amazon S3 Creating a S3 Bucket Amazon S3 Bucket Enumeration However, misconfigured s3 buckets can be a gateway to sensitive data exposure. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. Navigating the complexities of aws s3 enumeration is crucial for. Amazon S3 Bucket Enumeration.
From cuno.io
How to Mount an Amazon S3 Bucket as a Local Drive using cunoFS cunoFS Amazon S3 Bucket Enumeration Misconfigurations in these buckets can. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common. Amazon S3 Bucket Enumeration.
From trailhead.salesforce.com
Understanding Amazon S3 Features & Usage Salesforce Trailhead Amazon S3 Bucket Enumeration This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration. Amazon S3 Bucket Enumeration.
From aws.amazon.com
Store and Retrieve a File with Amazon S3 Amazon S3 Bucket Enumeration Misconfigurations in these buckets can. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. S3 buckets, a popular. Amazon S3 Bucket Enumeration.
From www.seagate.com
How Amazon S3 Buckets Work Seagate US Amazon S3 Bucket Enumeration This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Misconfigurations in these buckets can. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. S3 buckets, a popular storage solution provided by amazon. Amazon S3 Bucket Enumeration.
From www.nakivo.com
Amazon S3 Bucket Encryption Overview & Setup Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Misconfigurations in these buckets can. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. However, misconfigured s3 buckets can be. Amazon S3 Bucket Enumeration.
From buddymantra.com
Amazon S3 Bucket Everything You Need to Know About Cloud Storage Amazon S3 Bucket Enumeration S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets. Amazon S3 Bucket Enumeration.
From thamizhiniyancs.gitbook.io
S3 Bucket Enumeration Resources Amazon S3 Bucket Enumeration This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Misconfigurations in these buckets can. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets,. Amazon S3 Bucket Enumeration.
From kratikal.com
AMAZON AWS S3 BUCKET A QUICK OVERVIEW Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying. Amazon S3 Bucket Enumeration.
From codeonedigest.wordpress.com
Amazon S3 Bucket Feature Tutorial Part2 Explained S3 Bucket Features Amazon S3 Bucket Enumeration This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Misconfigurations in these buckets can. S3 buckets, a popular. Amazon S3 Bucket Enumeration.
From www.vrogue.co
How To Create An S3 Bucket On Aws Complete Guide vrogue.co Amazon S3 Bucket Enumeration Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Misconfigurations in these buckets can. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. In this guide, we. Amazon S3 Bucket Enumeration.
From community.spiceworks.com
How to Back up an Amazon S3 Bucket. Complete stepbystep tutorial with Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Implement activity monitoring in your amazon s3 to detect. Amazon S3 Bucket Enumeration.
From www.youtube.com
Slurp Amazon AWS S3 Bucket Enumeration [Cloud Security] YouTube Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon. Amazon S3 Bucket Enumeration.
From aws.amazon.com
Synchronizing Amazon S3 Buckets Using AWS Step Functions AWS Compute Blog Amazon S3 Bucket Enumeration Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. In this guide, we will delve into advanced methods. Amazon S3 Bucket Enumeration.
From ninotronix.com
A Comprehensive Guide to Amazon S3 Buckets Features, Benefits, and Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Navigating the complexities of aws s3 enumeration is crucial. Amazon S3 Bucket Enumeration.
From hevodata.com
Working with Amazon S3 Keys 3 Critical Aspects Learn Hevo Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. However,. Amazon S3 Bucket Enumeration.
From awstrainingwithjagan.com
What is S3 bucket in AWS Amazon S3 Bucket Enumeration Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. However,. Amazon S3 Bucket Enumeration.
From k21academy.com
Amazon S3 Bucket AWS S3 Storage Classes S3 Types Amazon S3 Bucket Enumeration Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters. Amazon S3 Bucket Enumeration.
From aws.amazon.com
Find out the size of your Amazon S3 buckets AWS Storage Blog Amazon S3 Bucket Enumeration Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. Misconfigurations in these buckets can. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets,. Amazon S3 Bucket Enumeration.
From medium.com
How to Secure Your Amazon S3 Bucket with Encryption and Public Amazon S3 Bucket Enumeration In this guide, we will delve into advanced methods for s3 bucket reconnaissance —. Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. This report provides a comprehensive exploration of s3 bucket enumeration, a. Amazon S3 Bucket Enumeration.
From www.devstringx.com
Amazon S3 Bucket Features, Storage Classes, Practices, Use Cases DS Amazon S3 Bucket Enumeration Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and.. Amazon S3 Bucket Enumeration.
From medium.com
Misconfigured AWS S3 Bucket Enumeration by KANDULA.VENKATA NARENDRA Amazon S3 Bucket Enumeration Navigating the complexities of aws s3 enumeration is crucial for identifying and securing misconfigured s3 buckets, which are potential gateways to. Implement activity monitoring in your amazon s3 to detect unauthorized access attempts or bucket. However, misconfigured s3 buckets can be a gateway to sensitive data exposure. Misconfigurations in these buckets can. This report provides a comprehensive exploration of s3. Amazon S3 Bucket Enumeration.
From www.geeksforgeeks.org
Amazon S3 Creating a S3 Bucket Amazon S3 Bucket Enumeration S3 buckets, a popular storage solution provided by amazon web services (aws), have become a common target for bug bounty hunters and penetration testers. This report provides a comprehensive exploration of s3 bucket enumeration, a critical aspect of cloud security research focused on identifying vulnerable amazon s3 buckets and. Misconfigurations in these buckets can. Navigating the complexities of aws s3. Amazon S3 Bucket Enumeration.