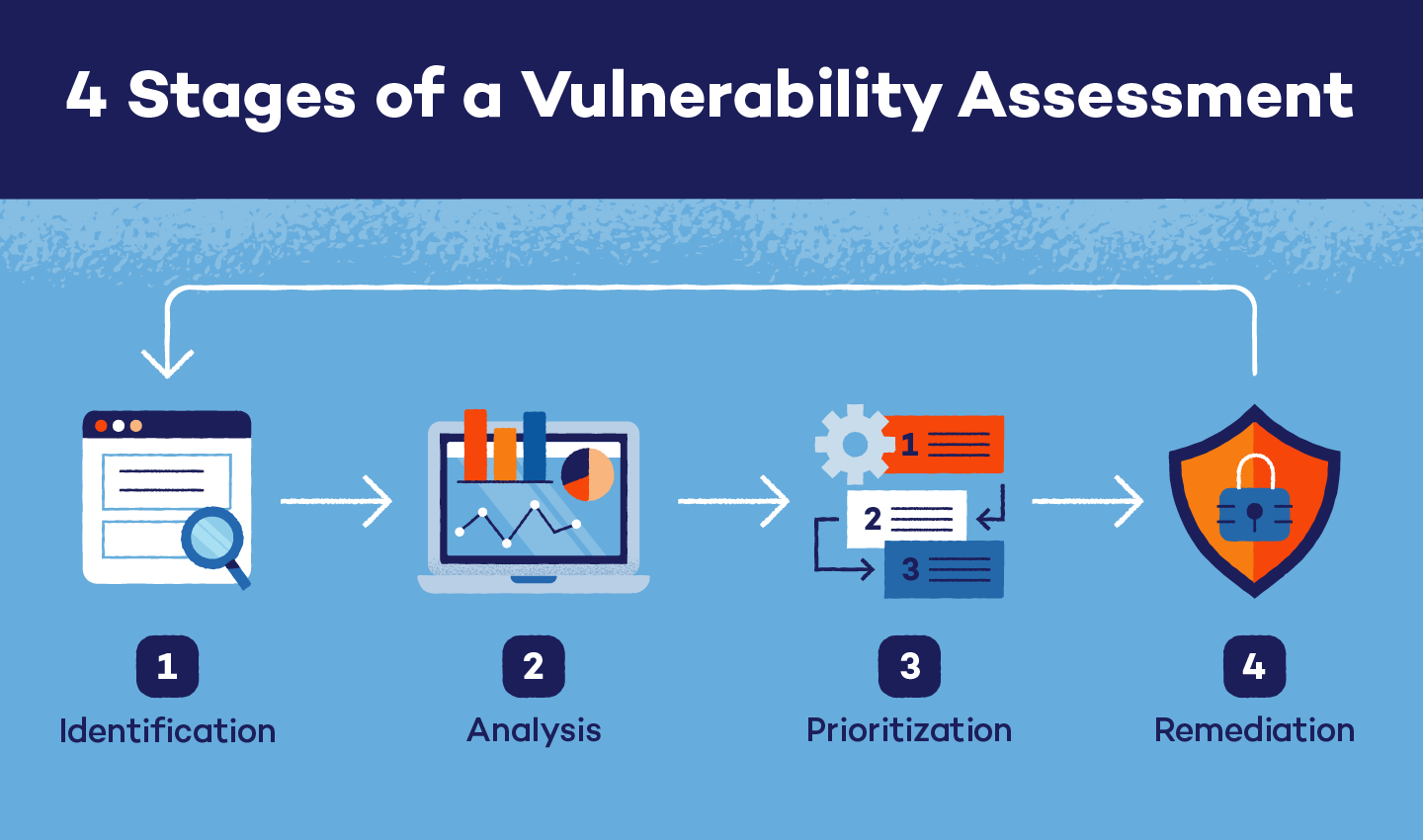
Goals Of Vulnerability Management . Determine scope of the program. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Create and refine policy and slas. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance.
from www.pandasecurity.com
Create and refine policy and slas. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. Determine scope of the program. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:.
What is a Vulnerability Assessment? Panda Security
Goals Of Vulnerability Management the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. Determine scope of the program. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Create and refine policy and slas. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more.
From wentzwu.com
Vulnerability Management by Wentz Wu, ISSAP, ISSEP, ISSMP CISSP, CCSP Goals Of Vulnerability Management vulnerability management is the process of continuously identifying, categorizing, and remediating technology. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. the objective of this document is to bridge. Goals Of Vulnerability Management.
From hyperproof.io
The Ultimate Guide to Vulnerability Management Hyperproof Goals Of Vulnerability Management the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. vulnerability management. Goals Of Vulnerability Management.
From www.manageengine.com
Vulnerability Assessment Process How to conduct a Vulnerability Goals Of Vulnerability Management the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. Determine scope of the program. the objective of this document is to bridge the gaps in information security by breaking down complex problems. Goals Of Vulnerability Management.
From www.researchgate.net
3 The MOVE Generic Framework used for vulnerability assessment Goals Of Vulnerability Management Create and refine policy and slas. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Determine scope of the program. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting. Goals Of Vulnerability Management.
From www.spiceworks.com
What Is Vulnerability Management? Definition, Lifecycle, Policy, and Goals Of Vulnerability Management Determine scope of the program. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. Create and refine policy and slas. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. vulnerability management is the process of continuously identifying, categorizing,. Goals Of Vulnerability Management.
From www.securityscientist.net
The 6 Steps in the Software Vulnerability Management Lifecycle Goals Of Vulnerability Management without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. Determine scope of the program. the objective of this document is to bridge the gaps in information security by breaking down. Goals Of Vulnerability Management.
From www.researchgate.net
Vulnerability framework (based on (Carley et al., 2018)) Download Goals Of Vulnerability Management the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. Create and refine. Goals Of Vulnerability Management.
From www.pandasecurity.com
What is a Vulnerability Assessment? Panda Security Goals Of Vulnerability Management the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Determine scope of the program. the objective of this document is to bridge the gaps in information security by breaking down. Goals Of Vulnerability Management.
From www.getastra.com
What is Vulnerability Management? Astra Security Blog Goals Of Vulnerability Management vulnerability management is the process of continuously identifying, categorizing, and remediating technology. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Determine scope of the program. Create and refine policy and slas. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating. Goals Of Vulnerability Management.
From zsecurity.org
Creating a Vulnerability Management Strategy zSecurity Goals Of Vulnerability Management Create and refine policy and slas. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. the goal of vulnerability management is to reduce the organization's overall risk. Goals Of Vulnerability Management.
From informer.io
Vulnerability Management Lifecycle A Guide For 2024 — Informer Goals Of Vulnerability Management the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. Create and refine policy and slas. Determine scope of. Goals Of Vulnerability Management.
From securityboulevard.com
8 Tips to Master Your Vulnerability Management Program Security Boulevard Goals Of Vulnerability Management the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. Determine scope of the program. without further delay, here are. Goals Of Vulnerability Management.
From purplesec.us
How To Build An Effective Vulnerability Management Program Goals Of Vulnerability Management the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. Create and refine policy and slas. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. Determine scope. Goals Of Vulnerability Management.
From socradar.io
Vulnerability Management Best Practices SOCRadar® Cyber Intelligence Inc. Goals Of Vulnerability Management Determine scope of the program. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. Create and refine policy and slas. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. the objective of this document is to bridge the gaps in information. Goals Of Vulnerability Management.
From www.enmaruindonesia.com
What Are The Benefits Of Using Vulnerability Management Software Goals Of Vulnerability Management the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. Create and refine policy and slas. without. Goals Of Vulnerability Management.
From blog.invgate.com
Vulnerability Management Processes and tools Goals Of Vulnerability Management the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Determine scope of the program. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. the goal of. Goals Of Vulnerability Management.
From www.youtube.com
Vulnerability Management 101 Best Practices for Success Goals Of Vulnerability Management Determine scope of the program. Create and refine policy and slas. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. vulnerability management is the process of continuously identifying, categorizing, and. Goals Of Vulnerability Management.
From toolkit.climate.gov
Vulnerability Assessment and Adaptation Framework U.S. Climate Goals Of Vulnerability Management Determine scope of the program. Create and refine policy and slas. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating. Goals Of Vulnerability Management.
From www.balbix.com
Vulnerability Management Program How to Built It? Balbix Goals Of Vulnerability Management the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. Create and refine policy and slas. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. the objective of this document is to bridge the gaps in information security by breaking down complex. Goals Of Vulnerability Management.
From www.manageengine.com
Vulnerability Assessment Tools & Checklists ManageEngine Goals Of Vulnerability Management without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. the goal of vulnerability management is to reduce. Goals Of Vulnerability Management.
From blog.teamascend.com
The Five Stages of Vulnerability Management Goals Of Vulnerability Management vulnerability management is the process of continuously identifying, categorizing, and remediating technology. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Create and refine policy and slas. Determine scope of the program. without further delay, here are the top four desired outcomes from security professionals in. Goals Of Vulnerability Management.
From academy.rapid7.com
Vulnerability Management Lifecycle Goals Of Vulnerability Management Create and refine policy and slas. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. without. Goals Of Vulnerability Management.
From www.youtube.com
Vulnerability Management What is Vulnerability Management? YouTube Goals Of Vulnerability Management the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. without further. Goals Of Vulnerability Management.
From brightsec.com
Vulnerability Management Lifecycle, Tools, and Best Practices Goals Of Vulnerability Management the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. . Goals Of Vulnerability Management.
From blueteamresources.in
Vulnerability Management Lifecycle Blue Team Resources Goals Of Vulnerability Management the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Determine scope of the program. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. . Goals Of Vulnerability Management.
From cyver.io
Bringing Pentests into Vulnerability Management Cyver Goals Of Vulnerability Management Determine scope of the program. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. the objective of. Goals Of Vulnerability Management.
From www.entrepreneurbusinessblog.com
An effective vulnerability management lifecycle Entrepreneur Business Goals Of Vulnerability Management without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. Determine scope of the program. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Create. Goals Of Vulnerability Management.
From threatpost.com
Vulnerabilities are Beyond What You Think Threatpost Goals Of Vulnerability Management Create and refine policy and slas. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. the. Goals Of Vulnerability Management.
From www.sofsol.co.nz
Vulnerability Manager Why vulnerability management is important Goals Of Vulnerability Management Determine scope of the program. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. Create and refine policy and slas. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. the goal of vulnerability management is to. Goals Of Vulnerability Management.
From securityboulevard.com
Building a Vulnerability Management Program Key Components and Tips to Goals Of Vulnerability Management the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. Create and refine policy and slas. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Determine scope of. Goals Of Vulnerability Management.
From www.crowdstrike.com
The Vulnerability Management Lifecycle (5 Steps) CrowdStrike Goals Of Vulnerability Management vulnerability management is the process of continuously identifying, categorizing, and remediating technology. Determine scope of the program. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Create and refine policy and slas. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating. Goals Of Vulnerability Management.
From securityboulevard.com
Vulnerability Management Lifecycle 5 Steps and Best Practices Goals Of Vulnerability Management the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Determine scope of the program. the objective of this document is to bridge the gaps in information security by breaking down. Goals Of Vulnerability Management.
From www.recordedfuture.com
Reduce Risk in Vulnerability Management With the Intelligence Goals Goals Of Vulnerability Management vulnerability management is the process of continuously identifying, categorizing, and remediating technology. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. without further delay, here are the top four desired outcomes. Goals Of Vulnerability Management.
From www.secpod.com
Vulnerability Management Process It's More Than Just Detecting Goals Of Vulnerability Management the objective of this document is to bridge the gaps in information security by breaking down complex problems into more. the goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many. vulnerability management is the process of continuously identifying, categorizing, and remediating technology. the goals of vulnerability management include reducing. Goals Of Vulnerability Management.
From www.crowdstrike.com
What is Vulnerability Management? CrowdStrike Goals Of Vulnerability Management without further delay, here are the top four desired outcomes from security professionals in the vulnerability risk management space:. Create and refine policy and slas. the goals of vulnerability management include reducing attack surfaces, improving an organization's security posture, meeting regulatory compliance. the objective of this document is to bridge the gaps in information security by breaking. Goals Of Vulnerability Management.