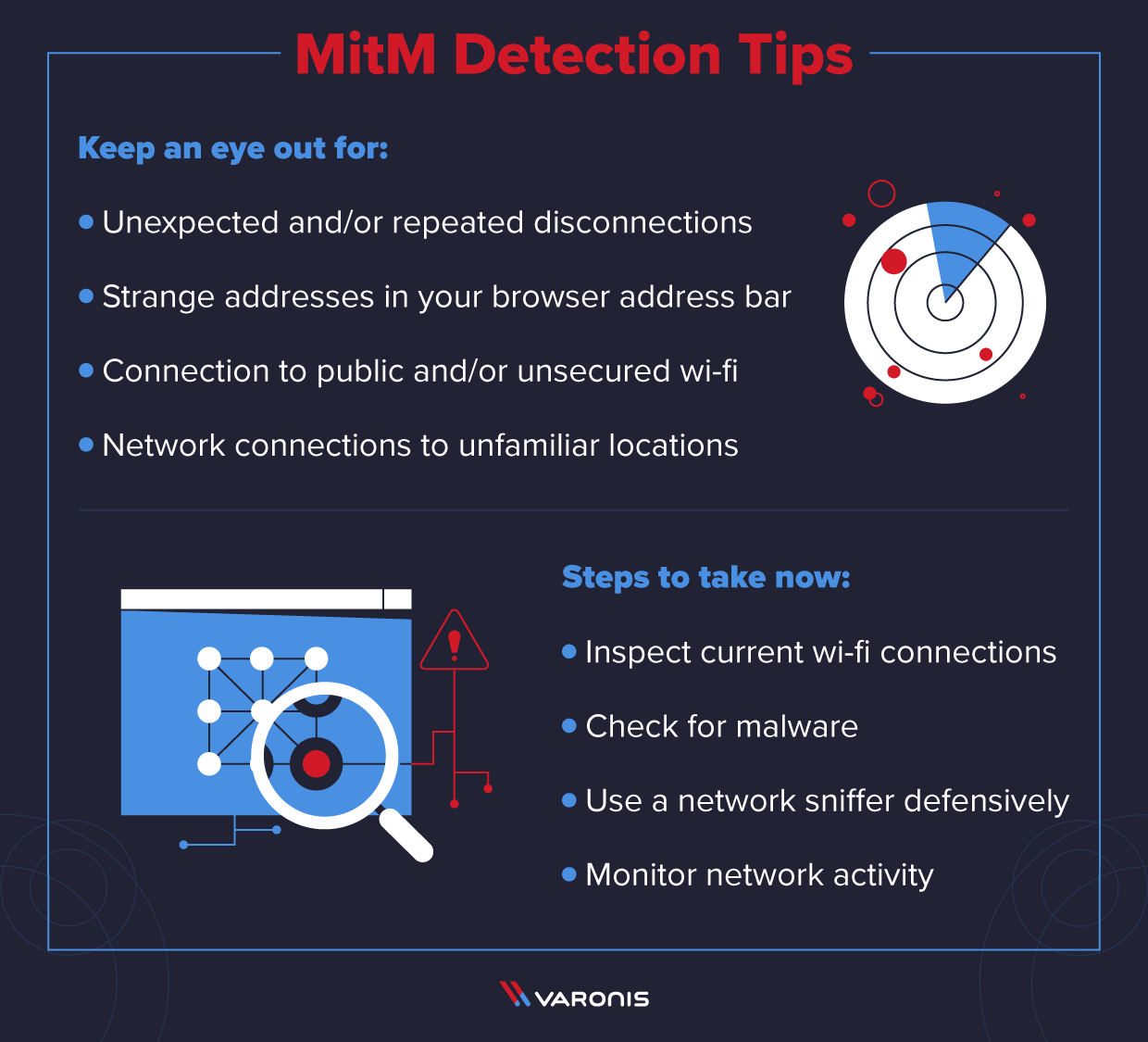
How To Prevent Mitm Attacks . What are the various techniques, types of attacks, and how to prevent and protect against them?. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Here are the signs to detect a mitm attack. Back in the early days of. Discover how does a mitm attack works and how to protect endpoints. How to prevent a mitm attack in 9 easy steps. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack.
from www.varonis.com
Back in the early days of. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. How to prevent a mitm attack in 9 easy steps. Discover how does a mitm attack works and how to protect endpoints. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Here are the signs to detect a mitm attack. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. What are the various techniques, types of attacks, and how to prevent and protect against them?.
What is a ManintheMiddle Attack Detection and Prevention Tips
How To Prevent Mitm Attacks Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Back in the early days of. Discover how does a mitm attack works and how to protect endpoints. How to prevent a mitm attack in 9 easy steps. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. What are the various techniques, types of attacks, and how to prevent and protect against them?. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Here are the signs to detect a mitm attack.
From www.appdome.com
DevSec Blog How to Prevent Mobile MiTM Attacks How To Prevent Mitm Attacks Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Discover how does a mitm attack works and how to protect endpoints. Here are the signs to detect a mitm attack. How to prevent a mitm attack in 9 easy steps. An automated certificate management system is perhaps one of the best ways to. How To Prevent Mitm Attacks.
From ccoe.dsci.in
What is Man in the Middle (MitM) Attacks? Types and How to Prevent Them How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Back in the early days of. Here are the signs to detect a mitm attack. What are the various techniques, types of attacks, and how to prevent and protect against them?. How to prevent a mitm attack in 9 easy steps.. How To Prevent Mitm Attacks.
From nestify.io
ManintheMiddle MITM Attacks 10 Ways to Prevent Them How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. What are the various techniques, types of attacks, and how to prevent and protect against them?. Discover how does a mitm attack works and how to protect endpoints. Back in the early days of. An automated certificate management system is perhaps. How To Prevent Mitm Attacks.
From www.patterndrive.com
Prevent ManintheMiddle Attack With These Tips Pattern Drive How To Prevent Mitm Attacks Discover how does a mitm attack works and how to protect endpoints. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Here are the signs to detect a mitm attack. What are the various techniques, types of attacks, and how to prevent and protect against them?. Below, 19 members of. How To Prevent Mitm Attacks.
From www.upguard.com
What Is a ManintheMiddle Attack? Prevention Tips and Guide UpGuard How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Discover how does a mitm attack works and how to protect endpoints. Back in the early days of. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Below, 19 members of forbes technology. How To Prevent Mitm Attacks.
From www.invicti.com
Avoiding maninthemiddle (MITM) attacks Invicti How To Prevent Mitm Attacks Back in the early days of. What are the various techniques, types of attacks, and how to prevent and protect against them?. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Discover how does a mitm attack works and how to protect endpoints. Below, 19 members of forbes technology council share expert. How To Prevent Mitm Attacks.
From www.fraud.com
ManintheMiddle Attacks Strategies for Prevention How To Prevent Mitm Attacks Back in the early days of. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. What are the various techniques, types of attacks, and how to prevent and protect against them?. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Here are. How To Prevent Mitm Attacks.
From www.ionos.co.uk
Maninthemiddle attack (MITM) Techniques & Prevention IONOS UK How To Prevent Mitm Attacks Discover how does a mitm attack works and how to protect endpoints. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Back in the early days of. How to prevent a mitm attack. How To Prevent Mitm Attacks.
From impanix.com
ManintheMiddle Attack (MITM) How To Detect and Prevent? How To Prevent Mitm Attacks Back in the early days of. Discover how does a mitm attack works and how to protect endpoints. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Here are the signs to detect a mitm attack. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack.. How To Prevent Mitm Attacks.
From www.appsecmonkey.com
MITM (ManInTheMiddle) Attacks and Prevention AppSec Monkey How To Prevent Mitm Attacks An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Discover how does a mitm attack works and how to protect endpoints. Back in the early days of. How to prevent a mitm attack in 9 easy steps. What are the various techniques, types of attacks, and how to prevent and protect against. How To Prevent Mitm Attacks.
From heimdalsecurity.com
ManintheMiddle Attack Definition, Examples, Prevention How To Prevent Mitm Attacks Discover how does a mitm attack works and how to protect endpoints. How to prevent a mitm attack in 9 easy steps. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Back in the. How To Prevent Mitm Attacks.
From www.logsign.com
10 Steps to Prevent Man in the Middle Attacks Logsign How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Back in the early days of. Here are the signs to detect a mitm attack. How to prevent a mitm attack in 9 easy steps. An automated certificate management system is perhaps one of the best ways to prevent an mitm. How To Prevent Mitm Attacks.
From www.internetsecurity.tips
What is a Maninthe Middle Attack? How Can We Stay Protected? How To Prevent Mitm Attacks Discover how does a mitm attack works and how to protect endpoints. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Here are the signs to detect a mitm attack. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. A certificate management system monitors and. How To Prevent Mitm Attacks.
From www.efani.com
MITM Attacks Types, Signs & Symptoms, and Protection Methods How To Prevent Mitm Attacks Here are the signs to detect a mitm attack. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. What are the various techniques, types of attacks, and how to prevent and protect against them?. A certificate. How To Prevent Mitm Attacks.
From www.geeksforgeeks.org
How to Prevent Man In the Middle Attack? How To Prevent Mitm Attacks Discover how does a mitm attack works and how to protect endpoints. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Back in the early days of. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. A certificate management system monitors and maintains the lifecycle. How To Prevent Mitm Attacks.
From approov.io
How Certificate Pinning Prevents Mobile ManintheMiddle (MitM) Attacks How To Prevent Mitm Attacks Back in the early days of. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Here are the signs to detect a mitm attack. Discover how does a mitm attack works and how to protect endpoints. What are the various techniques, types of attacks, and how to prevent and protect against them?. A. How To Prevent Mitm Attacks.
From www.youtube.com
Maninthemiddle attack EXPLAINED HOW can you to prevent MITM attack How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Discover how does a mitm attack works and how to protect endpoints. How to prevent a mitm attack in 9 easy steps. Here are the signs to detect a mitm attack. Below, 19 members of forbes technology council share expert strategies. How To Prevent Mitm Attacks.
From www.haltdos.com
What is a MITM Attack and How to prevent it? Haltdos How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Back in the early days of. Discover how does a mitm attack works and how to protect endpoints. How to prevent a mitm attack in 9 easy steps. Below, 19 members of forbes technology council share expert strategies organizations should review. How To Prevent Mitm Attacks.
From www.techsagar.com
Tips to Prevent a Man In The Middle Attack TechSagar How To Prevent Mitm Attacks Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Discover how does a mitm attack works and how to protect endpoints. Here are the signs to detect a mitm attack. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. How to prevent a. How To Prevent Mitm Attacks.
From clario.co
What is a ManintheMiddle Attack? Tips for Preventing MITM Attacks How To Prevent Mitm Attacks Back in the early days of. Discover how does a mitm attack works and how to protect endpoints. What are the various techniques, types of attacks, and how to prevent and protect against them?. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. How to prevent a mitm attack in. How To Prevent Mitm Attacks.
From blog.hypr.com
How to Prevent ManintheMiddle Attacks HYPR How To Prevent Mitm Attacks What are the various techniques, types of attacks, and how to prevent and protect against them?. Here are the signs to detect a mitm attack. Discover how does a mitm attack works and how to protect endpoints. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. A certificate management system monitors and maintains. How To Prevent Mitm Attacks.
From www.firstpoint-mg.com
How to Prevent Man in the Middle Attacks [with Examples] FirstPoint How To Prevent Mitm Attacks An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Back in the early days of. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. What are the various techniques, types of attacks, and how to prevent and protect against them?. Discover how does a mitm. How To Prevent Mitm Attacks.
From www.razorman.net
Ataque Man in the Middle qué es, cómo funciona y cómo protegerse How To Prevent Mitm Attacks What are the various techniques, types of attacks, and how to prevent and protect against them?. Here are the signs to detect a mitm attack. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Discover how does a mitm attack works and how to protect endpoints. Below, 19 members of. How To Prevent Mitm Attacks.
From geekflare.com
What are ManintheMiddle attacks and How to Prevent them? Geekflare How To Prevent Mitm Attacks Discover how does a mitm attack works and how to protect endpoints. Here are the signs to detect a mitm attack. How to prevent a mitm attack in 9 easy steps. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Below, 19 members of forbes technology council share expert strategies. How To Prevent Mitm Attacks.
From laptrinhx.com
What is a Man in the Middle (MitM) Attack? (And How to Prevent Them How To Prevent Mitm Attacks How to prevent a mitm attack in 9 easy steps. What are the various techniques, types of attacks, and how to prevent and protect against them?. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Here. How To Prevent Mitm Attacks.
From securenetworksitc.com
Man In The Middle Attack and Proven Ways to Prevent It Secure How To Prevent Mitm Attacks An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Here are the signs to detect a mitm attack. Back in the early days of. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Discover how does a mitm attack works and how to protect endpoints.. How To Prevent Mitm Attacks.
From www.programmingcube.com
How to Prevent Man in the Middle Attack Programming Cube How To Prevent Mitm Attacks Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. What are the various techniques, types of attacks, and how to prevent and protect against them?. How to prevent a mitm attack in 9 easy steps. Back in the early days of. An automated certificate management system is perhaps one of the best ways. How To Prevent Mitm Attacks.
From data-flair.training
MITM (Man in the Middle) Attack Types and Prevention DataFlair How To Prevent Mitm Attacks Back in the early days of. Discover how does a mitm attack works and how to protect endpoints. Here are the signs to detect a mitm attack. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates). How To Prevent Mitm Attacks.
From www.pandasecurity.com
¿Qué es un ataque ManintheMiddle (MITM)? Definición y prevención How To Prevent Mitm Attacks Discover how does a mitm attack works and how to protect endpoints. Back in the early days of. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Here are the signs to detect a mitm attack.. How To Prevent Mitm Attacks.
From locker.io
A Guide On Defending Against ManintheMiddle Attacks How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Here are the signs to detect a mitm attack. Back in the early days of. What are the various techniques, types of attacks, and how to prevent and protect against them?. Discover how does a mitm attack works and how to. How To Prevent Mitm Attacks.
From www.varonis.com
What is a ManintheMiddle Attack Detection and Prevention Tips How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. An automated certificate management system is perhaps one of the best ways to prevent an mitm attack. Back in the early days of. Here are the signs to detect a mitm attack. How to prevent a mitm attack in 9 easy. How To Prevent Mitm Attacks.
From www.varonis.com
What is a ManintheMiddle Attack Detection and Prevention Tips How To Prevent Mitm Attacks Discover how does a mitm attack works and how to protect endpoints. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. An automated certificate management system is perhaps one of the best ways to. How To Prevent Mitm Attacks.
From locker.io
A Guide On Defending Against ManintheMiddle Attacks How To Prevent Mitm Attacks A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. How to prevent a mitm attack in 9 easy steps. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Here are the signs to detect a mitm attack. What are the various techniques, types. How To Prevent Mitm Attacks.
From medium.com
What is a MITM Attack and How to prevent it? by Haltdos Medium How To Prevent Mitm Attacks How to prevent a mitm attack in 9 easy steps. Below, 19 members of forbes technology council share expert strategies organizations should review and implement to. Back in the early days of. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Here are the signs to detect a mitm attack.. How To Prevent Mitm Attacks.
From www.artofit.org
Man in the middle mitm attack definition types prevention methods Artofit How To Prevent Mitm Attacks Here are the signs to detect a mitm attack. What are the various techniques, types of attacks, and how to prevent and protect against them?. A certificate management system monitors and maintains the lifecycle of all digital x.509 certificates (ssl certificates) within the system. Discover how does a mitm attack works and how to protect endpoints. How to prevent a. How To Prevent Mitm Attacks.