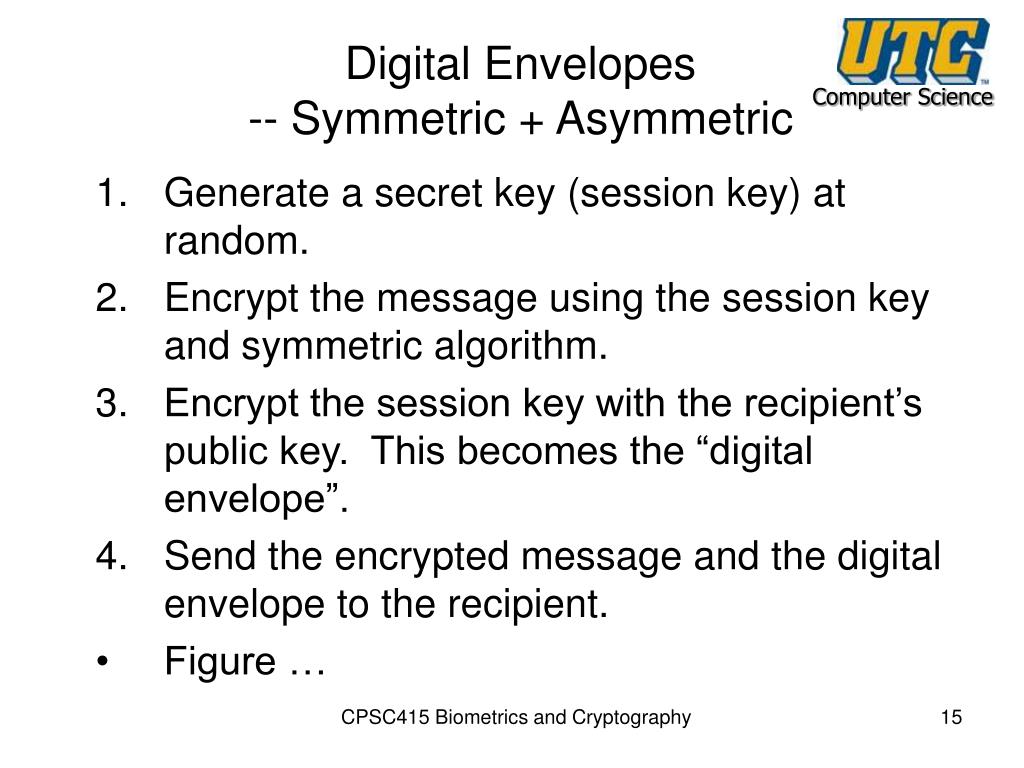
Envelope Key Encryption . Typically, one key is derived from a longer. Envelope encryption is a technique that uses two layers of encryption. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. One strategy is to encrypt. One layer secures the data through a blend of asymmetric and symmetric encryption. Envelope encryption uses two or more cryptographic keys to secure a message. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. When you encrypt your data, your data is protected, but you have to protect your encryption key.
from www.slideserve.com
Typically, one key is derived from a longer. One strategy is to encrypt. When you encrypt your data, your data is protected, but you have to protect your encryption key. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. One layer secures the data through a blend of asymmetric and symmetric encryption. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. Envelope encryption is a technique that uses two layers of encryption. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption uses two or more cryptographic keys to secure a message.
PPT Introduction to Public Key Cryptography PowerPoint Presentation
Envelope Key Encryption Envelope encryption uses two or more cryptographic keys to secure a message. One layer secures the data through a blend of asymmetric and symmetric encryption. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. When you encrypt your data, your data is protected, but you have to protect your encryption key. Envelope encryption uses two or more cryptographic keys to secure a message. Typically, one key is derived from a longer. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. Envelope encryption is a technique that uses two layers of encryption. One strategy is to encrypt.
From medium.com
Envelope Encryption (From Cloud to the Ground) App Security Vault by Envelope Key Encryption Envelope encryption uses two or more cryptographic keys to secure a message. One strategy is to encrypt. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key. Envelope Key Encryption.
From asecuritysite.com
AWS Public Key Encryption Envelope Key Encryption One layer secures the data through a blend of asymmetric and symmetric encryption. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Envelope encryption is a technique that uses two layers of encryption. Typically, one key is derived from a longer. Envelope encryption is the method of. Envelope Key Encryption.
From matthewcaseres.gitbook.io
Introduction to Cryptography OMSCS Notes Envelope Key Encryption When you encrypt your data, your data is protected, but you have to protect your encryption key. One layer secures the data through a blend of asymmetric and symmetric encryption. Envelope encryption uses two or more cryptographic keys to secure a message. One strategy is to encrypt. An example of multiple layer of keys is envelope encryption, which is the. Envelope Key Encryption.
From asecuritysite.com
AWS Envelope Encryption Envelope Key Encryption Envelope encryption uses two or more cryptographic keys to secure a message. One layer secures the data through a blend of asymmetric and symmetric encryption. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. Kubernetes offers envelope encryption of secrets with a kms provider,. Envelope Key Encryption.
From ironcorelabs.com
Envelope Encryption IronCore Labs Envelope Key Encryption Typically, one key is derived from a longer. One strategy is to encrypt. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. When you encrypt your data, your data is protected, but you have to protect your encryption key. An example of multiple layer of keys is envelope encryption, which is. Envelope Key Encryption.
From ironcorelabs.com
Envelope Encryption IronCore Labs Envelope Key Encryption Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with. Envelope Key Encryption.
From www.freecodecamp.org
How to Manage Encryption at Scale with Envelope Encryption & Key Envelope Key Encryption Envelope encryption uses two or more cryptographic keys to secure a message. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. When you encrypt your data, your data is protected, but you have to protect your encryption key. One layer secures the data through a blend of. Envelope Key Encryption.
From www.youtube.com
AWS KMS Key Management Service Customer Master Key, Data Key Envelope Key Encryption When you encrypt your data, your data is protected, but you have to protect your encryption key. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized.. Envelope Key Encryption.
From www.slideserve.com
PPT Introduction to Public Key Cryptography PowerPoint Presentation Envelope Key Encryption Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. Envelope encryption uses two or more cryptographic keys to secure a message. Kubernetes. Envelope Key Encryption.
From hackernoon.com
What the Heck Is Envelope Encryption in Cloud Security? HackerNoon Envelope Key Encryption Typically, one key is derived from a longer. Envelope encryption uses two or more cryptographic keys to secure a message. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. One layer secures the data through a blend of asymmetric and symmetric encryption. Kubernetes offers envelope encryption of secrets. Envelope Key Encryption.
From docs.aws.amazon.com
AWS Database Encryption SDK concepts AWS Database Encryption SDK Envelope Key Encryption One strategy is to encrypt. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. One layer secures the data through a blend of asymmetric and symmetric encryption. Envelope encryption is a technique that uses two layers of encryption. An example of multiple layer of keys is envelope encryption, which is the. Envelope Key Encryption.
From dev.to
Enhancing Security through Certificates, Envelope Encryption and Key Envelope Key Encryption When you encrypt your data, your data is protected, but you have to protect your encryption key. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. Envelope encryption is a technique that uses two layers of encryption. Envelope encryption uses two or more cryptographic. Envelope Key Encryption.
From www.youtube.com
DEMO AWS KMS ENVELOPE ENCRYPTION YouTube Envelope Key Encryption Envelope encryption uses two or more cryptographic keys to secure a message. Envelope encryption is a technique that uses two layers of encryption. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. One strategy is to encrypt. Typically, one key is derived from a longer. An example. Envelope Key Encryption.
From transnexus.com
Certificate management for STIR/SHAKEN TransNexus Envelope Key Encryption When you encrypt your data, your data is protected, but you have to protect your encryption key. One layer secures the data through a blend of asymmetric and symmetric encryption. Typically, one key is derived from a longer. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. Envelope encryption uses two. Envelope Key Encryption.
From www.youtube.com
Encrypting Your Encryption Key?? Storing Secrets Securely in AWS Envelope Key Encryption Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. One strategy is to encrypt. Kubernetes offers envelope encryption of secrets with a. Envelope Key Encryption.
From luubinhan.gitbook.io
KMS Terminology Envelope Key Encryption Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. Envelope encryption is a technique that uses two layers of encryption. Envelope encryption uses two or more. Envelope Key Encryption.
From medium.com
KMS and Envelope Encryption Explained by Juan Carlos Garzon Envelope Key Encryption An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption is a technique that uses two layers of encryption. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. When you encrypt your data, your data is protected, but. Envelope Key Encryption.
From ironcorelabs.com
Envelope Encryption IronCore Labs Envelope Key Encryption Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. When you encrypt your data, your data is protected, but you have to protect your encryption key. Typically, one key is derived from a longer. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a. Envelope Key Encryption.
From morioh.com
Envelope Encryption using AWS CLI Envelope Key Encryption An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption uses two or more cryptographic keys to secure a message. One strategy is to encrypt. One layer secures the data through a blend of asymmetric and symmetric encryption. Kubernetes offers envelope encryption of secrets with a kms. Envelope Key Encryption.
From towardsdata.dev
Envelope Encryption Putting Your Encryption Key in an Envelope Is the Envelope Key Encryption When you encrypt your data, your data is protected, but you have to protect your encryption key. Typically, one key is derived from a longer. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Envelope encryption is the method of encrypting data with a data encryption key. Envelope Key Encryption.
From medium.com
KMS and Envelope Encryption Explained by Juan Carlos Garzon Envelope Key Encryption One layer secures the data through a blend of asymmetric and symmetric encryption. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption is a. Envelope Key Encryption.
From www.slideserve.com
PPT Introduction to Public Key Cryptography PowerPoint Presentation Envelope Key Encryption An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption is a technique that uses two layers of encryption. One layer secures the data through a blend of asymmetric and symmetric encryption. One strategy is to encrypt. When you encrypt your data, your data is protected, but. Envelope Key Encryption.
From www.slideserve.com
PPT Basic Cryptography PowerPoint Presentation, free download ID27561 Envelope Key Encryption Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. When you encrypt your data, your data is protected, but you have to protect your encryption key. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a. Envelope Key Encryption.
From www.ibm.com
Bring your own key for serverside encryption at rest Envelope Key Encryption When you encrypt your data, your data is protected, but you have to protect your encryption key. One strategy is to encrypt. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Typically, one key is derived from a longer. An example of multiple layer of keys is. Envelope Key Encryption.
From towardsdata.dev
Envelope Encryption Putting Your Encryption Key in an Envelope Is the Envelope Key Encryption Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. Envelope encryption uses two or more cryptographic keys to secure a message. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption,. Envelope Key Encryption.
From speakerdeck.com
Protect sensitive data in pipeline with Tink and Cloud KMS as Envelope Envelope Key Encryption Envelope encryption is a technique that uses two layers of encryption. Envelope encryption uses two or more cryptographic keys to secure a message. When you encrypt your data, your data is protected, but you have to protect your encryption key. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier. Envelope Key Encryption.
From www.shutterstock.com
3d Illustration Of Mail Envelope With Key, Encryption Concept Envelope Key Encryption Typically, one key is derived from a longer. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. One layer secures the data. Envelope Key Encryption.
From cloudash.dev
How does AWS KMS Envelope Encryption work? — Cloudash Blog Envelope Key Encryption Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. One strategy is to encrypt. Envelope encryption is a technique that uses two layers of encryption. Typically, one key is derived from a longer. Envelope encryption uses two or more cryptographic keys to secure a. Envelope Key Encryption.
From www.mybscit.com
Explain Symmetric and Asymmetric key cryptography together Envelope Key Encryption One strategy is to encrypt. One layer secures the data through a blend of asymmetric and symmetric encryption. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. When you encrypt your data, your data is protected, but you have to protect your encryption key. Typically, one key. Envelope Key Encryption.
From medium.com
Securing Encryption Keys in the Cloud Part 1 (AWS KMS) by Thando Envelope Key Encryption When you encrypt your data, your data is protected, but you have to protect your encryption key. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Envelope encryption is a technique that uses two layers of encryption. Envelope encryption is the method of encrypting data with a. Envelope Key Encryption.
From www.alibabacloud.com
Use envelope encryption Key Management Service Alibaba Cloud Envelope Key Encryption Envelope encryption is a technique that uses two layers of encryption. Envelope encryption, by encrypting a data encryption key with a key encryption key, introduces a complex but highly effective barrier against unauthorized. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. Typically, one key is derived from a longer. An. Envelope Key Encryption.
From aws.amazon.com
How to Use Xplenty with AWS KMS to Provide FieldLevel Encryption in Envelope Key Encryption Typically, one key is derived from a longer. When you encrypt your data, your data is protected, but you have to protect your encryption key. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a. Envelope Key Encryption.
From subscription.packtpub.com
Solutions Architect's Handbook Envelope Key Encryption Typically, one key is derived from a longer. Envelope encryption is the method of encrypting data with a data encryption key (dek) and then encrypting the dek with a fully manageable root key. One strategy is to encrypt. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. When. Envelope Key Encryption.
From www.youtube.com
Use envelope encryption with data keys to protect messaging and Envelope Key Encryption One layer secures the data through a blend of asymmetric and symmetric encryption. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. Envelope encryption, by encrypting a data encryption key. Envelope Key Encryption.
From www.freecodecamp.org
How to Manage Encryption at Scale with Envelope Encryption & Key Envelope Key Encryption Kubernetes offers envelope encryption of secrets with a kms provider, meaning that a local key, commonly called a. One layer secures the data through a blend of asymmetric and symmetric encryption. An example of multiple layer of keys is envelope encryption, which is the process of encrypting a key with another key. Envelope encryption, by encrypting a data encryption key. Envelope Key Encryption.