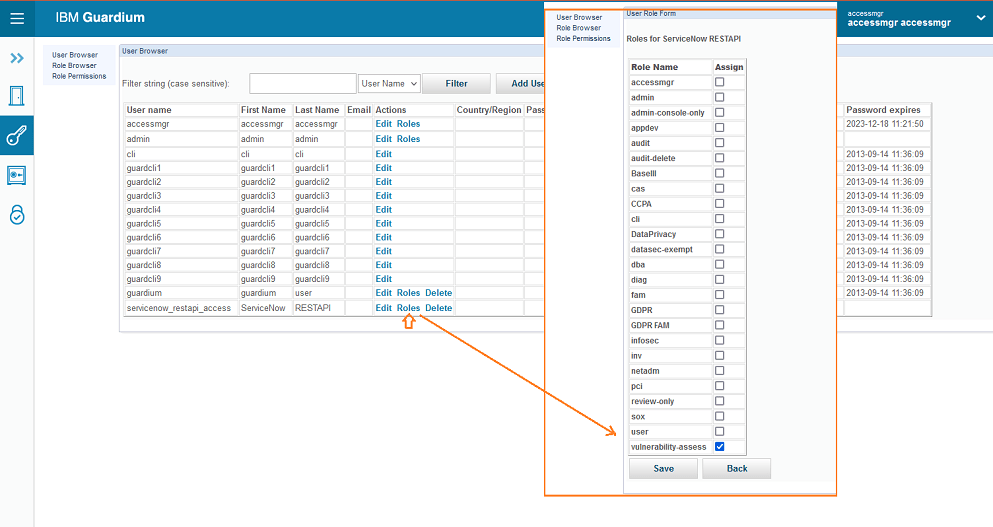
Servicenow Configure Image Vulnerability Keys . The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure approval rules for exception. It includes steps to get. Navigate to prisma cloud compute integration > configure image vulnerability keys b. Configure exception management for vulnerability response. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. The attached quickstart guide is a valuable resource to help you get started with vulnerability response.
from github-wiki-see.page
When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Navigate to prisma cloud compute integration > configure image vulnerability keys b. It includes steps to get. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure exception management for vulnerability response. Configure approval rules for exception. The attached quickstart guide is a valuable resource to help you get started with vulnerability response.
Getting started IBM/ServiceNowGuardiumVulnerabilityAssessment
Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. It includes steps to get. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure approval rules for exception. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets.
From www.invicti.com
Integrating Invicti Enterprise with ServiceNow Vulnerability Response Servicenow Configure Image Vulnerability Keys Navigate to prisma cloud compute integration > configure image vulnerability keys b. It includes steps to get. Configure approval rules for exception. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. The unified vulnerability response and attack surface dashboard is a single place to view aggregated. Servicenow Configure Image Vulnerability Keys.
From www.invicti.com
Integrating Invicti Enterprise with ServiceNow Vulnerability Response Servicenow Configure Image Vulnerability Keys It includes steps to get. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure. Servicenow Configure Image Vulnerability Keys.
From www.youtube.com
ServiceNow Demo Vulnerability Questionnaires YouTube Servicenow Configure Image Vulnerability Keys It includes steps to get. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure approval rules for exception. Navigate to prisma cloud compute integration > configure image vulnerability keys b. Configure exception management for vulnerability response. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack. Servicenow Configure Image Vulnerability Keys.
From ordr.net
Powering ServiceNow Vulnerability Response with Complete and Accurate Servicenow Configure Image Vulnerability Keys Configure approval rules for exception. It includes steps to get. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. Configure exception management for vulnerability response. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of. Servicenow Configure Image Vulnerability Keys.
From sysdig.com
Sysdig Brings Runtime Insights to ServiceNow Container Vulnerability Servicenow Configure Image Vulnerability Keys The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. It includes steps to get. Configure exception management for vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of. Servicenow Configure Image Vulnerability Keys.
From docs.crestron.com
Appendix A Configure ServiceNow for XiO Cloud Alerts Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. Configure approval rules for exception. Navigate to prisma cloud compute integration > configure image vulnerability keys b. It includes steps to get. The attached quickstart guide is a valuable resource to help you get started with vulnerability. Servicenow Configure Image Vulnerability Keys.
From www.invicti.com
Integrating Invicti Enterprise with ServiceNow Vulnerability Response Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The unified vulnerability response and attack surface dashboard is. Servicenow Configure Image Vulnerability Keys.
From www.youtube.com
servicenow vulnerability response Qualys integration Accelerate Servicenow Configure Image Vulnerability Keys The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure approval rules for exception. Configure exception management for vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of. Servicenow Configure Image Vulnerability Keys.
From kanini.com
How to Leverage the ServiceNow Vulnerability Response Application KANINI Servicenow Configure Image Vulnerability Keys The attached quickstart guide is a valuable resource to help you get started with vulnerability response. It includes steps to get. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure exception management for vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b.. Servicenow Configure Image Vulnerability Keys.
From kanini.com
How to Leverage the ServiceNow Vulnerability Response Application KANINI Servicenow Configure Image Vulnerability Keys The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. Configure approval rules for exception. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. The unified vulnerability response. Servicenow Configure Image Vulnerability Keys.
From sysdig.com
Reduce resolution time for container vulnerabilities with ServiceNow Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Navigate to prisma cloud compute integration > configure image vulnerability keys b. Configure approval rules for exception. It includes steps to get. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets.. Servicenow Configure Image Vulnerability Keys.
From securityonline.info
ServiceNow's 'Simple List' The Vulnerability Jeopardizing Thousands of Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Navigate to prisma cloud compute integration > configure image vulnerability keys b. Configure approval rules for exception. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. It includes steps to get. The unified vulnerability response and. Servicenow Configure Image Vulnerability Keys.
From www.invicti.com
Integrating Invicti Enterprise with ServiceNow Vulnerability Response Servicenow Configure Image Vulnerability Keys It includes steps to get. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. Configure approval rules for exception. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The unified vulnerability response and attack surface dashboard is a single place to view aggregated. Servicenow Configure Image Vulnerability Keys.
From aelumconsulting.com
Maximizing ServiceNow Application Vulnerability Response Aelum Consulting Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. It includes steps to get. The unified vulnerability response and attack surface dashboard is a. Servicenow Configure Image Vulnerability Keys.
From www.youtube.com
Configure NVD AutoUpdate Vulnerability Response Servicenow Tutorial by Servicenow Configure Image Vulnerability Keys The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure exception management for vulnerability response. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all.. Servicenow Configure Image Vulnerability Keys.
From www.youtube.com
ServiceNow Vulnerability Response Exception Process Walkthrough (New Servicenow Configure Image Vulnerability Keys The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure approval rules for exception. Configure exception management for vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. It includes steps to get. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack. Servicenow Configure Image Vulnerability Keys.
From github-wiki-see.page
Getting started IBM/ServiceNowGuardiumVulnerabilityAssessment Servicenow Configure Image Vulnerability Keys The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure approval rules for exception. Configure exception management for vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of. Servicenow Configure Image Vulnerability Keys.
From kanini.com
How to Leverage the ServiceNow Vulnerability Response Application Servicenow Configure Image Vulnerability Keys The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure exception management for vulnerability response. Configure approval rules for exception. Navigate to prisma cloud compute integration > configure image vulnerability keys b. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. The unified vulnerability response. Servicenow Configure Image Vulnerability Keys.
From github.com
GitHub IBM/ServiceNowGuardiumVulnerabilityAssessment Synchronize Servicenow Configure Image Vulnerability Keys Configure exception management for vulnerability response. Configure approval rules for exception. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. It includes steps to get. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. When used with the servicenow configuration management. Servicenow Configure Image Vulnerability Keys.
From www.real-sec.com
Automating Vulnerability Management with Qualys VMDR & ServiceNow Servicenow Configure Image Vulnerability Keys The attached quickstart guide is a valuable resource to help you get started with vulnerability response. It includes steps to get. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Navigate. Servicenow Configure Image Vulnerability Keys.
From aelumconsulting.com
Maximizing ServiceNow Application Vulnerability Response Aelum Consulting Servicenow Configure Image Vulnerability Keys It includes steps to get. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure approval rules for exception. Configure exception management for vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. When used with the servicenow configuration management database (cmdb), vulnerability response. Servicenow Configure Image Vulnerability Keys.
From www.real-sec.com
Automating Vulnerability Management with Qualys VMDR & ServiceNow Servicenow Configure Image Vulnerability Keys The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. It includes steps to get. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure. Servicenow Configure Image Vulnerability Keys.
From www.invicti.com
Integrating Invicti Enterprise with ServiceNow Vulnerability Response Servicenow Configure Image Vulnerability Keys Configure exception management for vulnerability response. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. It includes steps to get. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The attached quickstart guide is a valuable resource to help you get started with vulnerability response.. Servicenow Configure Image Vulnerability Keys.
From sysdig.com
Reduce resolution time for container vulnerabilities with ServiceNow Servicenow Configure Image Vulnerability Keys It includes steps to get. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. Configure approval rules for exception. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Navigate to prisma cloud compute integration. Servicenow Configure Image Vulnerability Keys.
From www.invicti.com
Integrating Invicti Enterprise with ServiceNow Vulnerability Response Servicenow Configure Image Vulnerability Keys Navigate to prisma cloud compute integration > configure image vulnerability keys b. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. It includes steps to get. Configure exception management for vulnerability response. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. The unified vulnerability response. Servicenow Configure Image Vulnerability Keys.
From snyk.io
Snyk enhances ServiceNow with comprehensive insights into Servicenow Configure Image Vulnerability Keys The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure approval rules for exception. Configure exception management for vulnerability response.. Servicenow Configure Image Vulnerability Keys.
From www.youtube.com
All about vulnerability groups Vulnerability Response ServiceNow Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. Configure approval rules for exception. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack. Servicenow Configure Image Vulnerability Keys.
From www.invicti.com
Integrating Invicti Enterprise with ServiceNow Vulnerability Response Servicenow Configure Image Vulnerability Keys Navigate to prisma cloud compute integration > configure image vulnerability keys b. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Configure exception management for vulnerability response. Configure approval rules for. Servicenow Configure Image Vulnerability Keys.
From techcommunity.microsoft.com
Microsoft vulnerability management integrates with ServiceNow VR Servicenow Configure Image Vulnerability Keys It includes steps to get. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Navigate to prisma cloud compute integration > configure image vulnerability keys b. Configure exception management for vulnerability response. The attached quickstart guide is a valuable resource to help you get started with vulnerability response.. Servicenow Configure Image Vulnerability Keys.
From aws.amazon.com
Sending Amazon Inspector’s Common Vulnerabilities and Exposures Servicenow Configure Image Vulnerability Keys The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure exception management for vulnerability response. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Navigate to prisma cloud compute integration > configure image vulnerability keys b. Configure approval rules for exception.. Servicenow Configure Image Vulnerability Keys.
From github-wiki-see.page
Getting started IBM/ServiceNowGuardiumVulnerabilityAssessment Servicenow Configure Image Vulnerability Keys Configure approval rules for exception. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure exception management for vulnerability response. The attached quickstart guide is a valuable resource to help you get started with vulnerability response.. Servicenow Configure Image Vulnerability Keys.
From techcommunity.microsoft.com
Microsoft vulnerability management integrates with ServiceNow VR Servicenow Configure Image Vulnerability Keys The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure approval rules for exception. Configure. Servicenow Configure Image Vulnerability Keys.
From www.youtube.com
Microsoft TVM Integration with ServiceNow Vulnerability Response YouTube Servicenow Configure Image Vulnerability Keys Configure approval rules for exception. It includes steps to get. When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. Configure exception management for vulnerability. Servicenow Configure Image Vulnerability Keys.
From www.paloaltonetworks.com
Prisma Cloud Secures Containers with ServiceNow Vulnerability Response Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. The unified vulnerability response and attack surface dashboard is a single place to view aggregated attack surface data for all assets. Configure approval rules for exception. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The attached quickstart guide is. Servicenow Configure Image Vulnerability Keys.
From aelumconsulting.com
Maximizing ServiceNow Application Vulnerability Response Aelum Consulting Servicenow Configure Image Vulnerability Keys When used with the servicenow configuration management database (cmdb), vulnerability response provides a comprehensive view of all. Navigate to prisma cloud compute integration > configure image vulnerability keys b. The attached quickstart guide is a valuable resource to help you get started with vulnerability response. It includes steps to get. Configure exception management for vulnerability response. The unified vulnerability response. Servicenow Configure Image Vulnerability Keys.