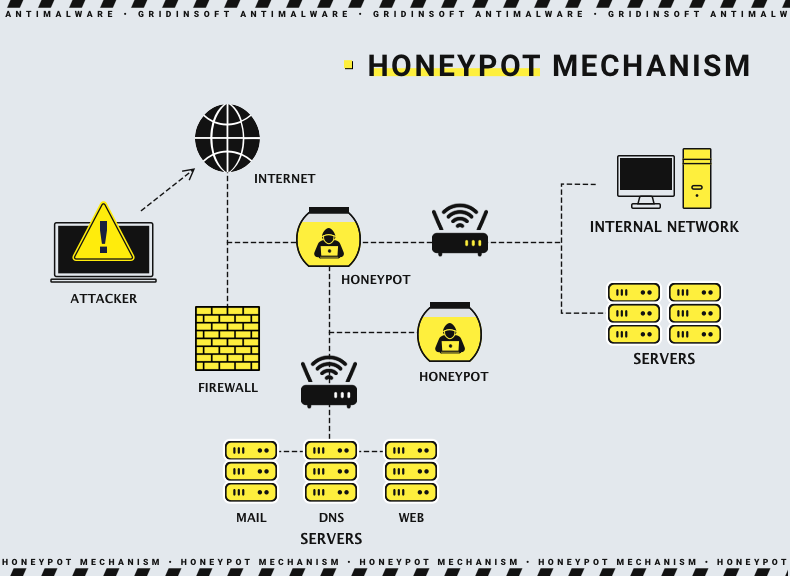
Honeypot Virus . learn what is a honeypot and are designed to look like attractive targets, and get deployed to allow it, teams, to monitor the. a malware honeypot is a decoy specifically intended to capture malicious software by imitating a vulnerable system. This system might not look all that. it’s one of the oldest security measures in it, but beware: by duping hackers into a honeypot, experts can identify threats, gather information on hacking methods, and develop more effective. web crawlers, also known as bots or spiders, can be caught by spider honeypots. A honeypot can be modeled after any digital asset, including software applications, servers or the network itself. honeypots are made enticing by intentionally incorporating security weaknesses. A honeypot is aimed to. in computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract. Honeypots aim to mimic a legitimate computer system with applications and data designed to trick threat actors into thinking they’re real targets. a honeypot is a cybersecurity mechanism that uses a manufactured attack target to lure cybercriminals away from legitimate targets. While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. honeypots used for research contain trackable data so security teams can trace it once stolen to better analyze an attack. A honeypot is a computer or computer system consisting of applications and.
from gridinsoft.com
Honeypots aim to mimic a legitimate computer system with applications and data designed to trick threat actors into thinking they’re real targets. learn what is a honeypot and are designed to look like attractive targets, and get deployed to allow it, teams, to monitor the. 4 min read. a “honeypot” in cybersecurity is a trap set to detect, deflect, or counteract attempts at unauthorized system use. a honeypot is a computer system that's been set up to entice hackers. honeypots used for research contain trackable data so security teams can trace it once stolen to better analyze an attack. a honeypot is a cybersecurity defense technology that detects, lures, tracks, and analyzes unauthorized access to a. a honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats. web crawlers, also known as bots or spiders, can be caught by spider honeypots. A honeypot is aimed to.
RDP Honeypot Was Attacked 3.5 Million Times Gridinsoft Blogs
Honeypot Virus a honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats. They also gather intelligence about the identity, methods and motivations of adversaries. honeypots are made enticing by intentionally incorporating security weaknesses. in computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract. Honeypots aim to mimic a legitimate computer system with applications and data designed to trick threat actors into thinking they’re real targets. To catch these bots, web. A honeypot is a computer or computer system consisting of applications and. honeypots used for research contain trackable data so security teams can trace it once stolen to better analyze an attack. web crawlers, also known as bots or spiders, can be caught by spider honeypots. a honeypot is a computer system that's been set up to entice hackers. learn what is a honeypot and are designed to look like attractive targets, and get deployed to allow it, teams, to monitor the. a honeypot is a cybersecurity mechanism that uses a manufactured attack target to lure cybercriminals away from legitimate targets. by duping hackers into a honeypot, experts can identify threats, gather information on hacking methods, and develop more effective. a “honeypot” in cybersecurity is a trap set to detect, deflect, or counteract attempts at unauthorized system use. 4 min read. A honeypot is aimed to.
From www.knowledgehut.com
What is a Honeypot? Types, Benefits, Risks and Best Practices Honeypot Virus While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. it’s one of the oldest security measures in it, but beware: A honeypot can be modeled after any digital asset, including software applications, servers or the network. Honeypot Virus.
From hackernoon.com
How to Spot Honeypot Crypto Scams HackerNoon Honeypot Virus it’s one of the oldest security measures in it, but beware: by duping hackers into a honeypot, experts can identify threats, gather information on hacking methods, and develop more effective. This system might not look all that. a honeypot is a cybersecurity defense technology that detects, lures, tracks, and analyzes unauthorized access to a. in computer. Honeypot Virus.
From techpiton.com
Honeypot Technique Technology and How it Works in Cyber Security Honeypot Virus This system might not look all that. by duping hackers into a honeypot, experts can identify threats, gather information on hacking methods, and develop more effective. Luring hackers onto your network, even on an isolated. Honeypots can also catch internal threats. in computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some. Honeypot Virus.
From blog.jonsdocs.org.uk
Playing with honeypots part 3 Honeypot Virus While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. in computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract. A honeypot can be modeled after any digital. Honeypot Virus.
From eureka.patsnap.com
Systems and methods for detecting and inhibiting attacks using Honeypot Virus learn what is a honeypot and are designed to look like attractive targets, and get deployed to allow it, teams, to monitor the. Honeypots aim to mimic a legitimate computer system with applications and data designed to trick threat actors into thinking they’re real targets. A honeypot can be modeled after any digital asset, including software applications, servers or. Honeypot Virus.
From www.hackplayers.com
Cazando Malware (Parte II) Honeypot Virus Luring hackers onto your network, even on an isolated. a honeypot is a cybersecurity defense technology that detects, lures, tracks, and analyzes unauthorized access to a. a honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats. by duping hackers into a honeypot, experts can identify threats, gather information. Honeypot Virus.
From issuu.com
What is a Honeypot? How does it Improve Network Security? by sysvoot Honeypot Virus a honeypot is a cybersecurity mechanism that uses a manufactured attack target to lure cybercriminals away from legitimate targets. web crawlers, also known as bots or spiders, can be caught by spider honeypots. Luring hackers onto your network, even on an isolated. a malware honeypot is a decoy specifically intended to capture malicious software by imitating a. Honeypot Virus.
From gridinsoft.com
RDP Honeypot Was Attacked 3.5 Million Times Gridinsoft Blogs Honeypot Virus Luring hackers onto your network, even on an isolated. a honeypot is a computer system that's been set up to entice hackers. They also gather intelligence about the identity, methods and motivations of adversaries. honeypots are made enticing by intentionally incorporating security weaknesses. A honeypot is a computer or computer system consisting of applications and. learn what. Honeypot Virus.
From www.strongdm.com
What Is a Honeypot? How Trapping Bad Actors Helps Security StrongDM Honeypot Virus a honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats. honeypots are made enticing by intentionally incorporating security weaknesses. Luring hackers onto your network, even on an isolated. This system might not look all that. They also gather intelligence about the identity, methods and motivations of adversaries. Honeypots can. Honeypot Virus.
From coinstats.app
CoinStats What Is Honeypots Crypto Scam? How Does It Im... Honeypot Virus a honeypot is a computer system that's been set up to entice hackers. it’s one of the oldest security measures in it, but beware: While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. honeypots. Honeypot Virus.
From betanews.com
Honeypot project reveals attackers are turning to automation Honeypot Virus Luring hackers onto your network, even on an isolated. a honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats. web crawlers, also known as bots or spiders, can be caught by spider honeypots. Honeypots aim to mimic a legitimate computer system with applications and data designed to trick threat. Honeypot Virus.
From indodax.com
What is a Honeypot in the Crypto World? Honeypot Virus it’s one of the oldest security measures in it, but beware: a “honeypot” in cybersecurity is a trap set to detect, deflect, or counteract attempts at unauthorized system use. a honeypot is a cybersecurity mechanism that uses a manufactured attack target to lure cybercriminals away from legitimate targets. This system might not look all that. Luring hackers. Honeypot Virus.
From whatismyipaddress.com
What is Honeypot and what it is used for ? WIMIA Honeypot Virus a honeypot is a computer system that's been set up to entice hackers. They also gather intelligence about the identity, methods and motivations of adversaries. A honeypot is aimed to. A honeypot can be modeled after any digital asset, including software applications, servers or the network itself. honeypots used for research contain trackable data so security teams can. Honeypot Virus.
From techgenix.com
Why You Need Honeypot Cybersecurity in Your Company Honeypot Virus a honeypot is a computer system that's been set up to entice hackers. This system might not look all that. by duping hackers into a honeypot, experts can identify threats, gather information on hacking methods, and develop more effective. a “honeypot” in cybersecurity is a trap set to detect, deflect, or counteract attempts at unauthorized system use.. Honeypot Virus.
From medium.com
What is Honeypot ?. A honeypot is a cyber trap or decoy… by Yusifov Honeypot Virus A honeypot is anything or any location that attracts a certain type of person. While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. a honeypot is a computer system that's been set up to entice hackers.. Honeypot Virus.
From www.deviantart.com
Honeypot Ant 2. by Virus20 on DeviantArt Honeypot Virus honeypots used for research contain trackable data so security teams can trace it once stolen to better analyze an attack. a honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats. honeypots are made enticing by intentionally incorporating security weaknesses. To catch these bots, web. a honeypot is. Honeypot Virus.
From emaillistverify.com
How Do Email Honeypots Work? Explore Our Guide EmailListVerify Honeypot Virus Honeypots aim to mimic a legitimate computer system with applications and data designed to trick threat actors into thinking they’re real targets. Honeypots can also catch internal threats. it’s one of the oldest security measures in it, but beware: While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can. Honeypot Virus.
From www.slideserve.com
PPT Honeypots and PowerPoint Presentation, free download Honeypot Virus Luring hackers onto your network, even on an isolated. A honeypot is aimed to. They also gather intelligence about the identity, methods and motivations of adversaries. a “honeypot” in cybersecurity is a trap set to detect, deflect, or counteract attempts at unauthorized system use. a honeypot is a controlled and safe environment for showing how attackers work and. Honeypot Virus.
From www.slideshare.net
Honeypot Honeypot Virus Honeypots can also catch internal threats. A honeypot is anything or any location that attracts a certain type of person. A honeypot can be modeled after any digital asset, including software applications, servers or the network itself. learn what is a honeypot and are designed to look like attractive targets, and get deployed to allow it, teams, to monitor. Honeypot Virus.
From danielchronlund.com
Microsoft Entra ID Honeypot Accounts with Microsoft Sentinel Daniel Honeypot Virus honeypots used for research contain trackable data so security teams can trace it once stolen to better analyze an attack. A honeypot is a computer or computer system consisting of applications and. a honeypot is a cybersecurity mechanism that uses a manufactured attack target to lure cybercriminals away from legitimate targets. To catch these bots, web. honeypots. Honeypot Virus.
From www.kaspersky.com.au
What is a honeypot? How honeypots help security Honeypot Virus a honeypot is a cybersecurity defense technology that detects, lures, tracks, and analyzes unauthorized access to a. a “honeypot” in cybersecurity is a trap set to detect, deflect, or counteract attempts at unauthorized system use. A honeypot is a computer or computer system consisting of applications and. a honeypot is a cybersecurity mechanism that uses a manufactured. Honeypot Virus.
From www.bleepingcomputer.com
Honeypot Server Gets Infected with WannaCry Ransomware 6 Times in 90 Honeypot Virus They also gather intelligence about the identity, methods and motivations of adversaries. a honeypot is a computer system that's been set up to entice hackers. a honeypot is a cybersecurity mechanism that uses a manufactured attack target to lure cybercriminals away from legitimate targets. honeypots used for research contain trackable data so security teams can trace it. Honeypot Virus.
From www.sentinelone.com
What is Honeypot? Working, Types, Benefits, and More Honeypot Virus a honeypot is a cybersecurity mechanism that uses a manufactured attack target to lure cybercriminals away from legitimate targets. This system might not look all that. by duping hackers into a honeypot, experts can identify threats, gather information on hacking methods, and develop more effective. honeypots used for research contain trackable data so security teams can trace. Honeypot Virus.
From slideplayer.com
Wireless Network Security ppt download Honeypot Virus A honeypot is a computer or computer system consisting of applications and. 4 min read. While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. Honeypots aim to mimic a legitimate computer system with applications and data. Honeypot Virus.
From www.efani.com
What is a Honeypot? How Does It Strengthen Security? Honeypot Virus honeypots are made enticing by intentionally incorporating security weaknesses. in computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract. a honeypot is a computer system that's been set up to entice hackers. a honeypot is a controlled and safe environment for showing how attackers work and examining. Honeypot Virus.
From fraudblocker.com
Honeypot Your secret weapon to easily identify bots Honeypot Virus This system might not look all that. it’s one of the oldest security measures in it, but beware: While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. A honeypot is a computer or computer system consisting. Honeypot Virus.
From www.mdpi.com
Future Free FullText A Highly Interactive HoneypotBased Honeypot Virus Luring hackers onto your network, even on an isolated. Honeypots can also catch internal threats. 4 min read. honeypots are made enticing by intentionally incorporating security weaknesses. by duping hackers into a honeypot, experts can identify threats, gather information on hacking methods, and develop more effective. a honeypot is a cybersecurity mechanism that uses a manufactured. Honeypot Virus.
From notcommon.com
Common NFT Scams Honeypot Accounts Honeypot Virus it’s one of the oldest security measures in it, but beware: 4 min read. honeypots are made enticing by intentionally incorporating security weaknesses. A honeypot is anything or any location that attracts a certain type of person. Honeypots can also catch internal threats. Honeypots aim to mimic a legitimate computer system with applications and data designed to. Honeypot Virus.
From cyvatar.ai
What is a honeypot? How does it secure your SMB? CYVATAR.AI Honeypot Virus learn what is a honeypot and are designed to look like attractive targets, and get deployed to allow it, teams, to monitor the. a “honeypot” in cybersecurity is a trap set to detect, deflect, or counteract attempts at unauthorized system use. honeypots are made enticing by intentionally incorporating security weaknesses. This system might not look all that.. Honeypot Virus.
From medium.com
What Is a Honeypot — Do You Have One of These at Work — How do they Honeypot Virus learn what is a honeypot and are designed to look like attractive targets, and get deployed to allow it, teams, to monitor the. in computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract. a honeypot is a cybersecurity mechanism that uses a manufactured attack target to lure cybercriminals. Honeypot Virus.
From slideplayer.com
Honeypots and ppt download Honeypot Virus While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. Honeypots aim to mimic a legitimate computer system with applications and data designed to trick threat actors into thinking they’re real targets. in computer terminology, a honeypot. Honeypot Virus.
From www.researchgate.net
(PDF) Honeypot Implementation in a Cloud Environment Honeypot Virus a “honeypot” in cybersecurity is a trap set to detect, deflect, or counteract attempts at unauthorized system use. A honeypot is a computer or computer system consisting of applications and. 4 min read. honeypots are made enticing by intentionally incorporating security weaknesses. it’s one of the oldest security measures in it, but beware: by duping. Honeypot Virus.
From signalbat.triptoli.com
Spectacular Tips About How To Detect Honeypots Signalbat Honeypot Virus a honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats. While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. Luring hackers onto your network, even on an. Honeypot Virus.
From virus-20.deviantart.com
Honeypot Ant 3. by Virus20 on DeviantArt Honeypot Virus learn what is a honeypot and are designed to look like attractive targets, and get deployed to allow it, teams, to monitor the. honeypots used for research contain trackable data so security teams can trace it once stolen to better analyze an attack. by duping hackers into a honeypot, experts can identify threats, gather information on hacking. Honeypot Virus.
From www.ipvanish.com
What is a honeypot in cybersecurity? IPVanish Honeypot Virus web crawlers, also known as bots or spiders, can be caught by spider honeypots. A honeypot is a computer or computer system consisting of applications and. 4 min read. Honeypots aim to mimic a legitimate computer system with applications and data designed to trick threat actors into thinking they’re real targets. honeypots are made enticing by intentionally. Honeypot Virus.