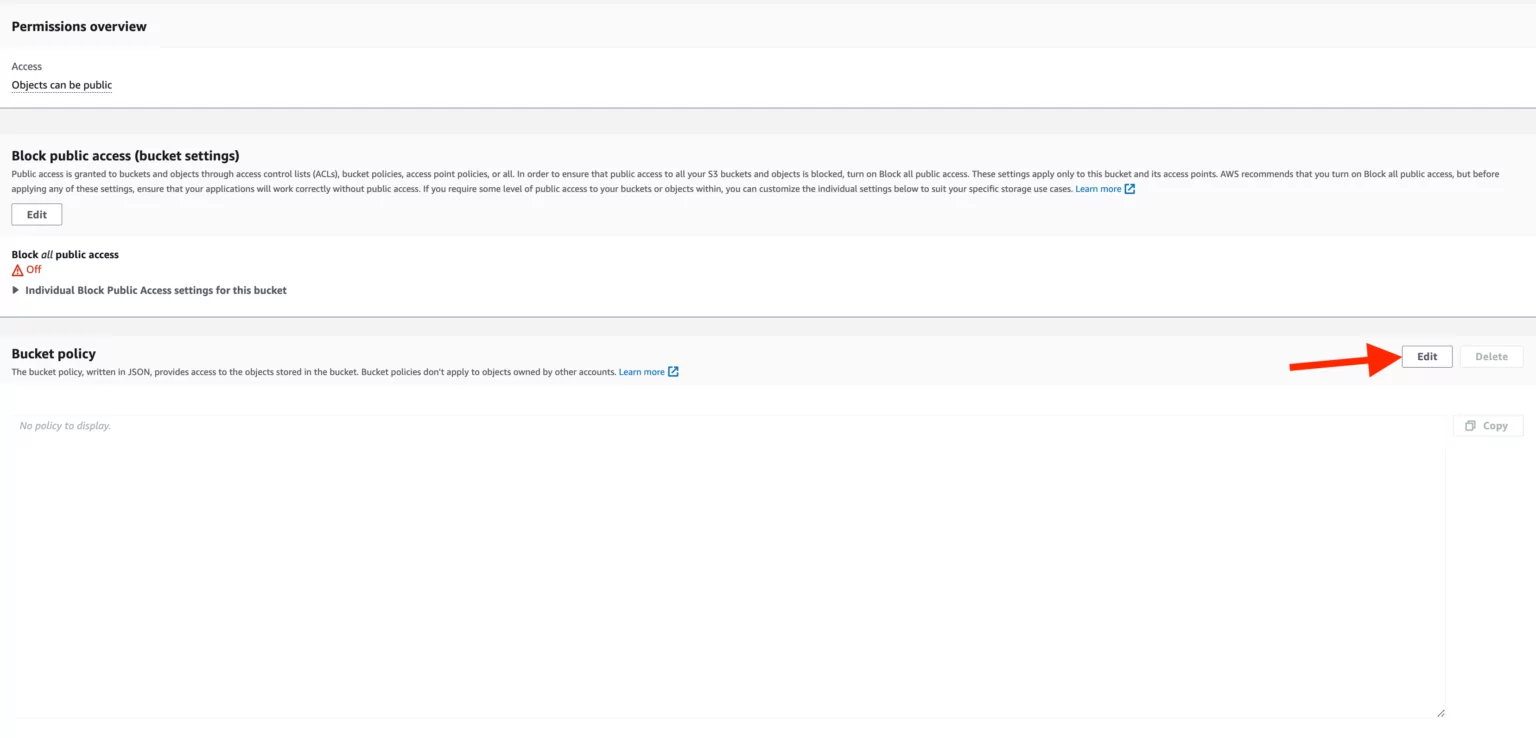
Aws Bucket Vulnerability . It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. So i thought why not. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. The following security best practices also address configuration and vulnerability analysis in amazon s3: Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully.
from socradar.io
Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. So i thought why not. The following security best practices also address configuration and vulnerability analysis in amazon s3: It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program.
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection
Aws Bucket Vulnerability This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. So i thought why not. The following security best practices also address configuration and vulnerability analysis in amazon s3: This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully.
From blog.securelayer7.net
Amazon AWS S3 Bucket Account Takeover Vulnerability Aws Bucket Vulnerability Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cloudformation was the first aws service that. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. The following security best practices also address configuration and vulnerability analysis in amazon s3: It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. The. Aws Bucket Vulnerability.
From www.vrogue.co
Aws S3 Bucket A Complete Guide To Create And Access D vrogue.co Aws Bucket Vulnerability The following security best practices also address configuration and vulnerability analysis in amazon s3: So i thought why not. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. The aws s3. Aws Bucket Vulnerability.
From www.youtube.com
HOW TO FIND AWS S3 BUCKET MISCONFIGURATION VULNERABILITIES CLOUD Aws Bucket Vulnerability Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. The aws s3 bucket takeover is. Aws Bucket Vulnerability.
From www.youtube.com
AWS S3 Bucket Versioning Implementation & Benefit YouTube Aws Bucket Vulnerability This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. Cybersecurity researchers. Aws Bucket Vulnerability.
From blog.securelayer7.net
Amazon AWS S3 Bucket Account Takeover Vulnerability Aws Bucket Vulnerability Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. The following security best practices also address configuration and vulnerability analysis. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. So i thought why not. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Aws Bucket Vulnerability Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. So i thought why not. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. The following security best practices. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. Recently i came across s3. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. Cloudformation was the first aws service that aqua tried to exploit — and successfully found. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. So i thought why not. The following security best practices also address configuration and vulnerability analysis in amazon s3: It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The aws s3 bucket takeover is a. Aws Bucket Vulnerability.
From blog.securelayer7.net
Handson Amazon S3 Bucket Vulnerabilities and learn exploiting them Aws Bucket Vulnerability So i thought why not. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Aws Bucket Vulnerability Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. The following security best practices also address configuration and vulnerability analysis in amazon s3: So i thought why not. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. It. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. So i thought why not. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. Recently i. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. The following security best practices also address configuration and vulnerability analysis in amazon s3: It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api. Aws Bucket Vulnerability.
From blog.securelayer7.net
Amazon AWS S3 Bucket Account Takeover Vulnerability Aws Bucket Vulnerability Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. The following security best practices also address configuration and vulnerability analysis in amazon s3: It is critical for cloud pen testers to understand the indicators of. Aws Bucket Vulnerability.
From vpnoverview.com
A Complete Guide to Securing and Protecting AWS S3 Buckets Aws Bucket Vulnerability It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. The following. Aws Bucket Vulnerability.
From blog.securelayer7.net
Amazon AWS S3 Bucket Account Takeover Vulnerability Aws Bucket Vulnerability It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. So i thought why not. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. Cloudformation was the first aws service. Aws Bucket Vulnerability.
From www.secureworld.io
'GhostWriter' Newly Discovered AWS S3 Bucket Threat Aws Bucket Vulnerability It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. The following security best practices also address configuration and vulnerability analysis in amazon s3: This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api. Aws Bucket Vulnerability.
From www.helecloud.com
Container Vulnerability Scanning on AWS with Clair and AWS Fargate Aws Bucket Vulnerability It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. The following security best practices also address configuration. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Aws Bucket Vulnerability It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. Cybersecurity researchers have. Aws Bucket Vulnerability.
From www.youtube.com
Identify vulnerable AWS buckets using AWSBucketDump YouTube Aws Bucket Vulnerability So i thought why not. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. Cybersecurity researchers have. Aws Bucket Vulnerability.
From blog.securelayer7.net
Amazon AWS S3 Bucket Account Takeover Vulnerability Aws Bucket Vulnerability Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. The following security best practices also address configuration and vulnerability analysis in amazon s3: So i thought why not. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. The aws s3 bucket takeover is a powerful. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cloudformation was the first aws. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability So i thought why not. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. This example describes how. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. This example describes how to create a cloudwatch alarm. Aws Bucket Vulnerability.
From www.armorcode.com
AWS S3 Bucket Security The Top CSPM Practices ArmorCode Aws Bucket Vulnerability The following security best practices also address configuration and vulnerability analysis in amazon s3: The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. It is critical for cloud pen testers to understand the indicators of. Aws Bucket Vulnerability.
From avd.aquasec.com
S3BucketVersioning Vulnerability Database Aqua Security Aws Bucket Vulnerability It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. Recently i came across s3 bucket misconfiguration vulnerability. Aws Bucket Vulnerability.
From blog.securelayer7.net
Amazon AWS S3 Bucket Account Takeover Vulnerability Aws Bucket Vulnerability Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. Cloudformation was the first aws service. Aws Bucket Vulnerability.
From aws.amazon.com
Vulnerability Assessment AWS Security Blog Aws Bucket Vulnerability It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage service. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. So i thought why not. Cloudformation was the first aws service that aqua. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Aws Bucket Vulnerability Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. So i thought why not. Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. The following security best practices also address configuration and vulnerability analysis in amazon s3: The aws s3 bucket takeover is a powerful. Aws Bucket Vulnerability.
From avd.aquasec.com
S3BucketAllUsersACL Vulnerability Database Aqua Security Aws Bucket Vulnerability Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. Cybersecurity researchers. Aws Bucket Vulnerability.
From onica.com
Vulnerability Detection in Containerized Architectures on AWS Onica Aws Bucket Vulnerability Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. It is critical for cloud pen testers to understand the indicators of s3 bucket vulnerabilities. The following security best practices also address configuration and vulnerability analysis in amazon s3: This example describes how to create a cloudwatch alarm that is triggered. Aws Bucket Vulnerability.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Aws Bucket Vulnerability So i thought why not. This example describes how to create a cloudwatch alarm that is triggered when an amazon s3 api call is made to put or delete. Recently i came across s3 bucket misconfiguration vulnerability on one of the private program. The aws s3 bucket takeover is a powerful attack that targets misconfigured buckets on amazon’s cloud storage. Aws Bucket Vulnerability.
From www.securityhq.com
Security 101 Compromised AWS S3 Buckets SecurityHQ Aws Bucket Vulnerability Cloudformation was the first aws service that aqua tried to exploit — and successfully found exposed hashes on github. Cybersecurity researchers have discovered multiple critical flaws in amazon web services (aws) offerings that, if successfully. The following security best practices also address configuration and vulnerability analysis in amazon s3: Recently i came across s3 bucket misconfiguration vulnerability on one of. Aws Bucket Vulnerability.