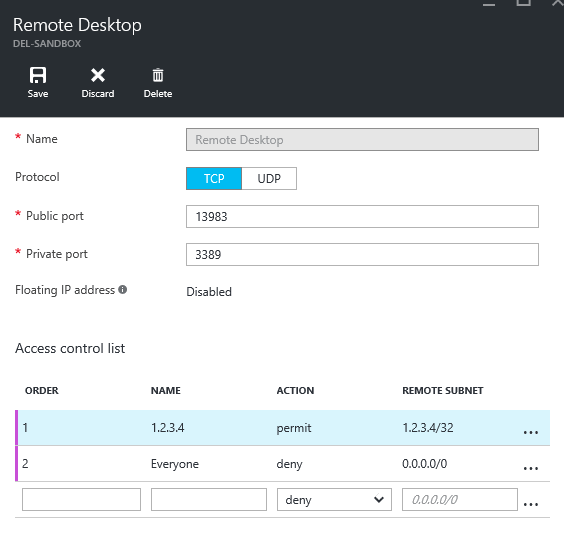
Network Acl Azure . Ip acls are useful for reducing network security. Ip acls are useful for. Powershell, az cli and postman. Ip based acls can be set up at different levels of a network from the network device to firewalls. Using network acls, you can do the following: Azure has a rich set of networking mechanisms that customers can use to secure their applications. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip based acls can be set up at different levels of a network from the network device to firewalls. Network acls can be configured to restrict access. Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods:
from www.mssqltips.com
Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Powershell, az cli and postman. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip acls are useful for reducing network security. Ip based acls can be set up at different levels of a network from the network device to firewalls. Using network acls, you can do the following: Network acls can be configured to restrict access. Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Ip acls are useful for.
Configuring SQL Server Endpoint and ACL Access in Windows Azure
Network Acl Azure Ip acls are useful for. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Ip acls are useful for. Powershell, az cli and postman. Ip acls are useful for reducing network security. Azure has a rich set of networking mechanisms that customers can use to secure their applications. Ip based acls can be set up at different levels of a network from the network device to firewalls. Network acls can be configured to restrict access. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Using network acls, you can do the following: Ip based acls can be set up at different levels of a network from the network device to firewalls. Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling.
From github.com
[Bug Report] Problems adding an ip address into the network acl Network Acl Azure Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip acls are useful for reducing network security. Powershell, az cli and postman. Azure has a rich set of networking mechanisms that customers can use to secure their applications. In this article, i will walk you through the process of setting azure storage account acls recursively using three. Network Acl Azure.
From www.softwaredesignpartners.com
Azure Application Gateway Network Acl Azure Ip based acls can be set up at different levels of a network from the network device to firewalls. Powershell, az cli and postman. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Azure has a rich set of networking mechanisms that customers can use to secure their applications. Ip acls are useful for. Ip acls are. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Selectively permit or deny incoming traffic based on remote subnet ipv4 address. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Ip acls are useful for. Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip based acls. Network Acl Azure.
From learn.microsoft.com
Azure portal を使用して Azure Data Lake Storage Gen2 で ACL を管理する Azure Network Acl Azure Ip acls are useful for reducing network security. Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Using network acls, you can do the following: Powershell, az cli and postman. Network acls can be configured to restrict. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Azure has a rich set of networking mechanisms that customers can use to secure their applications. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Ip acls are useful for. Network (or endpoint) access control list. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Network acls can be configured to restrict access. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Powershell, az cli and postman. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Using network acls, you can do the following: Ip based acls can be set. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Azure has a rich set of networking mechanisms that customers can use to secure their applications. Powershell, az cli and postman. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Using network acls, you can do the following: Ip based acls can be set up at different levels. Network Acl Azure.
From secops.one
Azure virtual network service endpoints Amal Mammadov Network Acl Azure Using network acls, you can do the following: Ip acls are useful for. Ip based acls can be set up at different levels of a network from the network device to firewalls. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Powershell, az cli and postman. Network acls. Network Acl Azure.
From learn.microsoft.com
Secure your resources with Conditional Access policy templates Network Acl Azure Ip based acls can be set up at different levels of a network from the network device to firewalls. Using network acls, you can do the following: Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Ip based acls can be set up at different levels of a network. Network Acl Azure.
From www.mssqltips.com
Configuring SQL Server Endpoint and ACL Access in Windows Azure Network Acl Azure Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip acls are useful for reducing network security. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods:. Network Acl Azure.
From www.thenetworkdna.com
Introduction to Azure Network Security Group (NSG) The Network DNA Network Acl Azure Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip acls are useful for reducing network security. Powershell, az cli and postman. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Selectively permit or deny incoming traffic based. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip acls are useful for reducing network security. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Using network acls, you can do the following: Powershell, az cli and postman. Network acls can be configured to. Network Acl Azure.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Network Acl Azure Using network acls, you can do the following: Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip acls are useful for reducing network security. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Network acls can be. Network Acl Azure.
From learn.microsoft.com
Architecture Global transit network architecture Azure Virtual WAN Network Acl Azure Azure has a rich set of networking mechanisms that customers can use to secure their applications. Network acls can be configured to restrict access. Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip acls are useful for reducing network security. Powershell, az cli and postman. Selectively permit or deny. Network Acl Azure.
From learn.microsoft.com
استخدم مدخل Microsoft Azure لإدارة قوائمACL في Azure Data Lake Storage Network Acl Azure Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Ip based acls can be set up at different levels of a network from the network device to firewalls. Powershell, az cli and postman. Ip acls are useful for reducing network security. Azure has a rich set of networking mechanisms. Network Acl Azure.
From www.agilevision.io
AWS Networking connectivity, network ACLs, and security groups Network Acl Azure Ip based acls can be set up at different levels of a network from the network device to firewalls. Using network acls, you can do the following: Ip acls are useful for. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Azure has a rich set of networking mechanisms that customers can use to secure their applications.. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Ip based acls can be set up at different levels of a network from the network device to firewalls. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip acls are useful for reducing network security. Azure. Network Acl Azure.
From www.snp.com
Azure’s Software Defined Connectivity — Virtual WAN SNP Technologies Network Acl Azure Ip acls are useful for. Ip acls are useful for reducing network security. Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Azure has a rich set of networking mechanisms that customers can use to secure their applications. Selectively permit or deny incoming traffic based on remote subnet ipv4. Network Acl Azure.
From harvestingclouds.com
Azure for AWS professionals Networking AWS 04 Network ACLs Network Acl Azure Using network acls, you can do the following: Network acls can be configured to restrict access. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip based acls can be set up at different levels of a network from the network device to firewalls. Network (or endpoint) access control list (acl) are the key to protecting web. Network Acl Azure.
From www.thenetworkdna.com
Azure NSG Vs Azure Firewall The Network DNA Network Acl Azure Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Ip based acls can be set up at different levels of a network from the network device to firewalls. Azure has a rich set of networking mechanisms that customers can use to secure their applications. Selectively permit or deny incoming. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Network acls can be configured to restrict access. Powershell, az cli and postman. Ip acls are useful for. Ip acls are useful for reducing network security. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Azure has. Network Acl Azure.
From tutorialsdojo.com
Azure Virtual Network Tutorials Dojo Network Acl Azure Network acls can be configured to restrict access. Ip acls are useful for reducing network security. Ip acls are useful for. Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip based acls can be set up at different levels of a network from the network device to firewalls. Using. Network Acl Azure.
From learn.microsoft.com
Networklevel segmentation workloads Azure Architecture Center Network Acl Azure Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip acls are useful for reducing network security. Using network acls, you can do the following: Ip based acls can be set up at different levels of a network. Network Acl Azure.
From www.opsramp.com
Azure Firewall vs NSG Tutorial & Examples OpsRamp Network Acl Azure Ip acls are useful for reducing network security. Network acls can be configured to restrict access. Ip based acls can be set up at different levels of a network from the network device to firewalls. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Powershell, az cli and. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Powershell, az cli and postman. Using network acls, you can do the following: Ip based acls can be set up at different levels of a network from the network device to firewalls. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Ip acls are useful for. Ip acls. Network Acl Azure.
From www.youtube.com
Learn AWS VPC Route Table, Gateway, Network ACL, Security Network Acl Azure In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Azure has a rich set of networking mechanisms that customers can use to secure their applications. Using network acls, you can do the following: Network (or endpoint) access control list (acl) are the key to protecting web or worker. Network Acl Azure.
From exyrqoycy.blob.core.windows.net
Network Acl Equivalent In Azure at Ramonita Wagner blog Network Acl Azure Powershell, az cli and postman. Ip based acls can be set up at different levels of a network from the network device to firewalls. Network acls can be configured to restrict access. Ip acls are useful for reducing network security. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip acls are useful for. Ip based acls. Network Acl Azure.
From blog.azureinfra.com
How to connect to Azure Services Network Acl Azure Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip acls are useful for reducing network security. Ip acls are useful for. Network acls can be configured to restrict access. Using network acls, you can do the following: Ip based acls can be set up at different levels of a network from the network device to firewalls.. Network Acl Azure.
From www.keepsecure.ca
Exploring Azure Virtual WAN Keep Secure IT Security Network Acl Azure Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Using network acls, you can do the following: In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Selectively permit or deny incoming traffic based on remote subnet ipv4. Network Acl Azure.
From cloudiofy.com
How to control network traffic using Network ACL Network Acl Azure Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Ip acls are useful for reducing network security. Powershell, az cli and postman. Network acls can be configured to restrict access. Using network acls, you can do the following: In this article, i will walk you through the process of. Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Ip acls are useful for reducing network security. Using network acls, you can do the following: Network (or endpoint) access control list (acl) are the key to protecting web or worker role public endpoints and controlling. Network acls can. Network Acl Azure.
From www.opsramp.com
Azure Firewall vs NSG Tutorial & Examples OpsRamp Network Acl Azure Powershell, az cli and postman. Ip acls are useful for. Using network acls, you can do the following: Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Ip based acls can be set up at different levels of a network from the network device to firewalls. Ip acls are useful for reducing network security. Network (or endpoint). Network Acl Azure.
From vcloud-lab.com
CREATE NEW NSG SECURITY GROUP VIRTUAL FIREWALL ACL) ON Network Acl Azure Using network acls, you can do the following: Ip acls are useful for. Ip acls are useful for reducing network security. Ip based acls can be set up at different levels of a network from the network device to firewalls. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Network (or endpoint) access control list (acl) are. Network Acl Azure.
From www.opsramp.com
Azure Firewall vs NSG Tutorial & Examples OpsRamp Network Acl Azure Powershell, az cli and postman. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. Using network acls, you can do the following: Ip acls are useful for. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Azure has a rich set of networking mechanisms that. Network Acl Azure.
From learn.microsoft.com
Azure portal を使用して Azure Data Lake Storage Gen2 で ACL を管理する Azure Network Acl Azure Ip based acls can be set up at different levels of a network from the network device to firewalls. Selectively permit or deny incoming traffic based on remote subnet ipv4 address. In this article, i will walk you through the process of setting azure storage account acls recursively using three different methods: Network acls can be configured to restrict access.. Network Acl Azure.