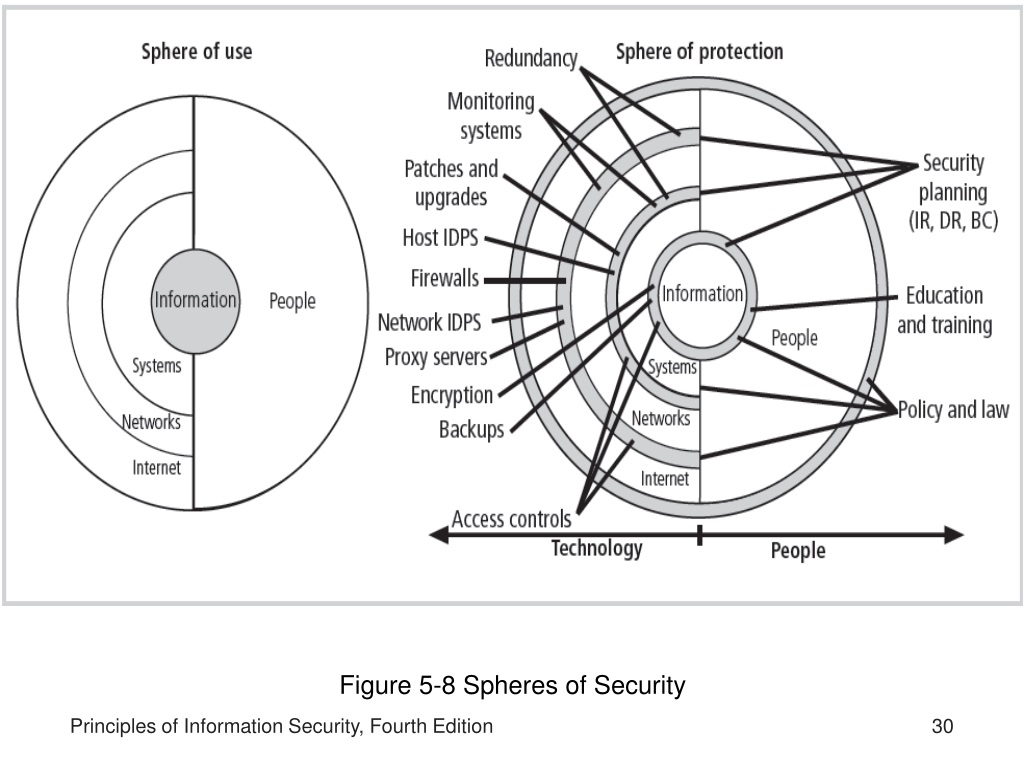
Sphere Of Protection Information Security . Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Understanding the spheres of information security is crucial for developing a comprehensive.
from www.slideserve.com
Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Understanding the spheres of information security is crucial for developing a comprehensive.
PPT Principles of Information Security, Fourth Edition PowerPoint
Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Understanding the spheres of information security is crucial for developing a comprehensive. A broad, integrated, and automated.
From www.researchgate.net
Model of the enterprise "sphere of security" Download Scientific Diagram Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding attack surface, increasingly sophisticated threats,. Sphere Of Protection Information Security.
From www.alamy.com
Cyber lock global sphere with shield design of Security password Sphere Of Protection Information Security Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. A broad, integrated, and automated. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.vecteezy.com
Cyber security. Information protect and or safe concept. Abstract 3D Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. A broad, integrated, and automated. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.pinterest.co.uk
GDPR awareness poster Awareness poster, College awareness, Awareness Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding attack surface, increasingly sophisticated threats,. Sphere Of Protection Information Security.
From www.slideserve.com
PPT Principles of Information Security, Fourth Edition PowerPoint Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.freepik.com
Premium Vector Security privacy safe glowing sphere of hexagon and Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Understanding the spheres of information security is crucial for developing a comprehensive. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality,. Sphere Of Protection Information Security.
From cartoondealer.com
Security Privacy Safe. Glowing Sphere Of Hexagon And Globe. High Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Understanding. Sphere Of Protection Information Security.
From www.ingenious.news
You Need Multiple Layers of Security Technology news to help Sphere Of Protection Information Security Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. A broad, integrated, and automated. Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection. Sphere Of Protection Information Security.
From www.slideserve.com
PPT Understanding Residential Safety and Security August 19, 2010 Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. A broad, integrated, and automated. Firewalls, intrusion detection. Sphere Of Protection Information Security.
From www.vecteezy.com
Cyber security. Information protect and or safe concept. Abstract 3D Sphere Of Protection Information Security A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection. Sphere Of Protection Information Security.
From www.sketchbubble.com
7 Layers of Security PowerPoint and Google Slides Template PPT Slides Sphere Of Protection Information Security Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Understanding the spheres of information security is crucial for developing a comprehensive. A broad, integrated, and automated. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.freepik.com
Premium Vector Polygon background security privacy safe glowing Sphere Of Protection Information Security Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. A broad, integrated, and automated. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection. Sphere Of Protection Information Security.
From www.bitdefender.com
What is Data Encryption? Bitdefender Cyberpedia Sphere Of Protection Information Security Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Understanding the spheres of information security. Sphere Of Protection Information Security.
From www.freepik.com
Premium Vector Cyber security technology concept in the shape of Sphere Of Protection Information Security Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Understanding. Sphere Of Protection Information Security.
From www.plixer.com
Layered security approach (is only as good as ….) Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding. Sphere Of Protection Information Security.
From ldra.com
Digital Battlefield Strategy to a Failproof Solution LDRA Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. A broad, integrated, and automated. Understanding the spheres of information security is crucial for developing a comprehensive. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security. Sphere Of Protection Information Security.
From www.alamy.com
Artificial intelligence of security privacy safe. Robot finger touch on Sphere Of Protection Information Security A broad, integrated, and automated. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security. Sphere Of Protection Information Security.
From cartoondealer.com
Security Privacy Safe. Glowing Sphere Of Hexagon And Globe. High Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. A broad, integrated, and automated. Understanding the spheres of information security is crucial for developing a comprehensive. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.alamy.com
Robot hand sphere Stock Vector Images Alamy Sphere Of Protection Information Security A broad, integrated, and automated. Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security. Sphere Of Protection Information Security.
From www.dreamstime.com
Abstract Polygonal Light Design of Monitor Protection Shield Stock Sphere Of Protection Information Security Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Understanding the spheres of information security is crucial for developing a comprehensive. A broad, integrated, and automated. Firewalls, intrusion detection. Sphere Of Protection Information Security.
From cartoondealer.com
Security Privacy Safe. Glowing Sphere Of Hexagon And Globe. High Sphere Of Protection Information Security Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection. Sphere Of Protection Information Security.
From www.vecteezy.com
3D vector illustration of a blue neon sphere with a poly structure Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Understanding the spheres of information security is crucial for developing a comprehensive. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality,. Sphere Of Protection Information Security.
From martinamurawski.blogspot.com
Martina Murawski's INFOSEC Blog Site Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. A broad, integrated, and automated. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Understanding. Sphere Of Protection Information Security.
From www.slideserve.com
PPT Management of Information Security Chapter 9 Protection Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. A broad, integrated, and automated. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.askbts.com
Cyber Security for Business / Medical, HIPAA, NIST Framework Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Understanding the spheres of information security is crucial for developing a comprehensive. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality,. Sphere Of Protection Information Security.
From www.slideserve.com
PPT CMPS 319 Blueprint For Security Chapter 6 PowerPoint Presentation Sphere Of Protection Information Security A broad, integrated, and automated. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Understanding. Sphere Of Protection Information Security.
From www.dreamstime.com
Earth Sphere and Cybersecurity Shield with Padlock, Protection Stock Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Firewalls, intrusion detection systems, malware scanners, integrity auditing. Sphere Of Protection Information Security.
From www.sketchbubble.com
Cyber Security Layers PowerPoint Template PPT Slides Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security. Sphere Of Protection Information Security.
From www.dreamstime.com
Cyber Security Protection Information Privacy Technology Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.slideserve.com
PPT CMPS 319 Blueprint For Security Chapter 6 PowerPoint Presentation Sphere Of Protection Information Security A broad, integrated, and automated. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Understanding the spheres of information security is crucial for developing a comprehensive. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.freepik.com
Premium Vector Data protection Personal data security Abstract 3D Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Firewalls, intrusion detection. Sphere Of Protection Information Security.
From www.safic.co.za
The Zones of Protection Sphere Of Protection Information Security Understanding the spheres of information security is crucial for developing a comprehensive. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Cisos today face an expanding. Sphere Of Protection Information Security.
From www.coursehero.com
[Solved] explain sphere of security, sphere of use and sphere of Sphere Of Protection Information Security Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. A broad, integrated, and automated. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality, integrity and availability of an organization’s. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Understanding. Sphere Of Protection Information Security.
From www.vecteezy.com
Cyber security. Information protect and or safe concept. Abstract 3D Sphere Of Protection Information Security Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Understanding the spheres of information security is crucial for developing a comprehensive. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security to holistically protect the confidentiality,. Sphere Of Protection Information Security.
From www.microsoft.com
IoT security will set innovation free Azure Sphere general Sphere Of Protection Information Security A broad, integrated, and automated. Understanding the spheres of information security is crucial for developing a comprehensive. Cisos today face an expanding attack surface, increasingly sophisticated threats, and an ongoing cybersecurity skills gap. Firewalls, intrusion detection systems, malware scanners, integrity auditing procedures, and local storage encryption tools. Defense in depth is a cybersecurity strategy that utilizes multiple layers of security. Sphere Of Protection Information Security.