Rest Endpoint Login . The api provider checks the credentials and, in the case. For a rest api endpoint, you would not have a typical login form sent from the server. Find out how to use aws services like aws. You would collect the credentials from a form. You can utilize all of the login. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. Optionally, you can include a connection parameter to log in with a specific provider. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. Use this endpoint to accept a saml request to initiate a login. To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. If no connection is specified, the. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example.
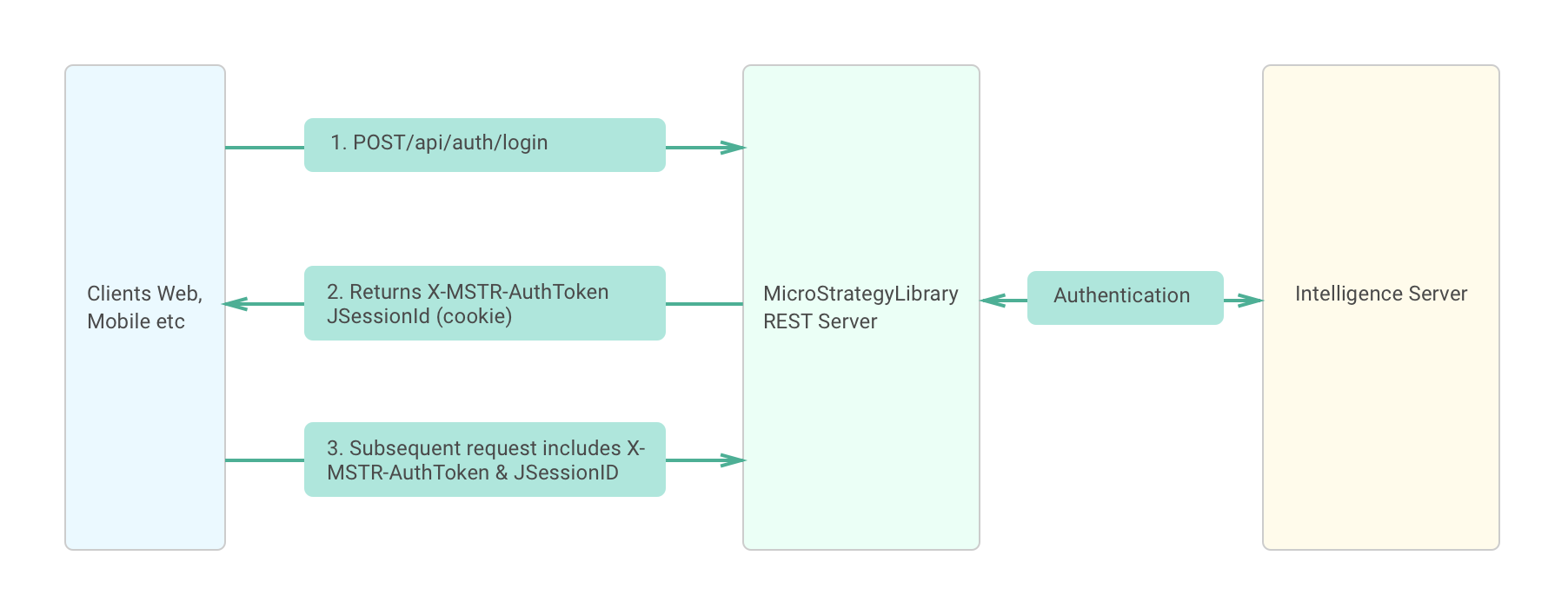
from microstrategy.github.io
To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. If no connection is specified, the. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. Optionally, you can include a connection parameter to log in with a specific provider. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. You would collect the credentials from a form. Find out how to use aws services like aws. The api provider checks the credentials and, in the case. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example.
Authentication REST API Docs
Rest Endpoint Login Use this endpoint to accept a saml request to initiate a login. For a rest api endpoint, you would not have a typical login form sent from the server. Optionally, you can include a connection parameter to log in with a specific provider. You would collect the credentials from a form. Find out how to use aws services like aws. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. You can utilize all of the login. If no connection is specified, the. The api provider checks the credentials and, in the case. Use this endpoint to accept a saml request to initiate a login. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example. To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request.
From livebook.manning.com
11 Consuming REST endpoints · Spring Start Here Rest Endpoint Login Use this endpoint to accept a saml request to initiate a login. You would collect the credentials from a form. The api provider checks the credentials and, in the case. You can utilize all of the login. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. In this article, we’ll cover one very powerful. Rest Endpoint Login.
From www.altexsoft.com
What is a REST API? Beginner's Guide AltexSoft Rest Endpoint Login To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. Find out how to use aws services like aws. Optionally, you can include a connection parameter to log in with a specific provider. You would collect the credentials from a form. You can utilize all of. Rest Endpoint Login.
From www.youtube.com
REST Endpoint API Walkthru YouTube Rest Endpoint Login For a rest api endpoint, you would not have a typical login form sent from the server. Use this endpoint to accept a saml request to initiate a login. The api provider checks the credentials and, in the case. You would collect the credentials from a form. Learn how to secure your rest api with tls, oauth2, openid connect, and. Rest Endpoint Login.
From www.youtube.com
Flutter Let's integrate login Rest API endpoint with GetX GetX controller Shopping App Rest Endpoint Login Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. You can utilize all of the login. For a rest. Rest Endpoint Login.
From www.ibm.com
Defining the REST service endpoints Rest Endpoint Login You can utilize all of the login. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination,. Rest Endpoint Login.
From hub.alfresco.com
Using REST call with a Start Signal Event in APS Alfresco Hub Rest Endpoint Login You would collect the credentials from a form. Use this endpoint to accept a saml request to initiate a login. Find out how to use aws services like aws. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. You can utilize all of the login. To access the api endpoint, the user must send a username and password. Rest Endpoint Login.
From marketplace.atlassian.com
BaseURL REST endpoint Atlassian Marketplace Rest Endpoint Login Shiro basically gives you a servlet filter purposed for authentication as well as authorization. For a rest api endpoint, you would not have a typical login form sent from the server. To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. Optionally, you can include a. Rest Endpoint Login.
From github.com
Social login for rest endpoints users · directus directus · Discussion 10384 · GitHub Rest Endpoint Login To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. Find out how to use aws services like aws. The api provider checks the credentials and, in the case. You can utilize. Rest Endpoint Login.
From medium.com
REST API for User Management in Authentication Server for Single SignOn Geek Culture Rest Endpoint Login Find out how to use aws services like aws. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. Optionally, you can include a connection parameter to log in with a specific provider. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. Use this endpoint to accept a saml request to initiate a login.. Rest Endpoint Login.
From www.youtube.com
06 Create a simple REST endpoint to understand the basics YouTube Rest Endpoint Login Find out how to use aws services like aws. Optionally, you can include a connection parameter to log in with a specific provider. You would collect the credentials from a form. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example.. Rest Endpoint Login.
From help.victorops.com
VictorOps REST Endpoint Knowledge Base Rest Endpoint Login You would collect the credentials from a form. For a rest api endpoint, you would not have a typical login form sent from the server. You can utilize all of the login. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. Learn how to secure your rest api with tls, oauth2, openid connect, and api. Rest Endpoint Login.
From www.mfpdocumentsecurity.com
Using the REST Endpoint Manager Rest Endpoint Login If no connection is specified, the. You would collect the credentials from a form. The api provider checks the credentials and, in the case. Find out how to use aws services like aws. For a rest api endpoint, you would not have a typical login form sent from the server. Learn how to secure your rest api with tls, oauth2,. Rest Endpoint Login.
From securityboulevard.com
Common REST API Authentication Methods Explained Security Boulevard Rest Endpoint Login You would collect the credentials from a form. Find out how to use aws services like aws. For a rest api endpoint, you would not have a typical login form sent from the server. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. Rest Endpoint Login.
From medium.com
Secure REST endpoint using Spring Security 5.x and JWT by nidhinbenjamin Medium Rest Endpoint Login Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. Find out how to use aws services like aws. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. You can utilize all of the login. To access the api endpoint, the user must send a username and password to the api provider in the. Rest Endpoint Login.
From help.rollworks.com
Find Your Marketo REST API Endpoint RollWorks Rest Endpoint Login Optionally, you can include a connection parameter to log in with a specific provider. For a rest api endpoint, you would not have a typical login form sent from the server. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example.. Rest Endpoint Login.
From www.ibm.com
Defining the REST service endpoints Rest Endpoint Login Find out how to use aws services like aws. The api provider checks the credentials and, in the case. To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. In this article, we’ll cover one very powerful yet simple way to secure a rest api using. Rest Endpoint Login.
From www.kingswaysoft.com
How to Work with RESTful Endpoints in your SSIS ETL Process Rest Endpoint Login Use this endpoint to accept a saml request to initiate a login. For a rest api endpoint, you would not have a typical login form sent from the server. If no connection is specified, the. The api provider checks the credentials and, in the case. To access the api endpoint, the user must send a username and password to the. Rest Endpoint Login.
From apps.splunk.com
REST Endpoint Examples Splunkbase Rest Endpoint Login Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example. Find out how to use aws services like aws. If no connection is specified, the. To access the api endpoint,. Rest Endpoint Login.
From www.workato.com
Introducing Workato's Callable Recipes and REST API Connector The Connector by Workato Rest Endpoint Login To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. The api provider checks the credentials and, in the case. Optionally, you can include a connection parameter to log in with a specific provider. In this article, we’ll cover one very powerful yet simple way to. Rest Endpoint Login.
From docs.streambase.com
REST API Rest Endpoint Login To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. If no connection is specified, the. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. Find out how to use aws services like aws. In this article, we’ll cover one very powerful yet simple. Rest Endpoint Login.
From blog.karmacomputing.co.uk
Drupal 8 REST Endpoint With Entity Reference Field Set To Unlimited Using Views Rest Endpoint Login Shiro basically gives you a servlet filter purposed for authentication as well as authorization. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. Use this endpoint to accept a saml request to initiate a login. Find out how to use aws services like aws. To access the api endpoint, the user must send a username and password to. Rest Endpoint Login.
From swatipoint.blogspot.com
SharePoint..... How to access REST Endpoint In SharePoint App in SharePoint Online? Rest Endpoint Login Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. Optionally, you can include a connection parameter to log in with a specific provider. For a rest api endpoint, you would not have a typical login form sent from the server. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. Use this endpoint to. Rest Endpoint Login.
From www.prisma.io
Building a REST API with NestJS and Prisma Authentication Rest Endpoint Login You would collect the credentials from a form. The api provider checks the credentials and, in the case. If no connection is specified, the. You can utilize all of the login. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. Find out how to use aws services like aws. Follow the guidelines for json,. Rest Endpoint Login.
From www.answeroverflow.com
JWT return Dto. Login and Register REST Endpoints Java Community Help. Code. Learn. Rest Endpoint Login Use this endpoint to accept a saml request to initiate a login. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. For a rest api endpoint, you would not have a. Rest Endpoint Login.
From www.freecodecamp.org
REST API Best Practices REST Endpoint Design Examples Rest Endpoint Login In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example. Find out how to use aws services like aws. If no connection is specified, the. Use this endpoint to accept a saml request to initiate a login. For a rest api. Rest Endpoint Login.
From www.algorithmicworldautomation.com
How to use a REST API Algorithmic World Automation Rest Endpoint Login Optionally, you can include a connection parameter to log in with a specific provider. To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. For a rest api endpoint, you would not have a typical. Rest Endpoint Login.
From wordpress.org
Simple JWT Login Allows you to use JWT on REST endpoints. WordPress plugin Rest Endpoint Login Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. To access the api endpoint, the user must send a username and password to the api provider in the authentication header of the request. Optionally, you can include a connection parameter to log in with a specific provider. The api provider checks the credentials and, in the case. In. Rest Endpoint Login.
From www.youtube.com
Secure REST Endpoints with Keycloak and Spring Method Security YouTube Rest Endpoint Login In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example. You would collect the credentials from a form. Find out how to use aws services like aws. To access the api endpoint, the user must send a username and password to. Rest Endpoint Login.
From www.youtube.com
Creating a REST endpoint in Hasura YouTube Rest Endpoint Login Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. Use this endpoint to accept a saml request to initiate a login. For a rest api endpoint, you would not have a typical login form sent from the server. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. To access. Rest Endpoint Login.
From support.smartbear.com
REST APIs ReadyAPI Documentation Rest Endpoint Login In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example. Optionally, you can include a connection parameter to log in with a specific provider. Shiro basically gives you a servlet filter purposed for authentication as well as authorization. Follow the guidelines. Rest Endpoint Login.
From docs.incountry.com
Managing REST endpoints InCountry Docs Rest Endpoint Login For a rest api endpoint, you would not have a typical login form sent from the server. You can utilize all of the login. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. To access the api endpoint, the user must send a username and password to the api provider in the authentication header. Rest Endpoint Login.
From arrify.com
Salesforce REST API Endpoints The Key to Unlocking Integration Success Arrify Rest Endpoint Login You would collect the credentials from a form. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. Follow the guidelines for json, nouns, errors, filtering, sorting, pagination, caching,. The api provider checks the credentials and, in the case. For a rest api endpoint, you would not have a typical login form sent from the. Rest Endpoint Login.
From devblogs.microsoft.com
REST Endpoint Invocation is now Generally Available Azure SQL Devs’ Corner Rest Endpoint Login You would collect the credentials from a form. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example. The api provider checks the credentials and, in the case. To access the api endpoint, the user must send a username and password. Rest Endpoint Login.
From docs.incountry.com
Managing REST endpoints InCountry Docs Rest Endpoint Login Optionally, you can include a connection parameter to log in with a specific provider. For a rest api endpoint, you would not have a typical login form sent from the server. You would collect the credentials from a form. Learn how to secure your rest api with tls, oauth2, openid connect, and api keys. Use this endpoint to accept a. Rest Endpoint Login.
From microstrategy.github.io
Authentication REST API Docs Rest Endpoint Login If no connection is specified, the. Use this endpoint to accept a saml request to initiate a login. In this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and implementing an example. To access the api endpoint, the user must send a username and password. Rest Endpoint Login.