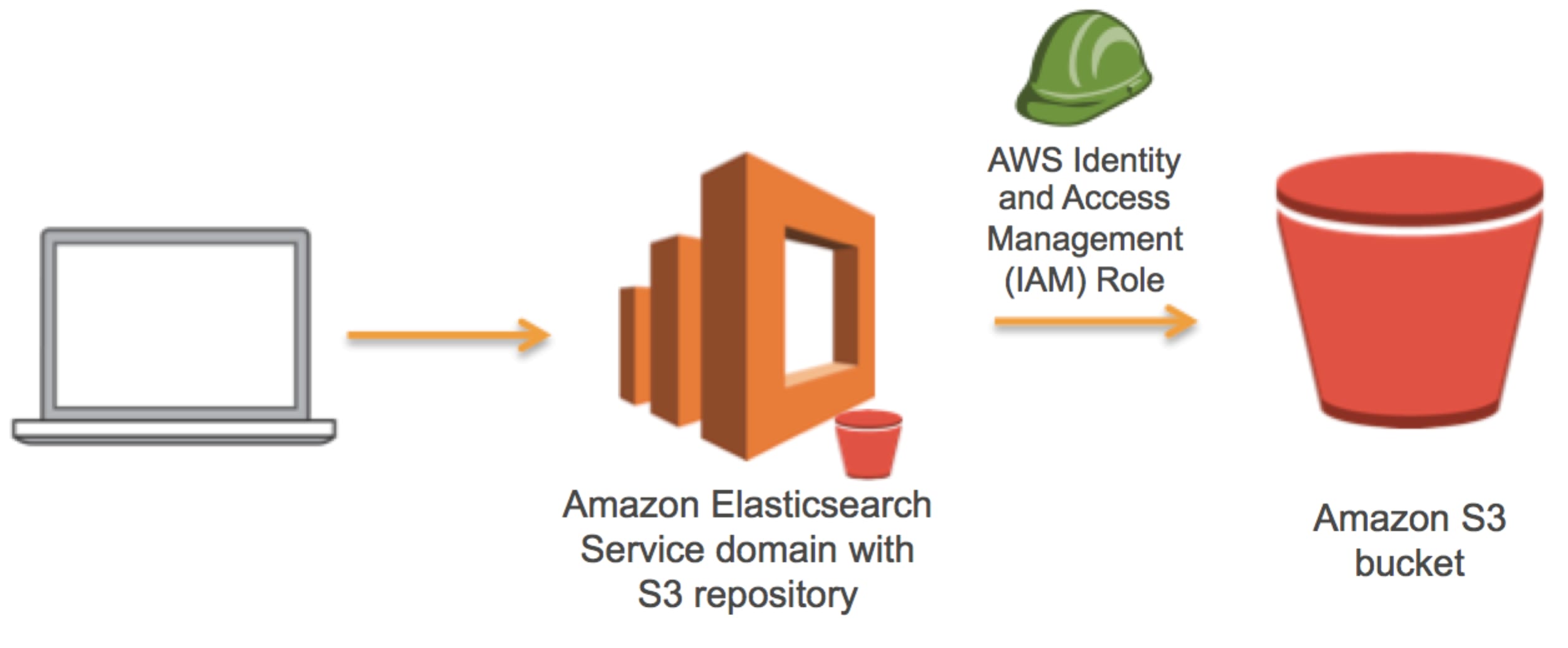
Limit S3 Bucket By Source Ip . to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all. if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,.
from hevodata.com
if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all.
Working with Amazon S3 Keys 3 Critical Aspects Learn Hevo
Limit S3 Bucket By Source Ip if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all.
From ip-slip.com
IP SLIP Over 100 Public AWS S3 Buckets Identified Limit S3 Bucket By Source Ip to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. if you want to allow servers in your network access to internal s3 buckets,. Limit S3 Bucket By Source Ip.
From medium.com
S3 Bucket Cross Account Resource Sharing with Encryption by Anupam Limit S3 Bucket By Source Ip recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. to prevent s3 data exposure, data loss, unexpected charges on your aws. Limit S3 Bucket By Source Ip.
From www.cloud-plusplus.com
Tutorial on AWS S3 bucket access to specific IP Limit S3 Bucket By Source Ip i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or. Limit S3 Bucket By Source Ip.
From docs.getcommandeer.com
Create S3 Bucket On AWS Commandeer Docs Limit S3 Bucket By Source Ip use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition. Limit S3 Bucket By Source Ip.
From itnext.io
Transfer terabytes of data between AWS s3 buckets crossaccount, cross Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict. Limit S3 Bucket By Source Ip.
From k21academy.com
Amazon S3 Bucket AWS S3 Storage Classes S3 Types Limit S3 Bucket By Source Ip i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip. Limit S3 Bucket By Source Ip.
From work.haufegroup.io
Configure Centralised S3 bucket replication from multiple S3 bucket Limit S3 Bucket By Source Ip you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. recently we were testing with aws vpc, and a requirement for our project was that we needed. Limit S3 Bucket By Source Ip.
From www.vrogue.co
How To Create An S3 Bucket On Aws Complete Guide vrogue.co Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. recently we were testing with aws vpc, and a requirement for our project was that we needed. Limit S3 Bucket By Source Ip.
From finleysmart.z13.web.core.windows.net
List Objects In S3 Bucket Aws Cli Limit S3 Bucket By Source Ip to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. i am trying this policy to allow users to put and list object access. Limit S3 Bucket By Source Ip.
From innovationm.co
S3 Bucket InnovationM Blog Limit S3 Bucket By Source Ip you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or. Limit S3 Bucket By Source Ip.
From www.manageengine.com
Amazon Simple Storage Service (S3) bucket logging Log management by Limit S3 Bucket By Source Ip if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all. to prevent s3 data exposure, data loss, unexpected charges on your. Limit S3 Bucket By Source Ip.
From exopcepsm.blob.core.windows.net
Aws S3 Bucket Replication Cdk at Bradley Knuth blog Limit S3 Bucket By Source Ip you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you. Limit S3 Bucket By Source Ip.
From aws.amazon.com
How to Use Bucket Policies and Apply DefenseinDepth to Help Secure Limit S3 Bucket By Source Ip use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. recently we were testing with aws vpc, and a requirement for our project was. Limit S3 Bucket By Source Ip.
From brandiscrafts.com
Aws S3 Bucket Limit? Top 11 Best Answers Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or. Limit S3 Bucket By Source Ip.
From work.haufegroup.io
Configure Centralised S3 bucket replication from multiple S3 bucket Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. recently we were testing with aws vpc, and a requirement for our project was that we. Limit S3 Bucket By Source Ip.
From cloudkatha.com
How to Create S3 Bucket Policy using Terraform CloudKatha Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. recently we were testing with aws vpc, and a requirement for our project was that we needed. Limit S3 Bucket By Source Ip.
From www.youtube.com
S3 Bucket Security like a PRO How to Restrict Amazon S3 Bucket Access Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. if you want to allow servers in your network access to internal s3 buckets, without making the. Limit S3 Bucket By Source Ip.
From blog.checkpoint.com
Automatically Remediate Publicly Exposed S3 Buckets Check Point Software Limit S3 Bucket By Source Ip use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict. Limit S3 Bucket By Source Ip.
From buddymantra.com
Amazon S3 Bucket Everything You Need to Know About Cloud Storage Limit S3 Bucket By Source Ip i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. if you want to allow servers in your network access to internal s3 buckets,. Limit S3 Bucket By Source Ip.
From lifesciences-resources.awscloud.com
Limit access to Amazon S3 buckets owned by specific AWS accounts Limit S3 Bucket By Source Ip if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. you can also create an amazon s3 bucket policy with the. Limit S3 Bucket By Source Ip.
From work.haufegroup.io
Configure Centralised S3 bucket replication from multiple S3 bucket Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want. Limit S3 Bucket By Source Ip.
From pprakash.me
Sync S3 bucket to multiple S3 buckets in different region Technology Limit S3 Bucket By Source Ip use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition. Limit S3 Bucket By Source Ip.
From work.haufegroup.io
Configure Centralised S3 bucket replication from multiple S3 bucket Limit S3 Bucket By Source Ip i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. recently we were testing with aws vpc, and a requirement for our project was that we. Limit S3 Bucket By Source Ip.
From aws.amazon.com
How to Use Bucket Policies and Apply DefenseinDepth to Help Secure Limit S3 Bucket By Source Ip you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. if you want to allow servers in your network access to internal s3 buckets,. Limit S3 Bucket By Source Ip.
From www.youtube.com
How to Create S3 Bucket in AWS Step by Step Tricknology YouTube Limit S3 Bucket By Source Ip use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. if you want to allow servers in your network access to internal s3 buckets,. Limit S3 Bucket By Source Ip.
From www.networkingsignal.com
What Is S3 Bucket In AWS And How To Create It? Limit S3 Bucket By Source Ip use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. i am trying this policy to allow users to put and list object access. Limit S3 Bucket By Source Ip.
From play.whizlabs.com
Lab Tasks Limit S3 Bucket By Source Ip use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip addresses can access the s3. if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. to prevent s3 data exposure, data loss, unexpected charges on your aws. Limit S3 Bucket By Source Ip.
From hevodata.com
Working with Amazon S3 Keys 3 Critical Aspects Learn Hevo Limit S3 Bucket By Source Ip to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. recently we were testing with aws vpc, and a requirement for our project was. Limit S3 Bucket By Source Ip.
From www.cloud-plusplus.com
Tutorial on AWS S3 bucket access to specific IP Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. i am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip. Limit S3 Bucket By Source Ip.
From www.geeksforgeeks.org
How To Store Data in a S3 Bucket? Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. recently we were testing with aws vpc, and a requirement for our project was. Limit S3 Bucket By Source Ip.
From www.cloud-plusplus.com
Tutorial on AWS S3 bucket access to specific IP Limit S3 Bucket By Source Ip you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. you can control which vpcs or vpc endpoints have access to your buckets by using. Limit S3 Bucket By Source Ip.
From www.geeksforgeeks.org
Amazon S3 Creating a S3 Bucket Limit S3 Bucket By Source Ip if you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet,. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition. Limit S3 Bucket By Source Ip.
From cloudkatha.com
How to Create S3 Bucket in AWS Step by Step CloudKatha Limit S3 Bucket By Source Ip you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. recently we were testing with aws vpc, and a requirement for our project was that we needed to allow nodes within. i am trying this policy to allow users to put and list object access with a particular. Limit S3 Bucket By Source Ip.
From manuals.supernaeyeglass.com
S3 Storage Bucket Configurations Options , Operations and Settings Limit S3 Bucket By Source Ip to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. you can control which vpcs or vpc endpoints have access to your buckets by using amazon s3 bucket policies. use a bucket policy to specify which vpc endpoints, vpc source ip addresses, or external ip. Limit S3 Bucket By Source Ip.
From blogs.perficient.com
How To Use The AWS API With S3 Buckets In Your Pen Test Perficient Blogs Limit S3 Bucket By Source Ip to prevent s3 data exposure, data loss, unexpected charges on your aws bill or you just want a central place to manage. you can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from. if you want to allow servers in your network access to internal s3 buckets,. Limit S3 Bucket By Source Ip.