Simulated Attack Meaning . It allows you to simulate. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. What is breach and attack simulation? An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. The goal is to test the effectiveness of. At a high level, security teams employ this approach to execute simulated attacks. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the.
from www.csoonline.com
Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. The goal is to test the effectiveness of. At a high level, security teams employ this approach to execute simulated attacks. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. What is breach and attack simulation? It allows you to simulate.
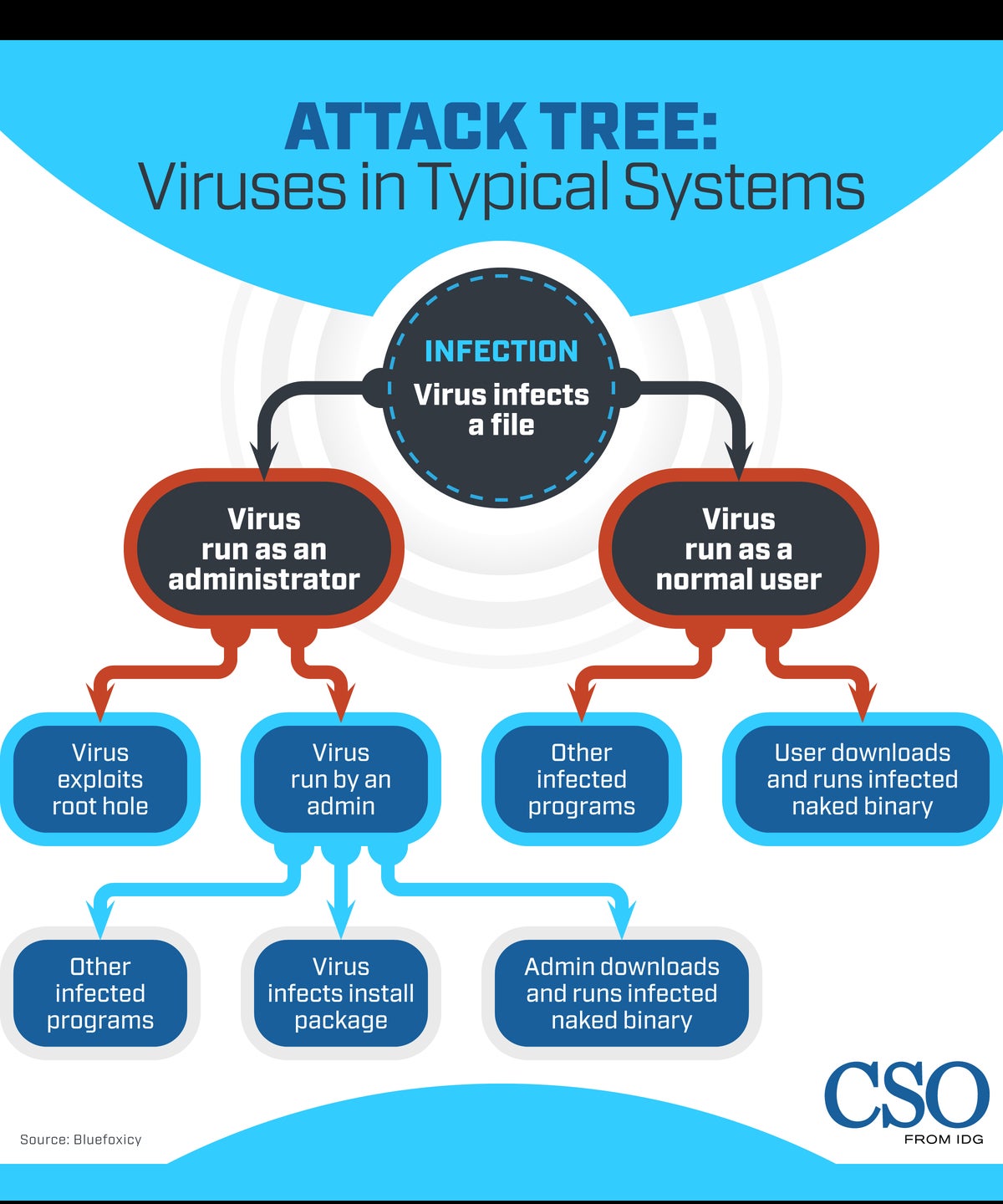
Threat modeling explained A process for anticipating cyber attacks
Simulated Attack Meaning Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. The goal is to test the effectiveness of. It allows you to simulate. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. At a high level, security teams employ this approach to execute simulated attacks. What is breach and attack simulation?
From www.semanticscholar.org
Figure 1 from Simulated Attack on DNP3 Protocol in SCADA System Simulated Attack Meaning Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. Breach and attack simulation. Simulated Attack Meaning.
From www.vrogue.co
Types Of Attacks Or Security Attacks Techblogmu vrogue.co Simulated Attack Meaning Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. At a high level, security teams employ this approach to execute simulated attacks. What is breach and attack simulation? Breach and attack simulation (bas). Simulated Attack Meaning.
From www.cyberthreatinsight.com
Threat Simulation Cyber Threat Insight Simulated Attack Meaning At a high level, security teams employ this approach to execute simulated attacks. What is breach and attack simulation? Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. Penetration testing is a process. Simulated Attack Meaning.
From rainyweathers.com
Types Of Attacks In Cyber Security Powerpoint Slides Diagrams Rainy Simulated Attack Meaning An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. At a high level, security teams employ this approach to execute simulated attacks. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. Breach and attack simulation (bas). Simulated Attack Meaning.
From www.cyberghostvpn.com
How to Stop Replay Attacks Forever Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. The goal is to test the effectiveness of. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the. Simulated Attack Meaning.
From kaffec.com
What is Tailgating in Cyber Security? [A Simple Definition & Examples Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems. Simulated Attack Meaning.
From www.youtube.com
Microsoft Attack Simulator Training YouTube Simulated Attack Meaning It allows you to simulate. At a high level, security teams employ this approach to execute simulated attacks. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Learn about the breach and. Simulated Attack Meaning.
From o365reports.com
Train Your Office 365 Users Against Phishing Attacks using Attack Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. What is breach and attack simulation? An attack simulation is a cybersecurity practice that mimics the behavior. Simulated Attack Meaning.
From www.assentriskmanagement.co.uk
Simulated Phishing Attack Check Awareness with a Test Phishing Email. Simulated Attack Meaning The goal is to test the effectiveness of. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. At a high level, security teams employ this approach to execute simulated attacks. It allows you to simulate. An attack simulation is a cybersecurity practice that mimics the behavior of hackers. Simulated Attack Meaning.
From www.studypool.com
SOLUTION Defending the network from a simulated attack 3e paras Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. The goal is to test the effectiveness of. Breach and attack simulation (bas) is an innovative approach to testing. Simulated Attack Meaning.
From 4sysops.com
Understanding Microsoft 365 Attack simulation training 4sysops Simulated Attack Meaning Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. At a high level, security teams employ this approach to execute simulated attacks. What is breach and attack simulation? It allows you to simulate. Breach and attack simulation (bas) is an innovative approach to testing the resilience of. Simulated Attack Meaning.
From cybermate.com.au
Cybermate Cyber Security Solutions & Training For SMEs Simulated Attack Meaning An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. What is breach and attack simulation? At a high level, security teams employ this approach to execute simulated attacks. Penetration. Simulated Attack Meaning.
From www.mdpi.com
Sustainability Free FullText ReplayAttack Detection and Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. It allows you. Simulated Attack Meaning.
From www.valimail.com
Complete Guide to Phishing Techniques & Mitigations Valimail Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. The goal is to test the effectiveness of. An attack simulation is a cybersecurity practice that mimics. Simulated Attack Meaning.
From www.dig8labs.com
Breach and Attack Simulation Digit Labs Simulated Attack Meaning At a high level, security teams employ this approach to execute simulated attacks. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. It allows you to simulate. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities.. Simulated Attack Meaning.
From www.sectigo.com
How A DDoS Attack Works And How To Prevent Them Sectigo® Official Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. The goal is to test the effectiveness of. What is breach and attack simulation? Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. It allows you to simulate. Learn about the breach. Simulated Attack Meaning.
From www.netwrix.com
Improve Cyberattack Detection and Response with Netwrix Solutions Simulated Attack Meaning Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. It allows you to simulate. Penetration testing is a process in which a security professional simulates an attack on a network or. Simulated Attack Meaning.
From knowledge.rtds.com
Realtime Simulation for Cybersecurity RTDS Technologies Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. What is breach and attack simulation? An attack simulation is a cybersecurity practice that mimics the behavior. Simulated Attack Meaning.
From www.csoonline.com
Threat modeling explained A process for anticipating cyber attacks Simulated Attack Meaning An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security. Simulated Attack Meaning.
From www.researchgate.net
Phases I and II of the reconstructed and simulated attack Danes and Simulated Attack Meaning It allows you to simulate. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. What is breach and attack simulation? Penetration testing is a process in which a security. Simulated Attack Meaning.
From www.globalsign.com
What is DDoS Attack and How to Prevent It? Simulated Attack Meaning Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. What is breach and attack simulation? At a high level, security teams employ this approach to execute simulated. Simulated Attack Meaning.
From www.techquityindia.com
Chrome Under Attack? On ZeroDay Vulnerabilities Simulated Attack Meaning Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. It allows you to simulate. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's. Simulated Attack Meaning.
From www.cybsafe.com
Some simulated attacks help reduce cyber risk. Others don't. CybSafe Simulated Attack Meaning An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. What is breach and attack simulation? It allows you to simulate. Breach and attack simulation (bas) is the process. Simulated Attack Meaning.
From risk3sixty.com
inar Pentest Engagement Types A Guide to Understanding Simulated Simulated Attack Meaning The goal is to test the effectiveness of. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance. Simulated Attack Meaning.
From www.wikitechy.com
Handling a Cyber Attack How to handle a Cyber Attack Cyber Security Simulated Attack Meaning An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. What is breach and attack simulation? Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. Penetration testing is a process in which a security professional simulates an attack on a network or computer. Simulated Attack Meaning.
From www.cdn5.com
what is a ddos attack and how does it work? Simulated Attack Meaning Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. The goal. Simulated Attack Meaning.
From mavink.com
Phishing Attack Diagram Simulated Attack Meaning What is breach and attack simulation? An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. The goal is to test the effectiveness of. It allows you to simulate. Breach. Simulated Attack Meaning.
From www.studypool.com
SOLUTION Defending the network from a simulated attack 3e paras Simulated Attack Meaning Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. What is breach. Simulated Attack Meaning.
From sosafe-awareness.com
What is a DDoS Attack? Examples & Prevention Tips Simulated Attack Meaning Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. At a high level, security teams employ this approach to execute simulated attacks. It allows you to simulate. Penetration testing is a process in. Simulated Attack Meaning.
From www.studypool.com
SOLUTION Defending the network from a simulated attack 3e paras Simulated Attack Meaning It allows you to simulate. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. What is breach and attack simulation? At a high level, security teams employ this approach to execute simulated attacks. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance. Simulated Attack Meaning.
From www.researchgate.net
Examples of Very High impact, cyber and cyberphysical attack path Simulated Attack Meaning At a high level, security teams employ this approach to execute simulated attacks. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. The goal is to test the effectiveness of. Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to. Simulated Attack Meaning.
From www.insightsonindia.com
Meaning and Types of Cybersecurity Threats INSIGHTS IAS Simplifying Simulated Attack Meaning An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. It allows you to simulate. What is breach and attack simulation? Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. The goal is to test the effectiveness of.. Simulated Attack Meaning.
From www.researchgate.net
The types of simulated attacks Download Scientific Diagram Simulated Attack Meaning Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in. Simulated Attack Meaning.
From www.informationntechnology.com
What are the Types of Phishing Attacks and How to Protect ourselves? Simulated Attack Meaning Learn about the breach and attack simulation (bas) technique that simulates cyber attacks on the organization's systems to identify vulnerabilities. At a high level, security teams employ this approach to execute simulated attacks. Breach and attack simulation (bas) is the process of a security operations center (soc) maintaining vigilance over the security posture of the. What is breach and attack. Simulated Attack Meaning.
From www.picussecurity.com
What Is an Attack Simulation? Simulated Attack Meaning An attack simulation is a cybersecurity practice that mimics the behavior of hackers to identify vulnerabilities in an organization's system. Breach and attack simulation (bas) is an innovative approach to testing the resilience of company networks. Penetration testing is a process in which a security professional simulates an attack on a network or computer system to evaluate. It allows you. Simulated Attack Meaning.