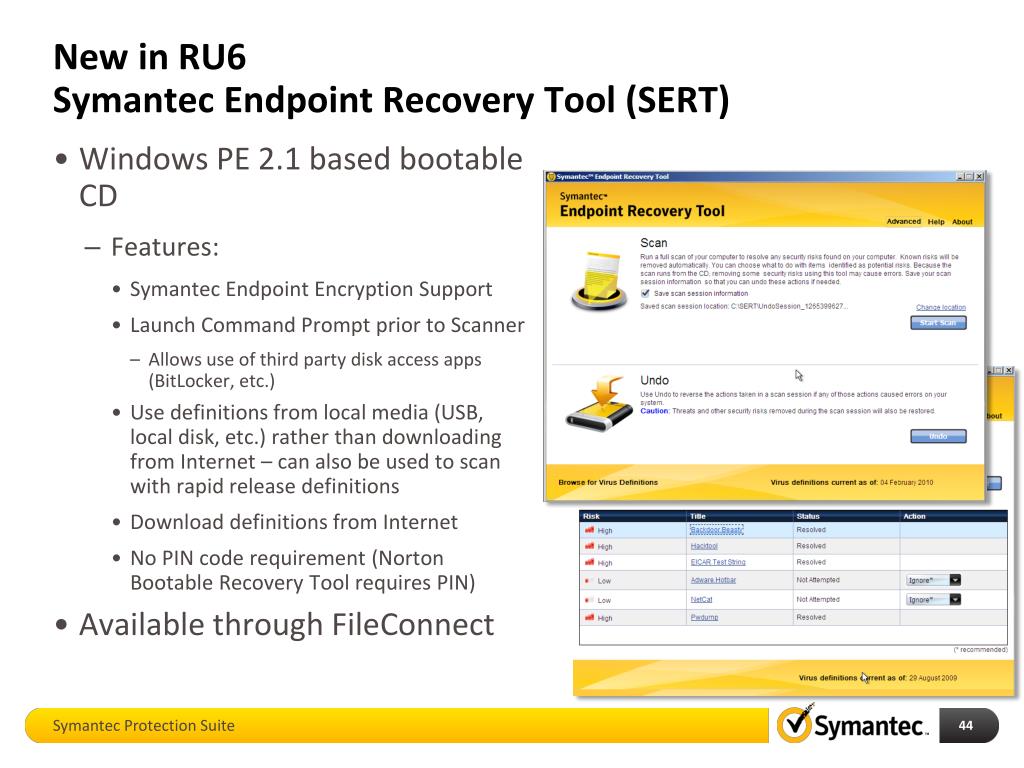
Safe Endpoint Recovery . The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. The backup systems should also. 57% of attacks are missed by traditional antivirus solutions. 69% spend more time managing tools than defending against the threats. Get back to business quickly. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. Time is of the essence. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with.
from www.slideserve.com
Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. Get back to business quickly. 57% of attacks are missed by traditional antivirus solutions. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. 69% spend more time managing tools than defending against the threats. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. The backup systems should also. Time is of the essence. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged.
PPT Symantec Endpoint Protection Technical Review PowerPoint
Safe Endpoint Recovery The backup systems should also. Get back to business quickly. Time is of the essence. 69% spend more time managing tools than defending against the threats. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. The backup systems should also. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. 57% of attacks are missed by traditional antivirus solutions. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with.
From techbast.com
Harmony Endpoint Recovery Full Disk Encryption Techbast Safe Endpoint Recovery Time is of the essence. 69% spend more time managing tools than defending against the threats. The backup systems should also. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. Get back to business quickly. 57% of attacks are missed by traditional antivirus solutions. The new release includes. Safe Endpoint Recovery.
From safe.yotta.com
ENDPOINT BACKUP AND RECOVERY Archives yottasafe Safe Endpoint Recovery The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. Time is of the essence. 69% spend more time managing tools than defending against the threats. Get back to business quickly. The key package and password will help decrypt. Safe Endpoint Recovery.
From spochub.com
The Complete Guide to Endpoint Backup Solutions and Why They are Vital Safe Endpoint Recovery The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. Time is of the essence. 69% spend more time managing tools than defending against the threats. Protect your critical business data against ransomware attacks on laptop and desktops, theft. Safe Endpoint Recovery.
From support.eset.com
[KB7894] ESET Endpoint Encryption recovery utility diagnostics Safe Endpoint Recovery Time is of the essence. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. The backup systems should also. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. Secure valuable endpoint data to keep your users safe and compliant,. Safe Endpoint Recovery.
From support.eset.com
[KB7894] ESET Endpoint Encryption recovery utility diagnostics Safe Endpoint Recovery 57% of attacks are missed by traditional antivirus solutions. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. The backup systems should also. Time is of the. Safe Endpoint Recovery.
From support.eset.com
[KB7894] ESET Endpoint Encryption recovery utility diagnostics Safe Endpoint Recovery 69% spend more time managing tools than defending against the threats. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. 57% of attacks are missed by traditional antivirus solutions. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of. Safe Endpoint Recovery.
From 4sysops.com
Free backup software for Windows Veeam Endpoint Backup 4sysops Safe Endpoint Recovery The backup systems should also. Time is of the essence. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. Get back to business quickly. 57% of attacks are missed by traditional antivirus solutions. The key package and password. Safe Endpoint Recovery.
From www.aegis.com.my
Endpoint Backup Saves Businesses Aegis Cloud Endpoint Backup Safe Endpoint Recovery Get back to business quickly. 69% spend more time managing tools than defending against the threats. The backup systems should also. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged.. Safe Endpoint Recovery.
From www.jagoanhosting.com
Lisensi Acronis untuk Backup Server Mudah & Praktis Safe Endpoint Recovery Get back to business quickly. The backup systems should also. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit. Safe Endpoint Recovery.
From techvids.sophos.com
Central Endpoint Recover Tamper Protected Windows Devices Sophos Safe Endpoint Recovery 69% spend more time managing tools than defending against the threats. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. Time is of the essence. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. Get back to business quickly.. Safe Endpoint Recovery.
From securuscomms.co.uk
Endpoint Protection and Why You Need it Safe Endpoint Recovery Get back to business quickly. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. Time is of the essence. 57% of attacks are missed by traditional antivirus solutions. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data. Safe Endpoint Recovery.
From www.gecomputers.com
Top 5 best file recovery software for 2022 GreenEdge Computers Safe Endpoint Recovery 57% of attacks are missed by traditional antivirus solutions. 69% spend more time managing tools than defending against the threats. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. The backup systems should also. The key package and. Safe Endpoint Recovery.
From metallic.io
Endpoint Backup & Recovery Metallic Safe Endpoint Recovery The backup systems should also. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. 57% of attacks are missed by traditional antivirus solutions. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery. Safe Endpoint Recovery.
From www.slideserve.com
PPT Symantec Endpoint Protection Technical Review PowerPoint Safe Endpoint Recovery Time is of the essence. The backup systems should also. 57% of attacks are missed by traditional antivirus solutions. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data. Safe Endpoint Recovery.
From learn.microsoft.com
Azure Backup のプライベート エンドポイントの作成と使用 Azure Backup Microsoft Learn Safe Endpoint Recovery The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. The backup systems should also. Time is of the essence. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. 57% of attacks are missed by traditional antivirus solutions. The new. Safe Endpoint Recovery.
From disaster-recovery.com.au
Endpoint Protection Disaster Recovery Safe Endpoint Recovery Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. Time is of the essence. 57% of attacks are missed by traditional antivirus solutions. 69% spend more time managing tools than defending against the threats. The new release includes a new option for recovery using safe boot, the option. Safe Endpoint Recovery.
From alwayster.weebly.com
How to remove symantec endpoint protection in safe mode alwayster Safe Endpoint Recovery 57% of attacks are missed by traditional antivirus solutions. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. 69% spend more time managing tools than defending against the threats. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. The. Safe Endpoint Recovery.
From www.crowdstrike.com
Endpoint Recovery Services Data Sheet CrowdStrike Safe Endpoint Recovery 69% spend more time managing tools than defending against the threats. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. Get back to business quickly. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. The key. Safe Endpoint Recovery.
From www.linkedin.com
Mastering Endpoint Recovery Navigating Challenges with Finesse Safe Endpoint Recovery The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix. Safe Endpoint Recovery.
From www.crowdstrike.com
Endpoint Recovery Services Data Sheet CrowdStrike Safe Endpoint Recovery Time is of the essence. 69% spend more time managing tools than defending against the threats. 57% of attacks are missed by traditional antivirus solutions. Get back to business quickly. The backup systems should also. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when. Safe Endpoint Recovery.
From ethertubes.com
Symantec Endpoint Recovery Tool (SERT) Pin Number (All of Them) Safe Endpoint Recovery The backup systems should also. 57% of attacks are missed by traditional antivirus solutions. Time is of the essence. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. Get back to business quickly. 69% spend more time managing tools than defending against the threats. The new release includes. Safe Endpoint Recovery.
From www.acronis.com
Cloud Solutions for Service Providers Acronis Safe Endpoint Recovery The backup systems should also. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. 69% spend more time managing tools than defending against the threats. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk. Safe Endpoint Recovery.
From www.youtube.com
Safe Endpoint Recovery Acronis Cyber Protect Cloud Acronis Cyber Safe Endpoint Recovery Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. Time is of the essence. Get back to business quickly. 57% of attacks are missed by traditional antivirus solutions. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data. Safe Endpoint Recovery.
From vistaitgroup.com
Join Us for an Endpoint Protection inar » Vista IT Group Safe Endpoint Recovery Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. The backup systems should also. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. 69% spend more. Safe Endpoint Recovery.
From www.youtube.com
How To Metallic™ Endpoint Backup & Recovery YouTube Safe Endpoint Recovery Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. Get back to business quickly. Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. The new release includes a new option for recovery using safe boot, the. Safe Endpoint Recovery.
From www.youtube.com
Yotta Safe Endpoint Backup & Recovery YouTube Safe Endpoint Recovery The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. Time is of the essence. Get back to business quickly. The backup systems should also. Protect your critical business data against ransomware attacks on laptop and desktops, theft of. Safe Endpoint Recovery.
From www.youtube.com
Veeam Endpoint Backup Free Install, Backup and Restore YouTube Safe Endpoint Recovery Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix. Safe Endpoint Recovery.
From iemlabs.com
Endpoint Security Keeping Network Endpoints Safe IEMLabs Blog Safe Endpoint Recovery Time is of the essence. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. The backup systems should also. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. 57%. Safe Endpoint Recovery.
From www.forbes.com
Quick Endpoint Recovery From Ransomware Is Needed Even With Data In The Safe Endpoint Recovery The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. Time is of the essence. Get back to business quickly. 69% spend more time managing tools than defending against the threats. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix. Safe Endpoint Recovery.
From techbast.com
Harmony Endpoint Recovery Full Disk Encryption Techbast Safe Endpoint Recovery Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. 69% spend more time managing tools than defending. Safe Endpoint Recovery.
From www.veeam.com
Veeam Endpoint Backup Free user guides and datasheets Safe Endpoint Recovery Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. The backup systems should also. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. The new release includes a new option for recovery using safe boot, the. Safe Endpoint Recovery.
From dellupdater.dell.com
to Dell Data Protection Endpoint Recovery Safe Endpoint Recovery Protect your critical business data against ransomware attacks on laptop and desktops, theft of devices, and accidental deletion of data with. The backup systems should also. The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. 69% spend more time managing tools than defending against the threats. Secure valuable endpoint data to. Safe Endpoint Recovery.
From www.crowdstrike.com
Endpoint Recovery Cybersecurity Services CrowdStrike Safe Endpoint Recovery The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. Time is of the essence. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit is installed,. The backup systems should also. Secure. Safe Endpoint Recovery.
From spochub.com
The Complete Guide to Endpoint Backup Solutions and Why They are Vital Safe Endpoint Recovery The key package and password will help decrypt the encrypted volume if the disk becomes corrupted or damaged. Get back to business quickly. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. 57% of attacks are missed by traditional antivirus solutions. Time is of the essence. 69% spend. Safe Endpoint Recovery.
From www.running-system.com
Create a Veeam Endpoint Backup Free Recovery Media Safe Endpoint Recovery Get back to business quickly. Secure valuable endpoint data to keep your users safe and compliant, and to simplify recovery from deletion, corruption and ransomware attack. The backup systems should also. The new release includes a new option for recovery using safe boot, the option to generate iso or usb, a fix for adk detection when the windows driver kit. Safe Endpoint Recovery.