Security Exposure Information . Explore with the attack surface map. security exposure management enriches asset information with security context that helps you to. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. Regardless of size, every organization has a broad set of assets. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. Query the enterprise exposure graph. security exposure management ingests security recommendations from multiple sources, including microsoft defender for. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets.
from capturetheatlas.com
Explore with the attack surface map. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Query the enterprise exposure graph. security exposure management ingests security recommendations from multiple sources, including microsoft defender for. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. security exposure management enriches asset information with security context that helps you to. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. Regardless of size, every organization has a broad set of assets.
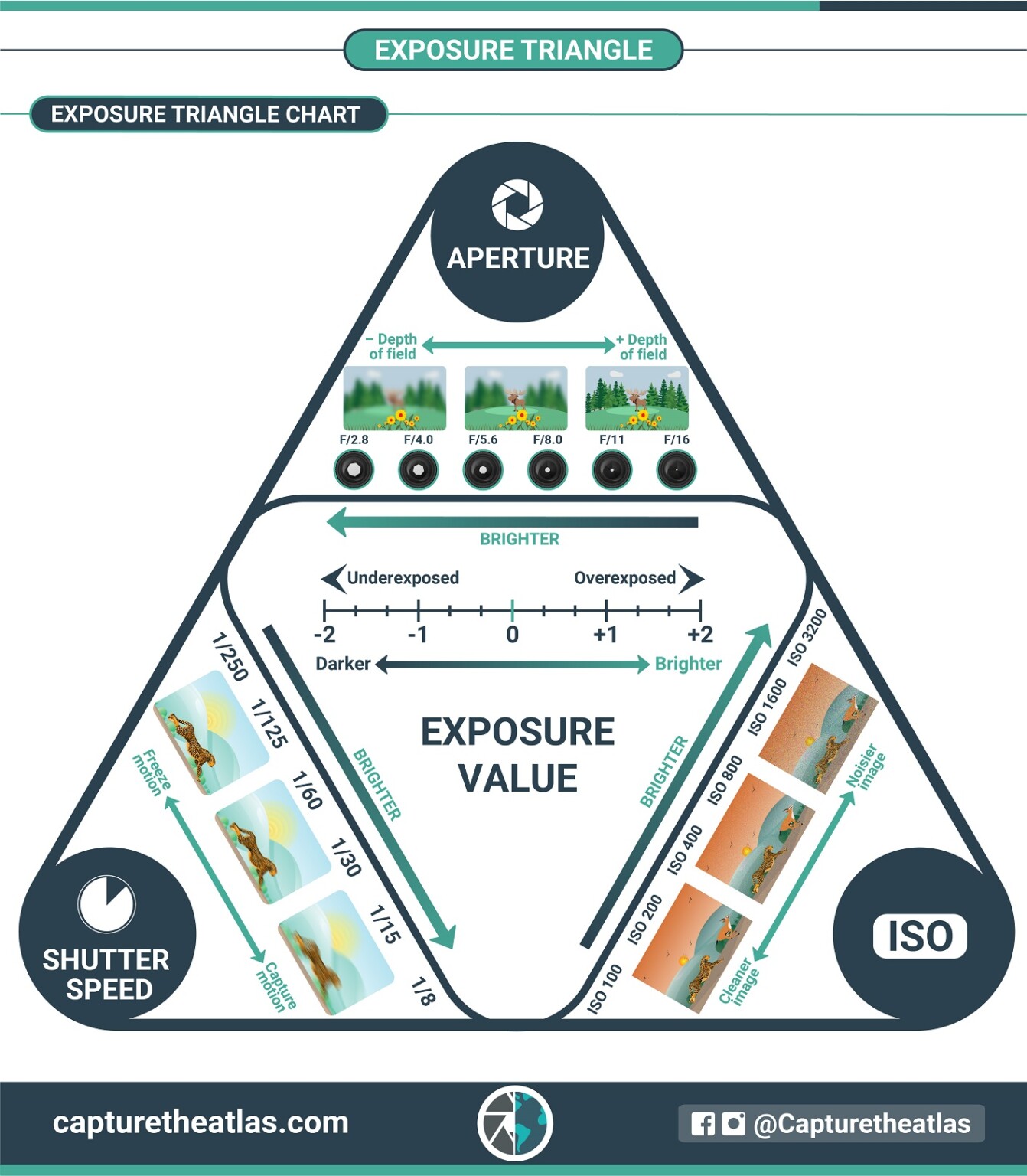
The Exposure Triangle in Photography Explained for Beginners
Security Exposure Information Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. Explore with the attack surface map. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Regardless of size, every organization has a broad set of assets. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. security exposure management enriches asset information with security context that helps you to. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. Query the enterprise exposure graph. security exposure management ingests security recommendations from multiple sources, including microsoft defender for. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets.
From safety4sea.com
Infographic Stages of common cyber attacks SAFETY4SEA Security Exposure Information transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. security exposure management enriches asset information with security context that helps you to. Explore with the attack surface map. Regardless of size, every organization has a broad set of assets. typically, this information includes sensitive personal information (pii) data. Security Exposure Information.
From newsitn.com
Cyberrisk quantification benefits and best practices News ITN Security Exposure Information Regardless of size, every organization has a broad set of assets. security exposure management enriches asset information with security context that helps you to. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths. Security Exposure Information.
From mavink.com
Cyber Security Kpi Dashboard Security Exposure Information Query the enterprise exposure graph. security exposure management enriches asset information with security context that helps you to. security exposure management ingests security recommendations from multiple sources, including microsoft defender for. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. microsoft security exposure management serves as a. Security Exposure Information.
From www.anoopcnair.com
Microsoft Security Exposure Management Using Defense Techniques HTMD Blog Security Exposure Information Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. security exposure management ingests security recommendations from multiple sources, including microsoft defender for. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. Query the enterprise exposure graph.. Security Exposure Information.
From www.theknowledgeacademy.com
What is Insider Threats in Cyber Security? Security Exposure Information typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. security exposure management enriches asset information with security context that helps you to. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. microsoft security exposure management serves as a cornerstone for. Security Exposure Information.
From mungfali.com
Safety Awareness Infographic Security Exposure Information Regardless of size, every organization has a broad set of assets. Explore with the attack surface map. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. Query the enterprise exposure graph. transform your security posture to stop attacks before they happen using microsoft’s security. Security Exposure Information.
From arcanum-cyber.com
Cyber Risk Management It’s not just for the IT Department! Security Exposure Information transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. Explore with the attack surface map. security exposure management ingests security recommendations from multiple sources, including microsoft defender for. security exposure management enriches asset information. Security Exposure Information.
From www.securitymagazine.com
Cybersecurity Index Shows the Most Exposed Countries 20200617 Security Exposure Information security exposure management enriches asset information with security context that helps you to. Explore with the attack surface map. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. transform. Security Exposure Information.
From www.corvusinsurance.com
Cyber Risks vs. Insurance Where Do They Intersect? Security Exposure Information Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Regardless of size, every organization has a broad set of assets. typically, this information includes sensitive. Security Exposure Information.
From www.wright.edu
Emergency Procedures Facilities Management and Services Wright Security Exposure Information security exposure management enriches asset information with security context that helps you to. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. Explore with the attack surface. Security Exposure Information.
From www.pinterest.de
This infographic illustrates the elements of a hazard control program Security Exposure Information Query the enterprise exposure graph. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. security exposure management enriches asset information with security context that helps you to. security exposure management ingests security recommendations from. Security Exposure Information.
From scantitan.com
site Security Exposure Scantitan Security Exposure Information microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. security exposure management enriches asset information with security context that helps you to. security exposure management ingests security recommendations from multiple sources, including microsoft defender for. Regardless of size, every organization has a broad set of assets. typically, this information includes sensitive personal. Security Exposure Information.
From xmcyber.com
Exposure Management Course XM Cyber Security Exposure Information Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. Regardless of size, every organization has a broad set of assets. Query the enterprise exposure graph. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. microsoft security. Security Exposure Information.
From blackkite.com
Reduce Your Cyber Exposure to Mitigate Your Cyber Risk Black Kite Security Exposure Information Explore with the attack surface map. security exposure management enriches asset information with security context that helps you to. Regardless of size, every organization has a broad set of assets. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. microsoft security exposure management. Security Exposure Information.
From xmcyber.com
What is Risk Exposure? XM Cyber Security Exposure Information security exposure management ingests security recommendations from multiple sources, including microsoft defender for. Explore with the attack surface map. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. security exposure management enriches asset information with security context that helps you to. Query the enterprise exposure graph. Aggregate your data and threat intelligence to. Security Exposure Information.
From www.slideserve.com
PPT Exposure Rating PowerPoint Presentation, free download ID1187198 Security Exposure Information Explore with the attack surface map. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. Regardless of size, every organization has a broad set of assets. Query the enterprise exposure graph. security exposure management enriches asset information with security context that helps you to.. Security Exposure Information.
From www.resmo.com
What is Continuous Threat Exposure Management (CTEM)? Resmo Security Exposure Information Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. security exposure management enriches asset information with security context that helps you to. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Explore with the. Security Exposure Information.
From blog.binaryedge.io
Security Exposure 2016 Security Exposure Information transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. Regardless of size, every organization has a broad set of assets. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model. Security Exposure Information.
From www.gartner.com
Cybersecurity Needs Continuous Threat Exposure Management Security Exposure Information Explore with the attack surface map. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. transform your security posture to stop attacks before they happen using microsoft’s. Security Exposure Information.
From themindstudios.com
How to Secure a site from Hackers Vulnerabilities + List of Tips Security Exposure Information Regardless of size, every organization has a broad set of assets. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Explore with the attack surface map. typically, this information includes sensitive personal information (pii) data. Security Exposure Information.
From capturetheatlas.com
The Exposure Triangle in Photography Explained for Beginners Security Exposure Information Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,.. Security Exposure Information.
From ehsdailyadvisor.blr.com
Infographic PFAS Exposure EHS Daily Advisor Security Exposure Information security exposure management ingests security recommendations from multiple sources, including microsoft defender for. security exposure management enriches asset information with security context that helps you to. Regardless of size, every organization has a broad set of assets. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose. Security Exposure Information.
From pentest-tools.com
How to detect Sensitive Data Exposure with Pentest Security Exposure Information Regardless of size, every organization has a broad set of assets. Explore with the attack surface map. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. Query the enterprise exposure graph. security exposure management enriches asset information with security context that helps you to. Aggregate your data and threat intelligence to proactively discover security. Security Exposure Information.
From learn.microsoft.com
Review attack paths in Microsoft Security Exposure Management Security Exposure Information Explore with the attack surface map. Query the enterprise exposure graph. Regardless of size, every organization has a broad set of assets. security exposure management enriches asset information with security context that helps you to. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets.. Security Exposure Information.
From www.slideserve.com
PPT Exposure Rating PowerPoint Presentation, free download ID1187198 Security Exposure Information transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. Query the enterprise exposure graph. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. Explore with the attack surface. Security Exposure Information.
From www.env.go.jp
Exposure Situations and Protection Measures [MOE] Security Exposure Information transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Query the enterprise exposure graph. security exposure management ingests security recommendations from multiple sources, including microsoft defender for. security exposure management enriches asset information with security context that helps you to. typically, this information includes sensitive personal information. Security Exposure Information.
From www.bankinfosecurity.com
Proactively Respond to Exposures Before Your Adversaries Do The Security Exposure Information Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. security exposure management ingests. Security Exposure Information.
From noeticcyber.com
The 5 Elements of Continuous Threat Exposure Management (CTEM) Security Exposure Information typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. security exposure management enriches asset information with security context that helps you to. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. transform your security posture to stop attacks before they happen using microsoft’s security exposure. Security Exposure Information.
From checkmarx.com
Code Exposure The Vulnerabilities in Your Code & Where They Originate Security Exposure Information typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. security exposure management enriches asset information with security context that helps you to. microsoft security exposure management serves as a cornerstone for. Security Exposure Information.
From www.picussecurity.com
Implement and Improve a Continuous Threat Exposure Management (CTEM Security Exposure Information security exposure management ingests security recommendations from multiple sources, including microsoft defender for. Query the enterprise exposure graph. Explore with the attack surface map. microsoft security exposure management serves as a cornerstone for proactive risk management, empowering. security exposure management enriches asset information with security context that helps you to. typically, this information includes sensitive personal. Security Exposure Information.
From medium.com
Sensitive Data Exposure Vulnerability Causes and Prevention by Security Exposure Information Explore with the attack surface map. security exposure management enriches asset information with security context that helps you to. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal. Security Exposure Information.
From www.threatq.com
Learn How to Detect and Manage External Exposure Risks Security Exposure Information transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. Regardless of size, every organization has a broad set of assets. security exposure management ingests security. Security Exposure Information.
From www.lockr.io
HOW TO PREVENT SENSITIVE DATA EXPOSURE Lockr Security Exposure Information security exposure management enriches asset information with security context that helps you to. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. Explore with the attack surface map. microsoft security exposure. Security Exposure Information.
From www.synapsa.tech
Security exposure index Synapsa Networks Security Exposure Information Regardless of size, every organization has a broad set of assets. typically, this information includes sensitive personal information (pii) data such as health records, credentials, personal data,. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Query the enterprise exposure graph. Aggregate your data and threat intelligence to proactively. Security Exposure Information.
From prophaze.com
What Is Sensitive Data Exposure Vulnerability & How To Prevent It Security Exposure Information Regardless of size, every organization has a broad set of assets. transform your security posture to stop attacks before they happen using microsoft’s security exposure management in microsoft defender. Aggregate your data and threat intelligence to proactively discover security gaps, identify cyberattack patterns and model attack paths that could expose your critical assets. typically, this information includes sensitive. Security Exposure Information.